Welcome back, my nascent hackers!
Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)
In several episodes, Elliot was seen sending secure emails. As a seasoned and savvy hacker, he would never use Gmail, Hotmail, or Yahoo to send confidential messages. Instead, Elliot chose the most secure email system available to non-military and non-spy people like you and me: ProtonMail.

In a world where Google and the NSA inspect every email, a truly secure email service would be a godsend. Several email systems have touted themselves as secure, but we eventually learned that they were flawed or that their servers could be grabbed and inspected or otherwise compromised.
About ProtonMail
ProtonMail was developed in 2013, at least in part due to the revelations that Edward Snowden provided regarding the NSA's world-wide surveillance (WWS) program. It was developed by researchers from CERN in Geneva, Switzerland. If you are not familiar with CERN, it's the world's largest subatomic research facility that many credit with the development of the World Wide Web, among other things.
Being based in Switzerland gives ProtonMail several advantages.
First, the EU has far more stringent privacy standards than the U.S, and although Switzerland is not a member of the EU, Europe has much greater respect for individual privacy than what is practiced in the U.S., presently.
Second, Switzerland has probably the most stringent privacy standards in all of Europe. Long a haven for neutrality and secret bank accounts, Switzerland has developed sophisticated laws to protect individuals' privacy. In addition, Switzerland is outside of the U.S. and EU legal jurisdiction. This makes it an almost perfect physical location for a private email server.
ProtonMail was designed to give the email user complete anonymity. To accomplish this anonymity, it provides the following.
- End-to-end encryption (emails are decrypted in your browser).
