Welcome back, my novice hackers!
The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.
Every time we send a packet to our intended target, that packet contains our IP address in the IP header. When we make a TCP connection, the target system will log our IP address as it logs all connections. If we set off any security alarms or alerts, our IP address will be logged. All of these events increase the possibility of detection.

In order to hack anonymously with the least chance of detection, we need to use an intermediary machine whose IP address will be left on the target system. This can be done by using proxies.
These systems are designed to accept our traffic and then forward it on to the intended target. Of course, the proxy will likely log our traffic, but an investigator would have to get a subpoena or search warrant to obtain the logs.
If we string multiple proxies in a chain, we make it harder and harder to detect our original IP address. If one of those proxies is outside the jurisdiction of the victim, it makes it very unlikely that any traffic can be attributed to our IP address.
Both Kali and BackTrack have an excellent tool for proxying our traffic called proxychains. In this tutorial, I will show how to use this simple, but powerful tool.
Step 1: Find Proxychains
Let's start by finding proxychains. Type:
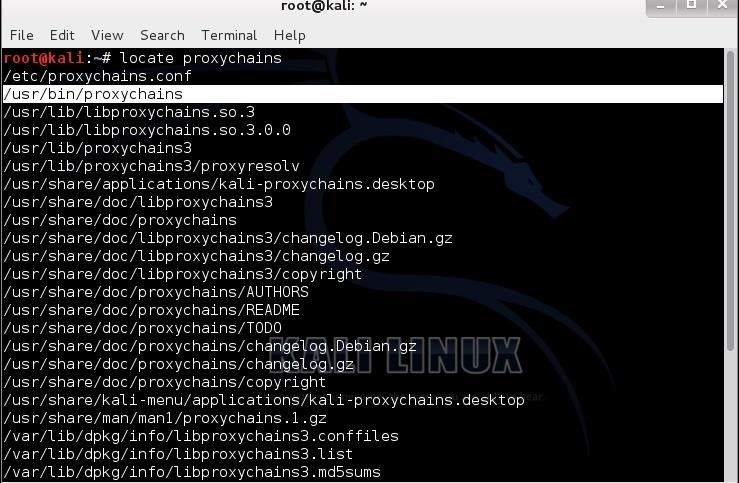
- kali > locate proxychains
As we can see in the screenshot below, proxychains is in the /usr/bin directory. Since /usr/bin is in our PATH variable, we can use it from any directory. This is just as we would want since we use proxychains with other commands, which may NOT likely be in the PATH variable.
Step 2: Proxychains Syntax
The syntax for the proxycahins command is simple and straightforward.
- kali> proxychains <the command you want proxied> <any arguments>
So, if I wanted to use proxychains to scan a site with nmap anonymously, I could type:
- kali> proxychains nmap -sS <IP address>
Step 3: Set Up the Config File
Like nearly every application in Linux/Unix, configuration is managed by a simple text file called the config file. In the case of proxychains, this file is /etc/proxychains.conf. We can open it in leafpad or any other text editor (vi, emacs, gedit, kwrite, etc.), by typing:
- kali > leafpad /etc/proxychains.conf
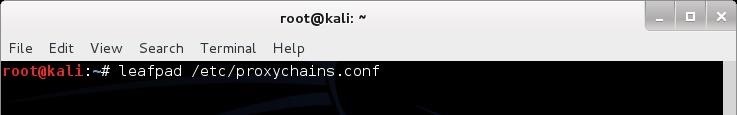
When we do so, we will see a file like that displayed below. If we scroll down this file a bit, we will see a section that I have highlighted labeled "add proxy list here...".
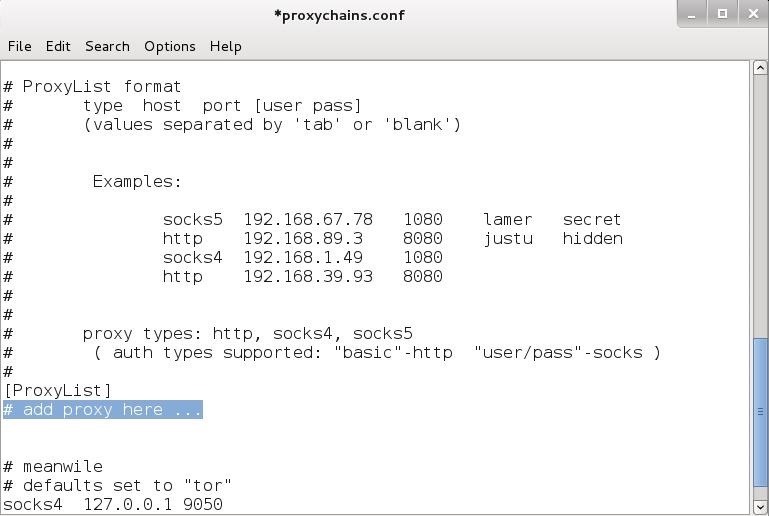
To get proxychains to use intermediary proxies, we simply need to add the IP addresses of the proxies we want to use here. It's important to note that proxychains defaults to use Tor.
