NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.
NMAP version 7 comes equipped with a ton of new scripts you can use to do everything from DoSing targets to exploiting them (with written permission, of course). The scripts cover the following categories
Auth: Use to test whether you can bypass authentication mechanism
Broadcast: Use to find other hosts on the network and automatically add them to scanning que.
Brute: Use for brute password guessing.
Discovery: Use to discover more about the network.
Dos: Use to test whether a target is vulnerable to DoS
Exploit: Use to actively exploit a vulnerability
Fuzzer: Use to test how server responds to unexpected or randomized fields in packets and determine other potential vulnerabilities
Intrusive: Use to perform more intense scans that pose a much higher risk of being detected by admins.
Malware: Use to test target for presence of malware
Safe: Use to perform general network security scan that's less likely to alarm remote administrators
Vuln: Use to find vulnerabilities on the target
For this tutorial, I will show you how to scan a target for vulnerabilities, actively try and exploit any vulnerabilities, test whether the target is vulnerable to DoS, and then finally launch a DoS attack.
Step 1: Download NMAP
Download nmap from https://nmap.org/download.html and follow the installation instructions for your particular Operating System. NMAP works easily on both Windows and Linux. After installing you will have NMAP and ZENMAP on your computer.
ZENMAP and NMAP are the same thing except ZENMAP provides you with a graphical user interface. For the rest of this tutorial you can chose to either run NMAP from your command line, or launch ZENMAP and enter the commands in the GUI.
Step 2: Run NMAP
Now that we've got NMAP installed, it's time to scan our target for vulnerabilities. As mentioned there is an entire category of scripts dedicated to finding vulnerabilities on a target. Invoking the following command will run all of the scripts against your target.
nmap -Pn --script vuln <target.com or ip> <enter>
*I always throw a -Pn in there just in case the target blocks ping probes, although it's optional.
Step 3: Review Results
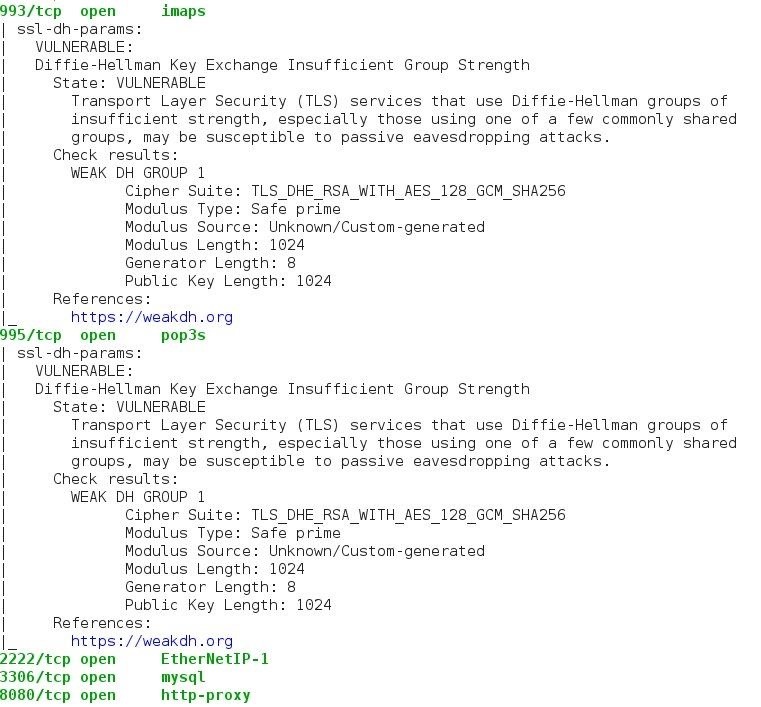
After your scan completes, review NMAPs output to determine what vulnerabilities were found. It will list it's findings along with applicable CVEs and links to any exploits that exist in Offensive Security's Exploit Database.
Use NMAP to Actively Exploit Detected Vulnerabilities
As mentioned, you can also use NMAP's exploit script category to have NMAP actively exploit detected vulnerabilities by issuing the following command:
nmap --script exploit -Pn <target.com or ip> <enter>
Use NMAP to Brute Force Passwords
Nmap contains scripts for brute forcing dozens of protocols, including http-brute, oracle-brute, snmp-brute, etc. Use the following command to perform brute force attacks to guess authentication credentials of a remote server.
nmap --script brute -Pn <target.com or ip> <enter>
Use NMAP to Test if Target Is Vulnerable to Dos
Use the following command to check whether the target is vulnerable to DoS:
nmap --script dos -Pn <target.com or ip> <enter>
This will tell you whether the target is vulnerable without actually launching a dos attack.
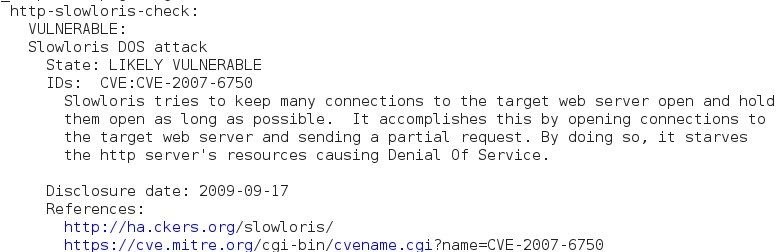
Use NMAP to Perform DOS Attack
Use the following command to perform an active DoS attack against a target for an indefinite period of time:
nmap --max-parallelism 750 -Pn --script http-slowloris --script-args http-slowloris.runforever=true
These are just a few very cool features NMAP has to offer. NMAP is very noob friendly so get yourself a copy.
On a side note, this week I was tasked with identifying vulnerabilities in a company's server as apart of the interview process Thanks to NMAP, I was able to identify, and then successfully verify, their server had the POODLE issue. This was something (shockingly) the company was not aware of. Nessus, Openvas, Acunetix, and BurpSuite did not identify the vulnerability and it did prove legit.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.





















16 Comments
Nicely written. +1 A few commands you left out though which I think you should have mentioned.
thanks. what other commands would you have liked me to mention? There are tons of commands for nmap. This post was more about category based scans.
I would take note of your use of the -T3 argument. It is essentially the default Nmap scan intensity and there is no need to specify it.
But overall the post was well written and easy to understand.
TRT
hmm i didn't realize. thx!
I think -sS falls under those categories, and -sU
yeah --script default will take care of the basics for you too :)
Thanks for the guide. Well explained and just the scripts I was after. Are these the common scripts you would run when scanning networks? What I mean is are these the scripts you would take with you on a job?
Yes, definitely, minus the actual dos attack unless they don't mind you taking them offline. You'd be using nmap during a pentest anyway because you need to map the network. The fact that you can now do all this extra stuff with it too is awesome!
Ok thanks, will be using this more often. I knew nmap was good, but I didn't realize it was this good. Another keeper in the good old digital tool box.
yeah it's getting better with every new release. The creator and I grew up in the same hometown, went to same HS except he's two yrs older. He's got a lot of very talented pple working on it w him and he's excited about the advancements. :)
if u will bypass AV detection, use -f option
nice. I'll add that to the tut
Love it.. Thanks man.
Awesome!
what command will you run if you want set a Dos attack at finite period of time
nmap --script dos -Pn <target.com or ip> <enter>, How does this command work. And does it launch a DoS attack? I'm a noob...
Share Your Thoughts