- Does not require a phone number or another email to open an account (that account might be used to track your identity).
- You can set your email to expire after a number of days—even hours.
- It keeps no logs.
- Even the administrators at ProtonMail can't read your email.
- It is located in a neutral nation that is known for its respect for privacy.
ProtonMail has become very popular because of these unique security features. Presently, there are over 250,000 users worldwide and growing rapidly. Due to this rapid growth, you may have to wait awhile to get an account. You need to first request an account and, when they have the capacity, they will email you back telling you that you are eligible to open an account. Presently, this takes 2-3 weeks, but it does vary.
Originally funded by crowdsourcing, ProtonMail recently received venture capital to expand. We can only hope that this will help them keep up with demand for their valuable service.
Step 1: Apply for a ProtonMail Account
The first step, of course, is to request for an account. Go to protonmail.ch and submit a request for an account.
Step 2: Create an Account
Once you receive the email notifying you that you can now open an account, click on the link they sent you. This will take you to a "Create Your Account" screen, such as below.
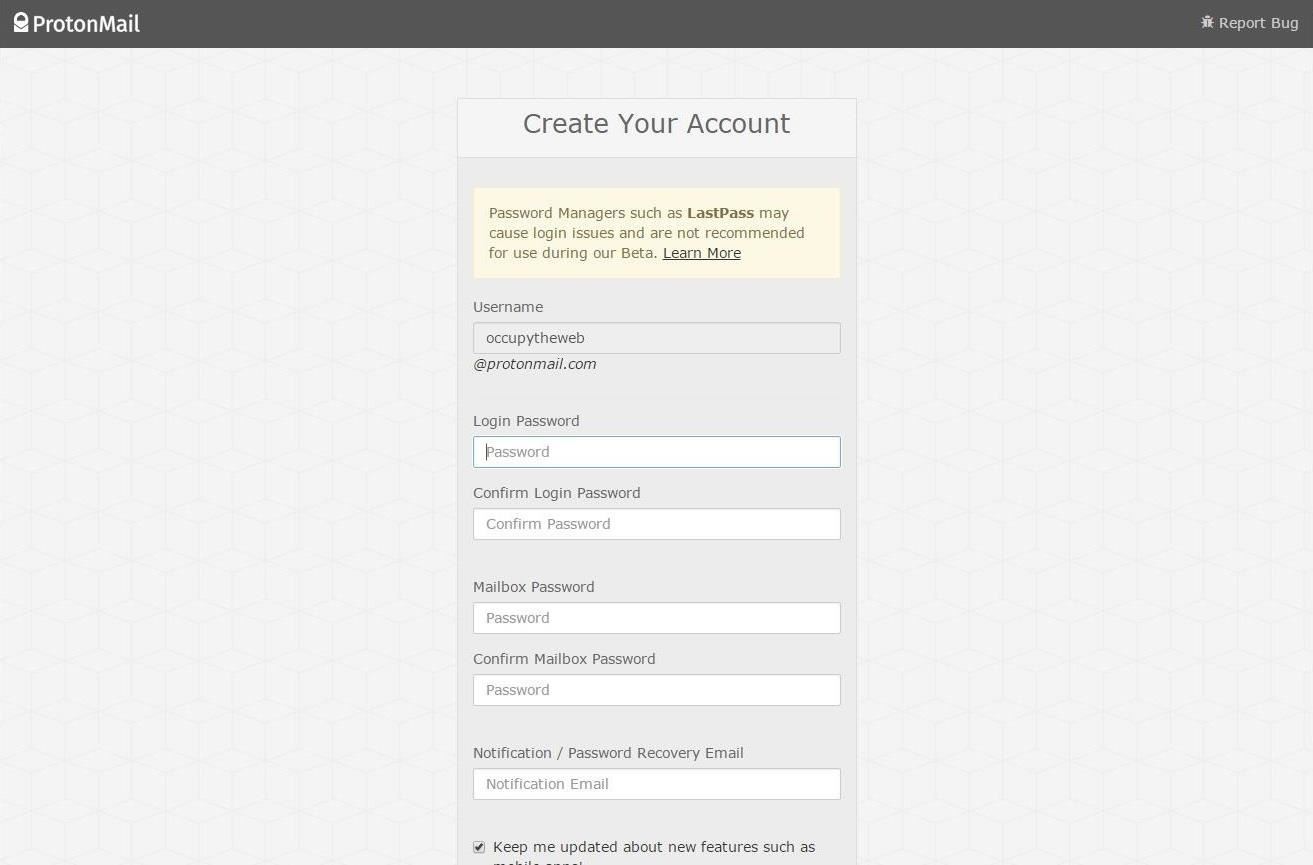
It looks a lot like any other webmail account form, with one exception: it requires two passwords. One is to log into your account and the other is to decrypt your email. For maximum security, make certain that these two are different.
Step 3: Log In
Once you have created an account, you can log in like any other webmail account.

Now that you have successfully logged in with your username and password, ProtonMail will prompt you for your second password which is used to decrypt your email.
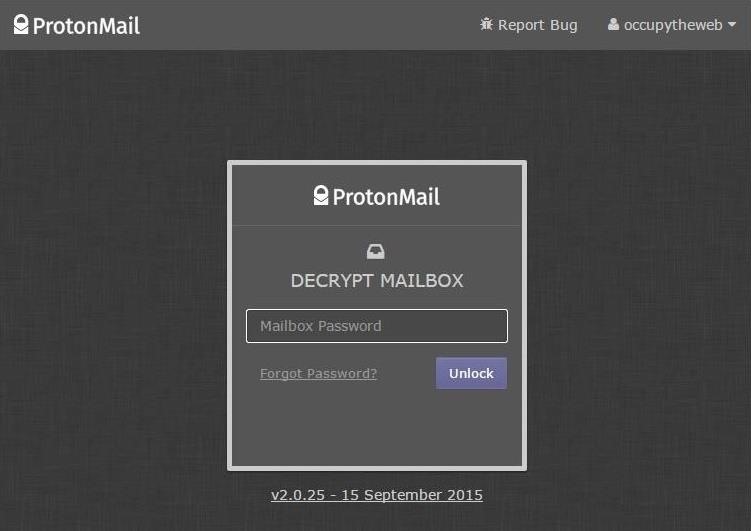
When you enter it, it begins working on decrypting your email as seen below.

When all of your email is decrypted, it will open a familiar email interface.