Notice the last line in the screenshot above. It directs proxychains to send the traffic first through our host at 127.0.0.1 on port 9050 (the default Tor configuration). If you are using Tor, leaves this as it is. If you are not using Tor, you will need to comment out this line.
As much as I like Tor, it is very slow and we now know that the NSA has broken Tor, so I am much less likely to depend upon it for anonymity.
Step 4: Let's Test It
Now that we have put a proxy between us and any traffic we send, let's test it out. In this case, I am simply going to do an nmap scan to wonderhowto.com anonymously by sending the scan through a proxy. The command would be as follows:
- kali > proxychains nmap -sS 8.26.65.101
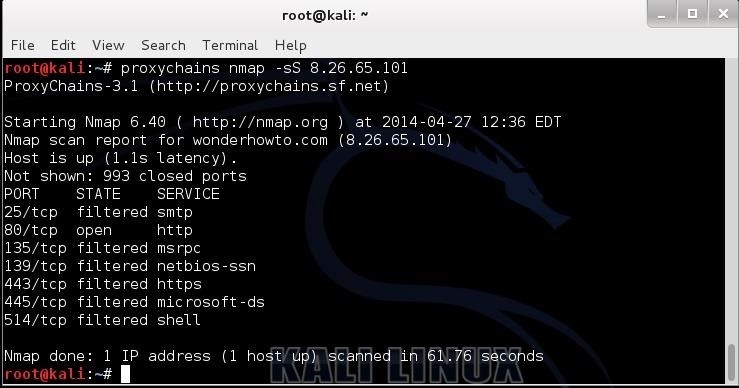
As you can see in the screenshot above, I have successfully scanned wonderhowto.com through my chosen proxy and returned the results back to me. In this way, it appears that my proxy scanned wonderhowto.com and not my IP address.
Some More Interesting Options
Now that we have proxychains working, let's look at some options that we can configure through the proxychains.conf. As we now have it set up, we are simply using a single proxy. We can put in numerous proxies and use all of them, we can use a limited number from the list, or we can have proxychains change the order randomly. Let's try all of those options.
Step 5: Add More Proxies
First, let's add some more proxies to our list. Open /etc/proxychains.config and add more proxy IPs like I've done below.
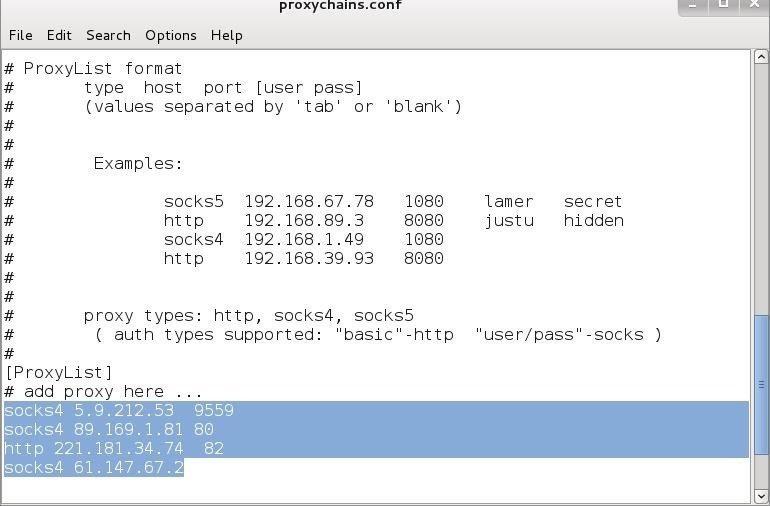
Step 6: Proxychaining
Now that we have multiple IPs in our proxychain.conf we can set up dynamic chaining. Dynamic chaining will enable us to run our traffic through every proxy on our list, and if one of the proxies is down or not responding, it will automatically go to the next proxy in the list without throwing an error.
To do so, let's first open the proxychains configuration file again.
