As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their way into and out of these systems will be in great demand.
More and more, international relations are done and dictated by hackers who work for national militaries, espionage, and security organizations. EVERY government now employs hackers to spy, steal, and disable their opponents.
Probably the best example of how international relations are being dictated by hackers and hacking is the worm that became known as "Stuxnet."

Stuxnet is/was a worm that by all indications was probably released into the wild by the NSA in 2009. The U.S. government, worried about the rapid advance of Iran's nuclear development program, was being pressured to take military action to stymie the developments. There was precedence for a stealth bombing attack, similar to what Israel conducted in 1981 against Iraq's nuclear power plant. Such a "kinetic" attack would likely cost many lives, provoke international outrage, and possibly elicit a counterattack from Iran. Could there be a better way?
The NSA and other national security leaders in the U.S. believed there was. What if the U.S. could hack into the nuclear facilities and disable them?

As it turned out, that is exactly what happened. The NSA was able to hack into the nuclear facilities in Iran and by messing with the controllers of their centrifuges, set back the Iranian nuclear ambitions by several years. It was this hack that made possible the present warming of relations between the U.S. and Iran and the proposed lifting of sanctions that was announced by President Obama on April. Stuxnet was most sophisticated malware in history.
Here's How They Did It
The NSA knew (using good, old "cloak and dagger" spying) that the Iranians had purchased programmable logic controllers (PLC) from Seimens of Germany for their centrifuges (a centrifuge is a device that spins very rapidly and precisely in order to enrich, in this case, uranium). They then acquired the specs for the Seimens controllers and set to work.
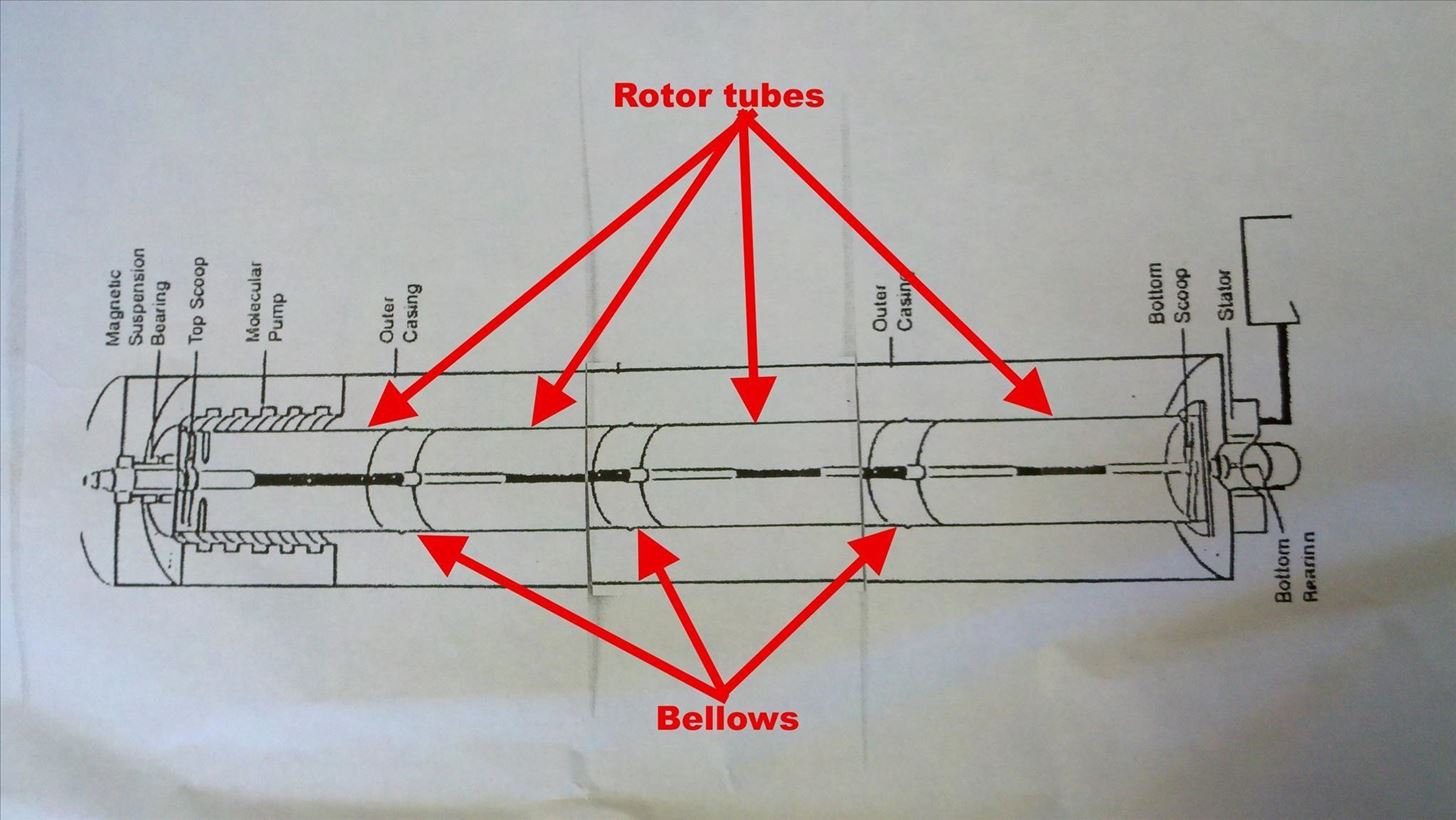
The NSA developed a worm that used the zero day vulnerability of Microsoft Windows systems that became known as MS10-046. This vulnerability exploits the processing of shortcuts/.lnk files. This vulnerability is nearly identical to the one we used here in this tutorial.
