Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!
Okay, it may be a potential skiddie toy, but it saves a lot of time when we already know the process of getting a password. This tool is able to do many attacks, such as Caffe-Latte, ChopChop, coWPAtty hashing, and.... yes, cracking the WPS Pin with Reaver!
I hope this guide isn't taken as a shortcut to OTW awesome guides, and it's taken as a complement to that knowledge, because this script won't work all the time, while doing attacks manually tend to be way more successful. Anyways, it's worth a try!
Step 1: Launch the Script and Select Wireless Device
For this tutorial, I will assume you're using your terminal as root.
If you're not, you can access root with by typing 'su' if you have root's password, or 'sudo su' if your account has superuser privileges.
Now we launch the script again, by typing
wifite
And if we have more than one wireless device, we'll be prompted which one we want to use.
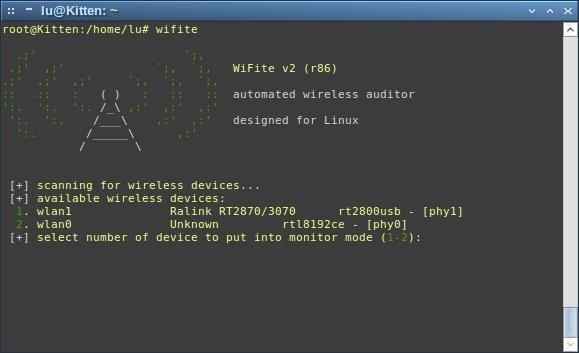
In my case, I have a TL-WN7200ND I bought, and the wireless card that comes onboard in my notebook. Be sure to check this guide to make sure you're using the right adapter. For this attack (and most wireless attacks, unless you're really patient) you'll need an adapter which allows packet injection.
I'll be using wlan1 because that's my adapter. If you're not sure which one is your adapter, one good indicator is reading that name to the left of [phy], for example, I have one that says 'usb' in it, and one that doesn't. And yep, I have it plugged to USB, so that one's it.
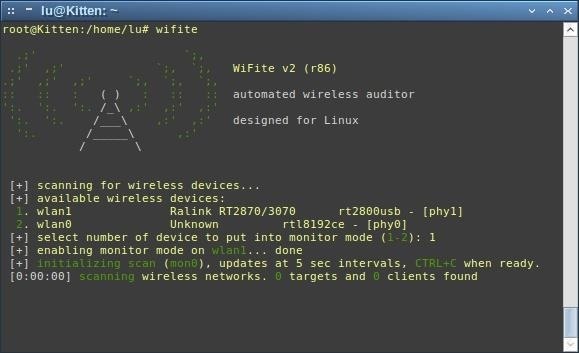
I choose it by typing '1', and the script enables monitor mode on that device (sometimes it doesn't, and you have to do it manually previous to running the script).
Step 2: Select Target Access Point
After 5 seconds, you'll be presented with something like this:
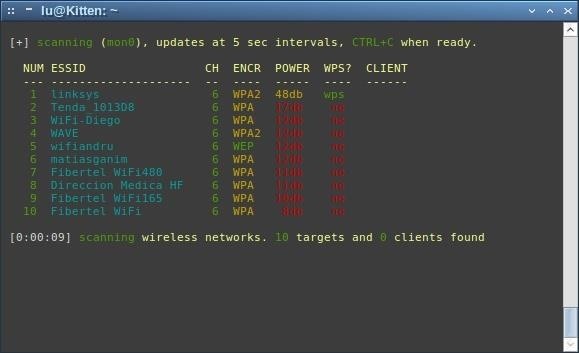
As you can see, there's a listing of the ESSID of near access points, the channel they're on, the type of encryption they're using, the power of signal our antenna is receiving (although if you see 99db, it may be a misreading), if it is WPS enabled, and if it has any client connected to the network. For this guide, we'll choose the first access point from this list, because it's has WPS.
Press 'Ctrl+C' to stop the wireless networks scan, and then type in the number corresponding to the AP you want to focus your attack on.
Step 3: Wait for the Attack to Complete
The script will start by attacking WPS first, because it's faster than capturing the handshake and it requires no clients attached.