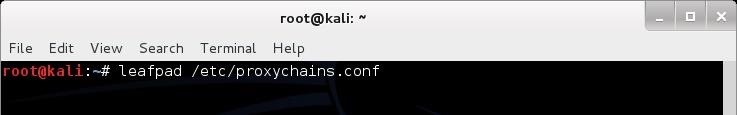
With this file open, uncomment out the "dynamic_chains" line. This will enable dynamic chaining of our proxies allowing for greater anonymity and trouble-free hacking.
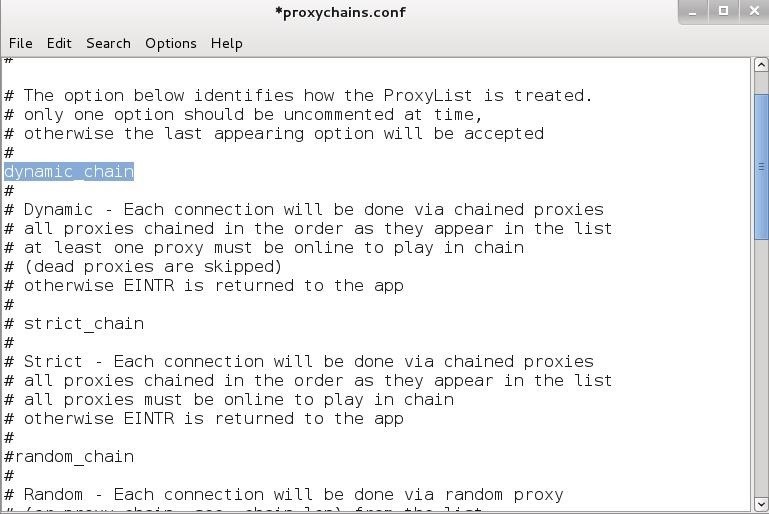
Step 7: Random Chaining
Finally, we can also use "random chaining". With this option, proxychains will randomly choose IP addresses from our list and use them for creating our proxychain. This means that each time we use proxychains, the chain of proxy will look different to the target, making it harder to track our traffic from its source.
To do so, open the /etc/proxychains.conf file and comment out "dynamic chains" and uncomment "random chain". Since we can only use one of these options at a time, make certain that you comment out the other options in this section before using proxychains.
In addition; you may want to uncomment the line with "chain_len". This will determine how many of the IP addresses in your chain will be used in creating your random proxy chain.
Now that you know how to use proxychains, you can do your hacking with relative anonymity. I say relative, because there is no surefire way to remain anonymous with the NSA spying on all our activity. All we can do is make detection MUCH harder, and proxychains can help do this for us.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























132 Comments
Is it better (safer) to run proxy chains from another wifi, like lets say starbucks and such places? Or is it safe to run proxy Chains from your own network? How are you detected behind a proxy if you are using multiple proxies? Does your IP ever leak, and if so how?
Thank you,
-Macro
Very noob question I recommend you looking at basic concepts like what's an ip ?, what's a dns?, what is a physical and local up? Before even messing up with some kind of testing tool or IOS you don't know how to use.
Macro:
It is ALWAYS safer to hack from an IP that can't be traced back to you.
First, each proxy will have the previous IP, so that if someone were trying to trace you they could go from proxy to proxy and trace you from the log files. That's why it is smart to use multiple proxies in multiple jurisdictions. Hopefully, at least one will be in a different jurisdiction that will not give up its logs.
OTW
It is difficult for the U.S. to get information from both Sweden and Russia, both of those countries should be in your chain.
Jon:
You are correct. U.S. law enforcement has no jurisdiction in the Russian Federation, so using a proxy in that country makes sense.
OTW
If you use a compromised computer as a proxy, how would you delete the logs? And is this even possible, because if so would that not be better than using a VPN or Proxy? Also, since your ISP can see the connections, should you first run a VPN then use Proxy chains?
Thank you for your time,
-Macro
Macro:
As for deleting logs on a compromised computer, it will depend upon what access you have. If you have the meterpreter, there is a script called clearev that clears the event log on Windows computers. If it is a Linux machine and you have root access, you can simply delete the log files as they are simple text files.
OTW
OK, thank you very much, I will more into that! :D
OTW:
isn't using proxychain dynamically somwhat similar to Tor? From what i understand, Bob's packets are sent in clear (i don't think that proxying implies VPN right?) with Bob's ip port and so on to the first proxy, then the second and so on. So if someone is between you and the first proxy you are still vulnerable right? In my case, their are no proxy in my country, so my packets will go through my ISP first right??