The worm was then released into the wild and infected machines throughout the Middle East and the world. Since the nuclear facilities in Iran had no Internet connection, they were counting on infecting so many systems that eventually someone would walk the worm in through a thumb drive or other removable device. In fact, that is what happened.
Once inside the Windows operating system, Stuxnet then targeted the operating system of the Seimens PLCs.
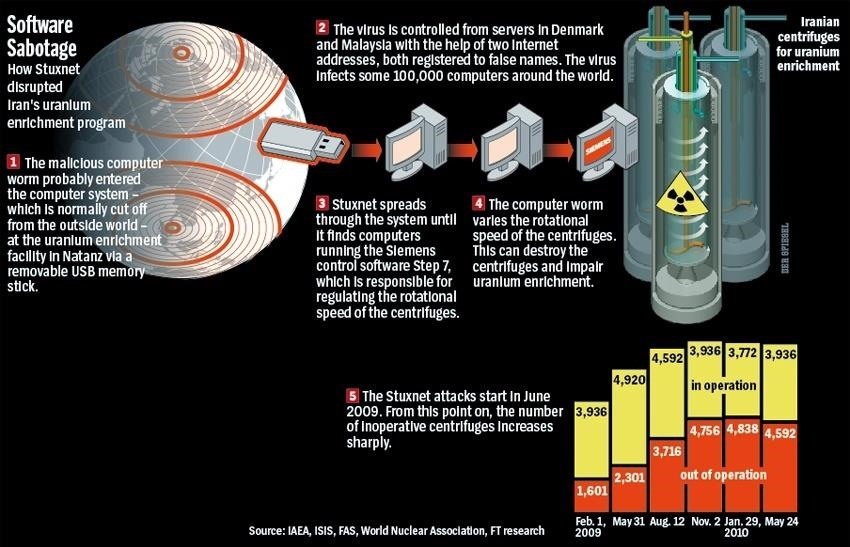
One of the most interesting parts of hack is that it used signed drivers to get past Microsoft's requirements that all drivers must have a certificate of a legitimate software company. As you know, Microsoft's operating systems secure against malicious software masquerading as new drivers (which then have access to the kernel) by checking the driver's certificate. Stuxnet initially used the certificate of Realtek and when Verisign revoked Realtek's certificate, Stuxnet then switched to the certificate of a little known Taiwanese company known as JMicron. This clearly illustrates the weakness of this certificate-based signing system.
