Welcome Back !! TheGeeks.
SQL Injection (SQLI) Part-1
I hope you all enjoyed my previous article on Email spoofing, if not you'll can go to my profile and check it.
My this article totally different from previous one. In this article i'll be teaching how to find vulnerable websites for SQL injection.
SQL injection is a code injection technique, used to attack data-driven applications. The SQL Injection attack allows external users to read details from the database, so attackers can dump whole website database and find admin username/password details.
Note: Unfortunately we CANNOT SQLi attack on all websites. The websites need a SQLi vulnerability in order to do this technique.
Website URL need a parameter like php?id=4 / php?id=any number to inject.
For example: http://www.example.com/products.php?id=5 www.example.com/products.php?id=5 <= This type of website is needed in order to do this trick
To Find these type of website, Use Google Dorks- dork will advance search on google
Some Pakistan google Dorks list:
gallery.php?id= site:.pk
products.php?id= "+92"
cat.php?id= "+92"
default.php?catID="+92"
There is no limit in dork list, you can make your own google dork with keywords. Or you search on google for "New Google Dorks List" you will get many results.
Here you can find http://pastebin.com/Tdvi8vgK 7000 google dork lists
Note: These dorks will search out other countries websites Too, if you like to do this to Pakistan based websites ADD site:.pk at the end of the dork for example: about.php?cartID= site:.pk
Once you find a website, then you can check for SQLi vulnerability.
Put an ' (Apostrophe) at the end of the URL Parameter.
I found a website http://www.piil.com.pk/new.php?id=25
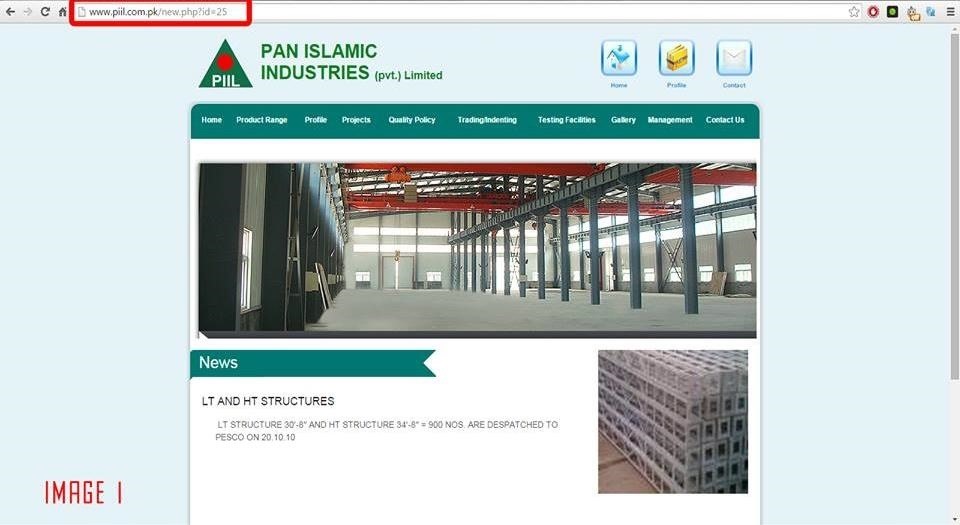
Let's, Check for SQLi Vulnerability, so i put an Apostrophe at the end of the URL Parameter.
http://www.piil.com.pk/new.php?id=25' (if you are using google chrome... Apostrophe will change to %27, it doesn't matter)
Now I found an error on this website!!!
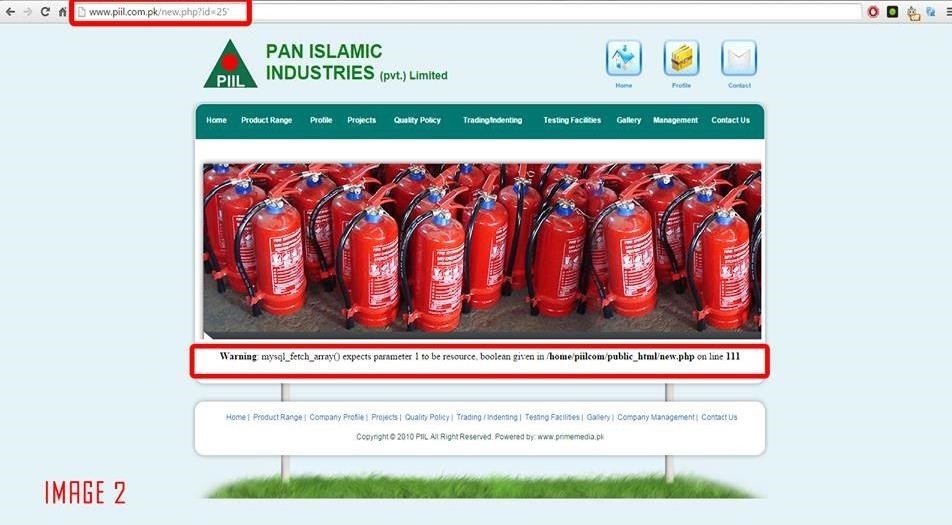
"Warning: mysqlfetcharray() expects parameter 1 to be resource, boolean given in /home/piilcom/publichtml/new.php on line 111"
Sometimes, we can see different SQLi error. Sometimes we cannot see this error at all, but it you will show some changes in website.
