Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "strong" passwords. Creating strong passwords is good, but just like OTW said, even his password-"I<3mtnb1k1ng&h1k1ng"(something like that), is not good enough against botnets and GPU's. But then again, it is a good, strong one. It would take a long while to crack that one, but I guess someone would really want to hack into your PC to try and brute force it. Unless of course you have FDE(Full Disk Encryption) on board and you are a suspect in "Hacking the Gibson."
Step 1: Create Password
First and foremost, Fire up your pentesting distro, kali/parrot/backbox...etc, I'll be using kali. Now create a password hash of any hashing algorithm, but I recommend MD5 as it is the weakest hashing algorithm thus takes a short time to crack - the iterations of passwords per second. Unlike some others like SHA1-512 which takes a pause after a wrong password is input, it will take a bit longer than MD5 to crack. You can use any tool for this. For a noob-friendly you can use CryptoFox, an add-on toolbar for Firefox which is an encryption/decryption tool and it can also encode/decode URL if you ever need it for SQLi. Just download it from here. It's easy to use, just select an algorithm from the drop down menu where it says 'select an option', then select MD5 encrypt. Now write your password and press ENTER. If that doesn't work, click Encode/Decode on the far right. I'll be using mkpasswd preinstalled in Unix.
Open your favourite terminal and type
kali > mkpasswd --help
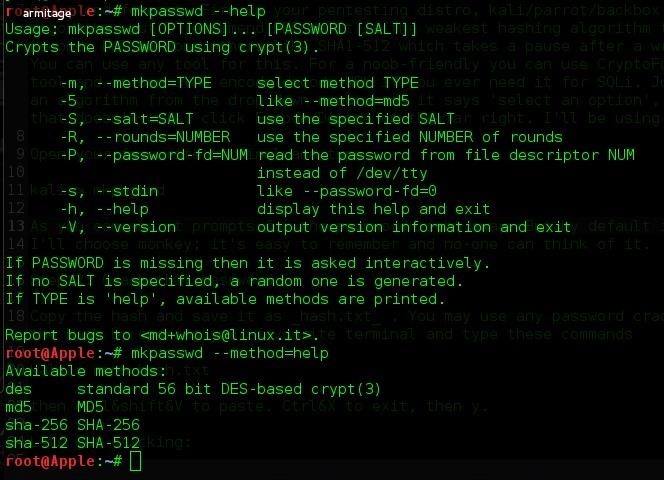
It shows us the help screen for this program and the available algorithms. Now let's create the password by
kali > mkpasswd
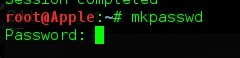
As you can see it prompts for the password right away. But by default it uses DES(Unix), so we have to change it to use MD5. From the help screen it seems easy as we just type
kali > mkpasswd -5
Now enter your password, I'll choose monkey; it's easy to remember and no-one can think of it.
Step 2: Crack Your Password
Copy the hash and save it as hash.txt . You may use any password cracker, I will be using JohnTheRipper. You can paste the hash by highlighting the hash copying it with Crtl+Shift+C and type these commands
kali > nano hash.txt
then ctrl&shift&V to paste. Ctrl&X to exit, then y.
Lets get cracking:
kali > john --wordlist=/usr/share/wordlists/*.* hash.txt
NOTE: with *.* it won't work as the it doesn't take wildcards. Thats just me showing you to use every wordlist in that directory.
If you are able to crack your password, then your password might not be safe because hackers use nearly the same tools = same wordlists. My 'monkey' password was cracked so I have to consider using another password, or do I. So now you understand why its necessary to check if your passwords exists on compromised ones.
Maybe you don't like this method, no problem, you can use something like grep, which is more useful than many would ever imagine. And grep comes pre-installed in linux, not sure if it's on Unix based systems. This is perfect as, if the password doesn't exist in any of the wordlists it won't be printed. But where's the fun in that. Anyway, here are the commands
kali > grep yourpassword /password/list.txt
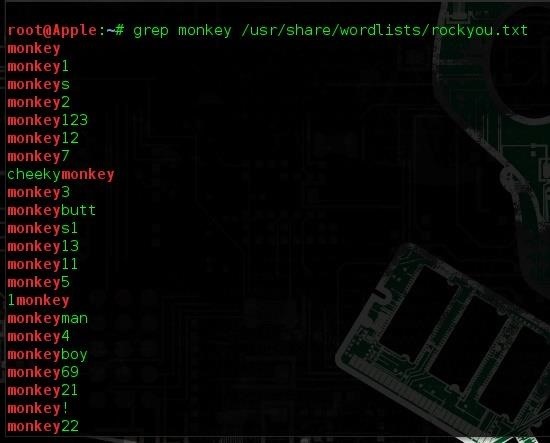
Damn, seems like monkey is pretty famous.
Step 3: What's next
So you now found that your "new" password is in one of the lists. What do you do? Well, the best thing would be to start from step 1, but there's another thing way. Take monkey for example, now you can go back to the basics of creating "strong" passwords and monkey will become M0nk3Y and maybe add a number at the end or in front. This could be your favourite number or something else, and no! it can't be your date of birth.
Conclusion
Well, this is it. Advice perhaps: Take an example from Ollie in Mr. Robot. His password was 123456Seven. Even though the password in the wordlists was 123456seven lower case s, if he would have used my method, Elliot probably would have faced some challenges other than cracking the password in 4 seconds. To actually see the power of wordlists when cracking passwords, even though this isn't a Black Hat Community and what I'm about to share may seem nefarious, cracking one's password was easy(for practice purposes). Remember Tanmay, the guy who created link this wonderful and amazing notebook which is password protected to keep your findings about the "Gibson" safe. I was able to crack
his password in a snap, literally. Keep in mind that still your password won't be 100% uncrackable, but it will get a hacker tired.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























5 Comments
Is there a difference between the many password crackers in Kali?
Also, I have some questions about encryption/hashes:
Another question,
why did you type "mkpassword -5" instead of "mkpassword -MD5"?
if 5 = MD5,
what does SHA and DES equal?
Thanks
I'm not 100% sure about all of these answer so anyone feel free to correct me.
1.Yes, they all have different options and different strong points. Before trying to break a password make sure you pick a cracker that best suited for said encryption/hash.
2.Yes, they all encrypt the password differently, different hashing algorithms will give you different result for the same input.
3.No, a hash is the final output of the encryption and the encryption key is the "secret" key used to encrypt and decrypt the hash.
Hope this helped.
Cheers,
Washu
addition:
I entered this command :
$ john --wordlist=/usr/share/wordlists/rockyou.txt passwd5.txt
And I get this warning (what does this mean?) :
Warning: detected hash type "md5crypt", but the string is also recognized as "aix-smd5"
Use the "--format=aix-smd5" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ MD5 128/128 AVX 4x3)
Will run 2 OpenMP threads
Illegal instruction
Illegal instruction suggests architecture incompatibility. Recompile john and try that again. Also, try to use the option --format=aix-smd5 like it tells you in the output.
Also check this out, it might help.
TRT
Share Your Thoughts