Welcome back, my tenderfoot hackers!
As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.
On the other hand, there are many here who come to Null Byte who do not have the time or inclination to study Linux in order to hack. They are looking for relatively sophisticated hacks/exploits, but want to do them on a Windows or Mac platform. Although Metasploit will run on either of those platforms, it does not work well. Many of its capabilities are non-functional on, for instance, a Windows platform.
There are some excellent hacking/pentesting applications that work well on Windows, such as Cain and Abel, Wikto, and FOCA, but a new hacking framework called Exploit Pack has emerged that is platform independent.
Exploit Pack, developed by Juan Sacco, is similar to Metasploit but written in Java. Besides its universality and easy-to-use GUI, Exploit Pack allows you to develop exploits in the language of your choice (Metasploit exploits must be written in Ruby). We will examine that at a later time.
Exploit Pack is open-source and released under the GPL license. Its free edition has over 350 exploits, while its Pro edition has nearly 35,000 exploits. Although we will be using the free edition here, the Pro edition costs 300 Euros (about $320 USD). As exploit frameworks go, that is very inexpensive.
It is my hope that by demonstrating some of these hacks with Windows tools, that newbies will get a taste of what is possible and be inspired to continue on Null Byte to learn Linux and its tools and capabilities. This is because Linux is really the only operating system to use as a professional hacker, but in the meantime—let's explore and use Exploit Pack!
Step 1: Download & Install Java
The first step, of course, is to download and install Exploit Pack. As I mentioned above, it is written in Java, so it is requisite that you have Java 8 installed. You can go to Oracle's website and download Java 8 for your architecture. Since I will be working on a 64-bit Windows 7 system, I downloaded the Windows x64 Java, as circled in the screenshot below.
Of course, if you are using a different architecture, make certain to download the Java specific to your architecture. Please note that before downloading it, you must accept the license agreement, and you need to have a free account with Oracle, as well.
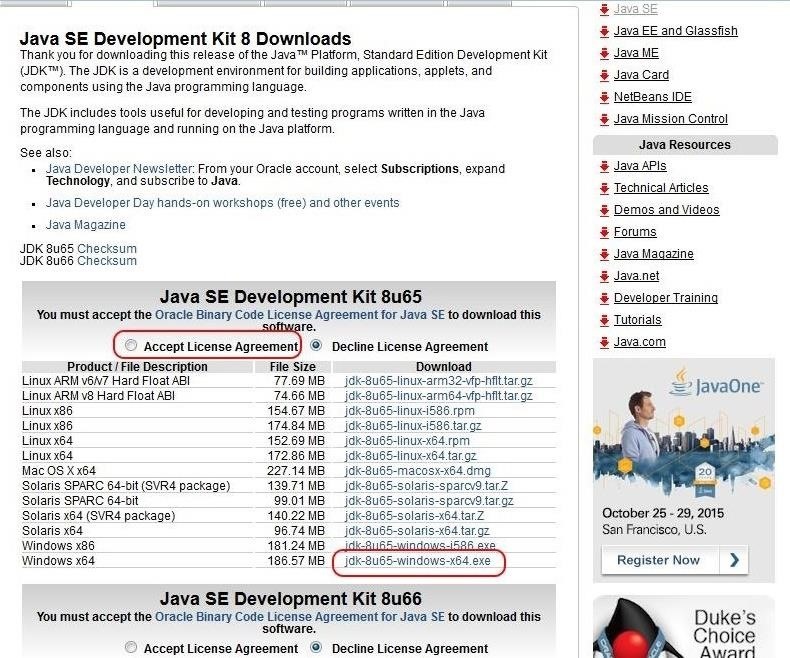
Next, go ahead and install Java on your system after downloading it.
Step 2: Download & Install Exploit Pack
Now, we can download and install Exploit Pack from the Exploit Pack website. Note that the MD5 hash is next to each of the downloads. It is a good practice to check to see if the MD5 of the downloaded code matches this MD5 to make certain that the code was not corrupted or otherwise altered.
