Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.
In today's modern age, it is important for the hacker to be able to dig up and find intelligence. Using the most popular search engine in the world as of 2015, the average hacker's job becomes easier. Not just easier, but very efficient.
Our friends over at Exploit Database have developed a library of "Google Dorks" that will pull up information on the spot. They are all user submitted, and frequently patched by companies all over the web, so it is important we know how to use this tool correctly. That is why today I present: The Google Bloodhound

Resources
First let's open up this library that is google hacking database and check out the layout.
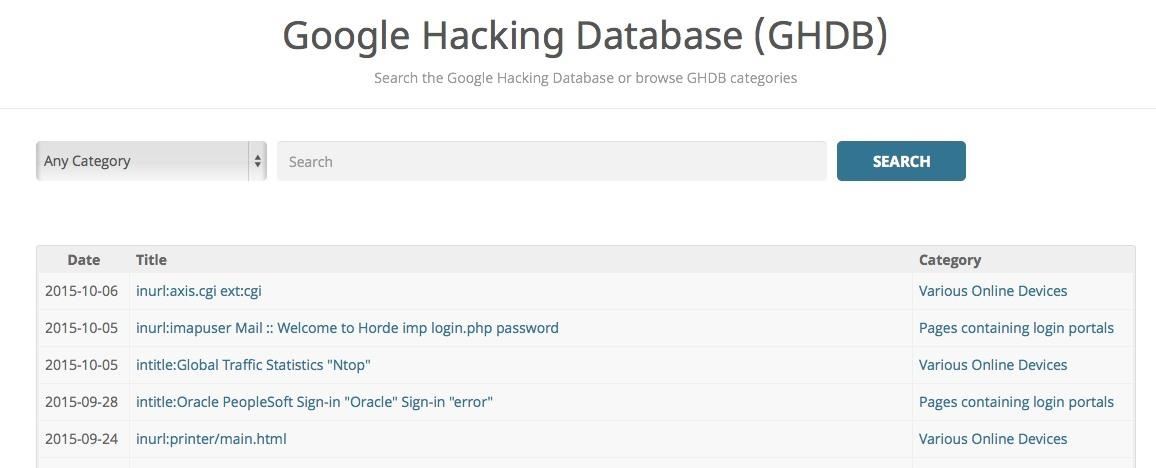
As you can see, this is a very easy layout to use. If we click on the categories tab, we can see that we have plenty of options to choose from.
Take Note: You will often find google dorks that simply do not work. These are all user submitted, so this is normal.
For the sake of simplicity I chose "File containing passwords" to prove how easy it is to gain access to an unauthorized account. I also did not want to search for a specific key phrase in the search box so instead I didn't type anything in, and hit enter.
Google Is My Friend
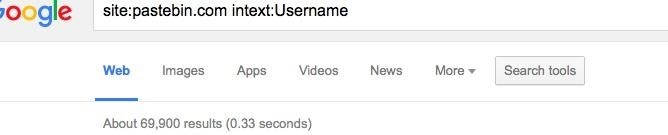
Ah, yes! I finally found a dork that is perfect for this tutorial.
Here is the one I will be using:
site:pastebin.com intext:Username
From the looks of this dork, we already know a couple of things.
- We know that it will pull results from pastebin.com, a popular website known to hold the world's most notorious pastes.
- We know that it will search for the keyword, "Username"
As you can see, we are bombarded with results. 69,000 to be exact.
Upon clicking a "juicy" link, we are bombarded with even more usernames and passwords.
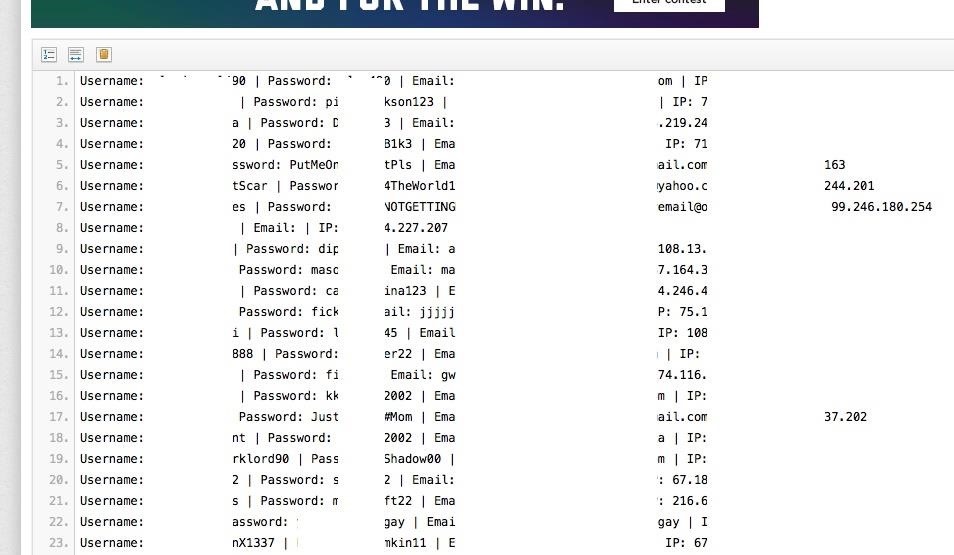
I have of course, edited out the actual passwords, but it is still surprising to see how many people are at risk. This is one link out of 69,000.
Conclusion
You, dear hacker, have found ways to creep in the dark corners of the internet through nothing but a google search. The moral of the story is not to actually be a creepy stalker, but to protect yourself.
Change passwords frequently.
Make sure you check to see if you have been "pwnd" at a very helpful website, http://www.haveibeenpwnd.com.
I hope you have enjoyed this tutorial, and please leave any questions or concerns in the comments.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















9 Comments
I always use Exploit Database and never heard about Google hacking database, Thanks for letting us know about it +1
Your welcome!
Google hacking is always my number one goto when starting a engagement. I like the GHD but the results are a bit broad in my opinion, I find the best is to make customs searches depending on what your after. Once you get good with google, it becomes one of the most powerful tools. Thank for the tutorial!
Cheers,
Washu
To me "hacking" with the GHD feels too easy. I do like it for recon though
It is really good if some people have figured out something unique or detailed. For example you can do web server version checks if the server hasnt disabled it. It is useful
I agree. This series is mostly focusing on recon.
This is awesome, def digging into this.
Wow I tried this and found a link of 15k brazzer accounts.... c'mon people lol. Great tutorial to expand what I thought I already knew. Thank you, Love this series, I hope you do some more
On another note, Does anyone know exactly where these huge dumps of passwords come from?
Share Your Thoughts