Step 4: Security Settings
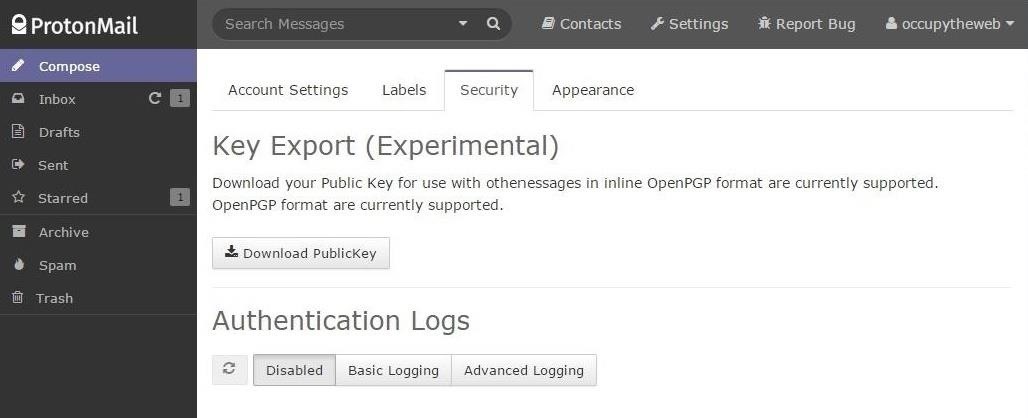
If you click on "Settings" in the top bar and then "Security," it brings you to the screen below. Notice that you can export your PublicKey for use in PGP-compatible services. Presently, it is only compatible with OpenPGP. Also notice in the lower half of the screen the "Authentication Logs." By default, they are "Disabled" and I recommend you keep them so for the highest level of security.
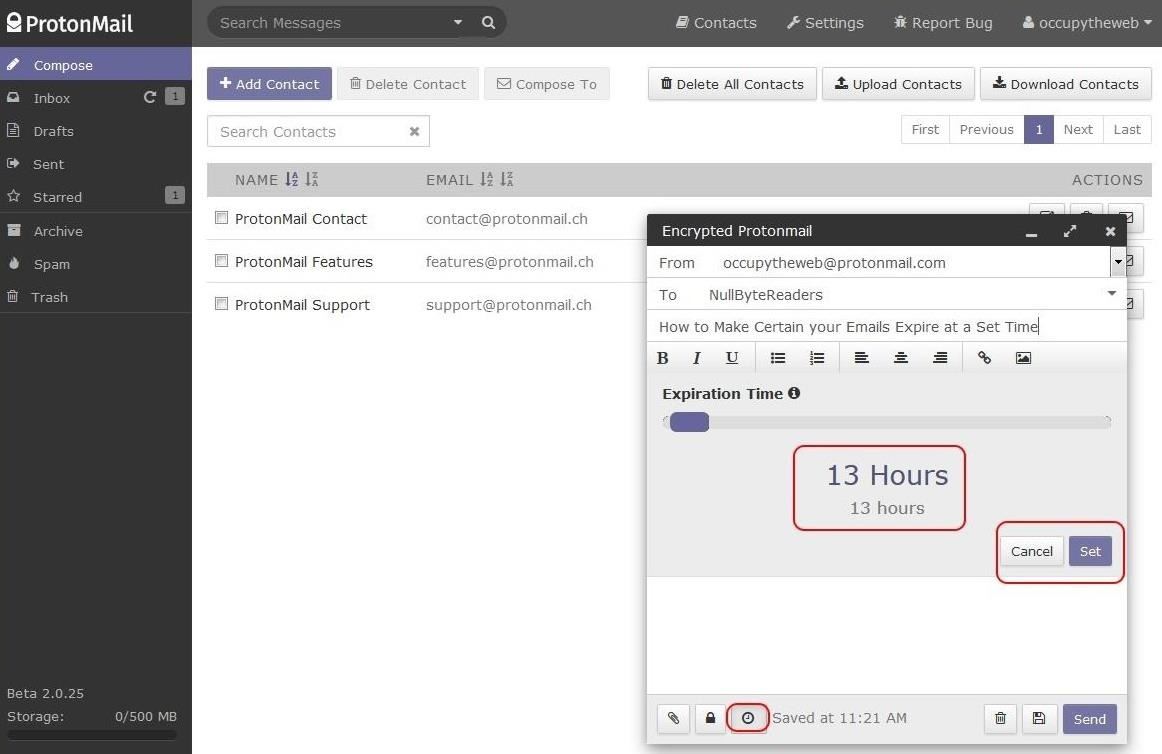
Step 5: Email Expiration
One of the features of ProtonMail that I really like is the email expiration feature. When you compose an email, you can choose how long it will exist on the server before "expiring."
