Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.
Scanf - Requesting Input
In the previous tutorial, we used the scanf man page. If you have read the page, then you will know what's going on. I will say again that I will no longer be explaining what functions do in detail unless they are ones that I have made myself (we will be covering functions in a later tutorial).
Similar to the printf, we can provide a format specifier to determine what kind of input we desire, be it an integer, a character, a string, etc. and we can give it another parameter as a variable to correspond with each mentioned format specifier. This will read from the console, obtain the value in the appropriate data type and store it into our variable. The difference between printf's and scanf's variable parameters is that the variable must be prepended with the address-of operator (&). The only variable where you do not need the address-of operator is when it is a character array. The reason for both of these phenomena will be presented in a tutorial on pointers and addresses.
Let's write some code to illustrate this.
Example Code
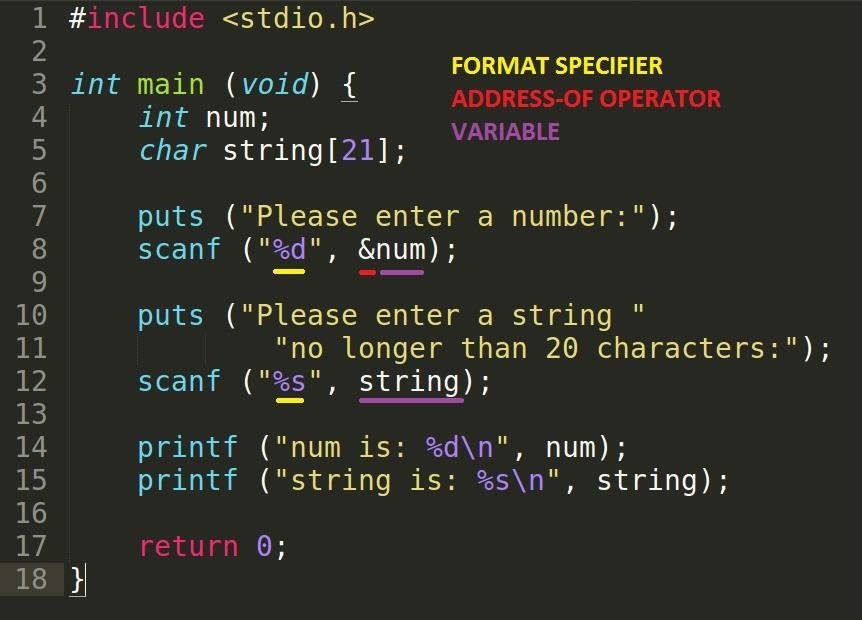
Note Do not put newline characters in the string parameter of scanf like you would do in printf.
Here we ask the user to enter in a number to be stored in the num variable and a string to be stored in the string variable.
Compiling and Running
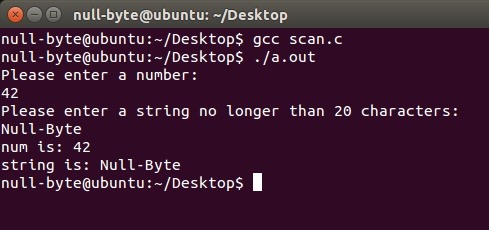
Works perfectly!
Gets - Requesting String Input
Besides the scanf function, there exists another function specifically for obtaining strings from the user. Let's see it in code.
Example Code
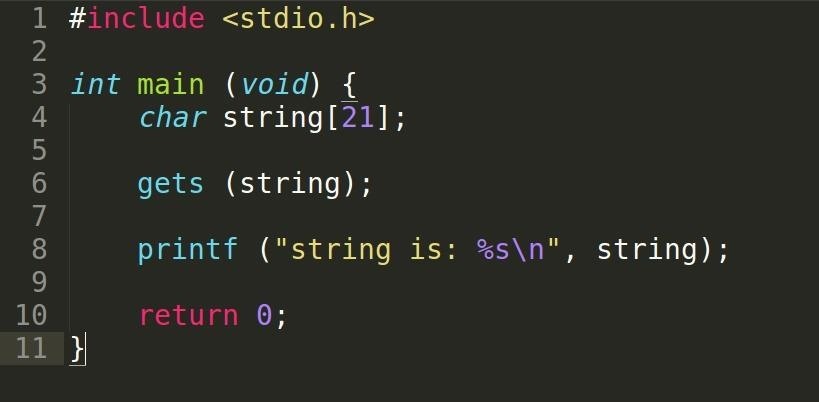
We can use the gets function to get a string from the user through the console and store it into the string variable.
Compiling and Running
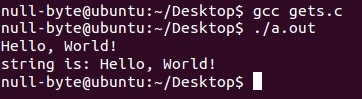
Nothing wrong with that... Or is there...?
Conclusion
Again, play around with these functions, do some crazy things people won't ever even think of. Just go wild with it! Next tutorial I will be introducing the buffer overflow vulnerability to you guys and I will also demonstrate what can happen when getting user input goes horribly, horribly wrong!
dtm.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















3 Comments
These tutorials look great so far.
Will you be covering C++ after you're done with C? I'd like to see some advanced tutorials that cover all those pesky small things.
Also, would be nice if you add a link or two for the functions you use in each tutorial, as official/trusted references.
PS: You'll be giving me quite a good pump after you're done, I wanted to learn C and C++. So yes my friend, we're reading them! stay motivated!
Nice How-To/Time ratio though!
Hey CyberMask!
Unfortunately, I am not well-versed in the C++ language. The only exposure I had with the language was when I had taken an object-oriented C++ course in the second half of 2015 which, in my honest opinion, was not very well taught. As Phoenix750 says, he will be covering the C++ part and C as well if he feels like it or if I've missed something. As for the details in the low level such as memory, it should carry over so that's nice. If it doesn't, I hope I'll have covered enough so that you can experiment for yourself!
Also, a big thanks for joining me on this journey and allowing me to teach and give the necessary skills to you for you to be able to expand both your programming and hacking skillset.
dtm.
out of curiosity,
What is that ".h" for?
Share Your Thoughts