By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century.
As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cyber warfare, hacking will shape the future of the world we live in.
What Happened?
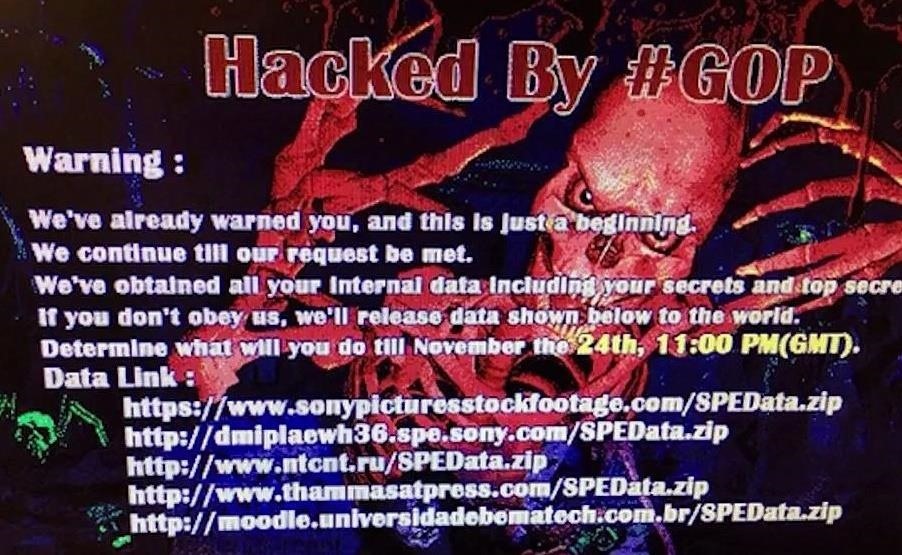
Sony Pictures Entertainment, the U.S. arm of the Japanese media conglomerate, was hacked by an organization calling themselves the Guardians of Peace (GOP). The hackers went into the servers and extracted films that haven't been released yet, emails, personal information, and more. All told, they exfiltrated over 100 TB (100,000 GB) of data.

Initially, the unreleased movies were posted to torrenting sites, but most were withdrawn quickly after legal threat. Probably more damaging was the release of the internal email between Sony executives and some of their producers and stars. The exfiltrated data also included personal information of employees including their medical, personal communication, and salary records. Now, these employees are suiting Sony for not adequately protecting their information.
The amount of data exfiltrated from Sony raises interesting questions. To remove that much data in a very short amount of time would have required a very fast internet connection. Or, it could mean that the hack took place over a relatively long time, maybe days or even weeks. If the hackers had used the data infrastructure of North Korea, they might still be exfiltrating the data. Instead, it appears the hackers used a broadband connection from China.
Why?
Seth Rogen and James Franco had developed a film about a small time TV talk show host (played by Franco) who is approached by the leader of North Korea about interviewing him. When the CIA finds out that they will be traveling to North Korea to interview Kim Jong-un, they employ the talk show host and his producer (played by Rogen) to assassinate the "fearless" leader. It's not an implausible plot by any stretch of the imagination.

As you might imagine, the humorless leaders of North Korea did not get the joke. They apparently set out to intimidate Sony from releasing the picture; when Sony refused, they hacked into Sony's servers and were leaking out the data through various peer-to-peer file sharing sites.
Ramifications
The costs to Sony will likely be staggering. Remediation costs alone will be in the hundreds of millions, but more important is the loss of trust and good will. In the few days since the hack was revealed, the value of the Sony conglomerate has fallen by 287B JPY (that's about 2.42B USD). This is a not a trivial amount of money, even for a corporation the size of Sony.
The movie was scheduled to be released on Christmas Day, but when the hackers threatened to create a 9/11-type attack on the theaters showing the movie, the major theater chains backed down and refused to show the movie, presumably to spare their patrons a terrorist attack. Then Sony pulled back the release of the movie.
Many political and social pundits criticized Sony for acceding to the terrorists' demands, and even President Obama chimed in that he thought Sony had made a mistake in not releasing the movie. Many in the artistic and political arena are fearful that Sony's backing down to these hackers will have negative implications for freedom of speech and expression in the United States.
Maybe even more important will be the impact of this hack on foreign relations between the U.S. and North Korea and North Korea and its neighbors. It's kind of staggering to think that a hack can change world events and dynamics, emphasizing once again the importance of our profession.
What Could Have Been Done to Prevent It?
Many people are pointing a finger of culpability at Sony for allowing this hack to take place. They probably deserve some blame (this isn't the first time around this block with Sony; remember the Sony online gaming hack of 2010?), but every corporation and institution with computers online is vulnerable to such an attack. There is no computer that is safe from being hacked, except one that is unplugged.
