Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it.

Let's begin, Why do we encrypt ?
-We encrypt, simply for privacy & secrecy
-We encrypt, in pro term : for Confidentiality & Integrity. Well, these are basics for encryption.
Now, how many of you use free/open source encryption software ? This is the time now, stop and think about your data & how you are securing it. Let me share the quote from TrueCrypt (assuming that you know about TrueCrypt), "TrueCrypt does not secure any data on a computer if an attacker has physical access to the computer before or while TrueCrypt is running on it" Ok then, why do we need such kind of encryption ?
Well now, below is a sort of FDE (Full Disk Encryption) Boot Process image of modern days CPU & I'll explain Boot Process, depending on this diagram.
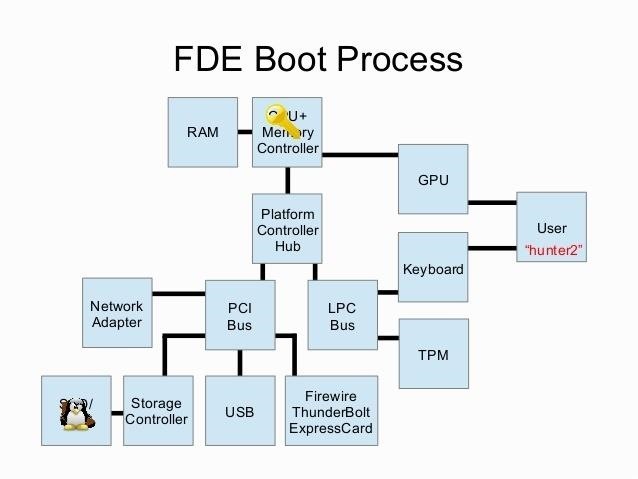
Img Src : defcon-21-selifonov
So, here is the process :
- Bootloader loads from secondary storage (SSD/HDD : Refer Image) on the computer by BIOS & it gets copied to main memory (RAM) via some sorts of so called data transfer.
- Then bootloader seeks the authentication credentials (password, tokens, keys or something like that) from USER (Refer image to find user).
- That password is then transferred to key, and is stored in RAM as long as system/computer is live/active.
- Then, bootloader transfer control to OS and then both OS & key remains in memory for transparent encryption and decryption of computer.
Coolest part is here, who might alter this process ? or try to alter ? Well, if someone tries to interfere this process, then he/she is trying to break the encryption part of disk/system. And yes, this is possible and already broken.

Img Src : eleanorburns88.files wordpress site
There are different approaches to deal with this (basically in terms of breaking the encryption). Here, in this series i'll be talking about some sorts of scripts, when executed via flash drives will then alter the FDE Boot Process. This is simply a initial approach. If, it fails.....then ? Well, next thing is, we have to now play with disk/system physically. We must try to de-attach the disk, open it with screw, and modify some sorts of chips. Some of the process involved in breaking encryption are :
- Compromised OS : In case, if victim is not using FDE. Here, admin or user gets tricked with some sort of exploits (assuming that you know about exploits), which then allows a attacker a kind of full control over systems file, logs, process & services. (other attacks will explained in next part)
Ok, world ! for now, this is it. Stay tuned for next part on this series. I have a lot to talk and share about.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























Be the First to Comment
Share Your Thoughts