To do so, simply click on the "clock" icon in the bottom of the compose email window and it will open a slider where you can choose how long the email will exist. In this case, I set the expiration to 13 hours. After you hit "Set," the clock will begin ticking, and when the time has expired, the email will expire and no longer be available to ANYONE.
In addition to keeping your emails safe from prying eyes, if you want to make certain your chat sessions are secure, check out my article on OTR. (OTR, or Off the Record, is an IRC client.)
Keep coming back, my nascent hackers, as we continue to explore the techniques and technologies of the world's most valuable skill set—hacking!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























28 Comments
Perfect timing, I needed some crypto news today!
As always, well written article, Thanks OTW, we're waiting for more of your tutorials and would like to see some new things, like new exploits or methods or whatever you like, anyways thanks.
Thanks! i love this series!
Thanks for this great article OTW. but what if these are just a bunch of lies? I mean think about it, which company or group do you know that know something about a bunch of hackers, but a government doesn't pressure them for those information? what if administrators check all the emails or the clock doesn't remove the email completely? i know i'm just paranoid, but i think these all are possible!
Great tutorial as always !!
@D@RKPRINCE
If you don't trust their end to end encryption, you can always encrypt your mails before sending. That will require some work for your recipient too, but that adds an extra layer to the cake. It's always a good practice to trust no one, your paranoia is a virtue.
hey OTW can you also make how to make our encrypt and decrypt mails .
This service encrypts and decrypts your email.
You mention that you don't need another email to sign up which decreases tracking, however you need to give them your current email to sign up to the site. Is this not a chink in the system?
You can delete that email once you make the account officially.
Good article! For most emails I send I don't care if someone sees it because most of the time it is a link to an article or a video and usually encrypt manually anyways or use peer to peer. What do you think of just peer to peer messaging instead?
Peer-to-peer messaging is not secure.
I mean if you encrypt it with private and public keys.
Hey Jeremiah, OTW made an article on a protocol called OTR (off the record). It shows how to install an IRC (internet relay chat) client called Pidgin with an OTR plugin onto Kali Linux. It uses AES encryption among other security measures. I've set it up and used it successfully myself. See here:
https://null-byte.wonderhowto.com/how-to/hack-like-pro-install-use-secure-irc-client-with-otr-0163318/
Great share and as always, well written.
Small doubt, if you are posting about protonmail everywhere, won't it attract more visitors? If it does that, won't security agencies get the attention and try to demask it?
Protonmail needs an invite I guess. The only other way round is to pay ;)
This is probably a huge topic but I was wondering if you could do an article in this series on the hack in 1x06 where he targets Isaacs S5 phone to get all the info on the drug business?
That one is coming!
Really looking forward it !! Can't think of anything, besides the (bad) luck of the dealer have some obex program already installed in his phone, an already paired device, and enough time on elliot's side to brute force a valid authorized bluetooth mac (he could have scanned the bad guys before and have already a log of their bt mac, just in case...). Bluetooth hacking on Android out-of-the-box is hard, and anything involving social engineering would have raised a red flag on the dealer (he knows Elliot is a hacker). He could have pulled it from some google play backup, or swooped some malicious apk via google play update, but it looks like he does is via bluetooth only sooo... that makes me wonder.
Well, I guess I just have to keep waiting for the guide.
Yeah! It was very impressive. I've been thinking about that scene a lot. Trying to figure it out, thinking of the pentesting implications. I cannot believe OTW watched it and thought.... "yup, easy." And I can't wait for the guide. Can we have a hint? ;)
I love you
am now a user of this account, is so better than all emails I've encounter
GREAT SHARE MASTER OTW.
I GOT ONE FOR ME AND FEEL MORE SECURE.
What are your thoughts on hushmail.com out of Canada?
Hushmail has already proven themselves unreliable. When asked for emails from US authorities, they complied.
Proton Mail is awesome.
Hello I have a doubt :
Can we send secure emails by using a SSH TUNNEL..sorry if it is a dumb question I am just curious (wondering too)..:)
Dude the show just got finished.For me it was the best two last seasons i have ever seen in a Tv series . There is a ton of things that needs of explanation and waiting for that from you
Share Your Thoughts