Given adequate skill, time, and motivation, any computer can be hacked. Most hackers have limited skills and are only capable of hacking low-hanging fruit, i.e., the relatively unprotected, unpatched computer systems. On the other hand, there are a number of hackers around the world with extraordinary technical skills, and when backed by a well-heeled client with deep pockets and enough time, they can violate any computer.
How the FBI Fingered North Korea
Attribution for any hack is problematic, at best. In some cases, it's impossible. In most cases, any visitor to a web server, or any server, will leave a trail. That trail includes their IP address. Knowing this, good hackers "bounce" their attacks off intermediary proxy servers and their trail will then only lead back to the last machine they were borrowing.
In cases where the evidence is a dead end (which is most cases), forensic investigators at the FBI or any of the private firms such as Mandiant, will search the victim system for the malware that made the hack possible. The malware itself can yield many clues as to the identity of the hackers. Once they have the malware, they then will begin a forensic analysis of the malware using tools such as Ida Pro or Ollydbg. These tools, originally designed as software debuggers, can disassemble the code and show each of its components/modules and the data flow as well as how it uses memory, registers, etc.
The screenshot below shows Ida Pro disassembling a virus. Notice that it is capable of disassembling each module and trace the data flow, giving us a clearer image of how the software actually functions (I'll be doing an article on Ida Pro in 2015, so stay tuned).
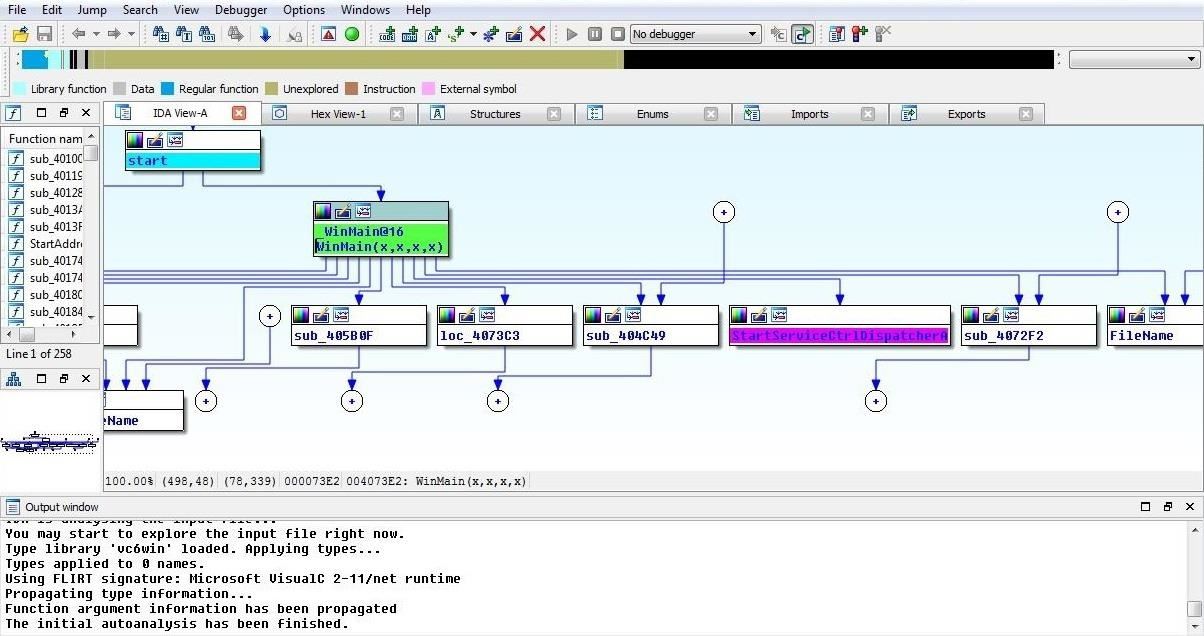
By using this type of analysis, the FBI and other forensic investigators can look for the fingerprint of the hackers.
Like any software development, hackers don't reinvent the wheel for each hack. They reuse existing code and repurpose it for a new hack. A skilled forensic analyst will disassemble the malware and then examine each module and compare it to known existing malware.
The screenshot below shows Ollydbg disassembling the same virus. Notice the list of executable modules in the upper right-hand window? These modules can provide the fingerprint of the hacker.
