A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop.

Although the movie did very poorly at the box office, I thought it was pretty good movie, as hacker movies go. In particular, the hacking was relatively authentic. One of my pet peeves about hacker movies is that Hollywood always makes hacking seem so fast and simple with lots of swirling, animated, geometric shapes. Brute-forcing passwords takes seconds instead of hours, days, or weeks. In Blackhat, we get a more realistic depiction of hacking... maybe that's why it failed at the box office?
Reportedly, Kevin Paulson served as the hacking consultant. If you haven't heard of Kevin, he was the guy who hacked the Los Angeles radio station KIIS (102.7 FM) so that he could be the 102nd caller and win the Porsche 944 S2 they were giving away. He ended up spending 5 years in prison and given a three-year prohibition on accessing the Internet (heaven forbid, that judge was inhuman). Now he is a senior writer for WIRED Magazine.
The Hemsworth character is loosely based upon the life of Max Butler (aka Max Vision). As many of you know, Max was a grey-hat hacker who was sentenced to a 14-year prison term at Lompoc and is cooperating with CERT to catch hackers. I have made reference to Max in a few articles, most particularly in my script to find vulnerabilities. In the movie, this Max-like character is released from prison to help the U.S. government stop a hacker who has taken down a nuclear plant in China.

Interestingly, the hack is almost eerily identical to the Stuxnet worm that the NSA perpetrated against Iran's uranium enrichment facility. Namely, it attacked the PLCs of the nuke plant's cooling system causing it to overheat, meltdown, and release radiation.
Throughout the movie, the character portrayed by Chris Hemsworth employs command line hacking techniques that reflect the real world of hacking (Chris Hemsworth must be the most attractive person to use a command line). In the scene below, he examines the contents of a thumb drive in Linux/Unix. Notice the command "ls /media" in this BASH Shell.
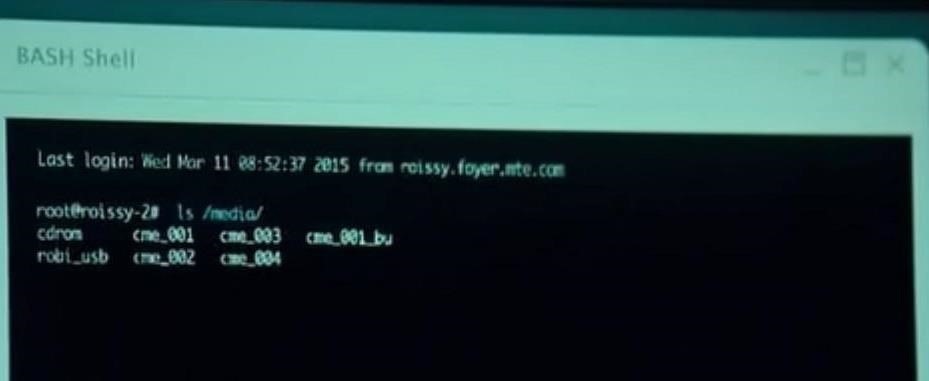
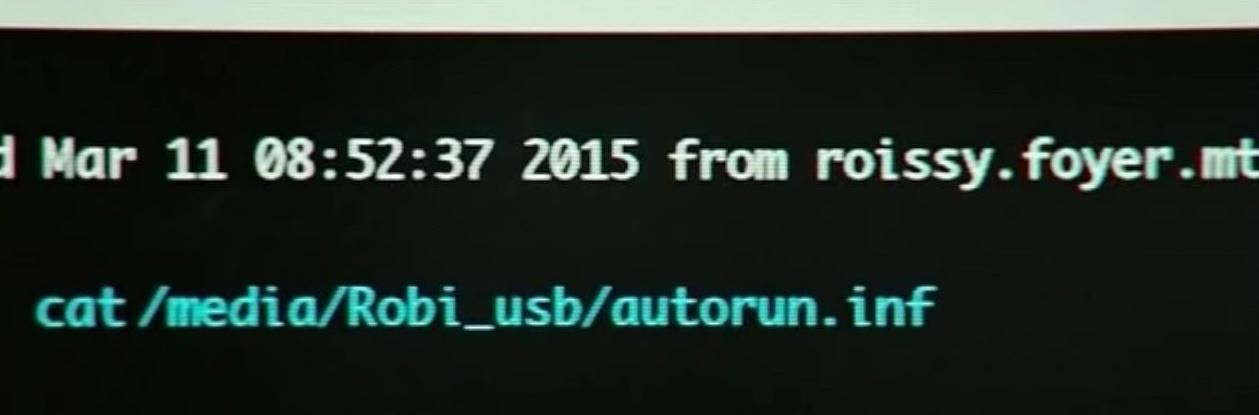
Then, he "cats" the file found at "/media/Robi_usb/autorun.inf."
