How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!
Here is a list of pre-requisites for this article. Make sure you understand at least most of the concepts here:
- Shellcoding or assembly fundamentals,
- PE file structure,
- DLLs
- Basic WinAPI and using the MSDN's WinAPI documentation,
- Coding in C.
If you aren't so familiar with these, then I will do my best to explain what's happening and why I do what I do. If you still have some doubts, please leave a comment and I might be able to explain further.
PE File Infection Technique
Coding the Infector
We'll be designing our program to take in a target file from the command line.
First of all, we need to get a handle to a file using thefunction with the read and write access permissions so that we are able to read data from and write data to the file. We'll also need to get the size of the file for the following task.
The function creates a handle to the mapping. We specify a read and write permission (same ) and also the maximum size we want the mapping to be, i.e. the size of the file.
After we can create the mapping itself. Here we cast the return value as a pointer to an unsigned char which is the same as a byte value.
Of course, for all of these functions, we'll need to add in error checking to see if something went wrong or not. If something does, we can find the issue and hopefully fix it.
Once we've verified and the target file is suitable for infection, we also calculate the size of the shellcode. I will show you what these functions look like later on and it will make much more sense.
Next, we'll need to find an appropriate-sized code. For this example we will be finding the cave in the last section. We obtainedfrom the previous code section which is a pointer. Using the header information, we can calculate the starting position which points to the beginning of the code in that section and we'll read to the end of the file using the size of the file.
Next, we'll need a buffer to store the shellcode itself so that we can modify the placeholder values in the shellcode function with the correct ones
Now that the shellcode is complete, we can inject it into the mapped file using a memcpy. copy the shellcode buffer with the size of the shellcode and voila!
Great! Now let's take a look at the shellcode function(s).
After the routine has finished and done what we wanted, we then recover the register values
Demonstration
In the following example, I use putty.exe as the target file. As always, don't forget to use `color 0a` for that extra 1337 pr0 haXX0rZ 3ff3k7.
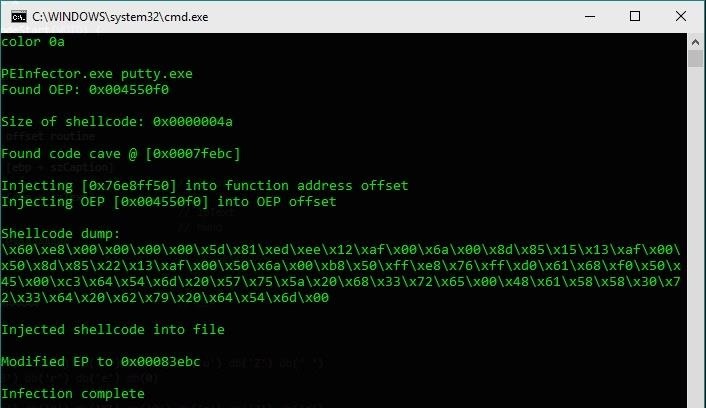
Lookin' good. Our payload is resting all tight and snug inside the cave, dormant, waiting to awaken and unleash its almighty power! Let's now run the infected putty.exe and see what happens.
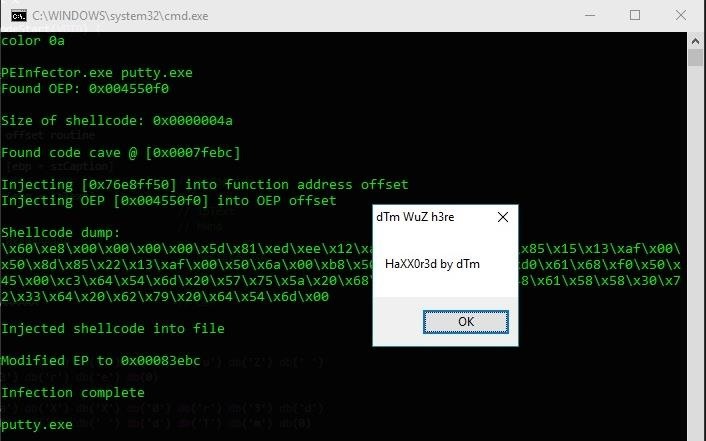
Sweet as, amirite?
Conclusion
Of course, you can modify the shellcode to whatever you want but you'll need to modify some things, obviously. The only limit is the available code caves within the target program and I'm sure there are more than enough within system files like explorer.exe or any large program for that matter. The possibilities are endless!
If you're seeking even more destruction, perhaps you can code your own little virus routine and attempt to infect all the files! Wow, that's pretty scary, actually!
Anyway... dtm signing off!
dtm.
P.S. Right, if you were looking for the code to get the PE headers and whatnot, please note that this was compiled with MSVS's compiler and may not work using others like MinGW. Here's a link to the entire project on Github
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























5 Comments
This series is great. Congratulations for this great article!
P.S.: These same technique can be used on GNU/Linux systems as well (at least use to be)
Thanks for following and reading m8te.
I guess there are a lot of crossovers since the PE format was based off the COFF and I guess ELF is too (I think).
Good stuff as always.
i don't understand how to use it
Hi,
Where are the next parts of these series?
Share Your Thoughts