What is Google Dorking?
Well, simply put, "Google Dorking" is just an efficient way to utilise keywords in order to perform very specific searches on a given subject. In this case, one would look for websites/servers that are vulnerable to attacks or are configured improperly by using specific search criteria that should yeild results, should it find matches to known mistakes/errors in a website or webserver.
Let's face it, some admins leave security settings as their default without much thought, when say they set up a MYSQL database, and that's where hackers find an opening.
The keywords used are varied and many, and when used properly can bring you straight to a website riddled with holes. A recent article at Gizmodo details how hackers found an unprotected FTP server and stole 43k social security numbers of students and faculty.
Step 1 Your First Dorkage
Right, what's the point of theory, when practice just kicks so much ass? Let's fire up guglz in a new tab/window and type this in:
admin account info" filetype:log
The very first result that I got was this:
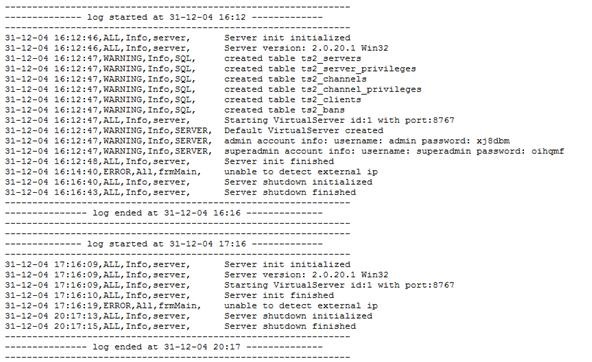
As you can see, we found a server log. Neat.
Let's 1-up ourselves...
Type in:
"# -FrontPage-" ext:pwd inurl:(service | authors | administrators | users) "# -FrontPage-" inurl:service.pwd
The first website I got was:
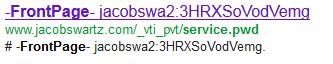
And the address is: http://www.jacobswartz.com/_vti_pvt/service.pwd
takes you to a username and password file.
Now if you just delete the service.pwd bit, and leave - http://www.jacobswartz.com/_vti_pvt/
It will take you here:
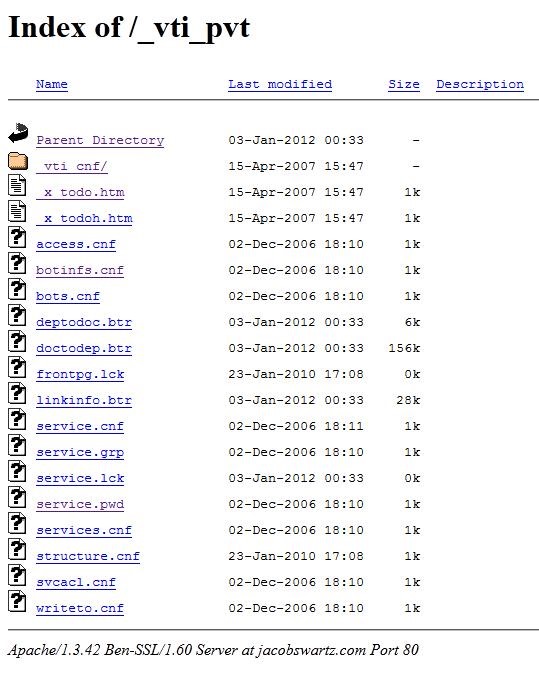
A whole directory. Yay.
Another example?
"index of/" "ws_ftp.ini" "parent directory"
Third result from the top, takes us to the parent dir of a Virginia University webpage.
So, even though what we did right now was searching for stuff, we have accessed some very low key areas of a few websites, but I am assuming the authors of those pages intended them not to be public.
To be perfectly honest, you can spend hours running different queries, and come up with f*ck-all, but you can also get lucky. If you know specifically what you set out to do, build your queries on that thought. Then find something that looks like it's prone to an sql injection (see pic).
...or another type of exploit and pound away.
Now that (hopefully) I have gotten you interested in this, why don't you check out the links below for a HUGE listing of dorking queries, which you can either use as-is or improve upon or adapt to your needs! Go forth and wreak havoc!
Nah just kidding, as with all hacks/exploits, don't do anything to anyone that you don't want done to you.
But... I encourage you to learn while utilising this technique. After all, smart people learn from the mistakes of others.
Should you find something missing from the article, or if you wish to express your critique, please leave me a comment at the bottom of the page.
Cheerio!
Mr.F
Resources and Further Reading
Also check out this WonderHowTo link to a video on how Dorking works.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























6 Comments
So nice and simple. Easily the most thorough and simple guide on the web, thank you :). It's exactly how I wanted it written :D.
Thanks. I was a little worried I was not thorough enough in terms of practical usage.
Nawh, it covers the basics. I can see where you mean "not thorough" in the sense that it doesn't supply many example dorks. But those should be left to the user to figure out. If they can't figure out how to google intext:@gmail.com etc for queries, the people shouldn't be "hacking" IMO.
Those who can't hack - threaten to bring down servers with DOS attacks from their home pc. *chuckle*
Haha, that made me think of being on Xbox Live with the "Im gunna hax u and hostboot u" kids xD. With their enormous botnet of 1 computer xD.
Oh noes... All ur achievemants are belong to them. xD
Share Your Thoughts