With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases.
Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been hacked by Chinese hackers and over 4 million personnel records of employees of the federal government were stolen. Not only were these employees' personally identifiable information (PII) stolen, but also their security clearance background checks. These background checks might have been the most critical information. It appears that the Chinese hackers had been there for over three (3) months before being detected. One has to ask, why would the Chinese, who are usually after intellectual property and state secrets, be interested in this information?
There are a couple of features of this hack that make it interesting.
First, it once again emphasizes for us that hacking is a key element of international relations in the 21st century. Nations are using hacking to spy and conduct low-level cyber warfare against each other EVERY day. Each nation has assembled teams of elite hackers to attack their adversaries.
Second, the Chinese were able to penetrate the much touted "Einstein 3" defense that the U.S. implemented just 3 years ago. This clearly demonstrates that given enough ingenuity, persistence, and creativity, any defense can be overcome and penetrated.
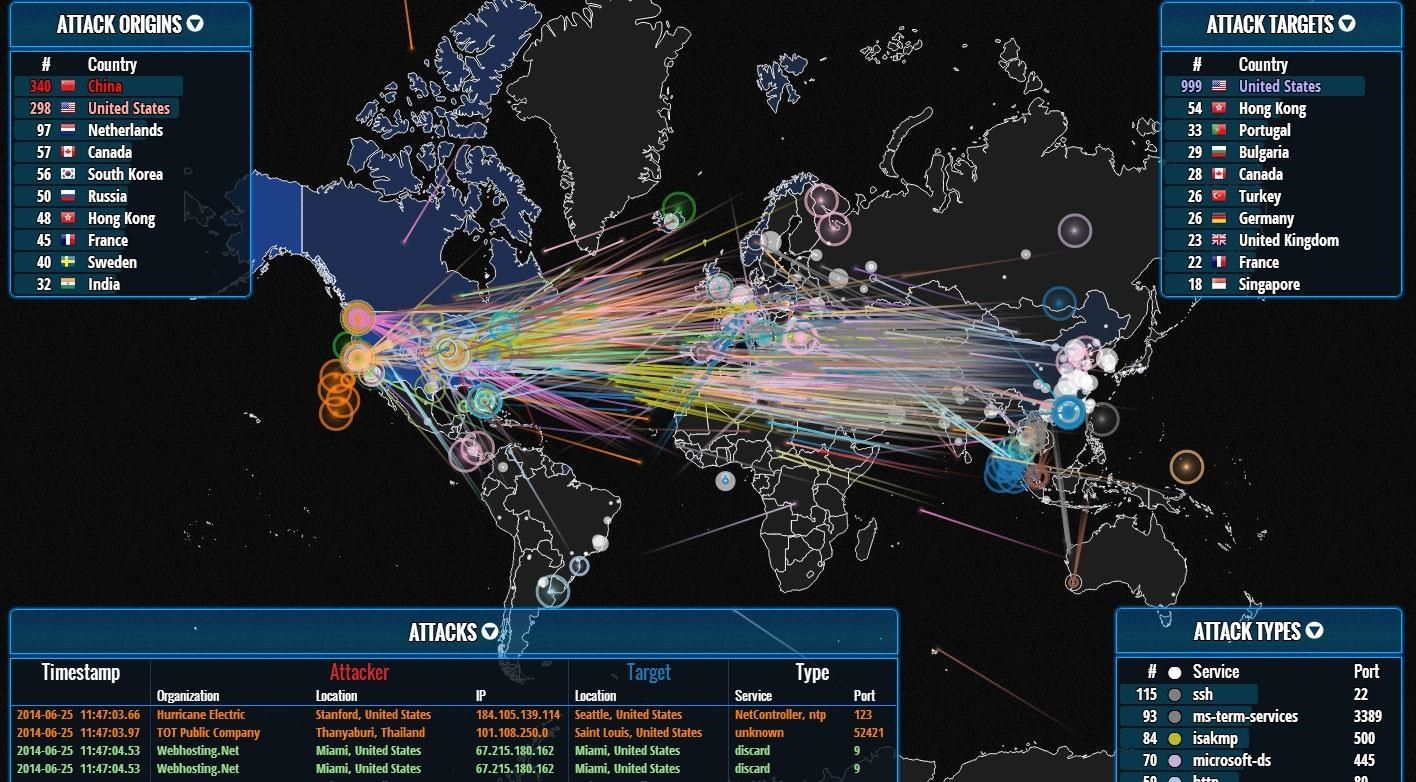
What Is Einstein 3?
Einstein 3 was a start-of-the-art perimeter defense developed first in 2012 for the U.S. government to protect against exactly these types of advanced persistent threat (APT) attacks. At a cost of nearly $1B, it is a signature-based system that includes all the known attack signatures and includes signatures supplied by the NSA that they find by hacking into the U.S.'s adversaries exploit development projects (every nation has exploit development projects).