He then finds the malware, and instead of finding swirling, geometric objects, he instead finds the malware in the more authentic formats of both hex and ASCII.

Eventually, Hemsworth's character needs the password of NSA's Black Widow (a special NSA program capable of reconstructing destructed or erased data) to reconstruct the malware of the bad guy hackers. Without the Black Widow, he can't track the bad guys.
When the NSA assistant director refuses them access to Black Widow, he social engineers him by sending an email from his boss, the NSA director, to him telling him he needs to change his password. He includes a new "Password Security Guidelines" PDF. Although it unrealistic to believe that the assitant director of the NSA would download a file to his machine, this type of social engineering is at the heart of so many of the major hacks in recent years (RSA, NY Times, Target, OPM, etc.). When he downloads the guidelines, they contain a hidden keylogger, so that when he changes his password, Hemsworth's character captures the keystrokes and thereby gets access to the Black Widow decrypter.
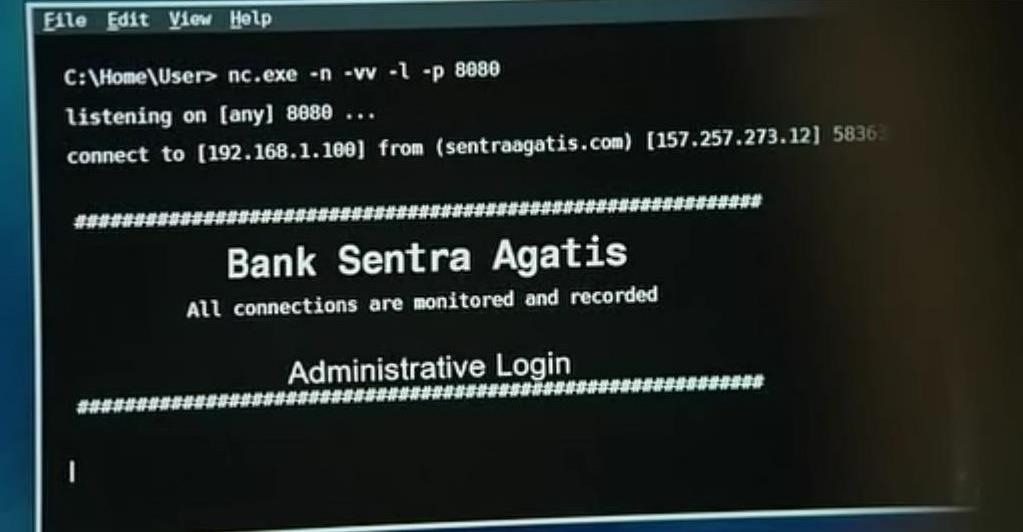
To get access to the bad guys' bank accounts and their ill-begotten money, the Chris Hemsworth's character has an inattentive security guard at the bank "seduced" by a beautiful Chinese network engineer to plug in her thumb drive to a networked printer to print some documents. The thumb drive has a Netcat listener on it that autoruns when the thumb drive is inserted and connects to Hemsworth's Netcat listener as seen below. See the netcat command in the screenshot below?
nc.exe -n -vv -l -p 8080
It's finally nice to see hacking portrayed realistically by Hollywood, but unfortunately, few people saw it. If you have a couple of hours and are interested seeing a moderately good movie with some of the most authentic hacking scenes Hollywood has ever produced, check out Blackhat.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























29 Comments
Great post! I really enjoyed this movie when i saw it in theaters. It's too bad it's not rated better though....and lol I thought the same thing when the power plant was in meltdown (stuxnet).
I saw this movie, and I liked the keylogger bit, I expected there to be a bit more "bruteforcing and malware making" and less "simple linux and unix commands". Nevertheless the movie portrays something quite realistic.