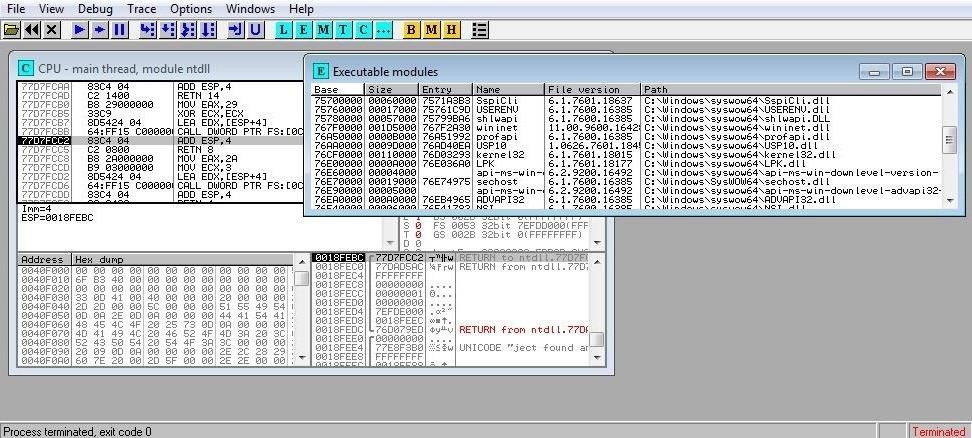
This is the process that led the FBI to conclude that the hack had come from North Korea. When they disassembled the malware, they found components that had been used by North Korean hackers in some of their recent cyber attacks on South Korea. Keep in mind, though, that although this type of analysis might be the best investigative tool in cases like this, it is circumstantial evidence. It does not provide a smoking gun, but says that the bullets found at the crime scene are the same type that the perpetrator had used in the past. This is far from conclusive, but it is strong circumstantial evidence.
Cyber attacks take place every day. There is nothing new about this attack other than the way Sony reacted and the worldwide reverberations. The ramifications are likely to be far-reaching into the world of international geopolitics, cyber warfare, first amendment rights, cyber intelligence, etc., but undoubtedly, it emphasizes how important hacking and cyber warfare will become in this beautiful, interconnected, brave new digital world.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























8 Comments
Greetings, something I found few days ago. Taken from a site where every group posts its doxs, hacks, victim letters, exploits etc.
"I Dear Mr. Michael Lynton (CEO of Sony Entertainment),
We shall first-off begin this message with an expression of sympathy as you have failed to release "The Interview" as you believe that hackers shall carry out a new operation to cause malicious damage within your organisation.
I would like to inform you that we all know the hacks didn't come from North Korea (we think everybody knows about this already).
What we would like to say is that by not releasing "The Interview", you are denying us the privilege of the Freedom Of Information Act (1966).
Unfortunately, due to your organisation panicking at first sight of trouble, we find this very cowardly of both yourself and your organisation (Sony Entertainment).
We know that Mr. Paulo Coelho has offered Sony Entertainment a sum of $100,000 for the rights of the movie; where he shall then be able to upload the movie onto BitTorrent.
Obviously, you shall not be responding to his generous offer - so please respond to ours with a public conference, we wish to offer you a deal...
Release "The Interview" as planned, or we shall carry out as many hacks as we are capable of to both Sony Entertainment, and yourself.
Obviously, this document was only created by a group of 25 - 30 Anons, but there are more of us on the internet than you can possibly imagine.
We are Anonymous,
We are Legion,
We do not forgive,
We do not forget,
Expect us. "
Either this statement really isn't coming from Anonymous, or they need to learn what the FOIA actually does.
The Freedom of Information Act (FOIA), 5 U.S.C. § 552, is a federal freedom of information law that allows for the full or partial disclosure of previously unreleased information and documents controlled by the United States government.
Last I check Sony Pictures wasn't even owned by an US company, let alone the United States government.
Don't overestimate the knowledge and grammar of Anonymous.
Thanks for that, CHH.
That makes this event even more intriguing.
Read this just this morning. Food for thought as to whether N Korea was responsible. http://news.techworld.com/security/3591637/think-north-korea-hacked-sony-think-about-this/
http://news.techworld.com/security/3591637/think-north-korea-hacked-sony-think-about-this/
It amuses me how they call themselves Guardians of Peace, and yet, use threats of terror to try and get their way.
I mean, come on, are they seriously that blindly stupid?
ghost_
(second time writing this, first time was a unsuccessful post, I should have copied it just in case.) Hey, I have been reading a lot of your articles lately. I find that the new innovative world will be focused on peoples ability to fend for themselves over the internet. So, I have been researching a lot of diverse programs (mostly through your articles) and you taught me how to find unprotected webcams, traffic light webcams, routers, ect. using Shodan. I also am currently downloading kali and will try and learn how to crack online passwords. I have decided to invest a chunk of my time everyday to learn a new program/ hacking tool. (for educational purposes of course) I am telling you this because I want you to know that you have a solid viewer constantly reading the threads you post. I hope we can further a conversation eventually, Until then, best regards from "jose".
If i reverse engineered a worm from NSA, and use those modules to build my hacking tool, and i used against to russia. will they point their fingers to NSA, right?
probably this might be happened.
Share Your Thoughts