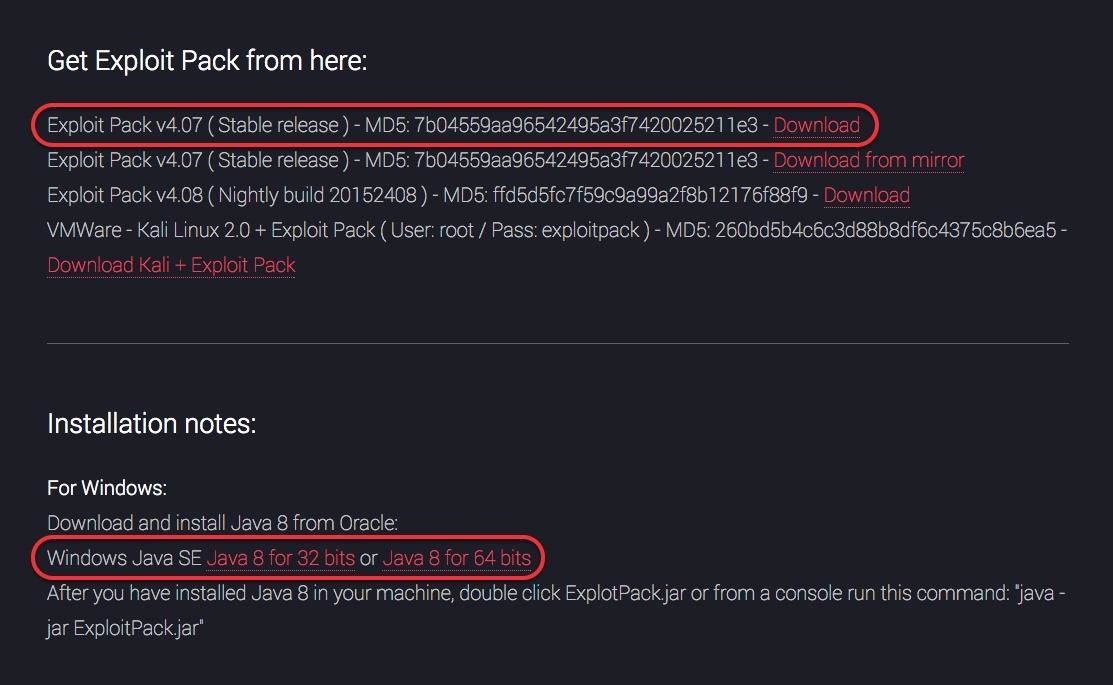
For those of you who want to use Exploit Pack with Kali Linux as a VMware virtual machine, note that Exploit Pack is available with Kali 2.0 as a VMware image (the last of the download choices).
Step 3: Start Exploit Pack
Once you have completed the Exploit Pack download, go to the directory you installed in. In my case, I created a directory named "Exploit Pack" and extracted all the components there.
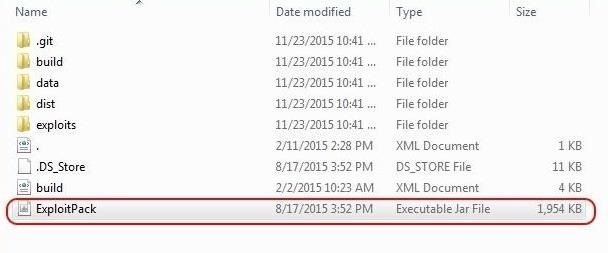
When you go to the directory with Exploit Pack, look for the executable .jar file as I circled above. Click on it and it will begin to open Exploit Pack.

Click on "Continue" when this you see this splash screen to open the Exploit Pack GUI.
Step 4: The Exploit Pack GUI
When Exploit Pack is done executing, you should be greeted by a user friendly GUI like that below. For those that more comfortable with "point and click" rather than the command line of Linux, you should find this interface intuitive and familiar, I hope.
