Welcome back, my fledgling hackers!
Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.
In this tutorial, we will look at several registry entries that will reveal what the attacker was doing on the suspect system. As Windows 7 is still the world's most widely used OS, by far, I will demonstrate these techniques on a Windows 7 machine.
Obviously, if you are investigating one of the UNIX-like systems (OS X, Linux, BSD, Unix, etc.), this will not apply. If you are investigating a pre-Vista Windows system, many of these techniques will not apply. But Windows Vista, Windows 7, and Windows 8 are generally all very similar in their overall build and registry.
Registry Keys
The registry can reveal a cornucopia of information on the attacker. Here we will look at few registry keys that we may want to look at to determine if the system has been compromised and how and who did it. Remember, the registry is made up up 5 "hives."
- HKEY_CLASSES_ROOT: configuration information on the application used to open files
- HKEY_CURRENT_USER: profile of the currently logged-on user
- HKEY_LOCAL_MACHINE: configuration information including hardware and software settings
- HKEY_USERS: contains all the loaded user profiles
- HKEY_CURRENT_CONFIG: hardware profile of the system at startup
If you need a refresher on the Windows registry, check out my Part 5 of Digital Forensics for the Aspiring Hacker, where I introduced forensics using the registry and we found evidence of the wireless access point the hacker was using in their attack.
Also, we can view and edit the registry using "regedit" as well as many of the most popular digital forensic suites, such as Encase, FTK, Oxygen, Paraben, Helix, and others.
The RecentDocs Key
The Windows registry tracks so much information about the user's activities. In most cases, these registry keys are designed to make Windows run more efficiently and smoothly. As a forensic investigator, these keys are like a road map of the activities of the user or attacker.
One of those keys is the "RecentDocs" key. It tracks the most recent documents used or opened on the system by file extension. It can be found at:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
So, for instance, the most recently used Word documents would be found under .doc or the .docx extension depending upon the version of Word they were created in (each key can hold up to the last 10 documents). If we go to the .docx extension, we see the last 10 Word documents listed under this key.
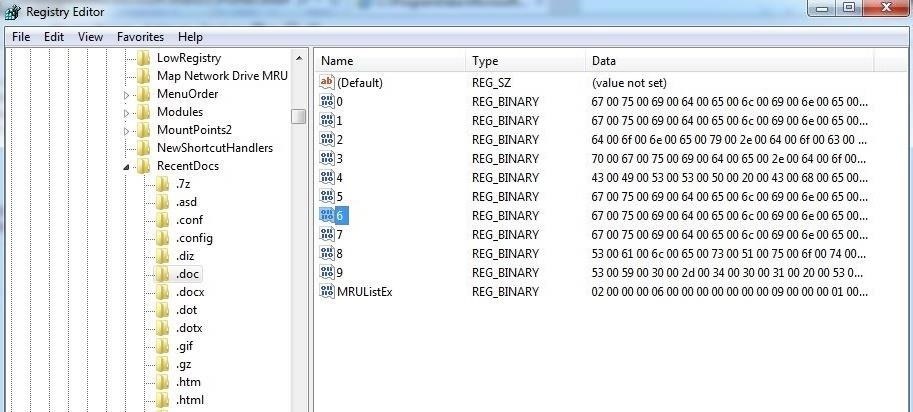
When we click on one of those keys, it reveals information about the document as seen below. We can view the document data in both hex, to the left, and ASCII, to the right. In this case, it show that this document was a Metasploit course outline.
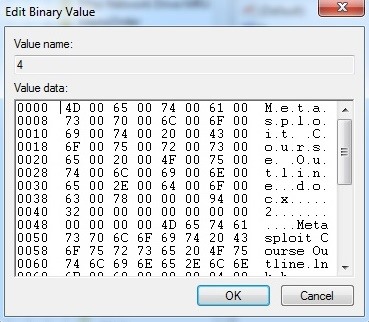
In many cases, an attacker will upload a .tar file, so that is a good place to look for breach evidence. In general, you won't see a .tar file extension on a Windows machine, so the presence of an entry here would be something that needs further investigation. Check the files in the .tar key and see what they might reveal about the attack or attacker.
In civil or policy violation investigations, evidence might be found in the various graphic file extensions such as .jpg, .gif, or .png.
The TypedURLs Key
When the user types a URL in Internet Explorer, this value is stored in the registry at:
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TypedURLs
When we open that key in the registry, it lists the last URLs that the user visited with IE. This could reveal the source of malicious malware that was used in the breach, or in civil or policy violation types of investigations, may reveal what the user was looking for/at.
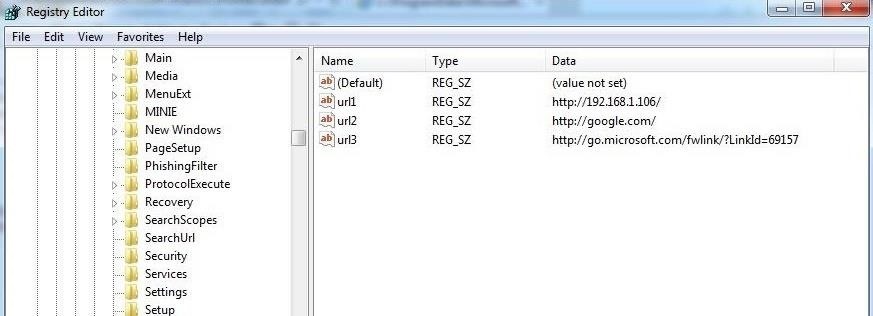
The values will run from urI1 (the most recent) to urI25 (the oldest).
