In our discipline, we may WANT to ignore the legal consequences until they slap us upside the head, but that is not a very prudent strategy. To help all my apprentice hackers better understand what is and is not legal in hacking, I dedicate this forum.

The Cyber Crime Law Enforcement
In the United States, most hacking is investigated and prosecuted by the federal law enforcement. Surprisingly, the Secret Service is the lead agency, but they primarily are involved in coordinating the response, usually not investigating. They delegate the investigation to one of numerous federal agencies, but the FBI's Cyber Crime Task Force is the agency most often involved.
There are cyber crime task forces in each locality. These local cyber crime task forces generally are assigned the smaller local cases and the local FBI special agents have limited training and background in hacking and forensics. They often rely on good old detective work to solve these cases. I can't tell how many times hackers have been tracked down because they bragged about their exploits. You don't have to be a techno-genius to track down a bragging hacker who suddenly is awash in money.
Although federal law makes it a felony to do more than $5,000 damage, the general rule is the FBI won't even get involved in cases that involve less than $100,000 in damages. Note that the key word here is "damages". This has nothing to do with how much the hacker gets away with, but rather how much damage is done to the individual or business.
As I pointed out in my guide on evading detection while DoSing, a one-minute DoS against Amazon would cause over $100,000 in revenue losses, and that does not even include the cost of lawyers and consultants to resolve the situation. A simple one-minute DoS against Amazon might mean over a $1 million in damages! Good luck paying that back in restitution.
Federal Laws Regarding Cyber Crime
Federal agencies in the U.S. prosecute cases using two primary federal statutes; U.S. Title 18 Section 1029 and 1030. These two statutes are so broad and ambiguous that many things that are not intended to be hacking, could very well be found to be illegal.
Of these two, U.S. Title 18 Section 1030 is most often used to prosecute hacking in the states. That being the case, let's take a look at it. I have reprinted the key section that defines what activity is illegal below. I know there is a lot of legalese here, but let's try to stay focused and examine the critical sections closely.
Title 18 - Crimes & Criminal Procedure - U.S.C. 1030 - Fraud & Related Activity in Connection with Computers

That section relates to unauthorized access to U.S. government computers.
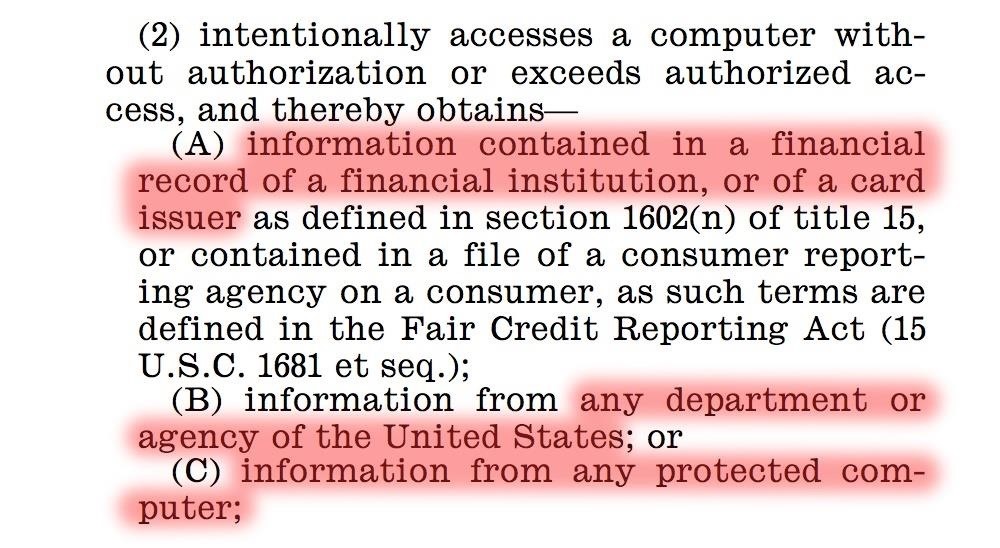
Please note the sections I have highlighted above to get your attention that among other things, makes accessing "information from any protected computer". Since the courts have ruled that "protected computer" can be a computer with as little protection as a password, this mean essentially that EVERY computer is covered in this section.