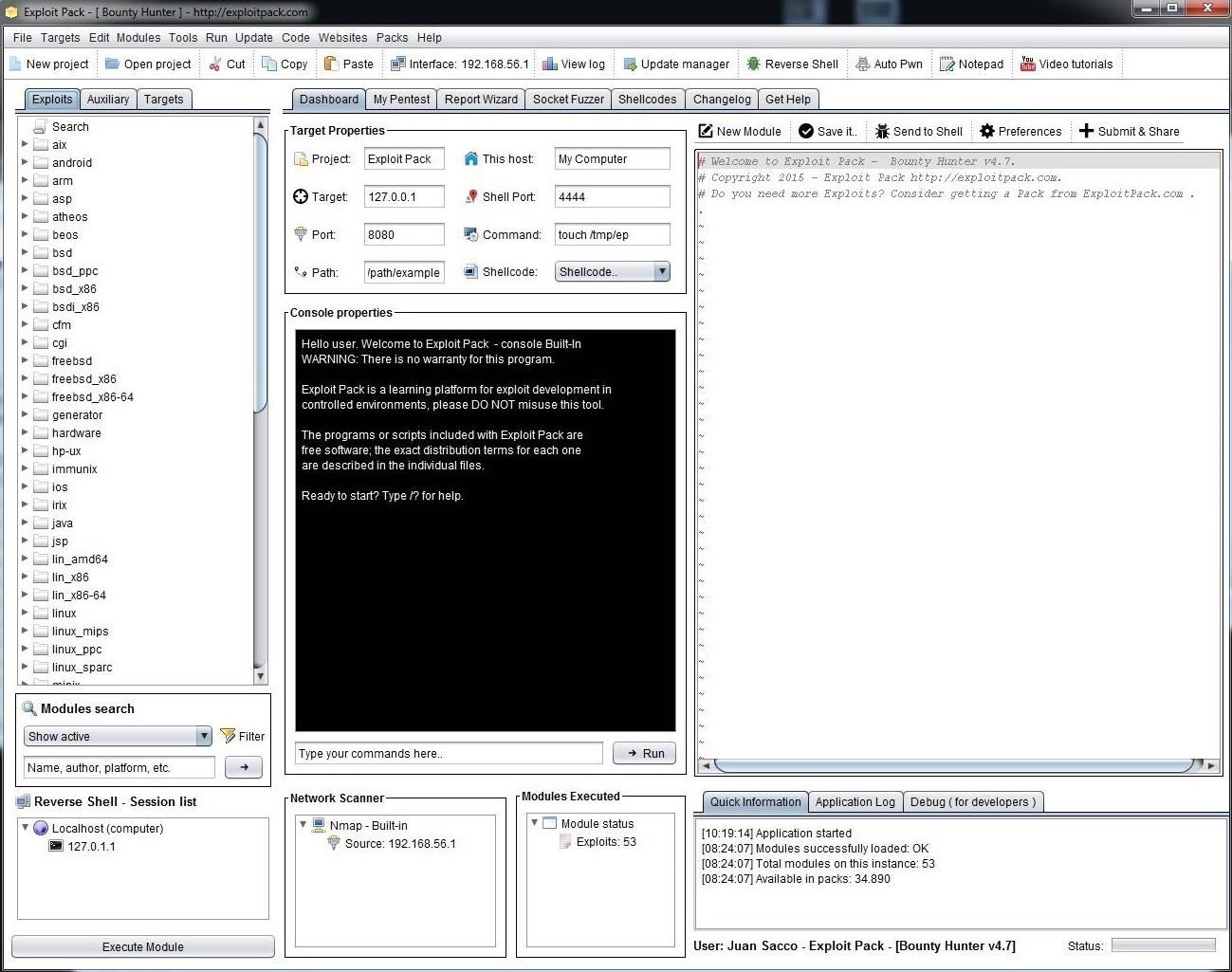
Step 5: Explore the Interface
Exploit Pack has a clean and easy-to-use interface. As you can see, if you go to the far left window, we can see three tabs, Exploits, Auxiliary and Target. If we click on Exploits, it brings up a long list of exploit categories, primarily classified by the target operating system (although there some some non-OS categories such as cgi, etc.).
