I read this whitepaper http://pastebin.com/Dg5wWSAm from anonsec. It explains each steps of how they managed to control a drone remotely. It is really interesting and I find real cases way more educational (they explain better than the theory/dedicated vulnerable web applications). I was wondering if anyone had other cases like this: they explain each steps on how they exploited a device? It is not to copy but to really understand in a real scenario, how they apply their knowledge and actually manage to gain root access, servers, web apps, etc.. Thanks peops =)
Forum Thread: Looking for whitepapers (real case/scenario)
- Hot
- Active
-
 Forum Thread:
HACK ANDROID with KALI USING PORT FORWARDING(portmap.io)
12
Replies
Forum Thread:
HACK ANDROID with KALI USING PORT FORWARDING(portmap.io)
12
Replies
2 days ago -
 Forum Thread:
Hydra Syntax Issue Stops After 16 Attempts
2
Replies
Forum Thread:
Hydra Syntax Issue Stops After 16 Attempts
2
Replies
3 wks ago -
 Forum Thread:
Hack Instagram Account Using BruteForce
208
Replies
Forum Thread:
Hack Instagram Account Using BruteForce
208
Replies
3 wks ago -
 Forum Thread:
Metasploit reverse_tcp Handler Problem
47
Replies
Forum Thread:
Metasploit reverse_tcp Handler Problem
47
Replies
2 mo ago -
 Forum Thread:
How to Train to Be an IT Security Professional (Ethical Hacker)
22
Replies
Forum Thread:
How to Train to Be an IT Security Professional (Ethical Hacker)
22
Replies
2 mo ago -
 Metasploit Error:
Handler Failed to Bind
41
Replies
Metasploit Error:
Handler Failed to Bind
41
Replies
2 mo ago -
 Forum Thread:
How to Hack Android Phone Using Same Wifi
21
Replies
Forum Thread:
How to Hack Android Phone Using Same Wifi
21
Replies
3 mo ago -
 How to:
HACK Android Device with TermuX on Android | Part #1 - Over the Internet [Ultimate Guide]
177
Replies
How to:
HACK Android Device with TermuX on Android | Part #1 - Over the Internet [Ultimate Guide]
177
Replies
3 mo ago -
 How to:
Crack Instagram Passwords Using Instainsane
36
Replies
How to:
Crack Instagram Passwords Using Instainsane
36
Replies
3 mo ago -
 Forum Thread:
How to Hack an Android Device Remotely, to Gain Acces to Gmail, Facebook, Twitter and More
5
Replies
Forum Thread:
How to Hack an Android Device Remotely, to Gain Acces to Gmail, Facebook, Twitter and More
5
Replies
3 mo ago -
 Forum Thread:
How Many Hackers Have Played Watch_Dogs Game Before?
13
Replies
Forum Thread:
How Many Hackers Have Played Watch_Dogs Game Before?
13
Replies
3 mo ago -
 Forum Thread:
How to Hack an Android Device with Only a Ip Adress
55
Replies
Forum Thread:
How to Hack an Android Device with Only a Ip Adress
55
Replies
4 mo ago -
 How to:
Sign the APK File with Embedded Payload (The Ultimate Guide)
10
Replies
How to:
Sign the APK File with Embedded Payload (The Ultimate Guide)
10
Replies
4 mo ago -
 Forum Thread:
How to Run and Install Kali Linux on a Chromebook
18
Replies
Forum Thread:
How to Run and Install Kali Linux on a Chromebook
18
Replies
5 mo ago -
 Forum Thread:
How to Find Admin Panel Page of a Website?
13
Replies
Forum Thread:
How to Find Admin Panel Page of a Website?
13
Replies
6 mo ago -
 Forum Thread:
can i run kali lenux in windows 10 without reboting my computer
4
Replies
Forum Thread:
can i run kali lenux in windows 10 without reboting my computer
4
Replies
6 mo ago -
 Forum Thread:
How to Hack School Website
11
Replies
Forum Thread:
How to Hack School Website
11
Replies
6 mo ago -
 Forum Thread:
Make a Phishing Page for Harvesting Credentials Yourself
8
Replies
Forum Thread:
Make a Phishing Page for Harvesting Credentials Yourself
8
Replies
6 mo ago -
 Forum Thread:
Creating an Completely Undetectable Executable in Under 15 Minutes!