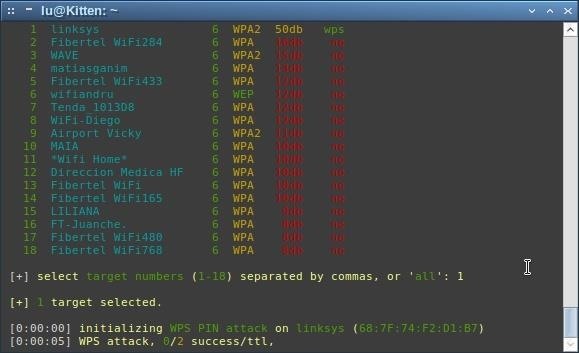
If the attack is working, you'll see a percent to start going up to the right of 'success/ttl'
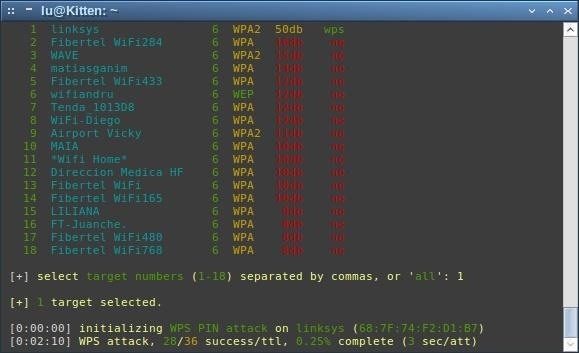
Remember, the more signal power you get from that AP, the less packets will be lost, and the fastest this attack will be completed. You can improve it with directional antennas, or simply by getting closer to the AP, if you know where it is (and you can move your PC there).
If you didn't want to do a WPS attack, and prefer to skip right to handshake capturing, pressing 'Ctrl+C' will stop this attack and start that one. If you press 'Ctrl+C' again, the script will exit.
Step 4: Success!
If the attack was successfully performed, you'll get a screen like this, with WPS PIN and the AP's password:
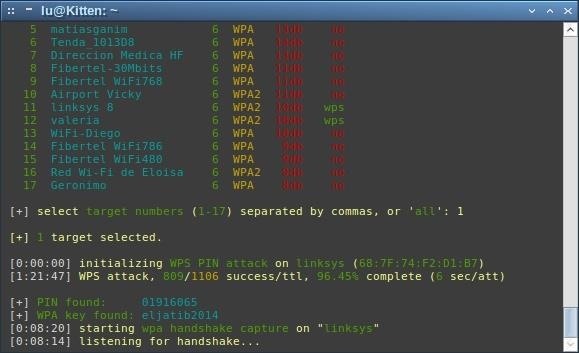
If you're lucky like me, it'll get one of the two pairs of 4 numbers in the pin really quick, and it'll go from 4% to 90% in a breeze. If that's not your case, this attack may take from 8 to 10 hours, all of which you should stay in range of the AP. It's not an attack you can perform on most notebooks battery power, but if you can plug it in and leave it working in place, you're good to go.
It will start capturing handshake after the attack, but what do you want it for? Ctrl+C and finish the script!
I hope you find this guide helpful, and learn the underworkings behind what this script does. If this guide has acceptance, I may explain other attack types with wifite as well, but I highly encourage for anyone to try it on their own (Hint: It can attack several AP's in a row!).
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















33 Comments
Greetings, nice guide and thanks for your time..
Did you spoof the MAC on the monitor?
Random Derps:
I use wifite >some< and know that to get the most from it you need to go into the script and make some edits to a few lines of options.
Prolly would of beat up that #6 WEP abit too.
Nope, I didn't spoof it, but it could be easily done with 'macchanger', or specifying --mac when running the script.
Which edits are you talking about? I know a bit of python, but not enough to go through this code and improve it. Could you give me some pointers?
I didn't understand what you said about WEP, but I found it failing the most when doing attacks to WEP.
Kitten:
I tried wifite and I got a problem, (note: I did choose networks with high db's) it could never capture the passes or have any successful ttls.
S_R
Yeah can the external or internal adapter packet inject?
Have you been into the script and added a wordlist for the handshake and tshark check the pcaps?
There's no need for a wordlist in a WPS attack, as Reaver tries every possible PIN for it. PIN's have 8 digits, or, to be more precise, two separate 4 digits passwords, so there isn't much to try out.
I'm writing a guide for dictionary attack right now, I'll publish the article today :)
Cyber:
My external adapter is capable of packet injections and mon0.
The problem I face is what to do with the handshake once captured.
S_R
You're not attempting a WPS crack but... if you got a '.cap' file, try this:
In Kali there's a dictionary located in /usr/share/wordlists/rockyou.txt.gz
You must extract it first by typing:
gzip -d /usr/share/wordlists/rockyou.txt.gz
And you will get a 'rockyou.txt' file, that's a pretty good dictionary!
Then, you just have to type
aircrack-ng -w /usr/share/wordlists/rockyou.txt <location of your .cap file>
Hope this helps :)
P.S.: In BackTrack you have two, located at:
/pentest/passwords/wordlists/rockyou.txt
and
/pentest/passwords/wordlists/darkc0de.lst
Kitten:
There's a problem.My Kali Linux states "gzip: No such file or directory"
S_R
Please do this:
ls /usr/share/wordlists > wordlists.txt
You'll get a text file with a list on your home folder. Copy me here what's in there.
Can't access it, says that there's no file or directory labeled as such
EDIT: ignore this comment
sudo or root to run command.
I'm running the command as root.
Have you tried locating them in your filesystem? Type:
locate rockyou
or
locate darkc0de
If nothing shows, try downloading them, then. Here is rockyou and here is darkc0de.