Soul:
Your packets will always go through your ISP first unless you are using ToR. Yes, if someone is between you and the first proxy and sniffing, they can see your IP and payload.
OTW
Sorry for asking again,
but why would my packets always go through my ISP if i am comunicating with someone on the same subnet? i mean, wouldn't the switches, routers, and bridges between sender and receiver automatically route the packets without the need to go through the ISP?
Or is my understanding of the infrastructure linking me to my ISP wrong.
soul:
He is talking in a WAN you are talking about LAN. In a lan you just need to spoof your mac and ip.
Soul:
You are correct. I should have said that whenever you go out to a public IP, the packet must go through the ISP. Thanks for correcting me.
OTW
hello OTW...so lets immagine i got my nice yagi antenna with this very very high gain...i've broken a couple of wifi passwords all like 5 kilometers from me...so how possibly can something done through any of that network be linked to me? i have my ideas but just immagine the scenario, give me all you got about a situation of the sort...
King:
This is exactly what should be done in conjunction with proxychains. It will be very difficult to identify you. In my work with law enforcement, they always focus on a radius of a few blocks in the cases of stolen wifi access and they are always correct.
Of course, good old detective work might find you. So many hackers are unable to keep from bragging about their exploits and this eventually leads to their downfall.
OTW
hahahahaha the bragging though ;) lol
but what do you exactly mean by "good old detective work" ?
King:
What I mean is simply asking questions. One of the cardinal rules of good old detective work is "follow the money". In addition, a good detective will start knocking on doors and making phone calls. They trust that someone will know something of what you did. If they suspect you, you they will subpoena your ISP and get a search warrant for your computer equipment. With that much info, they can nail you.
OTW
What does law enforcement think of you helping people online to be able to hack?
Do some people think you're hired by the authorities to obtain a list of all those who might potentially pose a threat and recruit those with potential? ;)
ok i got the point...but going by my style is very very hard work...which means one must also be as silent as possbile...thank you Master...your work on this site is very much appreciated!!!
Keep it up!
Thanks King! Its always good to hear that one's work is appreciated.
Check out the new OS tails , been playing with it seems to run great, tor runs fast
(Sorry this was suppose to be under Thelionking post)
Hello,
Have you not read news about TOR networks in the last 12 mos? I would avoid TOR like a plague if I was you.
Proxies as well unless I made the proxies on remote boxes.
Love Your work @OTW Keep it up..
Why Proxies and what are remote boxes?
Thank you,
Macro
Proxies: You don't know who made and maintains the proxy you are about to connect to. They could be reading everything you are doing during that connection or worse a lot worse.
Also I suspect they are being used (proxies) as a type of honeypot network and being monitored as people flee from TOR. Pretty sure it sends some sort of flag as you hit certain sites through a public (found) proxy chain.
Remote Boxes: i.e. Remote Systems either under Physical control and/or Remote control. (Boxes is just slang for a computer of some sort.) I would even call a Pi a box. 8)
So that being said, obtaining your own "computers" would be best, whether or not they are in your possesion? That seems to be what I'm finding.
what do you have to say about this OTW? I don't really understand the honeypot part, as an American investigation would require a subpoena if your proxy is in one of the places listed above. Is there something I'm missing, or is this all paranoia?
-Macro
Macro:
Obtaining your own proxy would be best. Yes, a subpoena would be necessary to obtain log files and if the machine is outside the local jurisdiction that will not be able to serve it and force compliance.
A honeypot is a decoy computer to entrap hackers.
OTW
Marco
Thanks Brook. I've been checking it out. Not sure I trust it yet.
Have you come to any further conclusions about Tails? I'm curious about why you wouldn't trust it..
looking forward to your feed back :-)
Hello Master OTW...
this is an interesting one...
i just went to visit a friend of mine and i was browsing using his wifi...to make the signal stronger sometimes i use this external wifi tplink wireless adapter ...
i noticed that when i attached the wireless adapter...i got limited access..and the problem was that the network could not assign my pc an ip address...but without the external wireless adapter i could connect alright..only with low signal..
my conclusion was that...so just by changing the NIC...my ip was changing and to the network i was always a different person?
can you confirm that? thanks in advance
What is an NIC?
A network interface controller (NIC, also known as a network interface card, network adapter, LAN adapter, and by similar terms) is a computer hardware component that connects a computer to a computer network.
King:
Yes, changing your NIC will change your IP internally , but not your external IP.
OTW
i see..thanks
can someone give a list of good proxies situated in different part of the world i can use in a chain? thanks
King,
I would also like to add that it is NOT a good idea to use free proxy services as they are not to be trusted. Best to use a pay service, which offers full anonymity and offers more countries and options. There are tons of very affordable proxy services out there now days.
