In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a friend pointed out to me, Ubuntu is currently the only distro implementing SHA-2 as the default. With SHA-2, your passwords take an unreasonably larger amount of time to calculate. This will greatly decrease how many passwords a person can brute-force.
So in this Null Byte, we're going to beef up the security in the way Linux hashes passwords to increase the security of our system.
Step 1 Edit the /etc/pam.d/passwd File
Bold text = commands entered in a terminal emulator.
First, we are going to need to modify the password hashing function, so when a password is entered, it runs it through our new algorithm. Lets open /etc/pam.d/passwd in our favorite text editor. I like nano:
sudo nano /etc/pam.d/passwd
You should get text that looks like this:
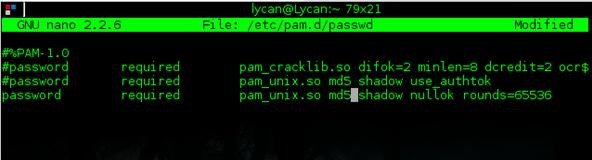
We need to change the bottom line. Change md5 to sha512:
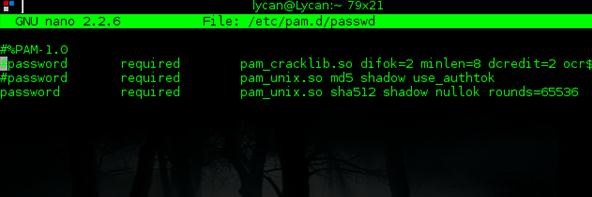
As you can see in mine, I have the rounds option enabled. This is how many times it's hashed, so for every round an attacker would need to computer another hash. I set mine at 65,536 for ridiculous security. After that is done, hit ctrl+x and y to save it.
Step 2 Change Your /etc/default/passwd
Let's modify our default /etc/default/passwd file now, so our computer knows to use this algorithm when creating or modifying passwords.
sudo nano /etc/default/passwd
Change the seventh line from des:
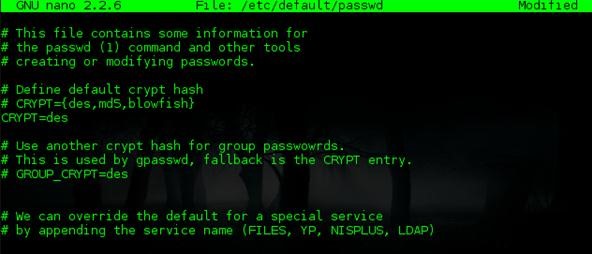
To sha512:
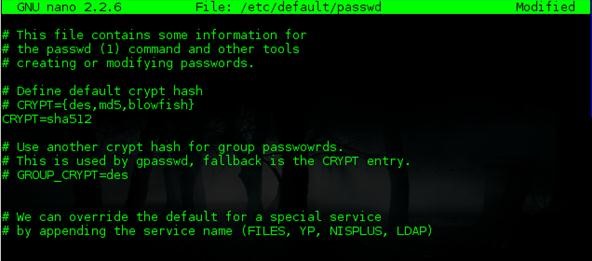
Onto our next mission!
Step 3 Edit Your /etc/login.defs
According to the passwd manual page, this file has to be edited when the /etc/shadow mechanism is used for storing passwords:
sudo nano /etc/login.defs
Add the following line to /etc/login.defs:
ENCRYPT_METHOD SHA512
Step 4 Rehash Your Passwords
We have to reset our passwords with the passwd command, so that they're stored in /etc/shadow with our new hash:
su root
Then change the users passwords who exists:
passwd <username>
You should now have incredibly strong passwords for your Linux box! Feel free to drop a line to me in IRC or start some discussions in the Null Byte Forums.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























6 Comments
Ubuntu uses SHA-2 as default? What about offshoots of Ubuntu... such as mint?
Yes, Ubuntu uses SHA-2 by default.
AFAIK, no, Mint it doesn't. But I could be wrong.
Interesting. When I go to my parents house next I shall look into this.
Ok... In my passwd file it doesn't have what is in yours. Instead it has @common-passwords, so I went back to pam.d and opened common-passwords and found something that looked much more like yours. Also, while it says the default is to encrypt with unix crypt, the only line on the page I can find that looks like the one you edited, already has sha512 written in it. It's not commented out. Halp?
So, that means you are already using SHA512 :D
Thats what I thought. Yay :)
Share Your Thoughts