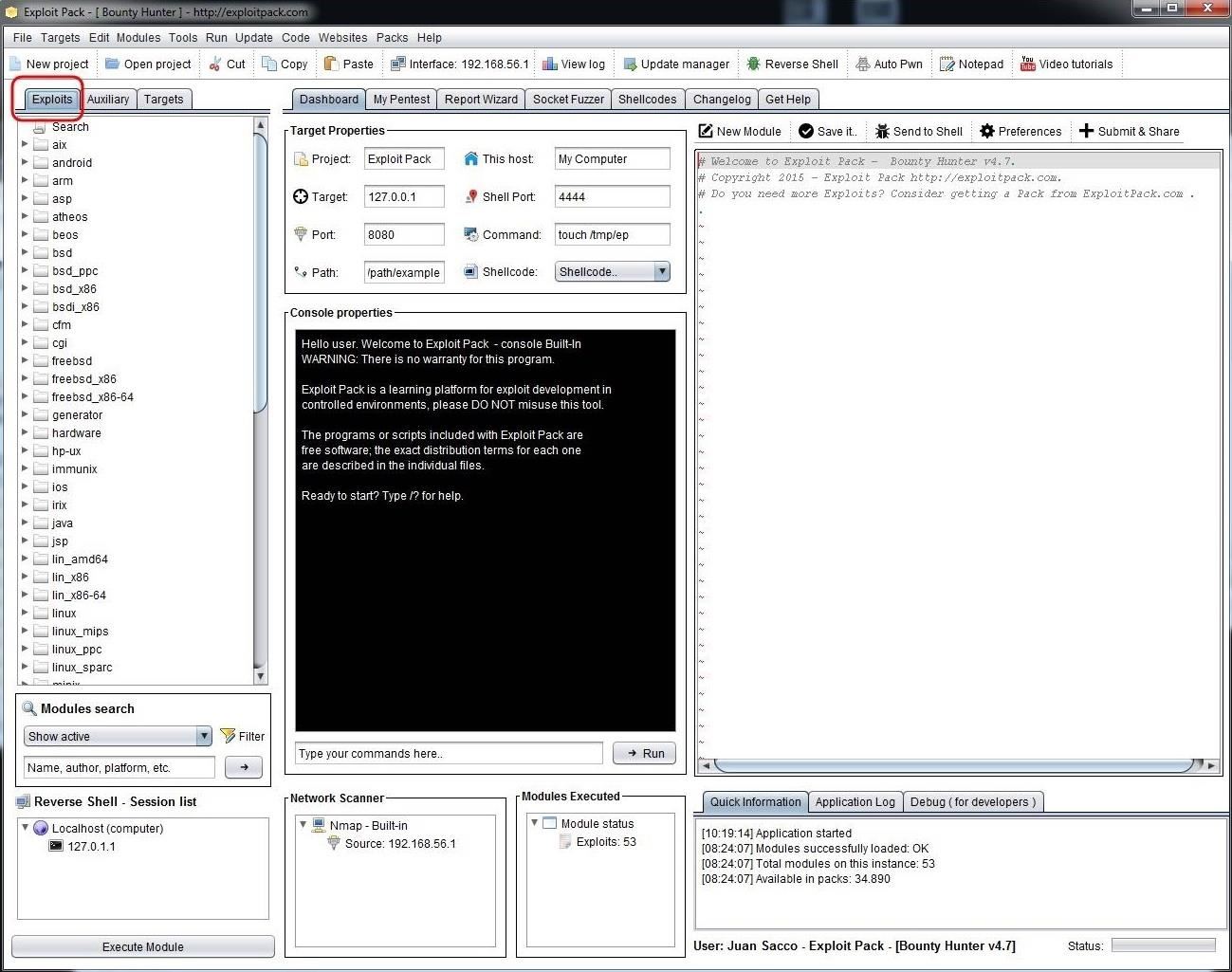
If we scroll down that list a bit, we will find the Windows exploits. Click and expand that list and it reveals a long list of Windows exploits that we might use to hack Windows systems. We will be using some of those in future tutorials.