Lion:
Simply google proxies. There are hundreds of sites with lists of proxies by country.
OTW
thanks OTW
hi.. i've a problem.. when i modified and uncomment the "dynamic" option or when i just insert one proxy server, i tried to do a nmap scan to another pc in my lan and i start to sniff with wireshark (in the target pc)..
the problem is that my lan address is visible in wireshark!
i've disabled the 127.0.0.1 line because i don't use tor proxy and i've enabled dynamic line and i've insert two public proxy..
where is the error?? thanks..
Soul:
Not all proxies are created equal. You need use one with a high level of anonymity and keep alive. Try some other proxies. Often some of the best are not free.
OTW
ok thanks OTW i'll try...
also make sure to say proxychains before doing your scan
like : proxychains nmap ipaddress
Jon
Yes i do it...
I'll try tonight after work and i will tel you..
Thanks at all !
I figured you did, but sometimes we brain fart, I know I have done it
spent hours trying to figure out my user error, that I knew how to use lol
Not working yet.. Grrrrr!!!
The proxy servers i've used seems to be all Alive..
I'll try tonight yet after work..
Hi guys it seems that proxychains willl not work for me... -.-
i've used lot of proxy server,and seems it work, but if i type this in my terminal:
proxychains firefox www.google.com
i receive this message
|DNS-response|: http://www.google.com is not exist
i've already changed default DNS server in
" /usr/lib/proxychains3/proxyresolv ",
but the message in my terminal it's the same..
Do somebody have any solution to this prob???
Thanks to all..
Dark, are you using kali??
If so I bet your trying to use it as a user. If you switch to root and if everything is setup correctly it will work.
Proxychains not working correctly for a user (not root) is an issue I have been working on myself.
The problem is that proxychains.conf permissions are not set correctly so when you try to use it you will get an access denied in your terminal
Solution is to log in as root, set it to read write all users.
Then it will work as a user
ps dont forget to use sudo proxychains, or again it wont work as a user
Jon
Yes i'm using kali..
I'll try to autenticate like root..
Thanks!
This can be the same solution for My msf console??
It give me an error that it can't reach the server at the port xxxx..
What do you think?
if your doing it as a user then yes, but if you fix the config then it will work
Jon
Ok Thanks a Lot!
I'll try later.
Hi guys, hi Jon,
it seems that nothing work for me!
i've changed the permission with chmode and i've done 777
i've used "sudo"
i'm logged root
but the result is the same..
proxychains give a DNS error
and msfconsole give this error:
Failed to connect to the database: could not connect to server: Connection refused
Is the server running on host "localhost" (::1) and accepting
TCP/IP connections on port 5432?
could not connect to server: Connection refused
Is the server running on host "localhost" (127.0.0.1) and accepting
TCP/IP connections on port 5432?
i have a question,
when i was installing kali, i wasn't able to install "Mirror" because i had not internet connection..
This "mirror" could be responsible about this error??
Thanks
Dark Soul:
The metasploit error is usually related to your not installing or updating metasploit while root.
The mirror issue has nothing to do with this problem.
OTW
I followed this tutorial a couple of days ago to add some new proxies which was successful, just checked it today and my entire proxychains.conf file empty any reasons as to why this may be happening?
maybe you want to open your proxychain.conf with leafpad in terminal and you are not in it's subdirectory?
it's happened myself..
Solved the issue, thanks for the input.
dartksoul:
Do an ifconfig make sure that lo is listed and check the address, it should be 127.0.01
sounds like it not active
Jon
Yes lo is listed..
And its local addres is the standard 127.0.0.1
Idk man, I am sure its not your dns. must be the proxy's. Try this reboot your system set proxychains for tor, in fact put in a clean install of proxychains. Kick in Tor, then try it from root. If that doesn't work, then IDK. If it does work, then its gotta be your proxy's
jon
ok i solved the msfconsole problem! yeah :D
and the proxychains seem work now with the only problem of this damn DNS server.. when i follow the terminal screen i see that most of proxy server are unreachable but sometimes some server works and also DNS works but the page isn't loaded..
i'll try what you said jon!
OTW
Thanks a lot!
in fact i've solved the msfconsole problem by this command line
service postgresql start
service metasploit start
I hope that this can be useful for anyone that have the same problem.
Thansk again OTW.
Hey, this is a really helpful post, and I have been loving these tutorials! I am having a few problems with proxychains though.
I am also having the DNS is not exist error. I wondered if this might be because google uses https and I only have http in my chain?