IP Addresses
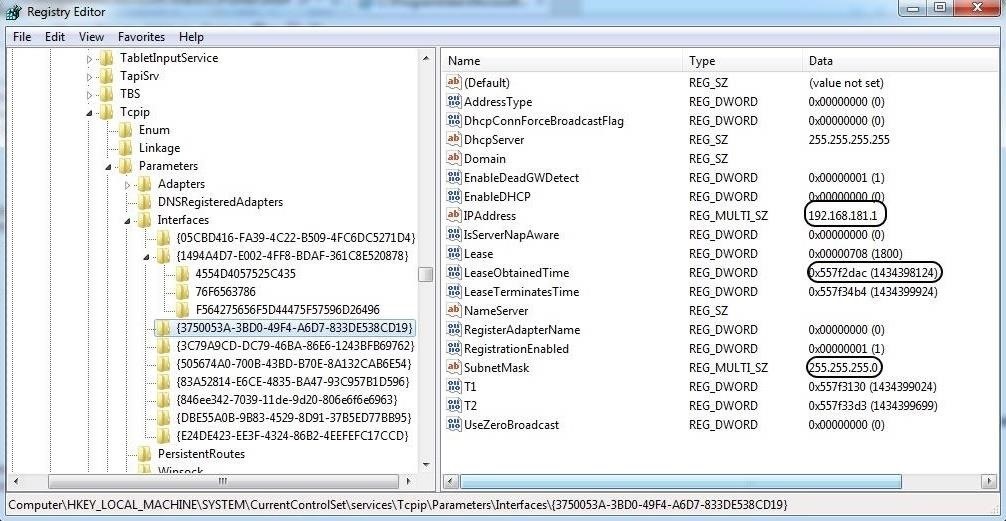
The registry also tracks the IP addresses of the user interfaces. Note that there may be numerous interfaces and this registry key tracks each interface's IP address and related information.
As we can see below, we can find the IP address assigned to the interface, the subnet mask, and the time when the DHCP server leased the IP. In this way, we can tell whether the suspect was using that particular IP at the time of the intrusion or crime.
Start Up Locations in the Registry
As a forensic investigator, we often need to find what applications or services were set to start when the system starts. Malware is often set to start each time the system restarts to keep the attacker connected. This information can be located in the registry in literally tens of locations. We will look at a just a few of the most commonly set keys. As a hacker, these are the keys that you want to set to get your software to run automatically on the system.
Probably the most used location is:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
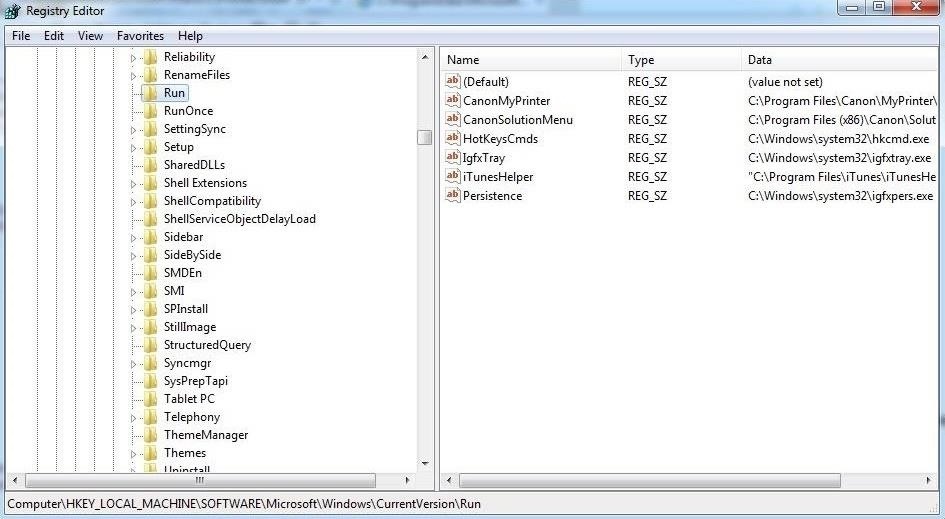
Any software/locations designated in these subkeys will start every time the system starts. Rootkits and other malicious software can often be found here and they will start each time the system starts.
RunOnce Startup
If the hacker just wanted the software to run once at start up, the subkey may be set here.
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
Start Up Services
The key below lists all the services that set to start at system startup. If the key is set to 2, the service starts automatically; if it is set to 3, the service must be started manually; and if the key is set to 4, the service is disabled.
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services
Start Legacy Applications
When legacy 16-bit applications are run, the program listed is run at:
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\WOW
Start When a Particular User Logs On
In the following key, the values are run when the specific user logs in.
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Digital forensics is an excellent complementary skill to hacking, as hackers with knowledge of forensics "cover their tracks," and digital forensic investigators with hacking skills are more likely to track the attacker.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























2 Comments
thanks for helpful topic, keep moving...
Great List, writing the essential bits and bytes down as read.
Understandably written, great article. Thanks, I'd like to know more.
Share Your Thoughts