This section is key as well. This section defines ways that a computer might be damaged such as "transmission of a program, information, code or command" or "accesses a protected computer without authorization" which then "causes damage or loss".
As you can see, this is so vaguely worded that even a vulnerability scan might be construed as criminal if the prosecutor and "victim" can show there was damage or loss. Imagine a scenario where you are doing a vulnerability scan on a poorly designed website and it crashes as a result. You may have committed a federal felony!

So, that is the law in its entirety. I left out the section on penalties, but you can imagine that it's not joyful reading.
Be Careful Out There!
My message to all of you is simply, "Be Careful Out There!". Even if you don't have malicious intentions, the knowledge that you now have can be misconstrued as bad intentions. If a website blows up while you are scanning it, no one is going to ask about your intentions before they throw you in prison.
For someone like myself who has danced on both sides of the law, I can tell you firsthand that when someone finds out you have BackTrack or Kali or any hacking tools AND the knowledge of how to use them, you are suddenly guilty until proven innocent.
Just a fair warning to all my hacker apprentices.
Newscast 1 and 2 images via CNN, Jeremy Hammond via Chicago PD









































20 Responses
(head bowed low) Yes sir got the message, stop nikto'ing everything that moves. I have been studying the options and know it can crash a system.
But I am thinkingggg, do some passive recon, light weight to make sure the system can stand a full scan. I mean how else am I gonna learn whats out there, but to get experience and exposure by exploring many sites. Sites I thought were weak I am now seeing are not that bad compared to some really really messy ones. I would never have known that without exploring. And I actually now understand, by seeing whats out there even a fairly weak site would be by passed as too much work when there is so much gravy still out there.
I personally have three rules that I limit myself to.
(They have the money and power to find you, no matter how good you are.)
(Crossing that kind of a line with friends/family can be damaging to relationships and really isolate you.)
(I'm not religious, but I live by the rule 'do unto others as you would have done to you'. Though, sometimes I do break rule 3 in regards to black hats...)
But that's just me. It's still good to know exactly what can and can't get you into trouble, especially these days where a simple DDoS can land you 10 years. Everyone looking at developing these skillsets should know what they're getting into before they start.
I just saved you all about 1k, fortunately I am a successful artist with a few attorney that collect my art so this didn't cost me real cash. I shot them an email of this article telling them that I want to scan systems for educational purposes with the possibility of starting a network security service. (BTW merchants who take credit cards have to get pen tested once a year).
I will make this brief, Intent is the key. Do like I am gonna do, trot down to your local city hall and get a business license for network security.
Make a quick website for network security.
Shoot a few emails to sysadmins with your scan results asking if they would be interested in getting results like these once a month.
That's just a quick run down, what you are doing is laying the foundation for a defense with the intent for a legit business should one of your scans cause problems. While you will still be liable for damages should you crash a system, and while no defense is perfect (unless you can afford Johnnie Cochran) It will go a long way in helping to keep that ugly orange jump suit as your only choice of clothes.
If you all would like a more detailed brief shoot me a mssg and I will do a post.
Thanks for this info, Jon. I agree with your strategy.
Yep my dad warned me about hacking now I know why he did. Thnx for the info
Sir OTW,
I want to replace backtrack with kali as a dual boot system. I want to have windows and kali as my only dual-boot os. Can you please tell me how to remove backtrack and replace it with kali, without damaging my windows os. I have backed up all my important files, but don't possess a windows cd. By the way my windows version is windows 7. Sir please reply quickly, as I don't get alot of time to spend on my laptop, because of my studies. Sir i am currently waiting for your reply, so please reply quickly. Thanks in advance Sir.
U31
U31:
All you need to do is delete the partition with BT on it and then install Kali on a new partition.