Also, I sometimes get a few succesfully chaining, but then one times out, and I don't understand why it does not just complete the request with the few that succeeded? Although it is the DNS error I get again, that is maybe a separate issue?
Finally, I don't know if I maybe just need to do some serious research on networks in general, but could anyone point me to any good articles regarding the following/help me out please?!
Say you wanted to add a router that you have access to externally (your own for example) to a list of proxies, is it not good enough to have access to it with a username and password? Does it need to be set up specifically to enable its use as a proxy, or could you just add the wan ip at port 80 with the user and pass to proxychains and it would work?
Or is there something specific you would need to set up? I have been having a look at port forwarding and pptp, but these seem to need to go through a computer on that network?
Just because, as mentioned above, it seems that finding your own proxies is safer than just using ones from a list (also, I guess these get flooded with requests.) I was thinking Shodan could help, but again, I am a bit to clueless. Would you search proxy server on there, and add the IP given on port 80?
Sorry if that is a load of questions and potentially pretty basic, but I have been going round in circles, and I'm not sure which part I may be getting wrong! Thanks for the great articles too, they really are awesome!
Okay, after a whole two days of beating my head against a wall, I found a few things that might help other people too!
Firstly, I commented out proxydns as apparantly that doesn't work anymore? So that gets rid of the dns is not exist problem.
Secondly, the order of your proxy list seems to be super important (I read somewhere that http should be last?). So I started with all my socks, then the https, then http. That seemed to work for me and suddenly it is chaining away!
I am still stuck on a final hurdle though. I found something that said to test it using curl and a website address. But I finally realised that when it keeps chaining and then timing out (I asked the question previously of why it didn't just use the ones that worked.) But it is the actual website I am curling that is timing out. I have tried a few different website, and they all timeout. Does anyone have any advice on that please?
Hope that might save other people some time!
I know it's been a while, but I just recently came across this tutorial and saw you were having the same issues I was with Curl. For whatever reason http and socks4 proxies would always timeout or be denied; however, since I've been using socks5 proxies I haven't had any issues. Hope this helps.
hello otw,i have followed the guide and made changws to .conf file and added the proxies as in the image ....but when i try to nmap a host prefixing proxychains i get error that all those proxies getting timed out ....???please reply
Greetings, the time out may be because:
Perhaps you are using socks5 instead of socks4.
Perhaps you are using strict rules instead of dynamic.
Perhaps is no route back?
The proxies you are using suck?
The second question: service --status-all #Do we have - ? + for the services needed to run msf?
and also why cant i update my metasploit on kali..?msfupdate isnt working...
Sorry to inform you that you didn't quite evade detection. Let me explain. Your scan didn't go throw Tor because you used stealth scan .
I also didn't find a solution. In order to channel your scan through Tor , you must use TCP connect scan.
Tor is horribly slow nigh impossible with nmap and using -sT is detected/blocked very easy. Using SYN (-sS) won't use Tor.
Would just going to a random wifi store not provide enough anonymity for nmaps?
If you read carefully, I wasn't using Tor. I no longer trust ToR.
You have mentioned that you do not trust TOR anymore, so you believe that proxy chains are better??
It depends upon who you are trying to remain anonymous from. ToR can't be trusted to remain anonymous from the NSA, but is effective to remain anonymous from nearly everyone else. The combination of a good proxy and ToR is best.
Hi all,
is there any way to make website hits to selected URL with multiple proxies from my proxylist? I need to open/hit specific sites for marketing (it can't be pinged only; sites e.g. http://www.ad-link.sk/p.php?l=139373297932323&r=111421145364456) How to make proxychains work with these long URLs?
Greetings, sounds like you need to learn some Python.
Do you have tips for me how to do some script for this?
Hey OTW I'm new here but I'm just wondering, is Tor a good alternative to this? Or rather, is Tor similar to this, in the sense that Tor IP's can't be traced?
Just wondering...
Is it possible to connect to a paid VPN you trust (to avoid your ISP from logging), and then from that point (the VPN IP addresse) conduct a proxychain for extra anonymity?
Great topic.
Mind blown...
OTW,
Having the same problem with DNS it is either denied, timed out , or it says the specific sight does not exist. Interestingly enough iceweasel and proxychains works fine if im just connecting through TOR, but once i add a proxy in there it all falls apart and i get the DNS error. Nmap is not working at all through proxychains. I tried scanning wonderhowto.com using a TCP scan as sudo proxychains nmap -sT <ip> through TOR and i got one OK request and the rest were denied. As soon as i threw a proxy into the nmap scan it was nothing but timeouts. I tried numerous things including commenting out the proxydns , adding a different DNS address to proxyresolve using http after socks , giving chmod 777 permissions to proxychains.conf, running as root, etc. Still nothing. I am currently dual booting Kali of my laptop, when I used Kali in VMware in my old desktop i had no issues however this was like 6 months ago. I need some help, any suggestion on what else i could trywould be appreciated?