When the NSA successfully hacks into another nation's hacking team, it captures their exploits and feeds the signatures into Einstein 3 even before the exploits are used. In addition, since NSA is peeking inside all the world's Internet "pipes," it can see attacks before they have even hit their victims. This information also was being fed back into the Einstein 3 system. In summary, Einstein 3 is a signature-based IDS, similar to Snort, but on steroids.
I think IT security professionals can take at least two lessons from the failures of Einstein 3.
Defense in Depth
First, perimeter defenses are NOT enough. Defense MUST be in-depth with multiple layers of defense. Once the hackers penetrate the perimeter, there must be other layers of defense to provide obstacles to reaching their intended prey. In this case, if OPM had simply been looking for data flowing OUT from their system, they might have detected the breach before it was too late.
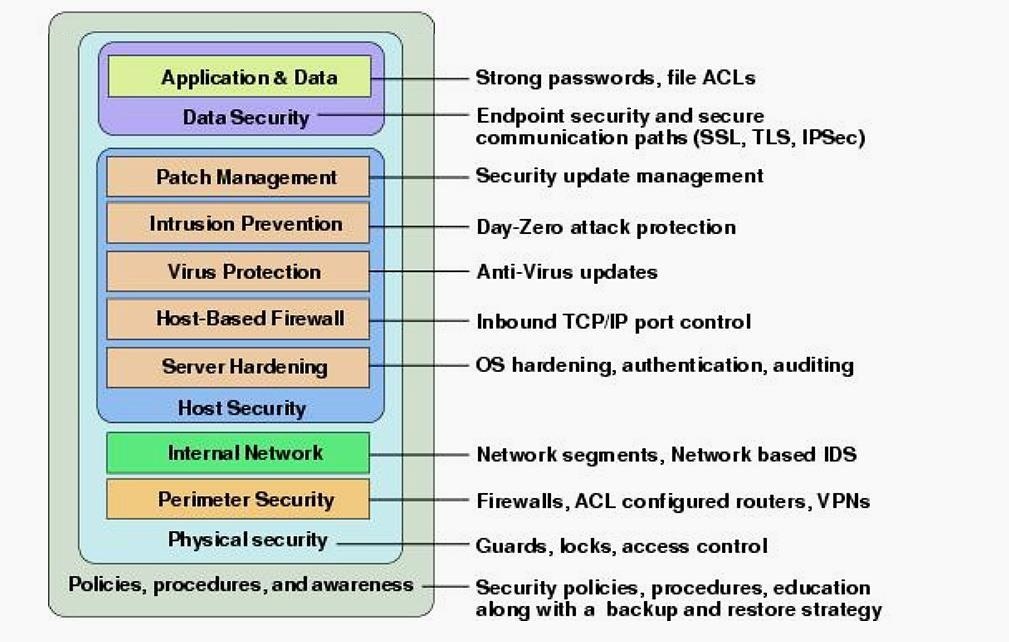
Signature-Based Systems Are Inadequate
Second, signature based defense systems are an antiquated way of defending information and networks. Security admins need to employ more heuristic and anomaly-based approaches to perimeter defense. This would include looking for more than just signatures, as attackers can easily take the same attack and change its signature. Furthermore, signature-based attacks are ineffectual for detecting zero-day attacks.
Next generation perimeter defenses must include effective heuristics, not limiting themselves to a static database of exploit signatures like Einstein3 did, but instead look at file analysis and behavior among many variables to alert system admins that the code might be malicious. In essence, to effectively defend the perimeter, a type of artificial intelligence (AI) must be developed that understands what to look for. Think of this type of intelligence as incorporating the knowledge and skill of a malware researcher, but automated and capable of doing its work in milliseconds, instead of weeks or months (I hope to start a series on malware research before the end of 2015). Granted, this requires significantly more CPU cycles to accomplish, but it is the ONLY way to protect these crucial systems. Without such protection, hackers will have a field day and we can expect more and more breaches of confidential information such as this one.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























10 Comments
Fascinating read! I really enjoyed this, OTW.
Nice read, some of this makes me feel as if real life would be happening into a movie script.
Is it justifiable to question the legitimacy of these attacks? While I do not doubt it's possibility, it seems for too convenient at a time where the government wishes to take totalitarian control the internet...
So Einstein 3 was really just one of those projects about perimetral defense.
Thankyou for posting, great synthesis as always, helped me figure out what was going on with far less words than the others.
A thought-provoking read. As always I enjoy reading your articles OTW, thank you for posting.
Out of curiosity, are you one of these elite hackers OTW? :P
Thanks Obama... Another failed government program.
awesome read
Nice article !
I'd be glad to read a series on malware research writen by you.
Its coming.
Share Your Thoughts