In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.
The filtering capabilities here are very comprehensive. You can filter on just about any field of any protocol, even down to the hex values in a data stream. Sometimes, the hardest part about setting a filter in Wireshark is remembering the syntax, so below are the top display filters that I use. All examples below are from a 10 minute period of packet capture on my lab network. I am simply using filters to manage the view.
What Is a Filter?
When you first fire up Wireshark, it can be daunting. Servers are broadcasting, computers are asking for webpages, and on top of this, the colors are difficult to digest with confusing number sequences to boot. Working from this mess would be a headache!
Moving into larger wireless networks, the sheer amount of broadcast traffic alone will slow you down and get in your way. Thankfully, Wireshark includes a rich yet simple filter language that allows you to build quite complex expressions. You can compare values in packets, search for strings, hide protocols you don't need, and so much more.
Wait! Where Do I Find These Filters?!?
The most visible and easy to use spot is right in front of you!
![]()
Whoop there it is. You can type filter syntax right into this field and watch in wonder as your once jumbled pile of messages transforms into a neat clean stack ordered how you tell it. This works on a live capture, as well as in files of dates you might be importing.
Also, as you type, notice the color of the text field changes from red to green, signaling when you have a valid filter. The auto complete guesses are also there to help you put together new combos of filtering.
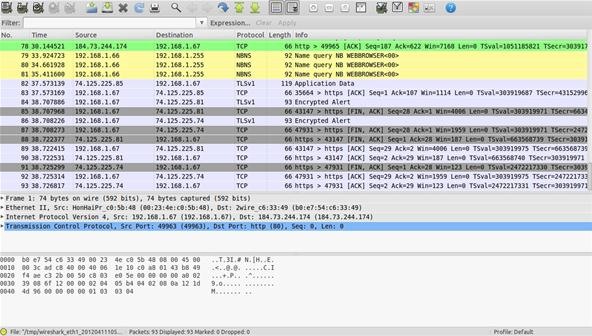
ip.addr ==x.x.x.x
Sets a filter for any packet with x.x.x.x, as either the source or destination IP address. This is useful if you want to look for specific machines or networks. A good example would be some odd happenings in your server logs, now you want to check outgoing traffic and see if it matches. This is a great filter for that.
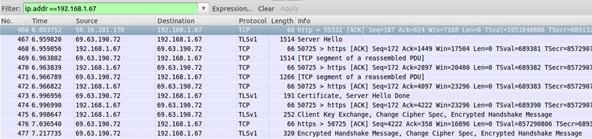
ip.addr ==x.x.x.x && ip.addr ==x.x.x.x
Sets a conversation filter between the two IP addresses. This is useful to watch communication between two specific hosts or networks. Sometimes you only need specific data, so there is no need to bother sifting through the others.
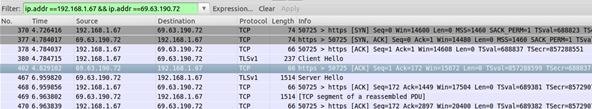
Also of note with the '&&' operator—those of you who are familiar with programming will know this—but it could be repeated. The '&&' will return both conditions in the statement, and not one or the other as is sometimes thought. And yes, you need both of the ampersands.
http or dns
Sets a filter based on protocol. You do not always need to know every single packet traveling across, so being able to narrow down to the exact protocol you need is helpful. Looking to track some odd FTP traffic? set it for 'ftp'. Looking to see why you can't find any websites? Try setting it to 'dns' and see what is going on.

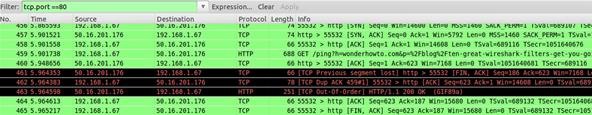
tcp.port==xxx
Sets filters based on TCP port numbers. Because port numbers can be reassigned and used in various places (within obvious limitations), it is useful to be able to just look at traffic going into and out of a specific port. Here we will look for all traffic using port 80 (HTTP).
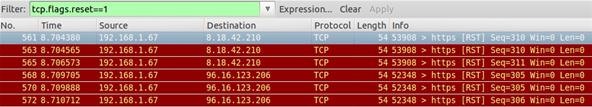
tcp.flags.reset==1
Sets filters to show all TCP resets. Each packet contains a TCP header. Each of these headers contains a bit known as the "reset" flag. In most packets, this bit is set to 0 and has no effect, however if this bit is set to 1, it indicates to the receiving computer that it should should immediately stop using the connection—A TCP reset basically kills a TCP connection instantly.
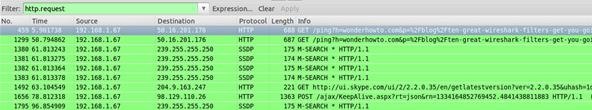
http.request
Sets a filter for all HTTP GET and POST requests. This will show webpages being accessed for the most part here.
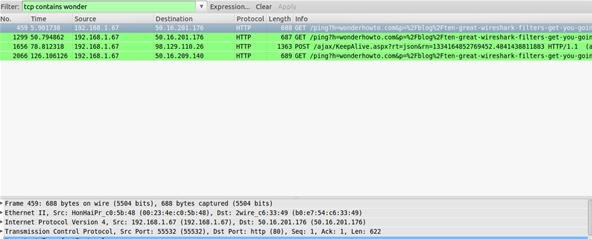
tcp contains xxx
Set a filter based on a string you provide and searches TCP packets for that string. If you were looking for a specific item or user name you knew was appearing in the packet, this is a filter you could use. Here we type 'wonder' as I am writing this article and we see:
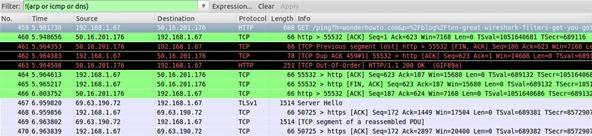
!(arp or icmp or dns)
This filter format is designed to filter out certain types of protocols you might not want. In my example, we have ARP, ICMP, and DNS—all of which are broadcasts—to hide. This lets our eyes work on other things.
In Closing
Do you have other filters you use? Share them with us! There are a lot of useful combos and I know I did not list all of them here.
Leave us a comment below, shoot me a message or start a thread in our forum.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























2 Comments
nice and juicy
cool
Share Your Thoughts