Thanks
13ee13uckeroo
I was wondering can i use someones computer as a proxy?
I need a specific location IP and i want to be personal and not public like socks and stuff.
If it is possible can you tell me the best way to establish that kind of connection.
Thanks...
Hi, Im new here :) im a bit confused here..Is it ok if uncomment both DynamicChains and random or just choose one of them?
Jason:
Welcome to Null Byte1
You can leave both uncommented, but the last option left uncommented will be the one the script uses.
OTW
Hi,
I know this is a fairly old post, but I was wondering if someone could give me a list of good proxy providers that I could use. I did some digging but I wanted an expert opinion. You can just give me the names and I'll look them up. Not sure if it is okay to post this type of things.
Thanks,
Matthew
Hi, I know this is an old post but I need clarification please!!!
The second question seems obvious to me, but I just need someone to confirm my thoughts for me...
Thanks
Phoenix
Do I need to use the proxychain command to run any command I want to go through the proxy chain? Or can I set my computer to use that proxy chain, so that any command, browser, or other internet-accessing thing I do will automatically go to the proxy chains?
Also,
If I wanted my browser, iceweasel, to proxychain, would I launch it from the command window with the proxy chain command, or would that not work for it?
{Deleted}
Yes, that works.
Okay, thankyou. How about my first question? (I had two there)
As for you first question, I don't believe there is a way.
Okay. (I was thinking you might be able to launch your network adapter driver with the proxychain command, to make all your internet go through the proxy chain, but that probably wouldn't work.)
Hey Cracked Ninja,
Actually that is normal done by using iptables. Here a stackoverflow link to it stackoverflow.com/questions/10727443/how-to-use-iptables-in-linux-to-forward-http-and-https-traffic-to-a-transparent
Worth mentioning is also the start-anonmode tool developed for parrot sec. I am pretty sure you can adapt that.
Im actually a little bit confussed about proxies, is a proxy chain when you connect to a proxy server lets say in china, who connects to another one in england and then goes to the server you wanna connect to (if you no have set up any more proxies)
or is it
one proxy server you connnect to and then connects to the server and the proces goes back. and then when you connect to the server again, you are using another route, and you continue doing that? (using another route all the time, to connect to the server)
And when you are connecting to these proxy servers are you encrypted then?
OTW.
Those sock4 proxies you uses.
Can we use them?
And where can I use any other sock4 or http proxies?
Thanks in Advance :)
You can use any proxy you want. There is no guarantee they are safe. Try googling for proxies that are available.
solved
are you using a http proxy?
Ok, sorry for bothering again, I didn't really solve the problem completely, I just thought I did, I used the -sT argument and it showed me the chains so I thought it works, but I didn't reallise it shows all scanned ports as closed, even those which are opened(normal nmap shows it so). Since I "removed" my comment above I'll explain it again shortly. Everything seems to be working as in the example, but when I tried running wireshark on a "targeted" machine it showed me packets going directly from the "attackers" IP, not from the proxy, it didn't show any packets going from the proxy server. Those proxies work on 100%, when I tried "proxychains iceweasel" and went to whatsmyip.com it showed me IP of the proxy server. I think the problem might be that I'm connected through 2 routers - nevermind, even when I tried it directly it didn't help.
Yes I tried using http, It didn't work.
Try using a socks4 or socks5 proxy. The HTTP proxies only work with HTTP.
But it works just with the -st argument and shows filtered as closed
I'm sorry for bothering, I just tried socks5 and it works through it, I'm really sorry I thought I tried all of them
im getting this error while running proxychains iceweasel (process:26241): GLib-CRITICAL *: gslicesetconfig: assertion 'syspagesize == 0' failed
Can someone help me?
Thansk
Hey all,
I am running hydra and using a dictionary attack on my own VPS. I am following the above using proxy chains with 3 or 4 proxies.
However, whenever I log into the VPS to look at the auth logs after its successful, I notice some how it is tracing back to my own home IP. It says the IP of the proxy but then says "reverse mapping checking getaddrinfo for MYHOMEIP"
I dont really understand how because the proxy chain seems to be working fine.
Can anyone help with why this happens? Do i just need a lot more proxies?
