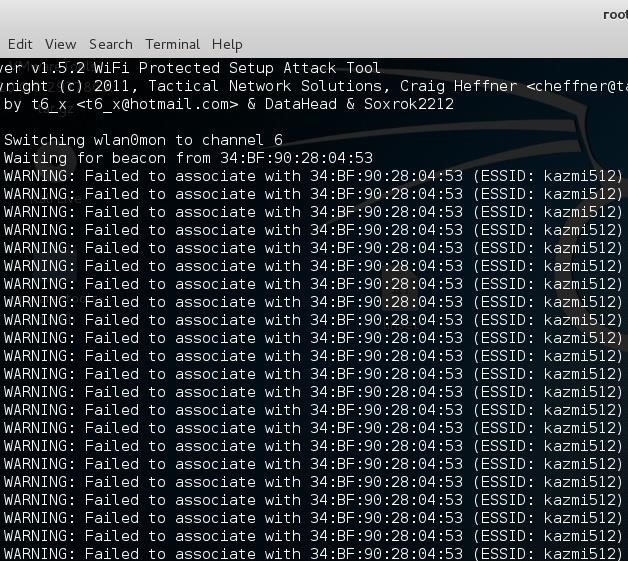
This is what shows up every time I try to start reaver regardless of the AP I'm trying to associate with. Tried it against all the routers that show up with the airodump-ng command and it fails every time.
P.S: I'm using Kali Sana on Vmware and it's fully updated.
Any help will be highly appreciated.







































12 Responses
This is a very generic and common error ... Give more details about your wifi hardware (internal / external ?) and the full reaver command you are issuing. Also consider to try on a live usb, as using reaver in a VM might give problems even if all planets align for the best.
I'm using Alfa awus036h. Previously I had tried reaver on Kali 1.1.0 against all the Wi-Fi networks around my vicinity and the reaver attack worked flawlessly. But now it doesn't even associate with the essid with Kali 2.0
Reaver command I'm using is : reaver -i wlan0mon -c -b -vv
Please tell me is there a way to fix this.
Also, let me tell you that I had cracked the router's PIN previously so I have the right PIN which can be used to crack the newly set password (since the router's password that I'm attacking has been changed)
So I even know the right PIN of the device I'm trying to infiltrate. I know I can try the Custom PIN with the addition of -p in the above mentioned code. All I want reaver to do is to 'associate with the network' so it could begin the cracking session and return me with the password within 5-10 secs.
Are you attempting a wps attack, if so why not use the wash command to find out what ap's have wps enabled, instead of airodump-ng. If not trying wps attack ignore this and provide some more info such as full reaver cmd as triphat mentioned.
Yes, it says "YES" next to WPS availability.
Here's the situation I'm into atm.
I'm using Alfa awus036h. Previously I had tried reaver on Kali 1.1.0 against all the Wi-Fi networks around my vicinity and the reaver attack worked flawlessly. But now it doesn't even associate with the essid with Kali 2.0
Reaver command I'm using is : reaver -i wlan0mon -c -b -vv
Please tell me is there a way to fix this.
Also, let me tell you that I had cracked the router's PIN previously so I have the right PIN which can be used to crack the newly set password (since the router's password that I'm attacking has been changed)
So I even know the right PIN of the device I'm trying to infiltrate. I know I can try the Custom PIN with the addition of -p in the above mentioned code. All I want reaver to do is to 'associate with the network' so it could begin the cracking session and return me with the password within 5-10 secs.
Did you run airmon-ng check kill before putting your adpater into monitor mode. I know in 2.0 this is needed. Hope that helps
Yep! I did.
I am having the same issue with a specific target. I always thought that the 'failed to associate' meant that that target is not vulnerable to this attack (blocks this method or something like that).
that has been my findings as well, but he mentioned he has used this attack with 1.1.0. I have not tried that yet, i have only used 2.0. Tempted to go down to see if it is more successful than 2.0.
That might be a good idea yeah I initially had the old one and automatically assumed newer was better. The first thing I noticed about 2.0 is that you NEED to first kill some processes before monitor mode as you mentioned above.
I am having a same issue with my Ralink RT3070 usb wifi card !
I am using latest kali -2016-1 on USB !
With 2,0 version everything worked fine ! Most funny is that my embedded wifi card (Atheros 9285) work fine, only range is to small !
Ralink show only failed to associate no matter whitch network i try to conect !
I have same cards and same problem... Did you find solution?
Go download the "minidwep-gtk" package for kali linux and on launching the attack once you get the error start minidwep-gtk and click scan ...you r done..
Share Your Thoughts