I do hope Hollywood continues with this more realistic style of hacking.
I only saw the first half.
I liked the hacking stuff (and the main character being a badass who keeps training his body when he can't train his brain), but the acting and flow of social interaction was so poor that I got bored.
It's the story of my life--minus the physical parts.
You got out of prison because your unique skills were required by the government of a country different than yours?
Yup... or at least I walked out of my house to get my cat out of the tree. :P
I have done that too!
That's basically whay Kitten said.
In the catland.
Im thinking more like Linux and tools never changed the whole time he was locked up. He must of used his laptop in his cell everyday to hack AP's in the cells next to him and keep up on his training..
Basic Linux commands have not changed in many years.
Remember at the beginning of the movie when they found the Android phone in his cell and they placed him is solitary for increasing the value of his fellow prisoners commissary accounts? He obviously was practicing with that.
I guess I should watch it again and pay more attention this time. I have put it on 3 times and watched it complete 0 times.
nice, I'm going to watch it now :D
POTENTIAL SPOILERS
I watched this movie a while ago; I was also impressed with the accuracy of the hacking shown.
However, I didn't like the logical fallacies present within the film. Early in the movie he's told that he will essentially have a babysitter and then very quickly that seems to dissipate and he's seemingly spearheading the investigation.
His babysitter literally gives the hacker his mobile phone? The same mobile he's using to keep a GPS tag on him?
That said, I did like the prisoner side of him. The stabbing scene was fairly primal.
It was an okay movie, good in the hacking sense, actual plot though? Needed work, it feels like they were confused as to what role the hacker should play in the film.
ghost_
Awesome Movie!
You should watch Mr. Robot, and tell us your thoughts
I have. I love it!
Yeah Mr. Robot is great!
Mr. Robot , a new TV series also depicts some real life hacking and all..
Yes, I really like Mr. Robot! Real life hacking and the hacker is hacking for good!
As I've watched Mr. Robot Episode 1 & 2 (the only ones that came out yet) I've tried harder and harder to just try to get a glimpse of some of the commands he is using. I basically tried to do what you did in this article (take pictures of some of the things used in the acting and compare it's accuracy.) I am amazed by how realistic this show seems and I beg of you to help explain some of the tactics used by "Eliot." For example how he cracks the passwords (I've read all of your articles and I'm still confused, although I aren't the brightest one xD)
But in conclusion, I believe everyone here can agree Blackhat and Mr. Robot would win the award for the most legitimate Hollywood Hacking. If only you Master OTW could help explain accurate this is, I'm sure everyone would love to hear.
"Esmail hired a cyber-security engineer to provide the data that appears on computer screens during various hacking scenarios, and accurate sound effects are key, too—you aren't hearing random blips and beeps." That is from http://www.fastcocreate.com/3047491/how-the-makers-of-mr-robot-cracked-the-code-of-a-realistic-hacker-drama which is a very interesting article. Thanks in advance Master OTW
Most of it is good, but he uses some commands that do not exist .
I'll plan on doing an article about it after a few more episodes.
Maybe he's using aliases!
Blackhat went down here b'coz Mann is known for Drama and action, not for Tech n all, he tried but it was all a hush-hush.
Next point here is over drama. Stuxnet basically infected the enrichment process and rest all the inner functioning of a Nuclear plant is analog, so basically one can't. There r many scenes in d movie where u can raise eyebrows ?? But comparatively to all the past movies like Hackers the bar is rising but still not upto the mark.
He just to tried to depict the possible consequences of digital world into physical world. Moreover, the real or more relative hacker world is information driven not action driven. Information is the newest currency that floats everywhere.
AND thanks for the link above.
http://www.imdb.com/title/tt3042408/
I've just watched "Who Am I" and I loved it, as a movie and as a hacking related video. I still don't know how reading machine code relates to Nmap and shutting the neighborhood's light system, but still, it's great :D
(I fell for he "Fight Club" ending, didn't expect such a twist, the movie socially engineered me)
damn good movie man...
Loved this movie but it appears that Hollywood can't get past the ending gun fights :c
finally some real hacking after nmap in matrix and die hard 4.0...but hemsworth who potrays a skilled hacker is using netcat? anyone on this post can do it ;)
Share Your Thoughts