More proxies probably won't help. You need good proxies. Try using another proxy.
Thanks for the reply. Is it advisable to also run this type of attack using a VPN? Or are Proxychains enough (assuming I can get it to work).
I have read some guides on setting up VPNbook on kali. is this advisable?
Hi
What's the best way to check if the proxychain is working? there's no confirmation in the shell as far as I can tell.
I do a sniff in Wireshark while executing the Nmap proxychains command but can't see any of the proxy IPs in there.
Some proxy will still forward information about your real IP, so it's possible that the VPS knows it. I'd suggest you manually check by inspecting headers sent or, if you're lazy, just go here. If you find your ip somewhere, the proxy is leaking your real identity.
Also, did you use the HYDRA_PROXY correctly ? Post your settings, problem might be there.
I stopped using proxychains hydra and changed to HYDRAPROXY however its still the same, my server says: "reverse mapping checking getaddrinfo for MYIP"
This is what I am running:
hydra -s 22 -v -V -l root -P /usr/share/wordlists/testlist.txt -t 4 -w 60 SERVERSIP ssh HYDRAPROXY=socks5://212.195.0.225:41724
Sorry for the slow reply. Thanks for the info I will try some other proxies.
In regards to settings, im a bit confused as to what you mean? I run the following command:
proxychains hydra -l root -P /usr/share/wordlists/fasttrack.txt -t 6 ssh://IPHERE:PORTHERE
KINGLEO :
If you have tor, try this command :
/etc/init.d/tor start
and then start running hydra :)
Also, why are we forced to log in with facebook? Why does Nullbyte want the identity of everyone getting into hacking? I hope this is not the community equivalent of an NSA honeypot ;)
Greetings.
I'm using vb till i can afford a nice box for my kali. Since i'm using the internet connection of my hoster OP is this still viable to avoid detenction? Or is it saffer to set of wifi on my host OP and get a connection trough my kali?
Thank you.
hello OTW,
i have one question
uncomment the line with "chainlen" will make it connect randomly from ip to the other ip to the website ? like from ip 11.11.11.11 to 22.22.22.22 to the website then from 22.22.22.22 to 11.11.11.11 to the website ?
Thank You.
Entering proxychains dig +short myip.opendns.com @resolver1.opendns.com into my terminal it returns my public ip and not the proxy ip. probably making noob mistake somewhere but after searching for a full day cant find a fix for this
i have a question.Now i know that proxy is used only for browsing an vpn hides everything.But at some games it has a connection option for proxy. so if i connect there my ip will be hidden in that game right?
MAYBE I'M LATE :( What abut using proxy chains in nested VM's? Is it secure?
-Energy
Hello this is a great site. I'm hoping someone can help me with proxychains. I can not seem to get it to work with iceweasel.
I configured the poxychains.conf file as explained in the tutorials.
Using Dynamic, then Random, then just a static known working proxy server.
Started iceweasel with the following command
proxychains iceweasel
Iceweasel starts but when I check my ip address in google its my real ip address/
What am I doing wrong?
If you enable dynamic and random proxies, does it automatically enable and change proxies or do you still have to type in proxychains netdiscover -i wlan0, proxychains nmap -Ss 192.168.0.1, proxychains firefox, etc. or can you omit proxychains?
ASK how to fix firefox unable to connect to everything after i run "proxychains firefox"
when i type in leafpad /etc/proxychains.conf it pulls upa blank box . do i have to type all that manually orr........
never mind i put ect not etc
am a bit confused here, when i add multiple proxy ips will i be able to remain anonymous even when i am using metasploit to run some exploits or not ?
If you are tell us that "I say relative, because there is no surefire way to remain anonymous with the NSA spying on all our activity" than how Anonymous hacker are not Traced............
Hello everyone,
is there a way to integrate this proxychains into other Kali 2 tools like SqlMap? I mean, let's say I would like SQlmap to use different proxy whenever it performs the next query injection attempt (in order to be abile avoid IDS detection), is there a way to do that? Maybe altering SQLMap's files? or maybe a generic solution for all such tools?
Regards
Thanks for the amazing tutorial.
How can I set LHOST and LPORT when using proxychains along with metasploit?
i have a doubt that adding proxies in proxylist when to use sock4 and when to use http....
and u r doing gr8
Hi, is it possible to use proxychain this way
my pc - > proxy -> tor -> proxy -> destination
Which means my entry is in a proxy, then from the proxy to tor entry node, then from tor exit node to another proxy before reaching the destination? If yes, then how?
Share Your Thoughts