If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.
Kon-Boot is useful for logging into your own computer after a password is forgotten. Alternatively, a malicious user could use the tool to easily log in as adminstrator without knowing the owner's password and steal sensitive info, or cause damage to your computer (or worse). I'm going to show you all, step-by-step, how to use the tool, as well as how protect yourself from it.
How Kon-Boot Works
Kon-Boot allows you to boot the software directly from the disc before the OS starts, hooking itself into the BIOS (basic input-output system) of your computer, and loading itself into RAM. Before the OS starts, it will modify the kernel so entering a password is not necessary, or in Linux's case, making the logon 'kon-usr'.
You Will Need
- A blank CD
- A bit torrent client (I recommened utorrent for Windows users, and transmission-gtk or rtorrent for Linux users)
- ISO burning software (Windows users: imgburn, or freeisoburner for simplicity; Linux users: brasero, or growisofs)
- Your brain!
Step 1 Step 1 Download Hiren's Boot CD
First, head over to a torrent tracker website, such as The Pirate Bay, and search for 'Hiren's Boot cd'. Download version 14.1. Make sure the torrent you get has TONS of seeds and comments stating the torrent is fast and clean.
Hiren's Boot CD is a bootable disc with 100+ freeware tools built-in to it. It's a great tool, and can serve many functions, so I recommend getting Kon-Boot this way. It only requires one CD, and will serve other nefarious purposes (mwuahaha!).
Step 2 Step 2 Burn the ISO File
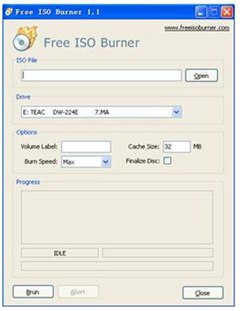 After your torrent is done, burn the .iso file to your blank CD using your image burning software of choice. If you're on Windows 7 or above, you can simply double-click the .iso file to burn it. If you're on an older OS, Free ISO Burner is the easiest choice for Windows. To burn the file, follow these steps:
After your torrent is done, burn the .iso file to your blank CD using your image burning software of choice. If you're on Windows 7 or above, you can simply double-click the .iso file to burn it. If you're on an older OS, Free ISO Burner is the easiest choice for Windows. To burn the file, follow these steps:
- Select the .iso with the 'Open' button.
- Make sure your proper CD/DVD burner is selected.
- Select a low burn speed. The slower you burn a disc, the better the quality. It's also less wear and tear on the laser, and almost never mis-burns this way. I burn every .iso as slow as possible.
- Click the 'Finalize Disc' checkbox.
- Click 'Burn'.
- Sit back, and go get some coffee :D.
Step 3 Step 3 Boot from your Kon-Boot CD
When your .iso is done, you're ready to go. Open your disc tray, pop in the CD and reboot.
When your computer is at the POST (Power On Self-Test), make sure to go into your BIOS and change the boot order. The POST should tell you what button lets you into the system setup/BIOS at the bottom of the screen. Generally, most will have a different button. Some computers have a F12 temporary boot menu, and you can just select the drive to boot from that way.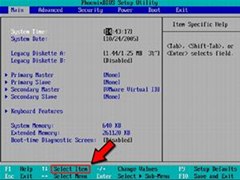
If you reach a screen that looks similar to this, you're good. Highlight 'Boot' or a similar option, and make sure the CD-ROM or DVD-ROM drive is at the top of the boot list, before the IDE/SATA hard drive.
Step 4 Step 4 Start the Kon-Boot Utility
After you've booted from the disc, find the 'Kon-Boot' utility and select it.
After that's done, it should boot automatically if you're using a normal, single OS system. If you're using a dual/multi-boot, just select the one you want to enter without a password :p.
That's pretty much all that there is to it! If you're in Windows, select an administrator account at the login screen and just hit enter. If you're doing this on Linux, make sure to type 'kon-user' as the username, without a password. If that doesn't work, login as 'root' again, without entering a password.
How Do I Protect Myself From Tools Like This?
There are a number of ways to protect your computer from being compromised with tools like Kon-Boot.
- Put a password on your BIOS on boot.
- Encrypt your hard drive with TrueCrypt or another disk encrpytion software.
- Use a secondary network authentication system.
- Disable booting from a disc in the BIOS, and set a password to the BIOS menu.
Putting a password on the BIOS can be done easily from the 'Security' tab, or something similar, once you're in the system setup menu. It's fairly straight forward. Just type in the desired password, which it will request upon boot, or whenever you enter the system setup (whichever you select, hard drive or protected BIOS settings).
Encrypting your hard drive is a bit more secure all around. Even if someone slaved your hard drive up, no one can steal your data (unless you have a REALLY weak password).
If you want to encrypt your whole system, install TrueCrypt. It's a free, open-source, on-the-fly disk encrpytion software. You can even encrypt drives when they are in use!
After that, to encrypt a system partition or entire system drive, select System > Encrypt System Partition/Drive and then follow the instructions in the wizard. To decrypt a system partition/drive, select System > Permanently Decrypt System Partition/Drive.
It's that simple. I hope you've learned how to protect yourself, plus how poorly operating systems can implement their passwords. Computer security goes further than a simple Windows password!
I encourage discussion and feedback in the Null Byte forums!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























6 Comments
Excellent recommendation with the truecrypt bit! Yeah I've heard of some people talking about it, and looked into it but I had no idea you could crypt your whole hard drive with it!
@Sol Gates I'm glad you picked something up from this ^_^
What aspects of tech are you most skilled at?
The first time I installed linux on an old computer years ago I messed up and forgot the password on the first try. Had to redo the whole thing. This would have been useful.
Also, kudos for using the word nefarious, I've always been partial to it, it's such a fun word.
@JD Coverly
Thank you, haha. There are a number of other ways to bypass Linux passwords, you can pass commands to the kernel during boot, or use a live CD to delete the contents of roots /etc/shadow file hash. :D
I wish I knew, I'd have helped you, haha.
Am I right in saying that this only tends to work on x86 CPUs?
I do believe a dual arch. version exists. I think, haha.
Share Your Thoughts