Hi all, Pro Hackers/Crackers,
Let's see how we can use batch for our own Protection instead of exploiting someone with it.
And this tutorial is going to explain the same.
#1 Protection, PC Security:
I will tell you how to add another level of security to your PC, instead of just the log-in screen, which is vulnerable and can be easily exploited.
Copy these two scripts below and save them as Protection.bat and Shutdown.bat respectively.
----------------------------------------------------
@echo off
echo Type the password here :
echo Time is limited (Only 10 seconds left)
echo.
echo If you don't know, switch to Guest (If there is one!)
ping localhost -n 2 > nul
echo OR Dont use the PC.
set /p pass=Password:
if %pass%==qwerty goto :Yes
if not %pass%==qwerty goto :No
:Yes
shutdown /a
exit
:No
cls
color 0a
echo Incorrect Password.
echo Time is running Out !!!
pause
goto :A
:A
cls
color 0c
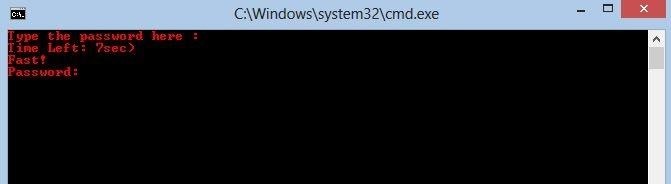
echo Type the password here :
echo Time Left: 4 sec
ping localhost -n 2 > nul
echo Fast!
set /p pass=Password:
if %pass%==qwerty goto :Yes
if not %pass%==qwerty goto :Bye
:Bye
exit
--------------------------------------------------
I hope you are able to understand it easily!
---------------------------------------------------
@echo off
shutdown /s /t 10 /c "Time UP"
exit
---------------------------------------------------
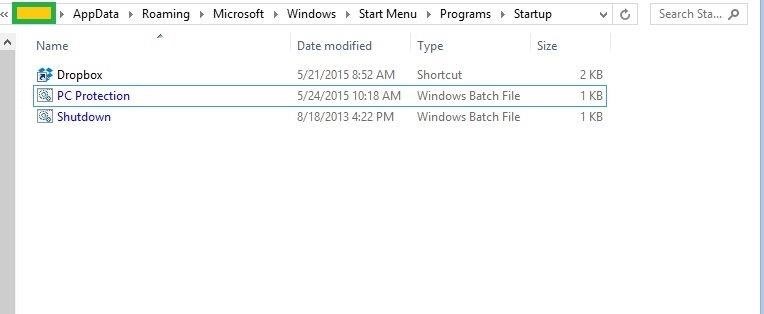
Copy both of these scripts to this folder/location:
C:\Users\%pf%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
DONE!
Whenever you start your PC, these scripts will be executed and you will have you put the correct password to log-in(again) (actually abort shutdown), or the system will shut-down, (Password: qwerty)
You will, only get 10 seconds to put the correct password, if you try to open a new command window, and try to type shutdown -a, it will be too late.
This CAN also be bypassed by logging into safe mode.
This makes a second layer of security.
#2 Locking Private Folders:
Let us, now make a script that locks (actually hides) our private folders.
Password: asdfgh
----------------------------------
@echo off
cls
title Folder Private
if EXIST "Locker" goto UNLOCK
if NOT EXIST Private goto MDLOCKER
:CONFIRM
echo Are you sure you want to lock the folder(Y/N)
set/p "cho=>"
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren Private "Locker"
attrib +h +s "Locker"
echo Folder locked
goto End
:UNLOCK
echo Enter password to unlock folder
set/p "pass=>"
if NOT %pass%==asdfgh goto FAIL
attrib -h -s "Locker"
ren "Locker" Private
echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDLOCKER
md Private
echo Private created successfully
goto End
:End
---------------------------------------
Cause:Makes a folder, which is important to the system, and hides it accordingly (Simple Words)
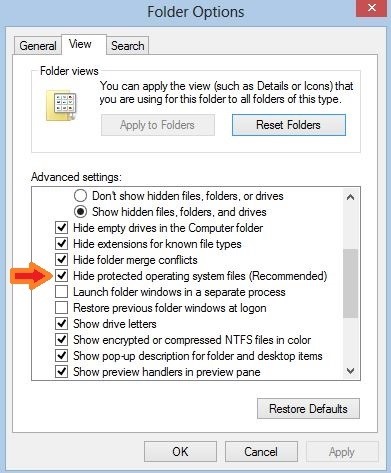
Solution:Go to Control panel, search for folder options, and uncheck the Hide Protected Operating System Files...
Meanings:It is an easy to understand script, but a little twisted.
1)if EXIST "Locker" goto UNLOCK: It means, if there is a folder named Locker then go to (the location) :UNLOCK
2)if NOT EXIST Private goto MDLOCKER: If a folder named Private does not exist then go to MDLOCKER.
3)Important Note: And if the both of the statements above are incorrect then the script moves to the next line i.e. :CONFIRM
4)ren: It means rename Private to Locker or vice-versa.
5)attrib +h +s: Means, to add these attributes (of h=hidden, s=system folder) to a folder.
6)attrib -h -s: Means, to subtract/Remove these attributes from the folder.
Output:

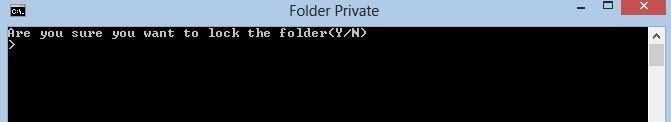

#3 Keeping a Check on Your Ports:
Let's make a script that checks if the port is open/closed and if any connection service has been established on it.
--------------------------
@echo off
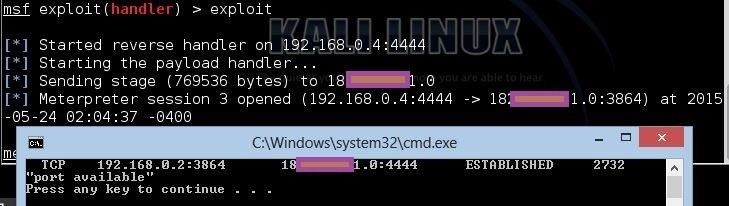
netstat -o -n -a | findstr 4444
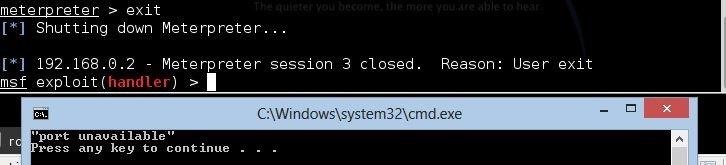
if %ERRORLEVEL% equ 0 (@echo "port available") ELSE (@echo "port unavailable")
pause
---------------------------
Meanings:
1)netstat -o -n -a: Displays all connections and listening ports (-a), Displays addresses and port numbers in numerical form (-n), Displays the owning process ID associated with each connection (-o).
2)| findstr 4444: It filters any output, except the one which contain :4444
3)%ERRORLEVEL%: It is used to tell about the error level, if the port is in use, and is open. (or not) (in this case)
Output:
I am being HACKED!!!
I am not being hacked:
The E.N.D.
This was the final Part about Batch Scripting, however, you have a lot more to learn, keep, the Spirit Up, Elites!
Good-Bye for now,
And remember to keep coming back!
Thank You,
F.3.A.R.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























9 Comments
Absolutely fantastic series! I'm hoping for more, F.E.A.R.
Thank You! Cameron
Wonderful ending! It's good to have an entire tutorial just for security!
Thank You, C|H
I actually use the second layer of login frequently, and it happened to be quite useful, so I thought I could share that with all of you.
thank you man
Welcome!
Hello guy!,Really u have made a positive change in my carrier!, Thanx a bunch!.
Thanks for a great tutorial. I've got a question about Metasploit though. Namely, how did you exploit the machine via the open port?
Ninja243
thank youuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuu
Share Your Thoughts