38
Replies
Forum Thread:
Creating an Completely Undetectable Executable in Under 15 Minutes!
38
Replies
7 mo ago -
 Forum Thread:
Hacking with Ip Only Part [1] { by : Mohamed Ahmed }
5
Replies
Forum Thread:
Hacking with Ip Only Part [1] { by : Mohamed Ahmed }
5
Replies
8 mo ago
-
 How To:
Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
How To:
Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
-
 How To:
Crack SSH Private Key Passwords with John the Ripper
How To:
Crack SSH Private Key Passwords with John the Ripper
-
 How To:
Hack Android Using Kali (Remotely)
How To:
Hack Android Using Kali (Remotely)
-
 Hack Like a Pro:
How to Spear Phish with the Social Engineering Toolkit (SET) in BackTrack
Hack Like a Pro:
How to Spear Phish with the Social Engineering Toolkit (SET) in BackTrack
-
 How To:
Dox Anyone
How To:
Dox Anyone
-
 How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
-
 How To:
Find Identifying Information from a Phone Number Using OSINT Tools
How To:
Find Identifying Information from a Phone Number Using OSINT Tools
-
 How To:
Find Passwords in Exposed Log Files with Google Dorks
How To:
Find Passwords in Exposed Log Files with Google Dorks
-
 BT Recon:
How to Snoop on Bluetooth Devices Using Kali Linux
BT Recon:
How to Snoop on Bluetooth Devices Using Kali Linux
-
 How To:
Use Command Injection to Pop a Reverse Shell on a Web Server
How To:
Use Command Injection to Pop a Reverse Shell on a Web Server
-
 How To:
Buy the Best Wireless Network Adapter for Wi-Fi Hacking in 2019
How To:
Buy the Best Wireless Network Adapter for Wi-Fi Hacking in 2019
-
 Android for Hackers:
How to Turn an Android Phone into a Hacking Device Without Root
Android for Hackers:
How to Turn an Android Phone into a Hacking Device Without Root
-
 How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
-
 How To:
Use Metasploit's WMAP Module to Scan Web Applications for Common Vulnerabilities
How To:
Use Metasploit's WMAP Module to Scan Web Applications for Common Vulnerabilities
-
 How To:
The Hacks Behind Cracking, Part 2: How to Generate Software Keys
How To:
The Hacks Behind Cracking, Part 2: How to Generate Software Keys
-
 Hack Like a Pro:
How to Hack Remote Desktop Protocol (RDP) to Snatch the Sysadmin Password
Hack Like a Pro:
How to Hack Remote Desktop Protocol (RDP) to Snatch the Sysadmin Password
-
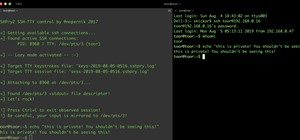
 How To:
Spy on SSH Sessions with SSHPry2.0
How To:
Spy on SSH Sessions with SSHPry2.0
-
 How To:
Exploit EternalBlue on Windows Server with Metasploit
How To:
Exploit EternalBlue on Windows Server with Metasploit
-
 How To:
Check if Your Wireless Network Adapter Supports Monitor Mode & Packet Injection
How To:
Check if Your Wireless Network Adapter Supports Monitor Mode & Packet Injection
-
 How To:
Find Vulnerable Webcams Across the Globe Using Shodan
How To:
Find Vulnerable Webcams Across the Globe Using Shodan
















7 Responses
On the Blackhat conference website you can find papers to the talks that were held.
Yes someone told me to search for this : filetype:pdf site:media.blackhat.com <"optional topic of interest">
'Web Application Hackers Handbook" has a bunch of examples. I've purchased the book and it is amazing. It will tell you everything you need to know plus real life examples of attacks. From what I hear you might be able to download it from the net for free by searching for the name of the book plus 'pdf' at the end.
I have the 2nd one at home xD
nice. me 2. that's the one I meant. I never really paid attn to reading the real scenarios before but I was last night and they were quite good.
Sans.org has a lot of papers too under reading room!
Thank, found them =)
Share Your Thoughts