For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.
In the last article, we spent some time going over the concepts of onion routing and how it can be useful to you. Before that, we covered the concept of deep web. In this article I will talk about Tor hidden services, what they are, and what they can be used for.
Tor Hidden Services
A Tor hidden service is simply a web server that runs locally and only takes requests from inside the Tor network. It is bound to localhost, so it is not visible or accessible to the outside Internet. Hidden services do not require registration or processing because they are anonymous, so there is no domain name to purchase and use. You may simply set up a web server, and point it to your loopback address. The network will then generate a Tor host name to be located by. Knowing this also explains the sometimes varied uptime of hidden services in general.
Due to the nature of hidden services being anonymous to a degree, the content can be extreme. Like anything in life, please exercise caution, but enjoy yourself. You will find hackers, crackers, porn and political discontent. You will find places to have your hashes cracked and places that sell drugs. It is the wild west of the modern day Internet. Viewer discretion is advised.
Setting Up Your Own Hidden Service
If you have gotten this far in my series, you are probably interested in setting up your own service. This can be for your friends or even to share things with random people across the world. You could even encrypt files and place them on your hidden service to be picked up by others, adding extra security.
Step 1 Get the Tor Client
In the previous article, we downloaded and used the Tor browser bundle. This works great for simple web browsing, but if we want to operate a hidden service, we need to download and install the actual Tor client. The installation is a simple matter in most cases, but might require a few extra steps for Ubuntu/Debian users.
After we're finished, we have the Tor client running on a default port of 9050 and are ready to go!
Step 2 Set Up Your Web Server
If you are using Linux, your absolute best choice for a web server is ThttpD. You may use more mainstream servers like Apache. Windows users will find a good home there, but in this tutorial, we will focus on ThttpD.
$ wget http://www.acme.com/software/thttpd/thttpd-2.25b.tar.gz
$ tar zxvf thttpd-2.25b.tar.gz
Move into the new directory to configure and compile from source:
$ sudo ./configure && make
$ mkdir hidserv; cd hidserv
$ cd ..
$ ./thttpd -p 5222 -h localhost
Tip
- Adding a semi colon to a command allows us to follow it up with another command!
The last command started the web server and told it to use port 5222 and localhost as its host. You can click this link to see if it worked. If you see the page below, you are on the right track.
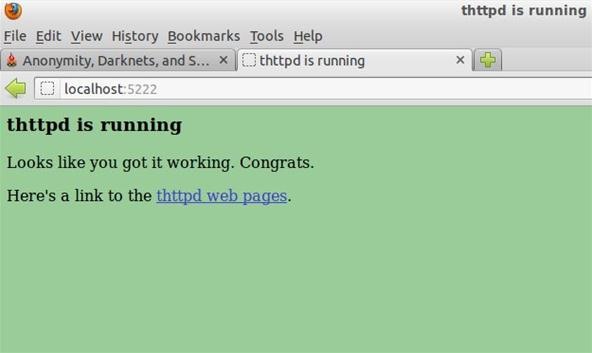
That's it! We are now ready to finish up and connect with Tor!
Step 3 Turning Your Web Server into a Hidden Service
Navigate to your /etc/tor directory and open the file named torrc with your favorite editor (I use vim). This is a configuration file for letting Tor know you are running a hidden service. Scroll down about halfway until you see the title:
### This section is just for location-hidden services ###
And add the following lines under that:
HiddenServiceDir /home/username/hidden_service/
HiddenServicePort 80 127.0.0.1:5222
Username is the name you log into on your Linux box with and hidden_service is whatever name you wish to give it.
Now restart Tor. When it starts back up, it reads the file torrc, follows the instructions, and bootstraps your service into the Tor network. It will then automatically create the 'hidden_service' directory that you specified (if necessary), and it will create two files there, private_key and hostname.
The private key is identical to the idea we discussed in our GPG article. Keep this key secret! Anyone who obtains it can impersonate your hidden service!
The hostname is a URL created by the network used to identify you from other services, it should look something like uy4htf7ssvv3gfh8g.onion.
Conclusion
This was just a taste of what's out there. From here you can branch out to configure your service however you need it. I implore you to spend some time on the Tor network and see what is all there. However, for the more savvy and security minded, Tor is not the best choice. In my next and final article in this series, I will go over the Invisible Internet Project known as i2p. The development of i2p started where Tor left off, improving upon its base and adding more features for the security minded.
UPDATE: Continue to Part Four to Learn About the Invisible Internet Project (I2P)
Questions? Concerns? Leave me a comment or drop by our IRC channel and say hello.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























7 Comments
Nice article, but I wish you'd go into more technical detail about how hidden services work. If you look into it, it's pretty cool and the anonymity is surprisingly robust.
It's still unclear to me why you present Tor as a kind of half-baked solution and hold up I2P as the real stuff. Both work in much the same way with regards to location-hidden services, but these days Tor is getting most of the research attention.
Finally, .onion addreses are lower-case, not mixed-case.
Onionland was more of an after thought on tor. I2P is designed to do what onionland does and does
it in a more eligant fashion. There is podcast on the history of IIP/I2P and Tor. (infosec podcat ep 569)
Podcast TL;DR:
When the EFF was face with choosing I2P vs Tor for a anonymity network to endorse they chose tor.
why? the developers of i2p used pseudonames while the main developer of tor was more open
about his identity. Tor at the time seemed much more professional while the I2P developers
were more of a "ragtag" group of mysterious hackers.
I2P is amazing on the technical level and onionland cannot come close to what I2P provides.
Here is an I2P torrent of said podcast
http://tracker2.postman.i2p/index.php?view=TorrentDetail&id=15905
As your average joe would you advise i not go any further?
I've heard that ThttpD might reveal your IP address or other identifying information, in case of 404 pages.
I use PIA (Private internet Access) VPN every day. Very simple to use and I've had no problems at all.
oh! come'n !!! one can't trust these VPN providers. They pour yr data as soon as authorities will search 4 u.
Share Your Thoughts