Welcome back, my fledgling hackers!
One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.
I've written a couple articles on performing active and passive recon already, but this article is dedicated to doing reconnaissance without being detected or blocked.

Our reconnaissance tool of choice is nmap, which sends crafted packets at the target system, and then based upon how it responds, determines what ports and services are open and what operating system is running. Unfortunately, these types of scans can easily be detected, logged, and even blocked by a good firewall and/or NIDS (network intrusion detection system).
In this article, I will show you a couple of techniques that help you do reconnaissance stealthily without being detected or blocked.
Step 1: Scan the Network with TCP Connect
Let's start by scanning the network with the TCP connect protocol. This is our most reliable scan as it opens up a connection with the target system. Note that we are using the -P0 switch here. This suppresses the ping that nmap sends out by default and is blocked by most firewalls.
- nmap -sT -P0 192.168.1.115
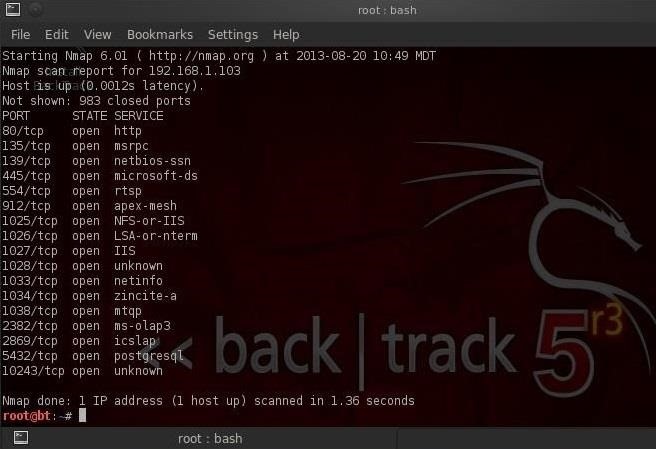
As you can see, it returns us a reliable report on the open TCP ports.
The problem with this type of scan is that it opens up a connection with the TCP three-way handshake to the target system and therefore it's logged in the Windows Security events. If eventually we hack this system, it wouldn't be hard for the system admin to determine who did it, as he would have our IP address in his logs from this scan.
Step 2: Scan with SYN Flag
One of the strengths and weaknesses of the TCP scan is that it opens a connection, making it very reliable and at the same time, very un-stealthy. As an alternative, we can use a TCP protocol with just the SYN flag set that never completes the three-way handshake of a TCP connection and therefore is never logged. We can do this with:
- nmap -sS -P0 192.168.1.115
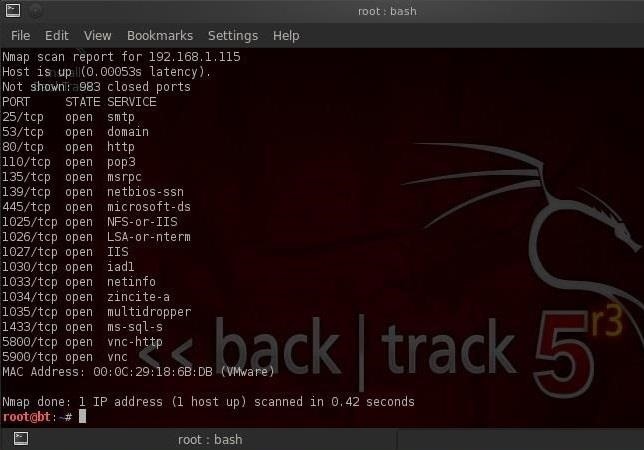
As you can see, it also provides us with us list of open ports and is nearly as reliable as the TCP connect scan, but without leaving a trail in the log files. Notice that this scan took .42 seconds according to nmap.
Step 3: Alternate Scans
Depending upon the system, we might also try a UDP scan (using the UDP protocol to find open ports), a NULL scan (a TCP packet with no flags set), and an Xmas (a TCP packet with the P, U, F flags set) scan. Each of these will return results, but with diminished reliability.
- nmap -sU -P0 192.168. 1.115
- nmap -sN -P0 192.168. 1.115
- nmap -sX -P0 192.168. 1.115
Step 4: Dropping Below the Threshold
Although these scans will not be logged, the firewall or NIDS may block or alert the system admin of the scan. Modern firewalls and nearly every NIDS can detect these types of scans and block your scan or send an alert. If you're blocked by the firewall or NIDS, the alert will capture your scan and IP address as it identifies your scan.
Most of these perimeter defenses, though, have a weakness. That weakness is that they only detect and alert on these scans when the number of packets that meet its signature exceed a certain level or threshold. If we can figure out what this threshold is and stay below it, we can run our reconnaissance scan without being blocked and without triggering an alert.
The most widely used NIDS in the world is Snort. It has signatures built into its ruleset to detect scans like those we are attempting from nmap, but because networks see so many port scans everyday (large corporate networks might see 1000s a day), they set a minimum threshold level that the scan must meet before it triggers an alert. In Snort, the threshold is set by default at 15 ports per second. If we scan scan below that threshold, our scan will go undetected!
Remember, the more we know about the firewall and NIDS, the better we can evade them. See my previous articles using evading an NIDS with Snort here and here for more information.