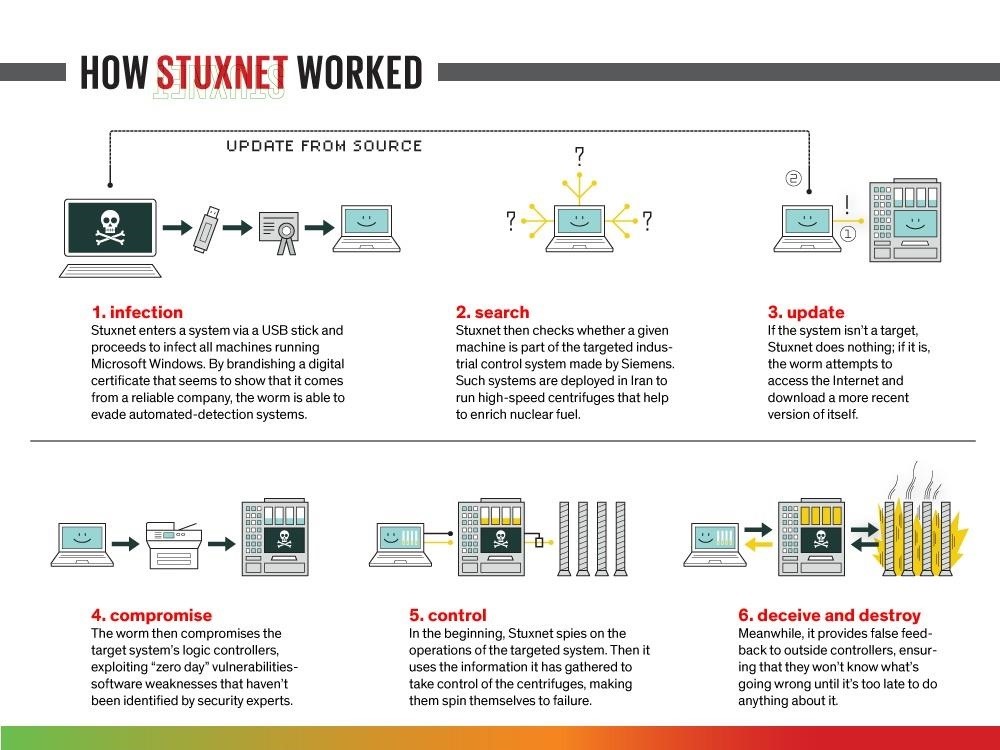
The Stuxnet worm, once it had penetrated the Microsoft operating system and then the PLCs' OS, had the centrifuges spinning out of control, eventually leading to their destruction. Since Stuxnet had penetrated ring 0 of the operating system (kernel level), it can control what the operating system reports to the user. As such, the operators of the plant were totally unaware of anything going wrong until it was too late. In this way, the Iranians remained unaware of the hack and the end result of months and years of work was improperly enriched uranium that was not suitable for use in peaceful nuclear applications, much less nuclear weapons.
Stuxnet was the MOST sophisticated hacking attack in the world of cyber warfare yet known, but I am certain it has and will be superseded by other attacks soon. One more reason to keep developing your hacking skills here at Null Byte, my rookie hackers!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















14 Comments
Have been following the stuxnet tale for quite long now, glad you made a post about it!
Most sophisticated attack has always yet to come...
good read.
That's actually very intelligent.
They did get a little lucky considering not many people would have gotten access to the internal systems. Still, I can't come up with a better attack.
Interesting article.
nah dude i used ++686.processor pipe commands to control the reactors liek a hard drive. i have many different viruses if you want to take a gander speak to me frankly in secondlife. gunmaker is the account name.
If, for example, you had an admin account on a compute and could disable antivirus, but certain Internet adresses were blocked and just IPs were marked as "uncategorised", what would be the best way to get the admin password or a meterpeter session (I can run the exploit but it can't connect back). Would a key logger work? If so, what do you recommend? Thank you for your tutorials and for the interesting article!
And i want the key logger to be able to record the passwords of users logging in to a domain (the admin account is local)
Hey OTW:
First time posting, Hey all, just wanted to know if you had any tricks for gaining access to Microsoft SharePoint 2010 and if so, would you direct me to which article you have created pertaining to this topic.
i think agent.btz was more complicated
Thank you for that opinion, but what makes Stuxnet unique is that it targeted a specific PLC on a specific system that was air-gapped. agent.btz, on the other hand, struck generic systems attached to the Internet. That's a much easier task.
This is an awesome article! It's great to hear about hacking being used for good things. So many people instantly think "illegal" when they hear the word hacking. However, hacking can also be used by the Government to stop terrorists from destroying the world! The way that they did this hack is pretty cool. They had it infect OSs (without being detected) and then transfer to USBs automatically. (Again, without being detected) And then transferring onto the computer in the plant, and infecting it automatically, without throwing anything that could alert the computer operators. A very brilliant hack indeed.
Well explained Master OTW
nice article i enjoyed !! @OTW
Just a few things to add:
You didn't said it clearly, but the main goal of the hack was not to destroy the centrifuges, but to make them run randomly during the night for the reason you said. It was a side effect that the centrifuges ran out of life faster. US didn't wanted to destroy them because until the hack was not discovered, Iran could loose research time and by the same time, delay the embarrassing explanations after the long forensic analyze (they had to change all their IT)
Also another fact is that the malware has found lots of false positives while trying to identify the right computer to infect, so we found the most elaborated malware (the 2nd downloaded part) on the home computer of peaceful civilians, quite funny.
I'd also add that the cost of the malware itself (without the needed informations to make it) was about ~2Millions$ on the current market, the biggest part taken by 0-days, 3 at least).
Anyway great article :)
ps: i know, bad english sorry :<
Share Your Thoughts