OTW
When i installed backtrack, i couldn't locate the partition where it actually installed. I have 2 hard drives, one with 2 partitions my OS (win8) and some data; and another one with 1 partition for some other data and some 25gb of unallocated space (that i intended for bt). Yet, when i installed bt the unallocated space stayed unallocated (at least in the disk manager of windows).
As i am just starting on backtrack, i was thinking of picking up the last version (kali) as it would be simpler than adapt to it in a few months and since it brought real changes from bt5r3 (debian vs ubuntu). should i just assume that my bt is installed on the unallocated space shown by win8? if that's the case why is it showing as unallocated? if it isn't the case, how could it be installed on one of my ntfs partitions (using a disk image file maybe)??
Sir OTW,
Thats exactly what I want to do. I know alot about partitions, but I don't know how to delete them. Sir if you can tell me how to do that, I would be really grateful.
U31
your have to do it in windows, search deleting partitions in windows, lots of tuts and its easy. get kali live usb or cd. Do a search for kali install, there are lots of tuts.
When you deleted the partition its now free space that kali will see on install. install to that partition that kali will create.
U31:
If you know a lot about partitions, you should know how to delete them. It's not hard, just format the partition and then it becomes free space.
ghost_
if he's going to do that he just needs to install kali to that partition as kali will delete everything anyways. I thought he was wanting to create un allocated space on the disk.
Amazing post as always from OTW.
I have been reading a lot of different articles on this website, and i find them really helpful. Also, i think that challenges and competitions could be nice additions for helping noobies like me get some experience in a "legal" fashion.
I have to admit that this article is very instructive. Although i don't live in the US it's nice to know that starting 100 000$ i could get busted by the FBI like in hollywood movies lool.
In a more serious tone, i think at least for us newbies virtualization can be good solution to stay out of trouble. But in the case we don't restrain ourselves, how can authorities find us if the isp doesn't know us (not considering here any "traditional" investigation mean). Assuming for example that i live next to a coffee with available WiFi, and that this connection is only used for hacking (in other words not using my personal pc, and not connecting to my fb account while hacking)?
Soulei1990:
First, the investigators could track you back to the IP address of the coffee shop. Having assisted investigators in similar investigations, they always insist that in over 90% of cases, the attacker is always within a few blocks of the IP address. So far, they have always been right. So, they would then begin to use good old detective techniques to investigate those who may have used the IP of the coffee shop. If they suspect you and get a search warrant, your computer will indict you with all the evidence of your activity.
Virtualization is no panacea. Your MAC address will still attached to the packet unless you use MAC spoofing. Evidence such as the file system and registry will still be there in the virtual machine.
OTW
I am still trying to master linux and have been working on moving all my var, tmp and swap files to a micro sd card (not as easy as one might think) Easy to remove and get rid of. Would this eliminate most of the evidence. I have not checked into it, but I am thinking just changing your mac address would be logged. Or would I just basically have to move my whole home directory?
Jon:
Yes, move your whole home directory to the SD card. Also, disable logging and set HISTFILE=0.
OTW
Aww ic, ok ok the var directory is actually within the root structure. So If I move my home var would still be present for forensic's. So we just make sure there is nothing in it to look at. :)
I am thinking of setting up a little pearl script to run before and after any security work since we are getting pearl training and this looks like a good project to build with..
Excellent idea, Jon. I hope you will share it with us. That would be an excellent use of Perl.
What happens if im sitting in my country (Denmark).
And hacking f.x. USA, will my country be able to do anything to me?
It's not because I'm hacking my country, so they shouldnt be able to arrest me right?
Than you have to look up the extradition policy that Denmark has with the states. It might very well be that you can be send there...
Share Your Thoughts