Fortunately, nmap allows us to scan at different speeds—and it has six different built-in speeds. We can change the speeds by using the -T switch followed by either the name of the speed or that speed's corresponding number. These are:
- paranoid 0
- sneaky 1
- polite 2
- normal 3
- aggressive 4
- insane 5
The two slowest speeds, paranoid and sneaky, are both below the Snort threshold for port scans. Now, we set our scan down to sneaky speed by using this command:
- nmap -sS -P0 -T sneaky 192.168.1.115
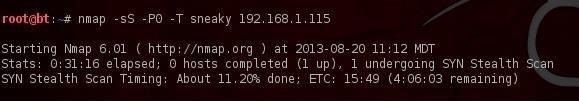
Our scan will now sail right past the NIDS and firewall without being detected. The downside, of course, is that we need to be VERY patient as this type of scan can take longer than a default scan or an insane scan (the fastest). For instance, the "sneaky" scan can take up to 5 hours per IP address vs. .42 seconds for the default scan. Your patience now, though, will likely be rewarded if you can get past the firewall or NIDS without being detected!
Questions?
If you have any questions on any of this, please ask them in the comments below. Or, if you have an unrelated hacking question, stop by the Null Byte forum. And as always, stay tuned for more hacking lessons!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.





















14 Comments
Very interesting post, a few day ago I been reading about nmap and I found very useful with a lot of options.
I read it from the "reference guide" of nmap.org, but is a little bit technical and difficult to understand when you read it for first time, so your post come perfectly for understand the basics of this tool.
I have seen that some parameters have changed in the lastest releases of nmap, like the -P0 parameter that is now -Pn (No ping), maybe that confuse somebody, but in BT is still working fine, I use the lastest version of Zenmap (GUI nmap) so i figured out of the changed of some parameters.
Well, i just want to clarify that. I like that you focus in this kind of tools and you explained so well, I appreciate your work and I'm waiting for more post like this.
Thank you.
Master OTW...i wanna go a lil bit off topic...how do i send you personal questions ? and the next question..how do i get the ip address of a particular target in any part of the globe? i saw your article of scanning vunerable ports...but lets say i wanna be specific...yeah like that story about the dictator wanting to bomb the world...how do i get his ip? sorry for such a noob question..but i have to start from some where..thanks in advance Master OTW...
King:
I would prefer that you ask me questions here in the forum, so that others that share the same question as you will get an answer as well.
As for how to get a particular IP? Well, it depends. If you know the domain, you can simply ping the domain and it will return the IP address.
OTW
thanks master OTW for the quick reply
Very Nice Article :-)
Great Tutorial OTW!!
I just have one question:
How come when i do a
"sudo nmap -v -sS -P0 -p 0-200 -T sneaky <IP of the victim>"
(2 hours later) i get the response that all of the 200 ports are filtered. But when I issue the same command just with one port (let say 135) i get a listing of the service on that port?
The machine I'm testing is a Win XP SP3, with the firewall enabled(VM).
Is it better to Google the most regular ports on that system and test them individually, tone down the scan from sneaky to paranoid or changing some other option in the command, as a means to get the info from the system?
I would really appreciate some insight on the subject.
Alpha
If you ran the commands the same, you should get the same output. In some cases, though, firewalls will see the scan across multiple ports as malicious behavior and block your IP.
Hey OTW,
First like usual great article ! Have a noob question though. Why is it that you suppressed your ping when you are doing a port scan for just one target IP. To my knowledge the benefits of using that no ping was for when you were scanning multiple IP's in one scan and didn't want to waste time discovering hosts first from the ping, but whats the point if you are only doing one ip? even if it does get block won't your port scan still continue regardless as it is a different packet that is sending the syn flag? anyway thanks in advance !
No.
If nmap doesn't detect a host with the ping, it won't send the other packet.
Ok I'll make sure i start adding that option to my scan from now on. Thanks for the quick response !
OTW
I finally decided to try Nmap and scan my network just for educational purposes
I know my router ip i used it in nmap and used diffrient scans like tcp,tcp no ping,reuglar scan and intensive scan
I found 3 tcp ports open also it shows my routers name
My only problem is how comes it dosent show the other devices connected to the router ??
Mizanur:
There are many reasons why nmap may not find devices on your network and it is largely dependent upon the type of scan you run. If you use -sT scan, it will find most devices that have at least port 80 open, but keep in mind that you must suppress the ping as many routers block ping.
OTW
Good. But may i ask one question out of topic. Or u can say its within. How do i understand how a website is hacked? Or which vulnerability is used by the crackers to hack a specific website? For eg: www.site.com/null.html
you see the / null.html is a page added by the cracker to that website. But how do we understand which method that they had adopted? I know some sites in this category. When they access /null.html
they are able to saw is the crackers deface page. Could any my doubt? Tnx in advance!
Thanks for great article!
But how can we see all devices on network and stay undetected?
1.Make a gateway + dns configuration + vpnbook + macchanger
2.proxychains nmap -sT -Pn -T paranoid (target ip)
3.after we found targets - how to get in with same undetectable and no trace?
How to ever-never leave footprints goin thru all stages of attacks?
I really hope you will answear me, I already readed many-many topics and I have now question for you so if you can answer - please :)
Thank you for sharing, big hugs :)
Share Your Thoughts