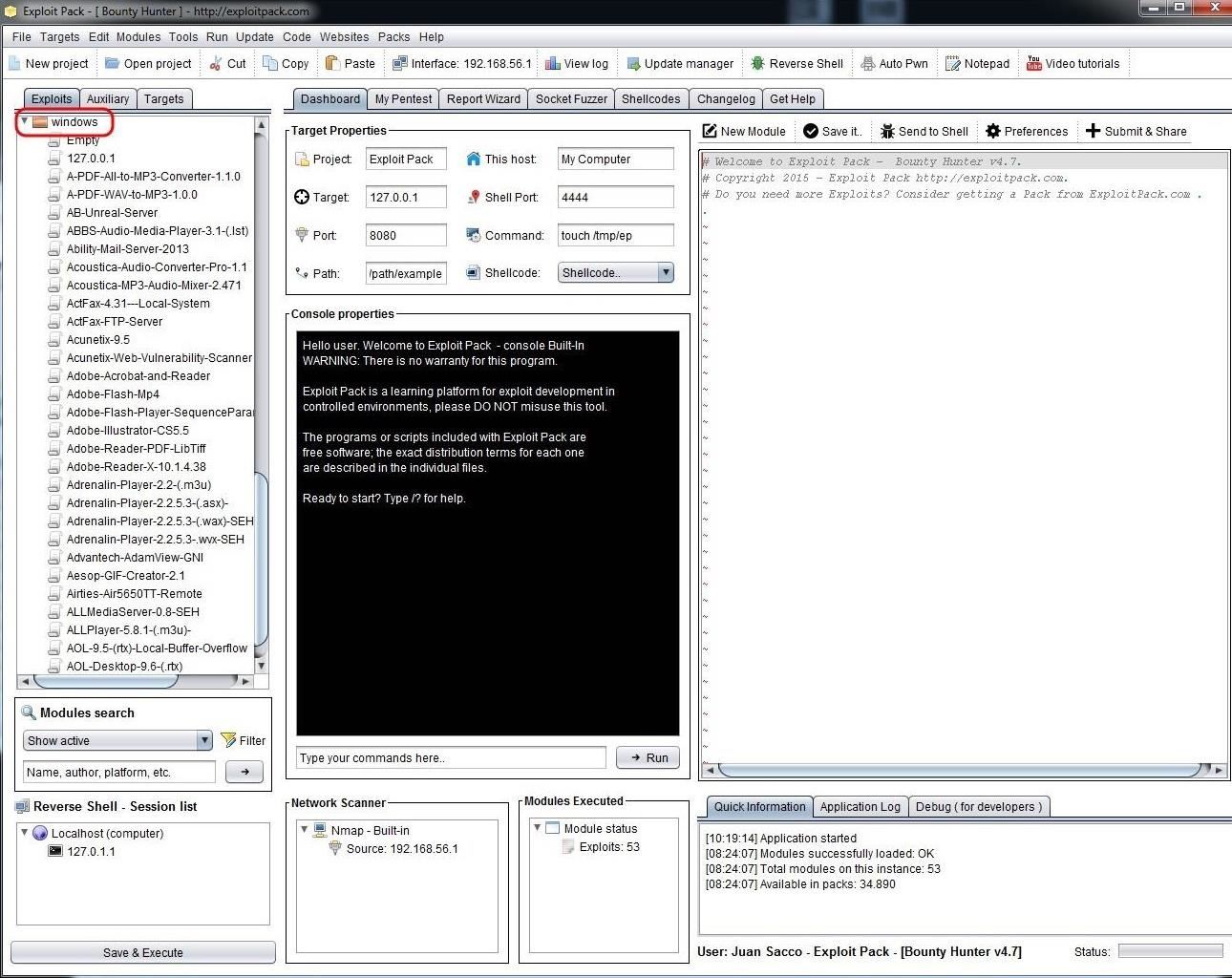
We can click on the "Auxiliary" tab and—similar to Metasploit—it contains the Scanner and DoS modules.
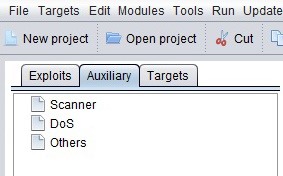
We can search for modules by going to the "Module Search" box beneath the Exploit window, as seen below.