For example
http://www.psn.com.pk/index.php?page=gallery.php&id=519
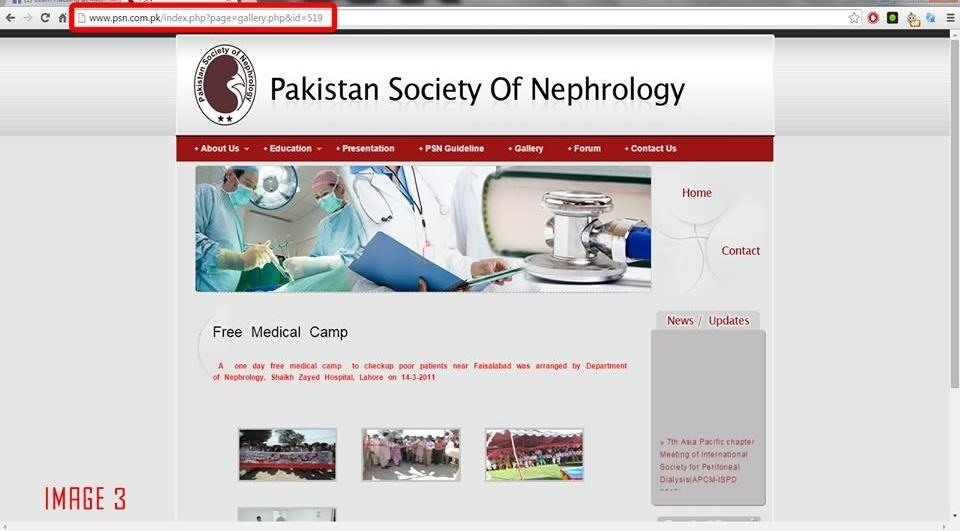
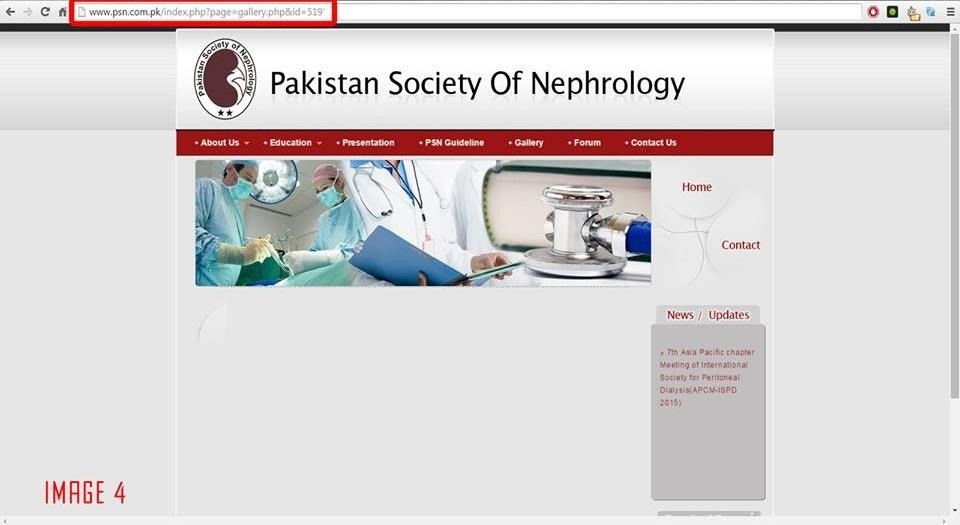
When i put an Apostrophe, The contents in that website got vanished
http://www.psn.com.pk/index.php?page=gallery.php&id=519'
thank you,
--ANAMIKA (TG)
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























13 Comments
Nice tutorial!
Thanks JOE SMITH
Can these exploits be used to get a remote shell on the server that the web page is hosted on?
Ninja243
In some cases, yes.
Are there any sites that I could practice this on?
You can install Metasploitable to practice on or DVWA.
Thank you
Ninja243
Oops nevermind
its cool tutorial but i dont think exposing this website here is legal...i really dont care but u know the rules around
Mr__nakup3nda
what if the website responds with "page not found" or it reloads only showing %27 on the end but without error messages and all in normal view?
Acunetix is showing sql vulnerability but links are not like "?php_id="
Help me what to do?
WOW!!! Superb list of dorks great article well i have also found a best Google Dorks List 2017 latest and fresh 100% working.
In this artical, you have mentioned site
http://www.psn.com.pk/index.php?page=gallery.php&id=519
is sql injection vulnerable. that is correct. I have found their database name is psn and they have following tables.
aboutus
admin_info
download
edu
edu_cat
executives
faq
gallery
gallery_cat
general
guide
history
news
newsletter
presentation
sponsor
userinfo
their admin username is Wadmin and password is 7ujm&%2K11 but they have htpasswd on admin page as well as I am not able to manipulate content of their index page. Can you please help me to achieve this?
Thanks
Elex
Share Your Thoughts