Did you do a full install or the mini install?
Kitten:
Did it after resolving an error and I got 2 files one that said wordlists the other said wordlists.txt not sure what to do next
Great! Try this now:
aircrack-ng -w <location of your dictionary file> <location of your .cap file>.
.cap usually gets saved into a folder named 'hs' into the folder your terminal was standing in when you ran the command 'wifite'
Kitten:
I'm still a noob so I'm not sure how to dictate the location in a command.
Open it and tell me what's in there. I though I was making it easier for you like that, you can use
ls /usr/share/wordlists
alone, and it will display on terminal what files are in there.
*sigh* You may find useful reading Linux Basics first...
1 2 3 4
Kitten:
Read Linux Basics already.... kali still not working still a noob.
S_R
Is your Wireless Adapter capable of injecting packets?
1- 4 digit pin 1- 3 digit pin and a checksum = 8?
It's clearer if you run Reaver in its verbose form (adding the -vv modifier).
For example, it will try 12345678, then 00005679, being 1234 and 5678 first, and then 0000 and 5679.
When it catches one of the two groups, it will keep repeating it. Let's say the first group is 1111.
It will then try every number starting with 1111, and the search narrows from 10 million to 10 thousand possibilities.
That's when my cracking went from 4% to 90%, because it had one early guess :)
I'm not a 100% sure this is right, but it seemed like that to me.
Here's the tl;dr version:
The PIN Number is hard-coded into the router (It does not change) and is therefore vulnerable to brute force attacks. The PIN is 8 digits long - 7 are chosen at random and the 8th is a checksum of the previous 7 digits. This leaves us with 7 unknown numbers, meaning there are a possible 10^7 (10,000,000) combinations which will take approximately 116 days to break at 1 attempt every second.
The flaw is centered around how the PIN number is authenticated. The PIN is split into two separate blocks of 4 digits each. The first PIN block must be correct before the access point or router will authenticate the second half. This severely reduces the amount of time required as we have now gone from 10^7 possible combinations to 10^4 (10,000) in the first half of the PIN and 10^3 (1,000 - Remembering the last digit is the checksum and does not have to be guessed like the rest) in the second half - Overall this means it will take a maximum of 11,000 combinations to break the PIN and return the password to the network. This reduces the time required to break the PIN to just over 3 hours - Again, assuming that 1 attempt is made every second.
This flaw was highlighted by a Swedish researcher in 2011 and as a result, many hardware vendors have since taken steps to either remove this vulnerability completely (By adding additional layers of security and/or authentication) or significantly increase the time required to break the PIN (Timeouts after x-amount of incorrect entries) to make the vulnerability appear unappealing to the vast majority of people.
So yeah, you were right, basically.
Great answer, glad you did research. ;-) was a loaded question.
https://null-byte.wonderhowto.com/how-to/hack-wpa-wifi-passwords-by-cracking-wps-pin-0132542/
"EDIT: see Cyber's reply, this is totally wrong.
5 months ago - edited 5 months ago Reply
CyberHitchHiker
CYBERHITCHHIKER
3
Greetings, CIUFFY.
An 8 digit pin using 0-9 = 10 to the 8th possible combinations (100,000,000).
However since the 8th digit isn't part of the pin it is just a check sum of the other 7, total = 10 to the 7th (10,000,000).
However WPS presents the pin in two halves for verification. So if one half of 4 digits are correct it will just work on the other half of 4.
Don't forget the second half has one space for a check sum, so really it's just 3 digits in the second half.
The correct total for WPS (10 to the 4th + 10 to the 3rd = 11,000). So the first half has 10,000 possible combinations and the second half has just 1,000."
Dear Kitten,
I waited for 8 mins and suddenly it starts to capture handshake but no PIN and WPA key found yet. Do you know what's the problem?
Regards,
Jacob.
The time limit was 660 seconds. Any way to make it longer?
Line 212 in the script, change it.
"212 self.WPS_TIMEOUT = 660 # Time to wait (in seconds) for successful PIN attempt_"
Try adding the option -wpat <seconds>
This refers to capturing handshake for a dictionary attack. This tutorial is for WPS crack, no handshake needed for this.
Thanks in advance
Hi. My WPS cracking is taking very long. My thoughts are that the router may have locked the WPS. What do you think? Thanks in advance
First of all, I don't know how much you consider "very long", but it usually takes quite long.
WPS may be locked (some routers can be WPS cracked even when they have WPS off, but you'd have to use Reaver), or your packets may be lost (if you're too far from the AP), or you don't have a compatible external adapter that's able to inject packets, or it has some security configured into their WPS that sets a max ammount of tries to avoid brute-forcing it, and Wifite can't get around that.
If that's the case, you should try to crack it with Reaver, and make use of it's advanced options (they're not too many), but that's beyond the scope of this tutorial (I'm assuming no WPS security has been set).
gracias guachoo
Share Your Thoughts