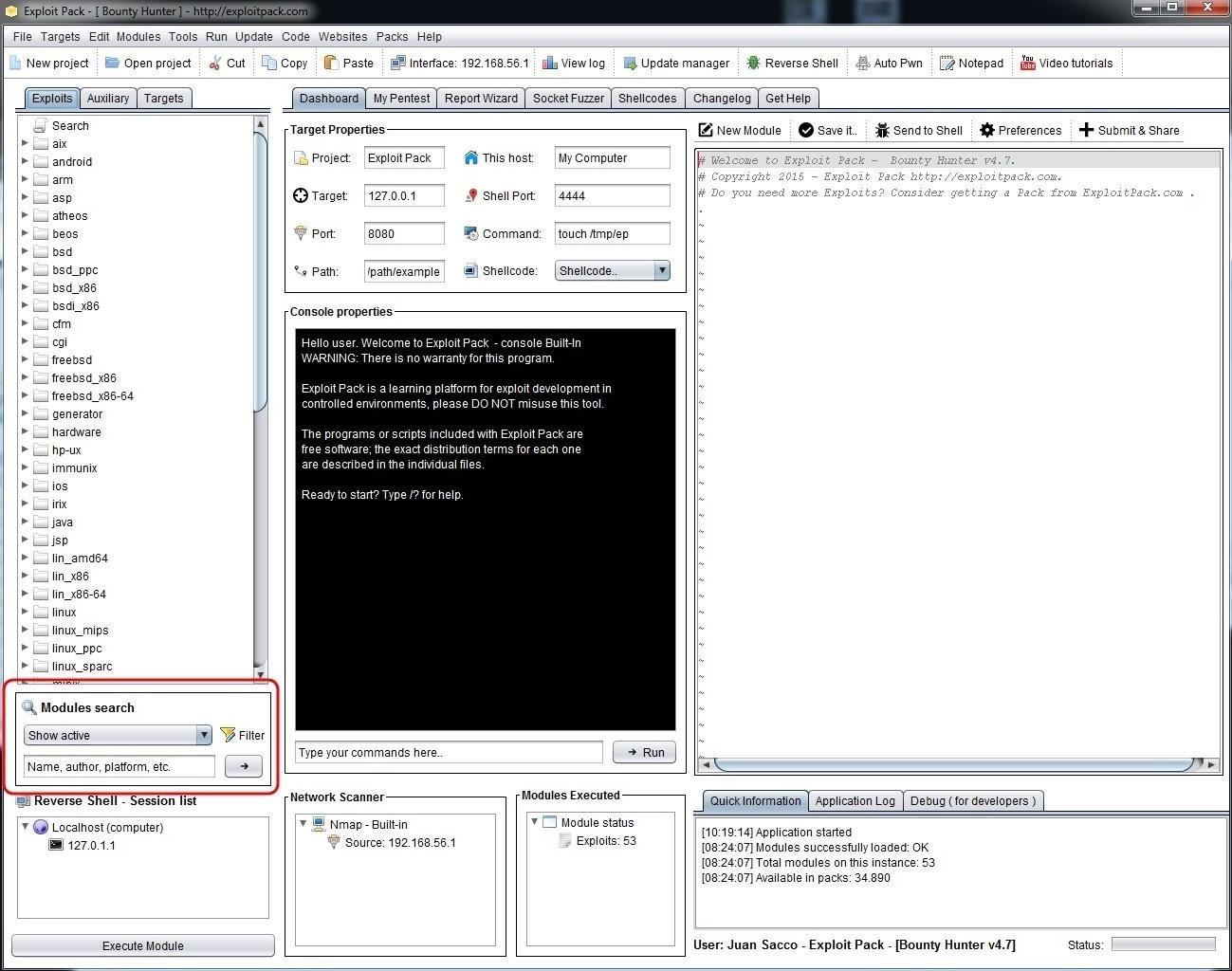
In the Module Search window, we can choose to show active, recent, or everything, as well as search by name, author, or platform.
Now that we have installed and have a basic understanding of Exploit Pack, come back to explore how to use it to hack nearly any type of system!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























11 Comments
Very interesting, I hadn't heard of it before but it reminds me of Armitage.
Cheers,
Washu
Another great hacking toolkit to add to my arsenal.
Thank you, OTW!
Thank you for starting this series! Looking forward to it.
i know this is a bit late in the digital world, but thank you OTW. :D
i am relatively green so i am still going thr ough the growing pains of learning to be comfortable with a cmi so this gui is a nice break. maybe i can get a little more done alittle faster. thnx
when the second part of this tutorial comes
was there ever a part 2 made?
Asking the same thing.......Did you in anyway get a reply?
Please where can i find the continuation of this thread or if it can be continued.....really interested and wish to continue.....
Everything is different now on the Exploit pack site.....the file is packed with virus 15/59
What do you mean by this?
Share Your Thoughts